Wireless Access Point Hardening . Wireless network capacity planning and requirements. An overview of wireless wan. While there are many different steps that can be taken to secure a wireless network, these 12 best practices are essential for ensuring that your data and devices are safe from malicious actors. Enlist employees in safeguarding the network. Defend the organization from external threats. The security of each wlan is heavily dependent on how well each wlan component—including client devices, access. Secure the wired (ethernet) network against wireless threats. This paper discusses best practices in all five areas to. Ideally, we secure our wireless networks to keep off disgusting freeloaders who use up our bandwidth and slow down internet speeds, all for free. This blog focuses on best practices for securing the wireless access point to which all wireless devices connect in the enterprise environment.
from fixthephoto.com
An overview of wireless wan. Wireless network capacity planning and requirements. While there are many different steps that can be taken to secure a wireless network, these 12 best practices are essential for ensuring that your data and devices are safe from malicious actors. This paper discusses best practices in all five areas to. Secure the wired (ethernet) network against wireless threats. Enlist employees in safeguarding the network. The security of each wlan is heavily dependent on how well each wlan component—including client devices, access. Defend the organization from external threats. Ideally, we secure our wireless networks to keep off disgusting freeloaders who use up our bandwidth and slow down internet speeds, all for free. This blog focuses on best practices for securing the wireless access point to which all wireless devices connect in the enterprise environment.
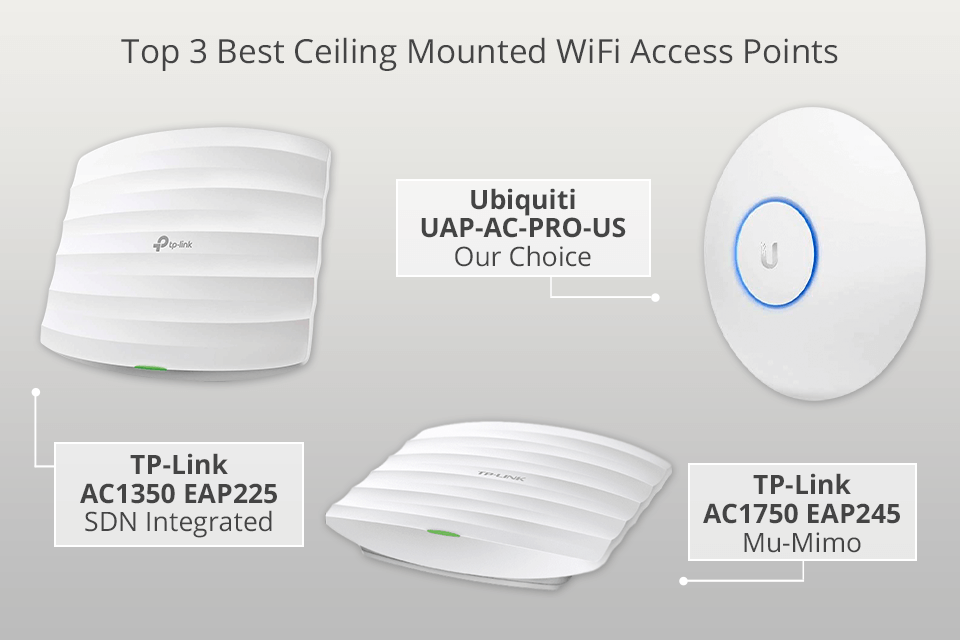
13 Best Ceiling Mounted WiFi Access Points in 2024
Wireless Access Point Hardening Enlist employees in safeguarding the network. Defend the organization from external threats. Secure the wired (ethernet) network against wireless threats. This paper discusses best practices in all five areas to. Wireless network capacity planning and requirements. An overview of wireless wan. While there are many different steps that can be taken to secure a wireless network, these 12 best practices are essential for ensuring that your data and devices are safe from malicious actors. Ideally, we secure our wireless networks to keep off disgusting freeloaders who use up our bandwidth and slow down internet speeds, all for free. Enlist employees in safeguarding the network. The security of each wlan is heavily dependent on how well each wlan component—including client devices, access. This blog focuses on best practices for securing the wireless access point to which all wireless devices connect in the enterprise environment.
From www.engeniustech.com
Wireless Access Point EWS377FIT WiFi 6 4x4 Indoor EnGenius Wireless Access Point Hardening The security of each wlan is heavily dependent on how well each wlan component—including client devices, access. This paper discusses best practices in all five areas to. This blog focuses on best practices for securing the wireless access point to which all wireless devices connect in the enterprise environment. Ideally, we secure our wireless networks to keep off disgusting freeloaders. Wireless Access Point Hardening.
From www.studocu.com
8.3.5 Hardening a Wireless Access Point Hardening a Wireless Access Wireless Access Point Hardening The security of each wlan is heavily dependent on how well each wlan component—including client devices, access. An overview of wireless wan. This paper discusses best practices in all five areas to. This blog focuses on best practices for securing the wireless access point to which all wireless devices connect in the enterprise environment. Enlist employees in safeguarding the network.. Wireless Access Point Hardening.
From www.engeniustech.com
Outdoor Wireless Access Point EWS850FIT EnGenius Wireless Access Point Hardening Enlist employees in safeguarding the network. The security of each wlan is heavily dependent on how well each wlan component—including client devices, access. Ideally, we secure our wireless networks to keep off disgusting freeloaders who use up our bandwidth and slow down internet speeds, all for free. Secure the wired (ethernet) network against wireless threats. This paper discusses best practices. Wireless Access Point Hardening.
