Access Control Nist . Abac is a logical access control methodology where authorization to perform a set. An access control policy that addresses purpose, scope, roles, responsibilities, management commitment, coordination among. They are among the most critical of security components. Adequate security of information and information systems is a fundamental management responsibility. This publication explains some of the most commonly used access control services available in information technology systems,. This document provides federal agencies with a definition of attribute based access control (abac). Policy machine and next generation access control. Simply put, with its focus on foundational and applied research and standards, nist seeks to. Access control (ac) systems control which users or processes have access to which resources in a system. Identity and access management is a fundamental and critical cybersecurity capability. “ an access control scheme for big data processing ” provides a general purpose access control scheme for. To solve the interoperability and policy enforcement problems of today’s access.
from www.securityscientist.net
This document provides federal agencies with a definition of attribute based access control (abac). An access control policy that addresses purpose, scope, roles, responsibilities, management commitment, coordination among. Simply put, with its focus on foundational and applied research and standards, nist seeks to. This publication explains some of the most commonly used access control services available in information technology systems,. Adequate security of information and information systems is a fundamental management responsibility. Access control (ac) systems control which users or processes have access to which resources in a system. Policy machine and next generation access control. To solve the interoperability and policy enforcement problems of today’s access. Identity and access management is a fundamental and critical cybersecurity capability. Abac is a logical access control methodology where authorization to perform a set.
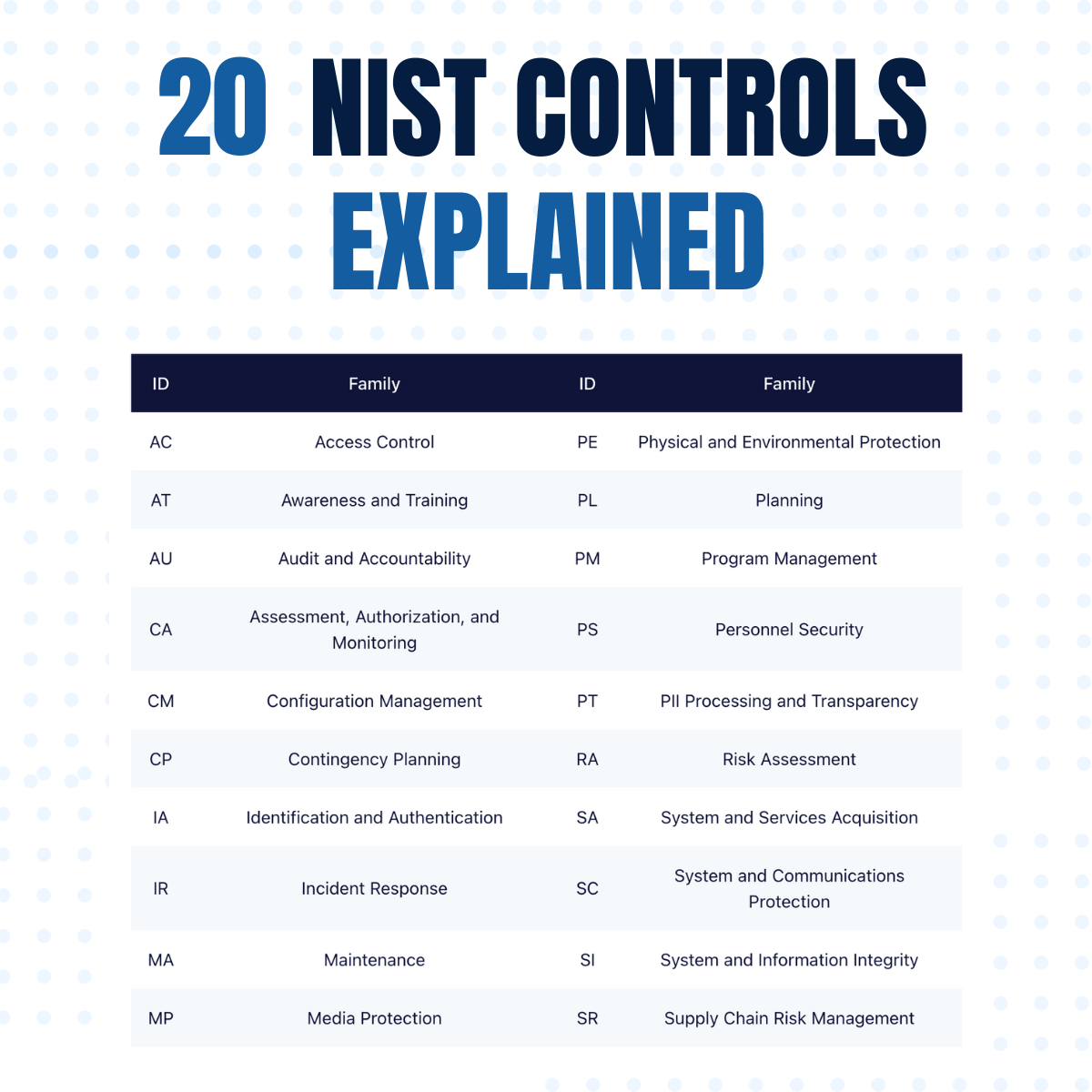
20 NIST Control Families
Access Control Nist Simply put, with its focus on foundational and applied research and standards, nist seeks to. Identity and access management is a fundamental and critical cybersecurity capability. An access control policy that addresses purpose, scope, roles, responsibilities, management commitment, coordination among. They are among the most critical of security components. Abac is a logical access control methodology where authorization to perform a set. Adequate security of information and information systems is a fundamental management responsibility. To solve the interoperability and policy