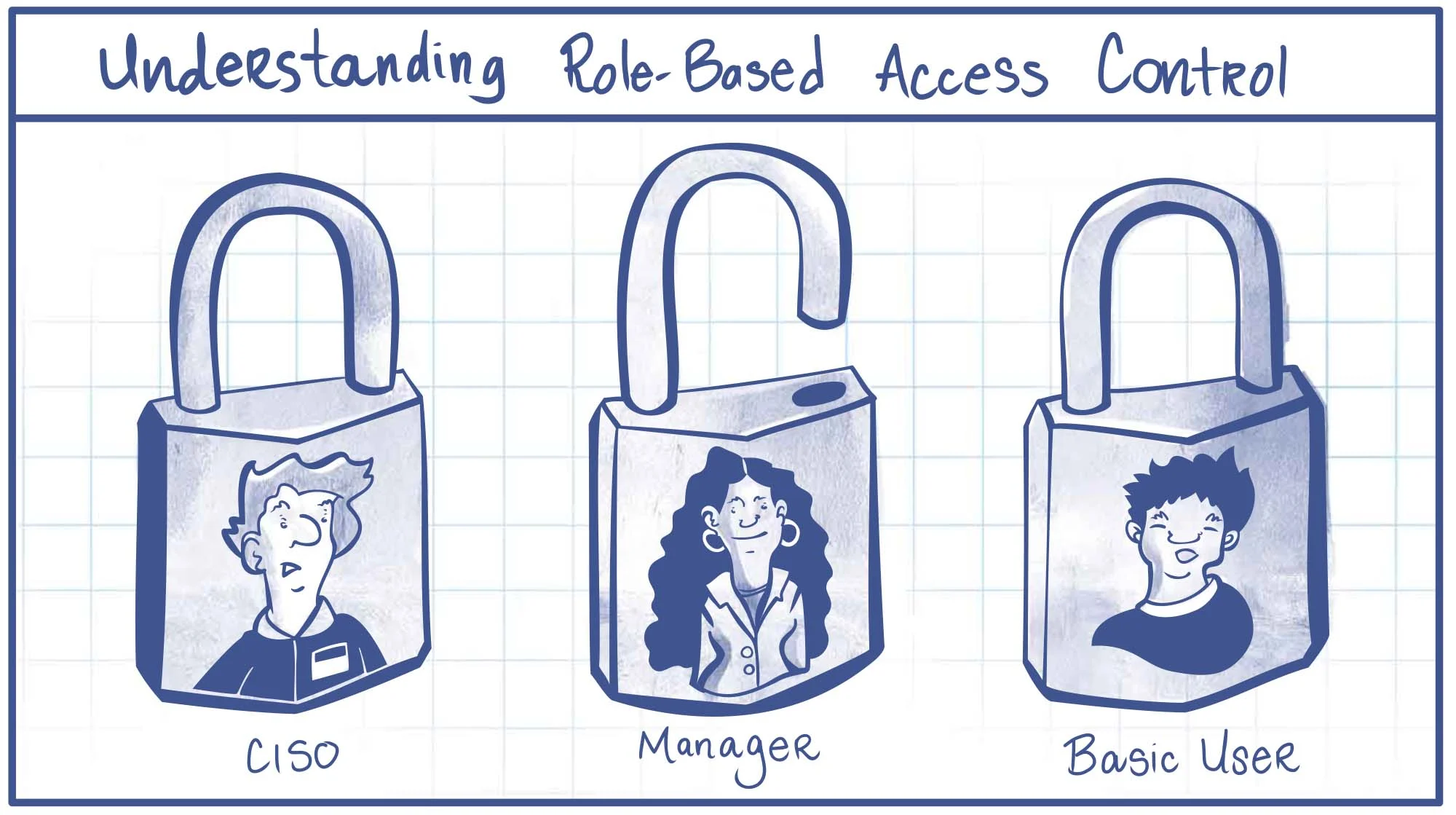
Access Control Based Security Approach . Access control is a type of security measure that limits the visibility, access, and use of resources in a computing environment. Access control is a security process that determines who can access certain resources (files, folders, apps, programs, etc.) and what they can do with them. Robust access controls secure sensitive data by making it hard for hackers to gain access. Under this model, access is granted based on the person’s job function and the resources required to do. Access control is a comprehensive data security mechanism that determines who is permitted to access specific digital resources, such as data,. Access control is crucial to identity and access management (iam) strategies, helping organizations navigate modern cybersecurity challenges. Access control systems exclude malicious actors and allow legitimate users to use company tools safely. Cybercriminals are becoming more sophisticated, utilizing advanced techniques to breach security systems and gain unauthorized access to resources.
