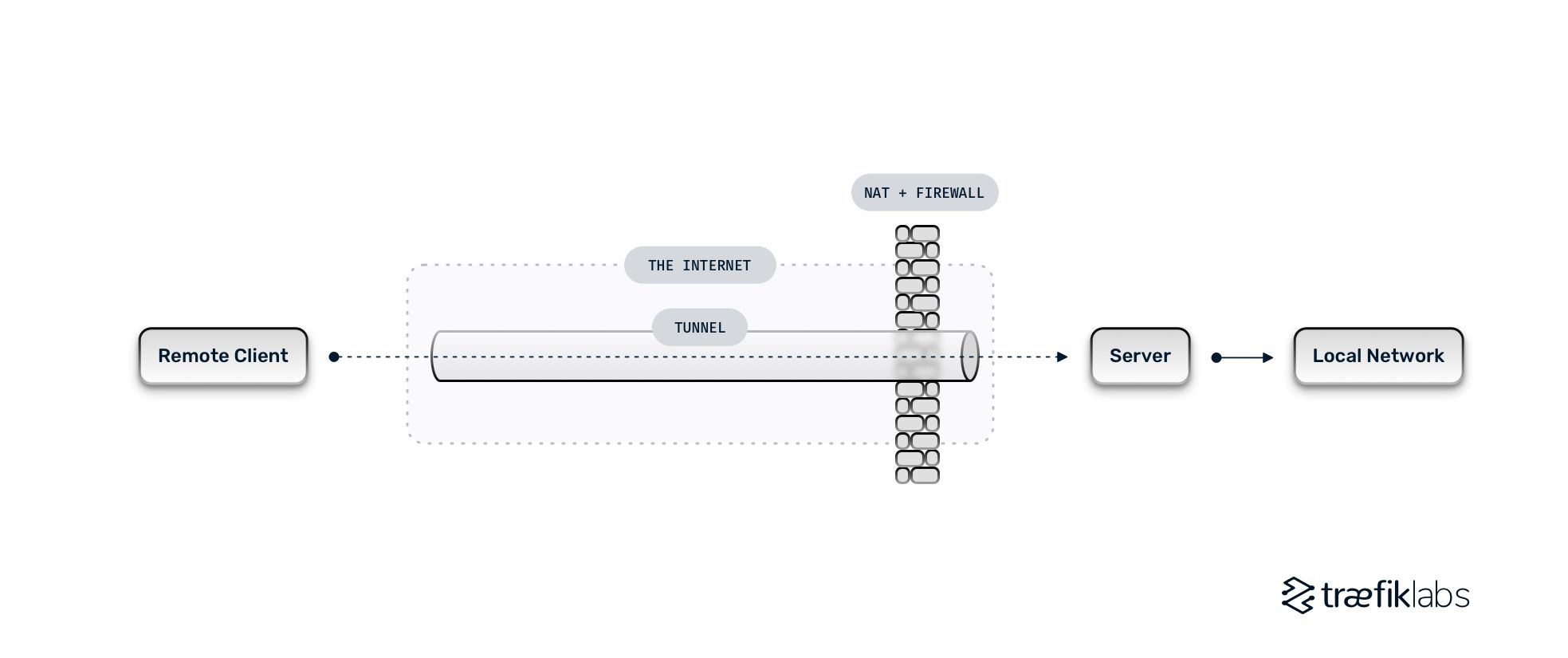
Tunneling Explained . tunneling is a networking technique used to securely transfer data over a public network. It can also be used to implement vpns (virtual private networks) and access intranet services across firewalls. a comprehensive guide to tunneling in networking, including how it works, types of tunneling, pros and cons,. It can be used to add encryption to legacy applications. Learn more about tunneling protocols here. ssh tunneling is a method of transporting arbitrary networking data over an encrypted ssh connection. tunneling is a method of discretely transmitting data across an otherwise public network. The transmission takes place using a public network; tunneling is redirecting network traffic from one port to another to enable secure access to network traffic and services across. tunneling is a protocol that allows for the secure movement of data from one network to another.