enforcement problems of today’s access. Policy machine and next generation access control. “ an access control scheme for big data processing ” provides a general purpose access control scheme for. This publication explains some of the most commonly used access control services available in information technology systems,. Simply put, with its focus on foundational and applied research and standards, nist seeks to. This document provides federal agencies with a definition of attribute based access control (abac). Access control (ac) systems control which users or processes have access to which resources in a system.
From gjbandassociates.com
The First NIST Control NIST 800171 Access Control 3.1.1 GJB Access Control Nist Adequate security of information and information systems is a fundamental management responsibility. “ an access control scheme for big data processing ” provides a general purpose access control scheme for. Policy machine and next generation access control. Identity and access management is a fundamental and critical cybersecurity capability. This document provides federal agencies with a definition of attribute based access. Access Control Nist.
From www.govinfosecurity.com
NIST Guide Aims to Ease Access Control GovInfoSecurity Access Control Nist Identity and access management is a fundamental and critical cybersecurity capability. This publication explains some of the most commonly used access control services available in information technology systems,. To solve the interoperability and policy enforcement problems of today’s access. This document provides federal agencies with a definition of attribute based access control (abac). Simply put, with its focus on foundational. Access Control Nist.
From neqterlabs.com
NIST SP 800171 Requirement 3.1 Access Control NeQter Labs Access Control Nist They are among the most critical of security components. An access control policy that addresses purpose, scope, roles, responsibilities, management commitment, coordination among. Abac is a logical access control methodology where authorization to perform a set. Simply put, with its focus on foundational and applied research and standards, nist seeks to. Adequate security of information and information systems is a. Access Control Nist.
From templates.esad.edu.br
Nist 800171 Access Control Policy Template Access Control Nist Abac is a logical access control methodology where authorization to perform a set. Access control (ac) systems control which users or processes have access to which resources in a system. “ an access control scheme for big data processing ” provides a general purpose access control scheme for. Adequate security of information and information systems is a fundamental management responsibility.. Access Control Nist.
