Security Monitoring Dashboard . Use turnkey threat detection rules to start monitoring your environment quickly. Get insights into external file sharing, visibility into spam and malware targeting users within your organization, and metrics to demonstrate your security effectiveness in a single,. Monitor for threats and leverage detailed observability data to accelerate security investigations. Cloud monitoring dashboards can help security teams achieve visibility in complex, sprawling environments. The list includes tools for windows, macos, and linux, with a focus on log management and siem tools that analytics features like threat. Here are three key reasons why dashboards should be regarded as essential: Analyze threats upon log ingestion for full security coverage at intake. Discover the top continuous security monitoring tools designed to protect against cybersecurity threats and breaches.
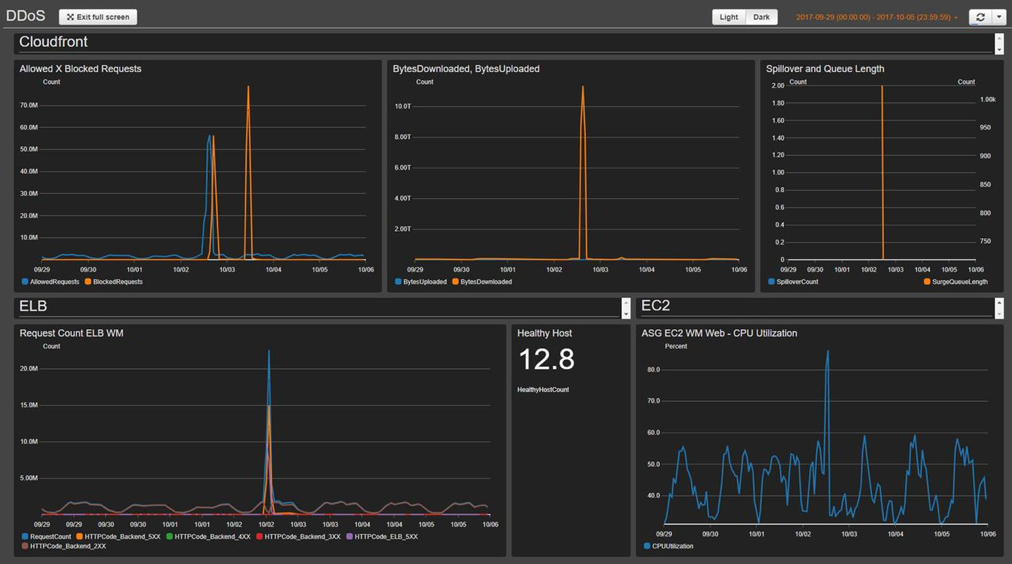
from docs.aws.amazon.com
Monitor for threats and leverage detailed observability data to accelerate security investigations. The list includes tools for windows, macos, and linux, with a focus on log management and siem tools that analytics features like threat. Cloud monitoring dashboards can help security teams achieve visibility in complex, sprawling environments. Get insights into external file sharing, visibility into spam and malware targeting users within your organization, and metrics to demonstrate your security effectiveness in a single,. Discover the top continuous security monitoring tools designed to protect against cybersecurity threats and breaches. Analyze threats upon log ingestion for full security coverage at intake. Use turnkey threat detection rules to start monitoring your environment quickly. Here are three key reasons why dashboards should be regarded as essential:
Build monitoring dashboard Security Automations for AWS WAF
Security Monitoring Dashboard Cloud monitoring dashboards can help security teams achieve visibility in complex, sprawling environments. Here are three key reasons why dashboards should be regarded as essential: Monitor for threats and leverage detailed observability data to accelerate security investigations. Use turnkey threat detection rules to start monitoring your environment quickly. Cloud monitoring dashboards can help security teams achieve visibility in complex, sprawling environments. The list includes tools for windows, macos, and linux, with a focus on log management and siem tools that analytics features like threat. Analyze threats upon log ingestion for full security coverage at intake. Get insights into external file sharing, visibility into spam and malware targeting users within your organization, and metrics to demonstrate your security effectiveness in a single,. Discover the top continuous security monitoring tools designed to protect against cybersecurity threats and breaches.