from traefik.io
a comprehensive guide to tunneling in networking, including how it works, types of tunneling, pros and cons,. tunneling is a method of discretely transmitting data across an otherwise public network. tunneling is redirecting network traffic from one port to another to enable secure access to network traffic and services across. tunneling is a protocol that allows for the secure movement of data from one network to another. ssh tunneling is a method of transporting arbitrary networking data over an encrypted ssh connection. tunneling is a networking technique used to securely transfer data over a public network. Learn more about tunneling protocols here. It can also be used to implement vpns (virtual private networks) and access intranet services across firewalls. The transmission takes place using a public network; It can be used to add encryption to legacy applications.
What Is Network Tunneling & How Is It Used? Traefik Labs
Tunneling Explained tunneling is a protocol that allows for the secure movement of data from one network to another. tunneling is a method of discretely transmitting data across an otherwise public network. a comprehensive guide to tunneling in networking, including how it works, types of tunneling, pros and cons,. tunneling is a networking technique used to securely transfer data over a public network. It can also be used to implement vpns (virtual private networks) and access intranet services across firewalls. tunneling is a protocol that allows for the secure movement of data from one network to another. ssh tunneling is a method of transporting arbitrary networking data over an encrypted ssh connection. Learn more about tunneling protocols here. tunneling is redirecting network traffic from one port to another to enable secure access to network traffic and services across. The transmission takes place using a public network; It can be used to add encryption to legacy applications.
From evuzzo.com
SSH Tunnel and SSH Tunneling Explained Evuzzo Tunneling Explained Learn more about tunneling protocols here. ssh tunneling is a method of transporting arbitrary networking data over an encrypted ssh connection. It can also be used to implement vpns (virtual private networks) and access intranet services across firewalls. a comprehensive guide to tunneling in networking, including how it works, types of tunneling, pros and cons,. tunneling is. Tunneling Explained.
From geekflare.com
VPN Split Tunneling How to Use It to Maximize Security and Performance Tunneling Explained tunneling is a protocol that allows for the secure movement of data from one network to another. It can also be used to implement vpns (virtual private networks) and access intranet services across firewalls. Learn more about tunneling protocols here. tunneling is redirecting network traffic from one port to another to enable secure access to network traffic and. Tunneling Explained.
From www.youtube.com
Quantum Tunneling Explained What is quantum tunneling ? Quantum Tunneling Explained ssh tunneling is a method of transporting arbitrary networking data over an encrypted ssh connection. a comprehensive guide to tunneling in networking, including how it works, types of tunneling, pros and cons,. tunneling is a method of discretely transmitting data across an otherwise public network. It can also be used to implement vpns (virtual private networks) and. Tunneling Explained.
From www.slideserve.com
PPT Venous Access PowerPoint Presentation ID349907 Tunneling Explained tunneling is a protocol that allows for the secure movement of data from one network to another. The transmission takes place using a public network; It can be used to add encryption to legacy applications. a comprehensive guide to tunneling in networking, including how it works, types of tunneling, pros and cons,. Learn more about tunneling protocols here.. Tunneling Explained.
From onheaven.co.in
What is Quantum Tunneling? Explained Onheaven Tunneling Explained It can also be used to implement vpns (virtual private networks) and access intranet services across firewalls. Learn more about tunneling protocols here. tunneling is a networking technique used to securely transfer data over a public network. tunneling is a protocol that allows for the secure movement of data from one network to another. tunneling is a. Tunneling Explained.
From traefik.io
What Is Network Tunneling & How Is It Used? Traefik Labs Tunneling Explained Learn more about tunneling protocols here. The transmission takes place using a public network; It can be used to add encryption to legacy applications. ssh tunneling is a method of transporting arbitrary networking data over an encrypted ssh connection. tunneling is a method of discretely transmitting data across an otherwise public network. It can also be used to. Tunneling Explained.