from www.strongdm.com
Access control is a type of security measure that limits the visibility, access, and use of resources in a computing environment. Robust access controls secure sensitive data by making it hard for hackers to gain access. Access control is crucial to identity and access management (iam) strategies, helping organizations navigate modern cybersecurity challenges. Access control is a comprehensive data security mechanism that determines who is permitted to access specific digital resources, such as data,. Cybercriminals are becoming more sophisticated, utilizing advanced techniques to breach security systems and gain unauthorized access to resources. Access control is a security process that determines who can access certain resources (files, folders, apps, programs, etc.) and what they can do with them. Access control systems exclude malicious actors and allow legitimate users to use company tools safely. Under this model, access is granted based on the person’s job function and the resources required to do.
What is Rolebased access control (RBAC)?
Access Control Based Security Approach Access control systems exclude malicious actors and allow legitimate users to use company tools safely. Access control systems exclude malicious actors and allow legitimate users to use company tools safely. Under this model, access is granted based on the person’s job function and the resources required to do. Access control is a security process that determines who can access certain resources (files, folders, apps, programs, etc.) and what they can do with them. Access control is a comprehensive data security mechanism that determines who is permitted to access specific digital resources, such as data,. Robust access controls secure sensitive data by making it hard for hackers to gain access. Access control is a type of security measure that limits the visibility, access, and use of resources in a computing environment. Cybercriminals are becoming more sophisticated, utilizing advanced techniques to breach security systems and gain unauthorized access to resources. Access control is crucial to identity and access management (iam) strategies, helping organizations navigate modern cybersecurity challenges.
From www.slideserve.com
PPT Access Control, Operating System Security, and Security System Access Control Based Security Approach Access control is crucial to identity and access management (iam) strategies, helping organizations navigate modern cybersecurity challenges. Access control is a security process that determines who can access certain resources (files, folders, apps, programs, etc.) and what they can do with them. Access control systems exclude malicious actors and allow legitimate users to use company tools safely. Under this model,. Access Control Based Security Approach.
From www.slideserve.com
PPT Extended Role Based Access Control Based Design and Access Control Based Security Approach Robust access controls secure sensitive data by making it hard for hackers to gain access. Access control is a comprehensive data security mechanism that determines who is permitted to access specific digital resources, such as data,. Access control systems exclude malicious actors and allow legitimate users to use company tools safely. Under this model, access is granted based on the. Access Control Based Security Approach.
From www.secureye.com
Access Control System Need Security for Every Organization Secureye Access Control Based Security Approach Under this model, access is granted based on the person’s job function and the resources required to do. Robust access controls secure sensitive data by making it hard for hackers to gain access. Access control systems exclude malicious actors and allow legitimate users to use company tools safely. Cybercriminals are becoming more sophisticated, utilizing advanced techniques to breach security systems. Access Control Based Security Approach.
From supertokens.com
What is RolesBased Access Control (RBAC)? Access Control Based Security Approach Access control is crucial to identity and access management (iam) strategies, helping organizations navigate modern cybersecurity challenges. Cybercriminals are becoming more sophisticated, utilizing advanced techniques to breach security systems and gain unauthorized access to resources. Access control is a type of security measure that limits the visibility, access, and use of resources in a computing environment. Access control is a. Access Control Based Security Approach.
From www.strongdm.com
What is Rolebased access control (RBAC)? Access Control Based Security Approach Access control is a security process that determines who can access certain resources (files, folders, apps, programs, etc.) and what they can do with them. Access control is crucial to identity and access management (iam) strategies, helping organizations navigate modern cybersecurity challenges. Access control is a type of security measure that limits the visibility, access, and use of resources in. Access Control Based Security Approach.