From www.safebreach.com
Using SafeBreach Flexible Dashboards to Enable Business SafeBreach Security Monitoring Dashboard Here are three key reasons why dashboards should be regarded as essential: Analyze threats upon log ingestion for full security coverage at intake. Get insights into external file sharing, visibility into spam and malware targeting users within your organization, and metrics to demonstrate your security effectiveness in a single,. Use turnkey threat detection rules to start monitoring your environment quickly.. Security Monitoring Dashboard.
From www.elastic.co
Monitoring Airport Security Operations with Canvas & Elasticsearch Security Monitoring Dashboard Discover the top continuous security monitoring tools designed to protect against cybersecurity threats and breaches. Cloud monitoring dashboards can help security teams achieve visibility in complex, sprawling environments. Use turnkey threat detection rules to start monitoring your environment quickly. Get insights into external file sharing, visibility into spam and malware targeting users within your organization, and metrics to demonstrate your. Security Monitoring Dashboard.
From www.real-sec.com
Unified Dashboard for Enhanced Security Visualization REAL security Security Monitoring Dashboard Cloud monitoring dashboards can help security teams achieve visibility in complex, sprawling environments. The list includes tools for windows, macos, and linux, with a focus on log management and siem tools that analytics features like threat. Here are three key reasons why dashboards should be regarded as essential: Discover the top continuous security monitoring tools designed to protect against cybersecurity. Security Monitoring Dashboard.
From www.slideteam.net
Security Monitoring Dashboard With Malicious Requests And Average Security Monitoring Dashboard Here are three key reasons why dashboards should be regarded as essential: Use turnkey threat detection rules to start monitoring your environment quickly. Get insights into external file sharing, visibility into spam and malware targeting users within your organization, and metrics to demonstrate your security effectiveness in a single,. Monitor for threats and leverage detailed observability data to accelerate security. Security Monitoring Dashboard.
From www.slideteam.net
Top 10 Cybersecurity Dashboard Templates With Samples and Examples Security Monitoring Dashboard Analyze threats upon log ingestion for full security coverage at intake. Get insights into external file sharing, visibility into spam and malware targeting users within your organization, and metrics to demonstrate your security effectiveness in a single,. Monitor for threats and leverage detailed observability data to accelerate security investigations. Here are three key reasons why dashboards should be regarded as. Security Monitoring Dashboard.
From www.splunk.com
Security Monitoring Splunk Security Monitoring Dashboard Analyze threats upon log ingestion for full security coverage at intake. Get insights into external file sharing, visibility into spam and malware targeting users within your organization, and metrics to demonstrate your security effectiveness in a single,. Use turnkey threat detection rules to start monitoring your environment quickly. Discover the top continuous security monitoring tools designed to protect against cybersecurity. Security Monitoring Dashboard.
From www.real-sec.com
Unified Dashboard Preview for Enhanced Security Visualization REAL Security Monitoring Dashboard Use turnkey threat detection rules to start monitoring your environment quickly. Discover the top continuous security monitoring tools designed to protect against cybersecurity threats and breaches. Analyze threats upon log ingestion for full security coverage at intake. The list includes tools for windows, macos, and linux, with a focus on log management and siem tools that analytics features like threat.. Security Monitoring Dashboard.
From www.securityinfowatch.com
Immix Dashboard Security Info Watch Security Monitoring Dashboard Discover the top continuous security monitoring tools designed to protect against cybersecurity threats and breaches. The list includes tools for windows, macos, and linux, with a focus on log management and siem tools that analytics features like threat. Analyze threats upon log ingestion for full security coverage at intake. Get insights into external file sharing, visibility into spam and malware. Security Monitoring Dashboard.
From swimlane.com
Security Orchestration, Automation and Response Swimlane Security Monitoring Dashboard Monitor for threats and leverage detailed observability data to accelerate security investigations. Get insights into external file sharing, visibility into spam and malware targeting users within your organization, and metrics to demonstrate your security effectiveness in a single,. Cloud monitoring dashboards can help security teams achieve visibility in complex, sprawling environments. The list includes tools for windows, macos, and linux,. Security Monitoring Dashboard.