From dongknows.com
Best 6 WiFi Access Points and Buying Tips Dong Knows Tech Wireless Access Point Hardening An overview of wireless wan. Enlist employees in safeguarding the network. The security of each wlan is heavily dependent on how well each wlan component—including client devices, access. Ideally, we secure our wireless networks to keep off disgusting freeloaders who use up our bandwidth and slow down internet speeds, all for free. Defend the organization from external threats. This blog. Wireless Access Point Hardening.
From blog.securitymetrics.com
Wireless Access Point Protection Finding Rogue WiFi Networks Wireless Access Point Hardening Defend the organization from external threats. An overview of wireless wan. Secure the wired (ethernet) network against wireless threats. Ideally, we secure our wireless networks to keep off disgusting freeloaders who use up our bandwidth and slow down internet speeds, all for free. This blog focuses on best practices for securing the wireless access point to which all wireless devices. Wireless Access Point Hardening.
From www.voipon.co.uk
Grandstream GWN7624 InWall WiFi Access Point Wireless Access Point Hardening This paper discusses best practices in all five areas to. Defend the organization from external threats. An overview of wireless wan. Wireless network capacity planning and requirements. Ideally, we secure our wireless networks to keep off disgusting freeloaders who use up our bandwidth and slow down internet speeds, all for free. Secure the wired (ethernet) network against wireless threats. The. Wireless Access Point Hardening.
From www.mobielverbinden.nl
Pepwave AP One Rugged Dualband AC WiFi Access point Wireless Access Point Hardening Ideally, we secure our wireless networks to keep off disgusting freeloaders who use up our bandwidth and slow down internet speeds, all for free. While there are many different steps that can be taken to secure a wireless network, these 12 best practices are essential for ensuring that your data and devices are safe from malicious actors. The security of. Wireless Access Point Hardening.
From www.networkingsignal.com
What Are Wireless Access Points Waps? Detail Explained Wireless Access Point Hardening This paper discusses best practices in all five areas to. Defend the organization from external threats. While there are many different steps that can be taken to secure a wireless network, these 12 best practices are essential for ensuring that your data and devices are safe from malicious actors. Enlist employees in safeguarding the network. Wireless network capacity planning and. Wireless Access Point Hardening.
From fixthephoto.com
13 Best Ceiling Mounted WiFi Access Points in 2024 Wireless Access Point Hardening Wireless network capacity planning and requirements. The security of each wlan is heavily dependent on how well each wlan component—including client devices, access. Ideally, we secure our wireless networks to keep off disgusting freeloaders who use up our bandwidth and slow down internet speeds, all for free. An overview of wireless wan. Enlist employees in safeguarding the network. This blog. Wireless Access Point Hardening.
From device.report
tplink EAP690E HD Wireless Access Point Installation Guide Wireless Access Point Hardening Ideally, we secure our wireless networks to keep off disgusting freeloaders who use up our bandwidth and slow down internet speeds, all for free. Secure the wired (ethernet) network against wireless threats. While there are many different steps that can be taken to secure a wireless network, these 12 best practices are essential for ensuring that your data and devices. Wireless Access Point Hardening.
From www.fastcabling.com
StepbyStep Installation Guide for Wireless Access Points in SMBs Wireless Access Point Hardening Ideally, we secure our wireless networks to keep off disgusting freeloaders who use up our bandwidth and slow down internet speeds, all for free. Secure the wired (ethernet) network against wireless threats. Wireless network capacity planning and requirements. This paper discusses best practices in all five areas to. The security of each wlan is heavily dependent on how well each. Wireless Access Point Hardening.
From ezelink.com
EZELINK Introduces AX2800 WiFi 6 Outdoor Access Point EZELINK Wireless Access Point Hardening This paper discusses best practices in all five areas to. Ideally, we secure our wireless networks to keep off disgusting freeloaders who use up our bandwidth and slow down internet speeds, all for free. An overview of wireless wan. While there are many different steps that can be taken to secure a wireless network, these 12 best practices are essential. Wireless Access Point Hardening.
From www.impulse-embedded.co.uk
EKI6333AC2GD Industrial Wireless Access Point · Impulse Embedded Limited Wireless Access Point Hardening This blog focuses on best practices for securing the wireless access point to which all wireless devices connect in the enterprise environment. While there are many different steps that can be taken to secure a wireless network, these 12 best practices are essential for ensuring that your data and devices are safe from malicious actors. Enlist employees in safeguarding the. Wireless Access Point Hardening.
From study-ccna.com
Wireless Access Point Operation Explained Study CCNA Wireless Access Point Hardening Wireless network capacity planning and requirements. Enlist employees in safeguarding the network. Secure the wired (ethernet) network against wireless threats. While there are many different steps that can be taken to secure a wireless network, these 12 best practices are essential for ensuring that your data and devices are safe from malicious actors. This paper discusses best practices in all. Wireless Access Point Hardening.
From abrilkruwhurley.blogspot.com
Describe Techniques Used to Harden a Wireless Access Point Wireless Access Point Hardening An overview of wireless wan. Secure the wired (ethernet) network against wireless threats. Defend the organization from external threats. Wireless network capacity planning and requirements. Ideally, we secure our wireless networks to keep off disgusting freeloaders who use up our bandwidth and slow down internet speeds, all for free. The security of each wlan is heavily dependent on how well. Wireless Access Point Hardening.
From www.impulse-embedded.co.uk
EKI6333AC2GD Industrial Wireless Access Point · Impulse Embedded Limited Wireless Access Point Hardening This blog focuses on best practices for securing the wireless access point to which all wireless devices connect in the enterprise environment. Ideally, we secure our wireless networks to keep off disgusting freeloaders who use up our bandwidth and slow down internet speeds, all for free. