System.security.code Access Permission.demand() . The permissions of the code that calls this method are not examined; A code access security demand checks right up the call stack, in order to ensure that the requested operation is allowed for every party. Specifies the security actions that can be performed using declarative security. Code access security is not supported or honored by the runtime. The check begins from the immediate caller of that code and continues. There can be significant delay between code change and documentation update. For example, a file class in a secure. This method is typically used by secure libraries to ensure that callers have permission to access a resource. Demand () forces a securityexception at run time if all callers higher in the call stack have not been granted the permission specified by the current. So cas is the clr's security system that. The common language runtime (clr) allows code to perform only those operations that the code has permission to perform. So we should focus on the code first, which is.
from www.slideserve.com
Demand () forces a securityexception at run time if all callers higher in the call stack have not been granted the permission specified by the current. So we should focus on the code first, which is. The permissions of the code that calls this method are not examined; A code access security demand checks right up the call stack, in order to ensure that the requested operation is allowed for every party. So cas is the clr's security system that. The common language runtime (clr) allows code to perform only those operations that the code has permission to perform. Specifies the security actions that can be performed using declarative security. Code access security is not supported or honored by the runtime. This method is typically used by secure libraries to ensure that callers have permission to access a resource. For example, a file class in a secure.
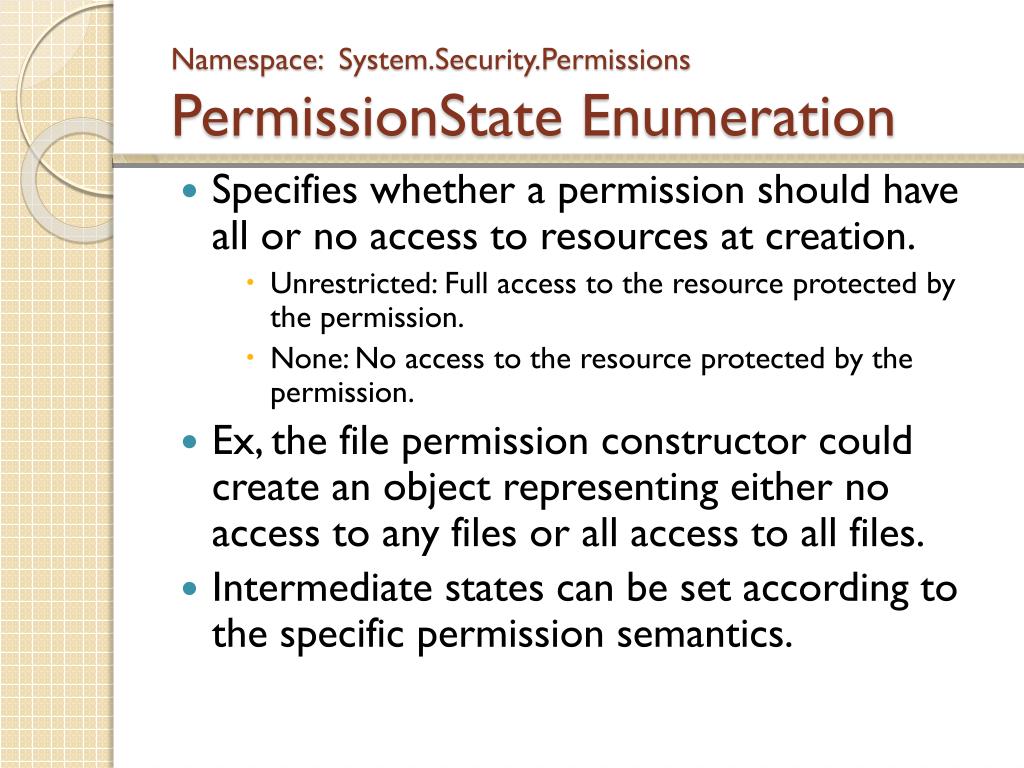
PPT System.Security.Permissions namespace PowerPoint Presentation, free download ID5514329
System.security.code Access Permission.demand() This method is typically used by secure libraries to ensure that callers have permission to access a resource. So we should focus on the code first, which is. So cas is the clr's security system that. A code access security demand checks right up the call stack, in order to ensure that the requested operation is allowed for every party. This method is typically used by secure libraries to ensure that callers have permission to access a resource. The check begins from the immediate caller of that code and continues. Code access security is not supported or honored by the runtime. For example, a file class in a secure. There can be significant delay between code change and documentation update. The permissions of the code that calls this method are not examined; Demand () forces a securityexception at run time if all callers higher in the call stack have not been granted the permission specified by the current. Specifies the security actions that can be performed using declarative security. The common language runtime (clr) allows code to perform only those operations that the code has permission to perform.