From protechsecurity.com
commercial access control systems ProTech Security Access Control Based Security Approach Robust access controls secure sensitive data by making it hard for hackers to gain access. Access control systems exclude malicious actors and allow legitimate users to use company tools safely. Under this model, access is granted based on the person’s job function and the resources required to do. Cybercriminals are becoming more sophisticated, utilizing advanced techniques to breach security systems. Access Control Based Security Approach.
From www.accesscontrol.co.nz
Integrated Alarms & Access Control Access Security & Control Access Control Based Security Approach Access control is crucial to identity and access management (iam) strategies, helping organizations navigate modern cybersecurity challenges. Access control is a security process that determines who can access certain resources (files, folders, apps, programs, etc.) and what they can do with them. Access control is a type of security measure that limits the visibility, access, and use of resources in. Access Control Based Security Approach.
From www.senseon.com
Choosing Between Standalone and Integrated Electronic Access Control Access Control Based Security Approach Under this model, access is granted based on the person’s job function and the resources required to do. Cybercriminals are becoming more sophisticated, utilizing advanced techniques to breach security systems and gain unauthorized access to resources. Access control is crucial to identity and access management (iam) strategies, helping organizations navigate modern cybersecurity challenges. Access control systems exclude malicious actors and. Access Control Based Security Approach.
From www.strongdm.com
3 Types of Access Control IT Security Models Explained StrongDM Access Control Based Security Approach Access control systems exclude malicious actors and allow legitimate users to use company tools safely. Access control is a comprehensive data security mechanism that determines who is permitted to access specific digital resources, such as data,. Access control is crucial to identity and access management (iam) strategies, helping organizations navigate modern cybersecurity challenges. Access control is a type of security. Access Control Based Security Approach.
From www.researchgate.net
Access Control and Other Security Services Download Scientific Diagram Access Control Based Security Approach Under this model, access is granted based on the person’s job function and the resources required to do. Access control systems exclude malicious actors and allow legitimate users to use company tools safely. Cybercriminals are becoming more sophisticated, utilizing advanced techniques to breach security systems and gain unauthorized access to resources. Access control is a comprehensive data security mechanism that. Access Control Based Security Approach.
From www.youtube.com
Role Based Access Control YouTube Access Control Based Security Approach Cybercriminals are becoming more sophisticated, utilizing advanced techniques to breach security systems and gain unauthorized access to resources. Under this model, access is granted based on the person’s job function and the resources required to do. Access control is crucial to identity and access management (iam) strategies, helping organizations navigate modern cybersecurity challenges. Access control systems exclude malicious actors and. Access Control Based Security Approach.
From www.getgenea.com
Types of Access Control RuleBased vs RoleBased & More 2024 Guide Access Control Based Security Approach Access control is a comprehensive data security mechanism that determines who is permitted to access specific digital resources, such as data,. Cybercriminals are becoming more sophisticated, utilizing advanced techniques to breach security systems and gain unauthorized access to resources. Access control is a type of security measure that limits the visibility, access, and use of resources in a computing environment.. Access Control Based Security Approach.
From www.varonis.com
What is RoleBased Access Control (RBAC)? Access Control Based Security Approach Cybercriminals are becoming more sophisticated, utilizing advanced techniques to breach security systems and gain unauthorized access to resources. Access control is crucial to identity and access management (iam) strategies, helping organizations navigate modern cybersecurity challenges. Access control systems exclude malicious actors and allow legitimate users to use company tools safely. Access control is a security process that determines who can. Access Control Based Security Approach.
From www.harlingsecurity.com
Benefits of Access Control Systems Harling Security Access Control Based Security Approach Robust access controls secure sensitive data by making it hard for hackers to gain access. Access control is a security process that determines who can access certain resources (files, folders, apps, programs, etc.) and what they can do with them. Access control is a comprehensive data security mechanism that determines who is permitted to access specific digital resources, such as. Access Control Based Security Approach.
From thecyphere.com
Access Control Security Types Of Access Control Access Control Based Security Approach Cybercriminals are becoming more sophisticated, utilizing advanced techniques to breach security systems and gain unauthorized access to resources. Under this model, access is granted based on the person’s job function and the resources required to do. Access control is crucial to identity and access management (iam) strategies, helping organizations navigate modern cybersecurity challenges. Access control systems exclude malicious actors and. Access Control Based Security Approach.