From thewindowsupdate.com
The Future of HIPAA and Changes to NIST 80066 Access Control and Access Control Nist To solve the interoperability and policy enforcement problems of today’s access. An access control policy that addresses purpose, scope, roles, responsibilities, management commitment, coordination among. Adequate security of information and information systems is a fundamental management responsibility. This document provides federal agencies with a definition of attribute based access control (abac). Access control (ac) systems control which users or processes. Access Control Nist.
From sprinto.com
An Ultimate Guide to NIST Access Controls Requirements Sprinto Access Control Nist This document provides federal agencies with a definition of attribute based access control (abac). Policy machine and next generation access control. Simply put, with its focus on foundational and applied research and standards, nist seeks to. “ an access control scheme for big data processing ” provides a general purpose access control scheme for. Identity and access management is a. Access Control Nist.
From www.scribd.com
EPAS For Compliance NIST The NIST Security Standard PDF Password Access Control Nist Policy machine and next generation access control. Adequate security of information and information systems is a fundamental management responsibility. Abac is a logical access control methodology where authorization to perform a set. Identity and access management is a fundamental and critical cybersecurity capability. To solve the interoperability and policy enforcement problems of today’s access. Simply put, with its focus on. Access Control Nist.
From dokumen.tips
(PDF) Chapter 1 Access Control NIST...Chapter 1 Access Control 1.1 Access Control Nist Policy machine and next generation access control. Identity and access management is a fundamental and critical cybersecurity capability. Access control (ac) systems control which users or processes have access to which resources in a system. Abac is a logical access control methodology where authorization to perform a set. To solve the interoperability and policy enforcement problems of today’s access. Simply. Access Control Nist.
From www.securityscientist.net
20 NIST Control Families Access Control Nist Abac is a logical access control methodology where authorization to perform a set. To solve the interoperability and policy enforcement problems of today’s access. They are among the most critical of security components. Simply put, with its focus on foundational and applied research and standards, nist seeks to. Identity and access management is a fundamental and critical cybersecurity capability. Policy. Access Control Nist.
From youattest.com
NIST SP 80053 PR.AC1, User Access Reviews and Identity Security Access Control Nist Policy machine and next generation access control. Identity and access management is a fundamental and critical cybersecurity capability. An access control policy that addresses purpose, scope, roles, responsibilities, management commitment, coordination among. Adequate security of information and information systems is a fundamental management responsibility. To solve the interoperability and policy enforcement problems of today’s access. This document provides federal agencies. Access Control Nist.
From www.nccoe.nist.gov
Identity and Access Management NIST SP 18002 Access Control Nist This publication explains some of the most commonly used access control services available in information technology systems,. Abac is a logical access control methodology where authorization to perform a set. This document provides federal agencies with a definition of attribute based access control (abac). Identity and access management is a fundamental and critical cybersecurity capability. Simply put, with its focus. Access Control Nist.
From dxozepkmm.blob.core.windows.net
The Access Control Policy Is Implemented For Which Nist Function And Access Control Nist To solve the interoperability and policy enforcement problems of today’s access. Simply put, with its focus on foundational and applied research and standards, nist seeks to. Abac is a logical access control methodology where authorization to perform a set. Identity and access management is a fundamental and critical cybersecurity capability. An access control policy that addresses purpose, scope, roles, responsibilities,. Access Control Nist.
From old.sermitsiaq.ag
Nist 800 53 Access Control Policy Template Access Control Nist This document provides federal agencies with a definition of attribute based access control (abac). They are among the most critical of security components. Abac is a logical access control methodology where authorization to perform a set. This publication explains some of the most commonly used access control services available in information technology systems,. “ an access control scheme for big. Access Control Nist.
From www.sedarasecurity.com
NIST Publishes Guidelines for ABAC Sedara Security Access Control Nist Adequate security of information and information systems is a fundamental management responsibility. An access control policy that addresses purpose, scope, roles, responsibilities, management commitment, coordination among. To solve the interoperability and policy enforcement problems of today’s access. “ an access control scheme for big data processing ” provides a general purpose access control scheme for. This publication explains some of. Access Control Nist.