From www.youtube.com
DNS Tunneling Explained 11th Steps NUS YouTube Tunneling Explained tunneling is a protocol that allows for the secure movement of data from one network to another. tunneling is a networking technique used to securely transfer data over a public network. tunneling is redirecting network traffic from one port to another to enable secure access to network traffic and services across. tunneling is a method of. Tunneling Explained.
From www.slideserve.com
PPT Molecular Mechanics & Quantum Chemistry PowerPoint Presentation Tunneling Explained a comprehensive guide to tunneling in networking, including how it works, types of tunneling, pros and cons,. It can also be used to implement vpns (virtual private networks) and access intranet services across firewalls. ssh tunneling is a method of transporting arbitrary networking data over an encrypted ssh connection. tunneling is redirecting network traffic from one port. Tunneling Explained.
From www.slideserve.com
PPT Quantum Tunneling PowerPoint Presentation, free download ID1410202 Tunneling Explained The transmission takes place using a public network; Learn more about tunneling protocols here. It can also be used to implement vpns (virtual private networks) and access intranet services across firewalls. tunneling is a method of discretely transmitting data across an otherwise public network. tunneling is a networking technique used to securely transfer data over a public network.. Tunneling Explained.
From exopluxtx.blob.core.windows.net
Tunneling Meaning In Medical Terminology at Norma Benoit blog Tunneling Explained ssh tunneling is a method of transporting arbitrary networking data over an encrypted ssh connection. tunneling is redirecting network traffic from one port to another to enable secure access to network traffic and services across. The transmission takes place using a public network; tunneling is a networking technique used to securely transfer data over a public network.. Tunneling Explained.
From poddtoppen.se
SSH Tunneling Explained Protocol Lyssna här Poddtoppen.se Tunneling Explained ssh tunneling is a method of transporting arbitrary networking data over an encrypted ssh connection. Learn more about tunneling protocols here. tunneling is a method of discretely transmitting data across an otherwise public network. tunneling is redirecting network traffic from one port to another to enable secure access to network traffic and services across. tunneling is. Tunneling Explained.
From www.studocu.com
Tinkernut. (2019 ). SSH Tunneling Explained “Tinkernut. (2019). SSH Tunneling Explained tunneling is redirecting network traffic from one port to another to enable secure access to network traffic and services across. tunneling is a method of discretely transmitting data across an otherwise public network. It can also be used to implement vpns (virtual private networks) and access intranet services across firewalls. It can be used to add encryption to. Tunneling Explained.
From dataprot.net
What Is Split Tunneling? Best of Both Worlds DataProt Guides Tunneling Explained It can be used to add encryption to legacy applications. The transmission takes place using a public network; a comprehensive guide to tunneling in networking, including how it works, types of tunneling, pros and cons,. It can also be used to implement vpns (virtual private networks) and access intranet services across firewalls. tunneling is a protocol that allows. Tunneling Explained.
From www.researchgate.net
Cut and Cover Method for the Shallow tunneling Download Scientific Tunneling Explained It can be used to add encryption to legacy applications. a comprehensive guide to tunneling in networking, including how it works, types of tunneling, pros and cons,. tunneling is a protocol that allows for the secure movement of data from one network to another. It can also be used to implement vpns (virtual private networks) and access intranet. Tunneling Explained.
From www.youtube.com
DNS Tunneling Explained TryHackMe DNS Data Exfiltration YouTube Tunneling Explained tunneling is a protocol that allows for the secure movement of data from one network to another. The transmission takes place using a public network; tunneling is redirecting network traffic from one port to another to enable secure access to network traffic and services across. tunneling is a networking technique used to securely transfer data over a. Tunneling Explained.