From docs.aws.amazon.com
Build monitoring dashboard Security Automations for AWS WAF Security Monitoring Dashboard The list includes tools for windows, macos, and linux, with a focus on log management and siem tools that analytics features like threat. Here are three key reasons why dashboards should be regarded as essential: Get insights into external file sharing, visibility into spam and malware targeting users within your organization, and metrics to demonstrate your security effectiveness in a. Security Monitoring Dashboard.
From www.splunk.com
Security Monitoring AnalyticsDriven Security Splunk Security Monitoring Dashboard The list includes tools for windows, macos, and linux, with a focus on log management and siem tools that analytics features like threat. Cloud monitoring dashboards can help security teams achieve visibility in complex, sprawling environments. Monitor for threats and leverage detailed observability data to accelerate security investigations. Get insights into external file sharing, visibility into spam and malware targeting. Security Monitoring Dashboard.
From secmonthoughts.blogspot.com
Security monitoring thoughts and more Monitoring Cisco Asa logs with ELK Security Monitoring Dashboard The list includes tools for windows, macos, and linux, with a focus on log management and siem tools that analytics features like threat. Use turnkey threat detection rules to start monitoring your environment quickly. Cloud monitoring dashboards can help security teams achieve visibility in complex, sprawling environments. Here are three key reasons why dashboards should be regarded as essential: Analyze. Security Monitoring Dashboard.
From programmer.ink
Real time SSH dashboard for security monitoring Security Monitoring Dashboard Discover the top continuous security monitoring tools designed to protect against cybersecurity threats and breaches. Analyze threats upon log ingestion for full security coverage at intake. Cloud monitoring dashboards can help security teams achieve visibility in complex, sprawling environments. Monitor for threats and leverage detailed observability data to accelerate security investigations. Use turnkey threat detection rules to start monitoring your. Security Monitoring Dashboard.
From grafana.com
Security Monitoring Grafana Labs Security Monitoring Dashboard Monitor for threats and leverage detailed observability data to accelerate security investigations. Analyze threats upon log ingestion for full security coverage at intake. Cloud monitoring dashboards can help security teams achieve visibility in complex, sprawling environments. Here are three key reasons why dashboards should be regarded as essential: Discover the top continuous security monitoring tools designed to protect against cybersecurity. Security Monitoring Dashboard.
From www.slideteam.net
Top 10 Cybersecurity Dashboard Templates With Samples and Examples Security Monitoring Dashboard Use turnkey threat detection rules to start monitoring your environment quickly. Analyze threats upon log ingestion for full security coverage at intake. Here are three key reasons why dashboards should be regarded as essential: Monitor for threats and leverage detailed observability data to accelerate security investigations. Get insights into external file sharing, visibility into spam and malware targeting users within. Security Monitoring Dashboard.
From smartmaritimenetwork.com
Cyber monitoring dashboard launched by Naval Dome Smart Maritime Network Security Monitoring Dashboard Use turnkey threat detection rules to start monitoring your environment quickly. Discover the top continuous security monitoring tools designed to protect against cybersecurity threats and breaches. Here are three key reasons why dashboards should be regarded as essential: Monitor for threats and leverage detailed observability data to accelerate security investigations. Get insights into external file sharing, visibility into spam and. Security Monitoring Dashboard.
From logz.io
What is SIEM? (Security Information and Event Management) Security Monitoring Dashboard The list includes tools for windows, macos, and linux, with a focus on log management and siem tools that analytics features like threat. Analyze threats upon log ingestion for full security coverage at intake. Cloud monitoring dashboards can help security teams achieve visibility in complex, sprawling environments. Get insights into external file sharing, visibility into spam and malware targeting users. Security Monitoring Dashboard.
From blog.aquasec.com
Operationalize Your Cloud Native Security with Aqua’s New Dashboard Security Monitoring Dashboard Cloud monitoring dashboards can help security teams achieve visibility in complex, sprawling environments. Here are three key reasons why dashboards should be regarded as essential: Discover the top continuous security monitoring tools designed to protect against cybersecurity threats and breaches. Get insights into external file sharing, visibility into spam and malware targeting users within your organization, and metrics to demonstrate. Security Monitoring Dashboard.