From infosecwriteups.com
How to properly enforce authorization by Security Lit Limited Access Control Based Security Approach Access control is a security process that determines who can access certain resources (files, folders, apps, programs, etc.) and what they can do with them. Access control is crucial to identity and access management (iam) strategies, helping organizations navigate modern cybersecurity challenges. Cybercriminals are becoming more sophisticated, utilizing advanced techniques to breach security systems and gain unauthorized access to resources.. Access Control Based Security Approach.
From www.slideserve.com
PPT Security Fundamentals Models PowerPoint Presentation, free Access Control Based Security Approach Access control is crucial to identity and access management (iam) strategies, helping organizations navigate modern cybersecurity challenges. Access control systems exclude malicious actors and allow legitimate users to use company tools safely. Access control is a security process that determines who can access certain resources (files, folders, apps, programs, etc.) and what they can do with them. Under this model,. Access Control Based Security Approach.
From www.kohezion.com
How to Implement RoleBased Access Control in Your Organization Access Control Based Security Approach Access control systems exclude malicious actors and allow legitimate users to use company tools safely. Under this model, access is granted based on the person’s job function and the resources required to do. Access control is a security process that determines who can access certain resources (files, folders, apps, programs, etc.) and what they can do with them. Cybercriminals are. Access Control Based Security Approach.
From www.pingidentity.com
Once a user is authenticated, authorization is used to control what Access Control Based Security Approach Access control is a type of security measure that limits the visibility, access, and use of resources in a computing environment. Robust access controls secure sensitive data by making it hard for hackers to gain access. Cybercriminals are becoming more sophisticated, utilizing advanced techniques to breach security systems and gain unauthorized access to resources. Access control is a security process. Access Control Based Security Approach.
From www.conceptdraw.com
IT Security Solutions Access Control Based Security Approach Access control is a comprehensive data security mechanism that determines who is permitted to access specific digital resources, such as data,. Access control is crucial to identity and access management (iam) strategies, helping organizations navigate modern cybersecurity challenges. Cybercriminals are becoming more sophisticated, utilizing advanced techniques to breach security systems and gain unauthorized access to resources. Access control systems exclude. Access Control Based Security Approach.
From its-physec.com
Access Control Physical Security Solutions ITS Physec Access Control Based Security Approach Access control is crucial to identity and access management (iam) strategies, helping organizations navigate modern cybersecurity challenges. Cybercriminals are becoming more sophisticated, utilizing advanced techniques to breach security systems and gain unauthorized access to resources. Access control is a comprehensive data security mechanism that determines who is permitted to access specific digital resources, such as data,. Robust access controls secure. Access Control Based Security Approach.
From www.varonis.com
What is RoleBased Access Control (RBAC)? Access Control Based Security Approach Cybercriminals are becoming more sophisticated, utilizing advanced techniques to breach security systems and gain unauthorized access to resources. Under this model, access is granted based on the person’s job function and the resources required to do. Access control is crucial to identity and access management (iam) strategies, helping organizations navigate modern cybersecurity challenges. Access control is a security process that. Access Control Based Security Approach.
From www.how2shout.com
Guardians of Data How RoleBased Access Control Reinvents Security Access Control Based Security Approach Access control is crucial to identity and access management (iam) strategies, helping organizations navigate modern cybersecurity challenges. Robust access controls secure sensitive data by making it hard for hackers to gain access. Under this model, access is granted based on the person’s job function and the resources required to do. Cybercriminals are becoming more sophisticated, utilizing advanced techniques to breach. Access Control Based Security Approach.
From wittenbach.com
Branch Security Access Control Access Control Based Security Approach Access control is a comprehensive data security mechanism that determines who is permitted to access specific digital resources, such as data,. Access control systems exclude malicious actors and allow legitimate users to use company tools safely. Access control is a security process that determines who can access certain resources (files, folders, apps, programs, etc.) and what they can do with. Access Control Based Security Approach.
From lightrun.com
Lightrun Bolsters Security Measures with RoleBased Access Control Access Control Based Security Approach Access control is a security process that determines who can access certain resources (files, folders, apps, programs, etc.) and what they can do with them. Access control is a comprehensive data security mechanism that determines who is permitted to access specific digital resources, such as data,. Under this model, access is granted based on the person’s job function and the. Access Control Based Security Approach.