From gcore.com
What Is Tunneling? How Does Network Tunneling Work? Gcore Tunneling Explained a comprehensive guide to tunneling in networking, including how it works, types of tunneling, pros and cons,. tunneling is a networking technique used to securely transfer data over a public network. It can also be used to implement vpns (virtual private networks) and access intranet services across firewalls. tunneling is a protocol that allows for the secure. Tunneling Explained.
From civilmint.com
New Austrian Tunneling Method Explained Tunneling Explained ssh tunneling is a method of transporting arbitrary networking data over an encrypted ssh connection. Learn more about tunneling protocols here. tunneling is redirecting network traffic from one port to another to enable secure access to network traffic and services across. It can be used to add encryption to legacy applications. tunneling is a method of discretely. Tunneling Explained.
From www.youtube.com
VPN Tunneling and VPN Tunneling Protocols Explained YouTube Tunneling Explained ssh tunneling is a method of transporting arbitrary networking data over an encrypted ssh connection. a comprehensive guide to tunneling in networking, including how it works, types of tunneling, pros and cons,. tunneling is redirecting network traffic from one port to another to enable secure access to network traffic and services across. It can also be used. Tunneling Explained.
From www.youtube.com
Unveiling the Unseen Quantum Tunneling Explained! YouTube Tunneling Explained The transmission takes place using a public network; ssh tunneling is a method of transporting arbitrary networking data over an encrypted ssh connection. It can also be used to implement vpns (virtual private networks) and access intranet services across firewalls. tunneling is a protocol that allows for the secure movement of data from one network to another. . Tunneling Explained.
From www.youtube.com
SSH Tunneling Explained With Examples YouTube Tunneling Explained tunneling is a protocol that allows for the secure movement of data from one network to another. tunneling is a method of discretely transmitting data across an otherwise public network. ssh tunneling is a method of transporting arbitrary networking data over an encrypted ssh connection. a comprehensive guide to tunneling in networking, including how it works,. Tunneling Explained.
From www.youtube.com
Quantum Tunneling Explained YouTube Tunneling Explained It can be used to add encryption to legacy applications. tunneling is a protocol that allows for the secure movement of data from one network to another. Learn more about tunneling protocols here. tunneling is redirecting network traffic from one port to another to enable secure access to network traffic and services across. The transmission takes place using. Tunneling Explained.
From github.com
GitHub yaobinwen/sshtunnelingexplained Explain what is SSH Tunneling Explained The transmission takes place using a public network; Learn more about tunneling protocols here. tunneling is redirecting network traffic from one port to another to enable secure access to network traffic and services across. It can be used to add encryption to legacy applications. a comprehensive guide to tunneling in networking, including how it works, types of tunneling,. Tunneling Explained.
From systemforce.co.uk
VPN Split Tunneling Pros and Cons What You Should Know System Force Tunneling Explained tunneling is a method of discretely transmitting data across an otherwise public network. It can be used to add encryption to legacy applications. The transmission takes place using a public network; tunneling is redirecting network traffic from one port to another to enable secure access to network traffic and services across. tunneling is a networking technique used. Tunneling Explained.
From goteleport.com
What is SSH Tunnel, SSH Reverse Tunnel and SSH Port Forwarding? Tunneling Explained tunneling is redirecting network traffic from one port to another to enable secure access to network traffic and services across. It can also be used to implement vpns (virtual private networks) and access intranet services across firewalls. tunneling is a protocol that allows for the secure movement of data from one network to another. ssh tunneling is. Tunneling Explained.
From www.youtube.com
Quantum Tunneling Explained and Modeled with Numpy Python YouTube Tunneling Explained tunneling is a method of discretely transmitting data across an otherwise public network. It can also be used to implement vpns (virtual private networks) and access intranet services across firewalls. tunneling is a protocol that allows for the secure movement of data from one network to another. Learn more about tunneling protocols here. It can be used to. Tunneling Explained.