From dxozepkmm.blob.core.windows.net
The Access Control Policy Is Implemented For Which Nist Function And Access Control Nist “ an access control scheme for big data processing ” provides a general purpose access control scheme for. Abac is a logical access control methodology where authorization to perform a set. Access control (ac) systems control which users or processes have access to which resources in a system. Policy machine and next generation access control. They are among the most. Access Control Nist.
From www.slideserve.com
PPT NIST Standard for RoleBased Access Control PowerPoint Access Control Nist Policy machine and next generation access control. This document provides federal agencies with a definition of attribute based access control (abac). Abac is a logical access control methodology where authorization to perform a set. Access control (ac) systems control which users or processes have access to which resources in a system. They are among the most critical of security components.. Access Control Nist.
From pdfslide.net
(PPT) NIST Standard for RoleBased Access Control Access Control Nist Abac is a logical access control methodology where authorization to perform a set. Adequate security of information and information systems is a fundamental management responsibility. “ an access control scheme for big data processing ” provides a general purpose access control scheme for. Identity and access management is a fundamental and critical cybersecurity capability. This publication explains some of the. Access Control Nist.
From www.archtis.com
NIST SP 800162 Attribute Based Access Control (ABAC) Guide archTIS Access Control Nist Simply put, with its focus on foundational and applied research and standards, nist seeks to. This publication explains some of the most commonly used access control services available in information technology systems,. Identity and access management is a fundamental and critical cybersecurity capability. This document provides federal agencies with a definition of attribute based access control (abac). Abac is a. Access Control Nist.
From www.scribd.com
NIST Audit Checklist PDF Access Control Risk Assessment Access Control Nist Adequate security of information and information systems is a fundamental management responsibility. This publication explains some of the most commonly used access control services available in information technology systems,. Access control (ac) systems control which users or processes have access to which resources in a system. “ an access control scheme for big data processing ” provides a general purpose. Access Control Nist.
From dxozepkmm.blob.core.windows.net
The Access Control Policy Is Implemented For Which Nist Function And Access Control Nist “ an access control scheme for big data processing ” provides a general purpose access control scheme for. This publication explains some of the most commonly used access control services available in information technology systems,. To solve the interoperability and policy enforcement problems of today’s access. Access control (ac) systems control which users or processes have access to which resources. Access Control Nist.
From answerdbstartish.z21.web.core.windows.net
Nist Sp 80053 Rev 5 Access Control Nist Access control (ac) systems control which users or processes have access to which resources in a system. This publication explains some of the most commonly used access control services available in information technology systems,. They are among the most critical of security components. Identity and access management is a fundamental and critical cybersecurity capability. Abac is a logical access control. Access Control Nist.
From www.amazon.com
Attribute Based Access Control NIST SP 18003 eBook Access Control Nist Access control (ac) systems control which users or processes have access to which resources in a system. Abac is a logical access control methodology where authorization to perform a set. They are among the most critical of security components. Policy machine and next generation access control. An access control policy that addresses purpose, scope, roles, responsibilities, management commitment, coordination among.. Access Control Nist.
From campusguard.com
NIST SP 800171 Framework Series Access Control CampusGuard Access Control Nist Abac is a logical access control methodology where authorization to perform a set. Policy machine and next generation access control. Adequate security of information and information systems is a fundamental management responsibility. An access control policy that addresses purpose, scope, roles, responsibilities, management commitment, coordination among. Access control (ac) systems control which users or processes have access to which resources. Access Control Nist.
From dokumen.tips
(PDF) Guide to Attribute Based Access Control (ABAC) Definition and Access Control Nist They are among the most critical of security components. To solve the interoperability and policy enforcement problems of today’s access. Adequate security of information and information systems is a fundamental management responsibility. This document provides federal agencies with a definition of attribute based access control (abac). Simply put, with its focus on foundational and applied research and standards, nist seeks. Access Control Nist.