From www.slideteam.net
Kpi Dashboard For Monitoring Workplace Information Security And Security Monitoring Dashboard Monitor for threats and leverage detailed observability data to accelerate security investigations. Cloud monitoring dashboards can help security teams achieve visibility in complex, sprawling environments. Here are three key reasons why dashboards should be regarded as essential: Discover the top continuous security monitoring tools designed to protect against cybersecurity threats and breaches. Analyze threats upon log ingestion for full security. Security Monitoring Dashboard.
From www.slideteam.net
Progressive Continuous Monitoring Plan Security Monitoring Dashboard Security Monitoring Dashboard Get insights into external file sharing, visibility into spam and malware targeting users within your organization, and metrics to demonstrate your security effectiveness in a single,. Use turnkey threat detection rules to start monitoring your environment quickly. Discover the top continuous security monitoring tools designed to protect against cybersecurity threats and breaches. Analyze threats upon log ingestion for full security. Security Monitoring Dashboard.
From www.slideteam.net
Top 10 Cybersecurity Dashboard Templates With Samples and Examples Security Monitoring Dashboard Discover the top continuous security monitoring tools designed to protect against cybersecurity threats and breaches. Get insights into external file sharing, visibility into spam and malware targeting users within your organization, and metrics to demonstrate your security effectiveness in a single,. Monitor for threats and leverage detailed observability data to accelerate security investigations. Here are three key reasons why dashboards. Security Monitoring Dashboard.
From github.com
GitHub ngc1514/splunksecuritymonitoringdashboard Splunk Dashboard Security Monitoring Dashboard Here are three key reasons why dashboards should be regarded as essential: Cloud monitoring dashboards can help security teams achieve visibility in complex, sprawling environments. Use turnkey threat detection rules to start monitoring your environment quickly. Analyze threats upon log ingestion for full security coverage at intake. Discover the top continuous security monitoring tools designed to protect against cybersecurity threats. Security Monitoring Dashboard.
From www.slideteam.net
Dashboard For Cyber Security Real Time Monitoring Presentation Security Monitoring Dashboard Cloud monitoring dashboards can help security teams achieve visibility in complex, sprawling environments. Monitor for threats and leverage detailed observability data to accelerate security investigations. Here are three key reasons why dashboards should be regarded as essential: Analyze threats upon log ingestion for full security coverage at intake. Use turnkey threat detection rules to start monitoring your environment quickly. Get. Security Monitoring Dashboard.
From www.n-able.com
Top Computer Security & Network Vulnerabilities Nable Security Monitoring Dashboard Get insights into external file sharing, visibility into spam and malware targeting users within your organization, and metrics to demonstrate your security effectiveness in a single,. Use turnkey threat detection rules to start monitoring your environment quickly. The list includes tools for windows, macos, and linux, with a focus on log management and siem tools that analytics features like threat.. Security Monitoring Dashboard.
From bluedog-security.com
Azure Monitoring Bluedog Security Security Monitoring Dashboard Cloud monitoring dashboards can help security teams achieve visibility in complex, sprawling environments. The list includes tools for windows, macos, and linux, with a focus on log management and siem tools that analytics features like threat. Use turnkey threat detection rules to start monitoring your environment quickly. Analyze threats upon log ingestion for full security coverage at intake. Discover the. Security Monitoring Dashboard.
From www.networkmanagementsoftware.com
SolarWinds Security Event Manager Review Best SIEM Tool of 2024! Security Monitoring Dashboard Cloud monitoring dashboards can help security teams achieve visibility in complex, sprawling environments. The list includes tools for windows, macos, and linux, with a focus on log management and siem tools that analytics features like threat. Use turnkey threat detection rules to start monitoring your environment quickly. Get insights into external file sharing, visibility into spam and malware targeting users. Security Monitoring Dashboard.