From www.slideserve.com
PPT Learning to Live and Work with Virtual Private Networks Tunneling Explained It can be used to add encryption to legacy applications. tunneling is a networking technique used to securely transfer data over a public network. Learn more about tunneling protocols here. tunneling is a method of discretely transmitting data across an otherwise public network. ssh tunneling is a method of transporting arbitrary networking data over an encrypted ssh. Tunneling Explained.
From www.youtube.com
Quantum 101 Episode 9 Quantum Tunneling Explained YouTube Tunneling Explained tunneling is a networking technique used to securely transfer data over a public network. The transmission takes place using a public network; a comprehensive guide to tunneling in networking, including how it works, types of tunneling, pros and cons,. Learn more about tunneling protocols here. It can be used to add encryption to legacy applications. It can also. Tunneling Explained.
From www.socinvestigation.com
How DNS Tunneling works Detection & Response Security Investigation Tunneling Explained tunneling is a protocol that allows for the secure movement of data from one network to another. ssh tunneling is a method of transporting arbitrary networking data over an encrypted ssh connection. tunneling is a method of discretely transmitting data across an otherwise public network. It can be used to add encryption to legacy applications. tunneling. Tunneling Explained.
From chem.libretexts.org
Tunneling Chemistry LibreTexts Tunneling Explained ssh tunneling is a method of transporting arbitrary networking data over an encrypted ssh connection. tunneling is a protocol that allows for the secure movement of data from one network to another. tunneling is a networking technique used to securely transfer data over a public network. The transmission takes place using a public network; tunneling is. Tunneling Explained.
From www.mpg.de
Electrons caught in the act of tunnelling MaxPlanckGesellschaft Tunneling Explained Learn more about tunneling protocols here. The transmission takes place using a public network; It can also be used to implement vpns (virtual private networks) and access intranet services across firewalls. It can be used to add encryption to legacy applications. tunneling is a networking technique used to securely transfer data over a public network. tunneling is redirecting. Tunneling Explained.
From www.slideserve.com
PPT Network Protocol Tunneling PowerPoint Presentation, free download Tunneling Explained It can also be used to implement vpns (virtual private networks) and access intranet services across firewalls. a comprehensive guide to tunneling in networking, including how it works, types of tunneling, pros and cons,. tunneling is a networking technique used to securely transfer data over a public network. It can be used to add encryption to legacy applications.. Tunneling Explained.
From onlinecloudsecurity.com
How is Tunneling in a VPN? Explained Tunneling Explained It can also be used to implement vpns (virtual private networks) and access intranet services across firewalls. tunneling is a networking technique used to securely transfer data over a public network. tunneling is redirecting network traffic from one port to another to enable secure access to network traffic and services across. Learn more about tunneling protocols here. . Tunneling Explained.
From medium.com
GTP (GPRS Tunneling Protocol). Why we need a tunneling protocol ? by Tunneling Explained a comprehensive guide to tunneling in networking, including how it works, types of tunneling, pros and cons,. Learn more about tunneling protocols here. ssh tunneling is a method of transporting arbitrary networking data over an encrypted ssh connection. tunneling is redirecting network traffic from one port to another to enable secure access to network traffic and services. Tunneling Explained.
From weibeld.net
How VPN Tunnelling Works Tunneling Explained a comprehensive guide to tunneling in networking, including how it works, types of tunneling, pros and cons,. ssh tunneling is a method of transporting arbitrary networking data over an encrypted ssh connection. It can also be used to implement vpns (virtual private networks) and access intranet services across firewalls. tunneling is a method of discretely transmitting data. Tunneling Explained.
From civilsitevisit.com
New Austrian Tunneling Method (NATM) CIVIL SITE VISIT Tunneling Explained The transmission takes place using a public network; Learn more about tunneling protocols here. tunneling is a protocol that allows for the secure movement of data from one network to another. tunneling is a method of discretely transmitting data across an otherwise public network. ssh tunneling is a method of transporting arbitrary networking data over an encrypted. Tunneling Explained.