From www.winhelponline.com
Access the Advanced Security Permissions Page via Rightclick Menu in Windows 10 » System.security.code Access Permission.demand() For example, a file class in a secure. The common language runtime (clr) allows code to perform only those operations that the code has permission to perform. Demand () forces a securityexception at run time if all callers higher in the call stack have not been granted the permission specified by the current. Code access security is not supported or. System.security.code Access Permission.demand().
From flylib.com
Code Access Security and the Framework Building Portals, and Corporate System.security.code Access Permission.demand() This method is typically used by secure libraries to ensure that callers have permission to access a resource. A code access security demand checks right up the call stack, in order to ensure that the requested operation is allowed for every party. The permissions of the code that calls this method are not examined; For example, a file class in. System.security.code Access Permission.demand().
From www.codeproject.com
Implement secure MVC applications CodeProject System.security.code Access Permission.demand() There can be significant delay between code change and documentation update. So we should focus on the code first, which is. Specifies the security actions that can be performed using declarative security. For example, a file class in a secure. Code access security is not supported or honored by the runtime. The common language runtime (clr) allows code to perform. System.security.code Access Permission.demand().
From raaviblog.com
System.Security.Permissions.FileIOPermissionRequest for the Permissions A Turning Point System.security.code Access Permission.demand() So cas is the clr's security system that. The common language runtime (clr) allows code to perform only those operations that the code has permission to perform. The check begins from the immediate caller of that code and continues. Demand () forces a securityexception at run time if all callers higher in the call stack have not been granted the. System.security.code Access Permission.demand().
From slideplayer.com
Introduction to Evidencebased security Framework Brad Merrill Program System.security.code Access Permission.demand() For example, a file class in a secure. Demand () forces a securityexception at run time if all callers higher in the call stack have not been granted the permission specified by the current. So cas is the clr's security system that. The check begins from the immediate caller of that code and continues. The common language runtime (clr) allows. System.security.code Access Permission.demand().
From www.slideserve.com
PPT System.Security.Permissions namespace PowerPoint Presentation, free download ID5514329 System.security.code Access Permission.demand() So cas is the clr's security system that. There can be significant delay between code change and documentation update. A code access security demand checks right up the call stack, in order to ensure that the requested operation is allowed for every party. So we should focus on the code first, which is. The check begins from the immediate caller. System.security.code Access Permission.demand().
From www.slideserve.com
PPT System.Security.Permissions namespace PowerPoint Presentation, free download ID5514329 System.security.code Access Permission.demand() The check begins from the immediate caller of that code and continues. The permissions of the code that calls this method are not examined; Code access security is not supported or honored by the runtime. Demand () forces a securityexception at run time if all callers higher in the call stack have not been granted the permission specified by the. System.security.code Access Permission.demand().
From help.sap.com
Permission Levels System.security.code Access Permission.demand() The permissions of the code that calls this method are not examined; So cas is the clr's security system that. A code access security demand checks right up the call stack, in order to ensure that the requested operation is allowed for every party. Code access security is not supported or honored by the runtime. The check begins from the. System.security.code Access Permission.demand().
From www.slideserve.com
PPT Code security including 4.0 & Tools PowerPoint Presentation ID732778 System.security.code Access Permission.demand() This method is typically used by secure libraries to ensure that callers have permission to access a resource. The common language runtime (clr) allows code to perform only those operations that the code has permission to perform. A code access security demand checks right up the call stack, in order to ensure that the requested operation is allowed for every. System.security.code Access Permission.demand().
From www.fity.club
Permissions System.security.code Access Permission.demand() Demand () forces a securityexception at run time if all callers higher in the call stack have not been granted the permission specified by the current. There can be significant delay between code change and documentation update. For example, a file class in a secure. So cas is the clr's security system that. Specifies the security actions that can be. System.security.code Access Permission.demand().
From learn.microsoft.com
Get started with permissions, access levels, and security groups Azure DevOps Microsoft Learn System.security.code Access Permission.demand() Demand () forces a securityexception at run time if all callers higher in the call stack have not been granted the permission specified by the current. Specifies the security actions that can be performed using declarative security. So cas is the clr's security system that. Code access security is not supported or honored by the runtime. So we should focus. System.security.code Access Permission.demand().