From www.slideteam.net
Security Information And Event Management Dashboard Siem For Security Security Monitoring Dashboard Cloud monitoring dashboards can help security teams achieve visibility in complex, sprawling environments. Use turnkey threat detection rules to start monitoring your environment quickly. Monitor for threats and leverage detailed observability data to accelerate security investigations. Here are three key reasons why dashboards should be regarded as essential: Get insights into external file sharing, visibility into spam and malware targeting. Security Monitoring Dashboard.
From dribbble.com
Smart City Security Monitoring Dashboard Concept by Pavel Shulyatikov Security Monitoring Dashboard Cloud monitoring dashboards can help security teams achieve visibility in complex, sprawling environments. Monitor for threats and leverage detailed observability data to accelerate security investigations. Analyze threats upon log ingestion for full security coverage at intake. Get insights into external file sharing, visibility into spam and malware targeting users within your organization, and metrics to demonstrate your security effectiveness in. Security Monitoring Dashboard.
From blog.aquasec.com
Operationalize Your Cloud Native Security with Aqua’s New Dashboard Security Monitoring Dashboard Monitor for threats and leverage detailed observability data to accelerate security investigations. Cloud monitoring dashboards can help security teams achieve visibility in complex, sprawling environments. Get insights into external file sharing, visibility into spam and malware targeting users within your organization, and metrics to demonstrate your security effectiveness in a single,. Here are three key reasons why dashboards should be. Security Monitoring Dashboard.
From www.slideteam.net
Top 10 Cybersecurity Dashboard Templates With Samples and Examples Security Monitoring Dashboard Use turnkey threat detection rules to start monitoring your environment quickly. The list includes tools for windows, macos, and linux, with a focus on log management and siem tools that analytics features like threat. Here are three key reasons why dashboards should be regarded as essential: Analyze threats upon log ingestion for full security coverage at intake. Cloud monitoring dashboards. Security Monitoring Dashboard.
From docs.42crunch.com
API monitoring Security Monitoring Dashboard Monitor for threats and leverage detailed observability data to accelerate security investigations. Analyze threats upon log ingestion for full security coverage at intake. Here are three key reasons why dashboards should be regarded as essential: Get insights into external file sharing, visibility into spam and malware targeting users within your organization, and metrics to demonstrate your security effectiveness in a. Security Monitoring Dashboard.
From hacklido.com
Security Information and Event Management (SIEM) ArcSight HACKLIDO Security Monitoring Dashboard Analyze threats upon log ingestion for full security coverage at intake. Here are three key reasons why dashboards should be regarded as essential: Use turnkey threat detection rules to start monitoring your environment quickly. Discover the top continuous security monitoring tools designed to protect against cybersecurity threats and breaches. Get insights into external file sharing, visibility into spam and malware. Security Monitoring Dashboard.
From www.processunity.com
Cybersecurity Program Management ProcessUnity Security Monitoring Dashboard Cloud monitoring dashboards can help security teams achieve visibility in complex, sprawling environments. Discover the top continuous security monitoring tools designed to protect against cybersecurity threats and breaches. Monitor for threats and leverage detailed observability data to accelerate security investigations. Here are three key reasons why dashboards should be regarded as essential: The list includes tools for windows, macos, and. Security Monitoring Dashboard.
From www.alertlogic.com
Managed Detection and Response (MDR) Solutions & Services Alert Logic Security Monitoring Dashboard Use turnkey threat detection rules to start monitoring your environment quickly. Cloud monitoring dashboards can help security teams achieve visibility in complex, sprawling environments. The list includes tools for windows, macos, and linux, with a focus on log management and siem tools that analytics features like threat. Discover the top continuous security monitoring tools designed to protect against cybersecurity threats. Security Monitoring Dashboard.
From help.deepsecurity.trendmicro.com
Customize the dashboard Deep Security Security Monitoring Dashboard The list includes tools for windows, macos, and linux, with a focus on log management and siem tools that analytics features like threat. Get insights into external file sharing, visibility into spam and malware targeting users within your organization, and metrics to demonstrate your security effectiveness in a single,. Cloud monitoring dashboards can help security teams achieve visibility in complex,. Security Monitoring Dashboard.