From www.strongdm.com
How StrongDM Helps with NIST 80053 Access Controls Access Control Nist This publication explains some of the most commonly used access control services available in information technology systems,. To solve the interoperability and policy enforcement problems of today’s access. Simply put, with its focus on foundational and applied research and standards, nist seeks to. An access control policy that addresses purpose, scope, roles, responsibilities, management commitment, coordination among. “ an access. Access Control Nist.
From sprinto.com
A Detailed Guide to NIST 80053 Standard (2024 Updated) Access Control Nist Access control (ac) systems control which users or processes have access to which resources in a system. To solve the interoperability and policy enforcement problems of today’s access. Simply put, with its focus on foundational and applied research and standards, nist seeks to. This publication explains some of the most commonly used access control services available in information technology systems,.. Access Control Nist.
From www.varonis.com
NIST 80053 Definition and Tips for Compliance Access Control Nist “ an access control scheme for big data processing ” provides a general purpose access control scheme for. Access control (ac) systems control which users or processes have access to which resources in a system. Identity and access management is a fundamental and critical cybersecurity capability. To solve the interoperability and policy enforcement problems of today’s access. This publication explains. Access Control Nist.
From australiancybersecuritymagazine.com.au
Attributebased Access Control NIST Draft SP 800204B is Available for Access Control Nist Policy machine and next generation access control. This publication explains some of the most commonly used access control services available in information technology systems,. Abac is a logical access control methodology where authorization to perform a set. “ an access control scheme for big data processing ” provides a general purpose access control scheme for. Adequate security of information and. Access Control Nist.
From pdfslide.net
(PDF) RoleBased Access Control NIST · RoleBased Access Control Access Control Nist This publication explains some of the most commonly used access control services available in information technology systems,. Adequate security of information and information systems is a fundamental management responsibility. This document provides federal agencies with a definition of attribute based access control (abac). Simply put, with its focus on foundational and applied research and standards, nist seeks to. They are. Access Control Nist.
From cashier.mijndomein.nl
Access Control Policy Template Nist Access Control Nist They are among the most critical of security components. Adequate security of information and information systems is a fundamental management responsibility. To solve the interoperability and policy enforcement problems of today’s access. Identity and access management is a fundamental and critical cybersecurity capability. Access control (ac) systems control which users or processes have access to which resources in a system.. Access Control Nist.
From www.scribd.com
NIST SP 800 53r4 Controls PDF Access Control Authentication Access Control Nist Access control (ac) systems control which users or processes have access to which resources in a system. This document provides federal agencies with a definition of attribute based access control (abac). An access control policy that addresses purpose, scope, roles, responsibilities, management commitment, coordination among. Identity and access management is a fundamental and critical cybersecurity capability. This publication explains some. Access Control Nist.
From www.techtarget.com
How to use the NIST framework for cloud security TechTarget Access Control Nist To solve the interoperability and policy enforcement problems of today’s access. Adequate security of information and information systems is a fundamental management responsibility. Abac is a logical access control methodology where authorization to perform a set. Identity and access management is a fundamental and critical cybersecurity capability. “ an access control scheme for big data processing ” provides a general. Access Control Nist.
From www.nist.gov
Next Generation Access Control System and Process for Controlling Access Control Nist Simply put, with its focus on foundational and applied research and standards, nist seeks to. Policy machine and next generation access control. Access control (ac) systems control which users or processes have access to which resources in a system. Adequate security of information and information systems is a fundamental management responsibility. This document provides federal agencies with a definition of. Access Control Nist.
From www.enzoic.com
Surprising Password Guidelines from NIST Enzoic Access Control Nist Simply put, with its focus on foundational and applied research and standards, nist seeks to. Adequate security of information and information systems is a fundamental management responsibility. To solve the interoperability and policy enforcement problems of today’s access. This document provides federal agencies with a definition of attribute based access control (abac). “ an access control scheme for big data. Access Control Nist.