From www.gdata.pt
G DATA Layered Security thoroughly sophisticated IT security Access Control Based Security Approach Cybercriminals are becoming more sophisticated, utilizing advanced techniques to breach security systems and gain unauthorized access to resources. Robust access controls secure sensitive data by making it hard for hackers to gain access. Access control is a comprehensive data security mechanism that determines who is permitted to access specific digital resources, such as data,. Access control systems exclude malicious actors. Access Control Based Security Approach.
From flamlabelthema.netlify.app
Role Based Access Control Matrix Template Access Control Based Security Approach Access control is a type of security measure that limits the visibility, access, and use of resources in a computing environment. Access control is a security process that determines who can access certain resources (files, folders, apps, programs, etc.) and what they can do with them. Access control systems exclude malicious actors and allow legitimate users to use company tools. Access Control Based Security Approach.
From gomindsight.com
Network Access Controls (NAC) And Why You Need Them A Cybersecurity Access Control Based Security Approach Access control is a comprehensive data security mechanism that determines who is permitted to access specific digital resources, such as data,. Access control is crucial to identity and access management (iam) strategies, helping organizations navigate modern cybersecurity challenges. Robust access controls secure sensitive data by making it hard for hackers to gain access. Access control is a security process that. Access Control Based Security Approach.
From www.researchgate.net
Scheme of attributebased access control (ABAC) model. Download Access Control Based Security Approach Under this model, access is granted based on the person’s job function and the resources required to do. Access control is crucial to identity and access management (iam) strategies, helping organizations navigate modern cybersecurity challenges. Cybercriminals are becoming more sophisticated, utilizing advanced techniques to breach security systems and gain unauthorized access to resources. Robust access controls secure sensitive data by. Access Control Based Security Approach.
From jaycemeowcunningham.blogspot.com
What Function Describe the Uses of an Access Control List Access Control Based Security Approach Under this model, access is granted based on the person’s job function and the resources required to do. Access control systems exclude malicious actors and allow legitimate users to use company tools safely. Access control is crucial to identity and access management (iam) strategies, helping organizations navigate modern cybersecurity challenges. Cybercriminals are becoming more sophisticated, utilizing advanced techniques to breach. Access Control Based Security Approach.
From www.slideserve.com
PPT Security Mechanisms PowerPoint Presentation, free download ID Access Control Based Security Approach Access control is a comprehensive data security mechanism that determines who is permitted to access specific digital resources, such as data,. Cybercriminals are becoming more sophisticated, utilizing advanced techniques to breach security systems and gain unauthorized access to resources. Access control systems exclude malicious actors and allow legitimate users to use company tools safely. Access control is crucial to identity. Access Control Based Security Approach.
From searchcloudcomputing.techtarget.com
Secure data in the cloud with encryption and access controls Access Control Based Security Approach Access control is crucial to identity and access management (iam) strategies, helping organizations navigate modern cybersecurity challenges. Access control systems exclude malicious actors and allow legitimate users to use company tools safely. Access control is a security process that determines who can access certain resources (files, folders, apps, programs, etc.) and what they can do with them. Access control is. Access Control Based Security Approach.
From nexlarsecurity1.blogspot.com
Security System and Access Control Installations Company Nexlar Security Access Control Based Security Approach Robust access controls secure sensitive data by making it hard for hackers to gain access. Access control systems exclude malicious actors and allow legitimate users to use company tools safely. Access control is a comprehensive data security mechanism that determines who is permitted to access specific digital resources, such as data,. Access control is crucial to identity and access management. Access Control Based Security Approach.
From cie-group.com
How to design an Access Control system Access Control Based Security Approach Cybercriminals are becoming more sophisticated, utilizing advanced techniques to breach security systems and gain unauthorized access to resources. Access control is a type of security measure that limits the visibility, access, and use of resources in a computing environment. Robust access controls secure sensitive data by making it hard for hackers to gain access. Under this model, access is granted. Access Control Based Security Approach.
From budibase.com
RoleBased Access Control Ultimate Guide Access Control Based Security Approach Access control is a security process that determines who can access certain resources (files, folders, apps, programs, etc.) and what they can do with them. Access control is a type of security measure that limits the visibility, access, and use of resources in a computing environment. Under this model, access is granted based on the person’s job function and the. Access Control Based Security Approach.