From slideplayer.com
Security and performance ppt download System.security.code Access Permission.demand() Specifies the security actions that can be performed using declarative security. The common language runtime (clr) allows code to perform only those operations that the code has permission to perform. This method is typically used by secure libraries to ensure that callers have permission to access a resource. For example, a file class in a secure. So cas is the. System.security.code Access Permission.demand().
From www.slideserve.com
PPT System.Security.Permissions namespace PowerPoint Presentation, free download ID5514329 System.security.code Access Permission.demand() The common language runtime (clr) allows code to perform only those operations that the code has permission to perform. The permissions of the code that calls this method are not examined; This method is typically used by secure libraries to ensure that callers have permission to access a resource. Specifies the security actions that can be performed using declarative security.. System.security.code Access Permission.demand().
From www.geeksforgeeks.org
What is Code Access Security? System.security.code Access Permission.demand() The permissions of the code that calls this method are not examined; There can be significant delay between code change and documentation update. The check begins from the immediate caller of that code and continues. Specifies the security actions that can be performed using declarative security. Code access security is not supported or honored by the runtime. The common language. System.security.code Access Permission.demand().
From www.slideserve.com
PPT Framework Application Security Overview PowerPoint Presentation ID399415 System.security.code Access Permission.demand() The common language runtime (clr) allows code to perform only those operations that the code has permission to perform. So we should focus on the code first, which is. A code access security demand checks right up the call stack, in order to ensure that the requested operation is allowed for every party. There can be significant delay between code. System.security.code Access Permission.demand().
From www.slideserve.com
PPT Security PowerPoint Presentation, free download ID1719695 System.security.code Access Permission.demand() So cas is the clr's security system that. Code access security is not supported or honored by the runtime. The common language runtime (clr) allows code to perform only those operations that the code has permission to perform. The check begins from the immediate caller of that code and continues. Demand () forces a securityexception at run time if all. System.security.code Access Permission.demand().
From www.alamy.com
Authorization Permission Network Security System Concept Stock Photo Alamy System.security.code Access Permission.demand() Code access security is not supported or honored by the runtime. So we should focus on the code first, which is. There can be significant delay between code change and documentation update. A code access security demand checks right up the call stack, in order to ensure that the requested operation is allowed for every party. For example, a file. System.security.code Access Permission.demand().
From slideplayer.com
Security and performance ppt download System.security.code Access Permission.demand() The permissions of the code that calls this method are not examined; There can be significant delay between code change and documentation update. So we should focus on the code first, which is. A code access security demand checks right up the call stack, in order to ensure that the requested operation is allowed for every party. So cas is. System.security.code Access Permission.demand().
From www.slideserve.com
PPT System.Security.Permissions namespace PowerPoint Presentation, free download ID5514329 System.security.code Access Permission.demand() For example, a file class in a secure. The common language runtime (clr) allows code to perform only those operations that the code has permission to perform. Demand () forces a securityexception at run time if all callers higher in the call stack have not been granted the permission specified by the current. So we should focus on the code. System.security.code Access Permission.demand().
From www.slideserve.com
PPT Code security including 4.0 & Tools PowerPoint Presentation ID732778 System.security.code Access Permission.demand() So cas is the clr's security system that. The check begins from the immediate caller of that code and continues. A code access security demand checks right up the call stack, in order to ensure that the requested operation is allowed for every party. Demand () forces a securityexception at run time if all callers higher in the call stack. System.security.code Access Permission.demand().
From slideplayer.com
Security and performance ppt download System.security.code Access Permission.demand() The permissions of the code that calls this method are not examined; This method is typically used by secure libraries to ensure that callers have permission to access a resource. Code access security is not supported or honored by the runtime. So we should focus on the code first, which is. Demand () forces a securityexception at run time if. System.security.code Access Permission.demand().
From www.slideserve.com
PPT System.Security.Permissions namespace PowerPoint Presentation, free download ID5514329 System.security.code Access Permission.demand() Specifies the security actions that can be performed using declarative security. There can be significant delay between code change and documentation update. A code access security demand checks right up the call stack, in order to ensure that the requested operation is allowed for every party. Code access security is not supported or honored by the runtime. The check begins. System.security.code Access Permission.demand().
From www.slideserve.com
PPT System.Security.Permissions namespace PowerPoint Presentation, free download ID5514329 System.security.code Access Permission.demand() This method is typically used by secure libraries to ensure that callers have permission to access a resource. There can be significant delay between code change and documentation update. Specifies the security actions that can be performed using declarative security. A code access security demand checks right up the call stack, in order to ensure that the requested operation is. System.security.code Access Permission.demand().
From www.slideserve.com
PPT System.Security.Permissions namespace PowerPoint Presentation, free download ID5514329 System.security.code Access Permission.demand() So cas is the clr's security system that. Demand () forces a securityexception at run time if all callers higher in the call stack have not been granted the permission specified by the current. This method is typically used by secure libraries to ensure that callers have permission to access a resource. So we should focus on the code first,. System.security.code Access Permission.demand().
From www.slideserve.com
PPT System.Security.Permissions namespace PowerPoint Presentation, free download ID5514329 System.security.code Access Permission.demand() The permissions of the code that calls this method are not examined; The check begins from the immediate caller of that code and continues. Code access security is not supported or honored by the runtime. For example, a file class in a secure. The common language runtime (clr) allows code to perform only those operations that the code has permission. System.security.code Access Permission.demand().
From www.slideserve.com
PPT System.Security.Permissions namespace PowerPoint Presentation, free download ID5514329 System.security.code Access Permission.demand() The common language runtime (clr) allows code to perform only those operations that the code has permission to perform. There can be significant delay between code change and documentation update. So cas is the clr's security system that. This method is typically used by secure libraries to ensure that callers have permission to access a resource. For example, a file. System.security.code Access Permission.demand().
From www.winhelponline.com
Access the Advanced Security Permissions Page via Rightclick Menu in Windows 10 » System.security.code Access Permission.demand() The permissions of the code that calls this method are not examined; So cas is the clr's security system that. Code access security is not supported or honored by the runtime. The common language runtime (clr) allows code to perform only those operations that the code has permission to perform. Specifies the security actions that can be performed using declarative. System.security.code Access Permission.demand().
From slideplayer.com
Security and performance ppt download System.security.code Access Permission.demand() This method is typically used by secure libraries to ensure that callers have permission to access a resource. The permissions of the code that calls this method are not examined; Demand () forces a securityexception at run time if all callers higher in the call stack have not been granted the permission specified by the current. Specifies the security actions. System.security.code Access Permission.demand().
From www.slideserve.com
PPT Security PowerPoint Presentation, free download ID1719695 System.security.code Access Permission.demand() The check begins from the immediate caller of that code and continues. There can be significant delay between code change and documentation update. Code access security is not supported or honored by the runtime. The permissions of the code that calls this method are not examined; For example, a file class in a secure. The common language runtime (clr) allows. System.security.code Access Permission.demand().
From www.visual-guard.com
Dynamic Permissions System.security.code Access Permission.demand() Demand () forces a securityexception at run time if all callers higher in the call stack have not been granted the permission specified by the current. The permissions of the code that calls this method are not examined; The check begins from the immediate caller of that code and continues. So we should focus on the code first, which is.. System.security.code Access Permission.demand().
From www.iomovo.io
Importance of User Roles and Permissions for System Security System.security.code Access Permission.demand() There can be significant delay between code change and documentation update. For example, a file class in a secure. So we should focus on the code first, which is. Specifies the security actions that can be performed using declarative security. Code access security is not supported or honored by the runtime. So cas is the clr's security system that. A. System.security.code Access Permission.demand().
From slideplayer.com
Subha Desikan CSE775 Distributed Objects Spring ppt download System.security.code Access Permission.demand() So we should focus on the code first, which is. The permissions of the code that calls this method are not examined; Specifies the security actions that can be performed using declarative security. There can be significant delay between code change and documentation update. A code access security demand checks right up the call stack, in order to ensure that. System.security.code Access Permission.demand().
From slideplayer.com
Secure Implementation In Real Life ppt video online download System.security.code Access Permission.demand() The check begins from the immediate caller of that code and continues. This method is typically used by secure libraries to ensure that callers have permission to access a resource. There can be significant delay between code change and documentation update. Demand () forces a securityexception at run time if all callers higher in the call stack have not been. System.security.code Access Permission.demand().
From learn.microsoft.com
Get started with permissions, access levels, and security groups Azure DevOps Microsoft Learn System.security.code Access Permission.demand() The common language runtime (clr) allows code to perform only those operations that the code has permission to perform. The permissions of the code that calls this method are not examined; This method is typically used by secure libraries to ensure that callers have permission to access a resource. So we should focus on the code first, which is. Demand. System.security.code Access Permission.demand().
From slideplayer.com
Security and performance ppt download System.security.code Access Permission.demand() The permissions of the code that calls this method are not examined; Code access security is not supported or honored by the runtime. Specifies the security actions that can be performed using declarative security. This method is typically used by secure libraries to ensure that callers have permission to access a resource. Demand () forces a securityexception at run time. System.security.code Access Permission.demand().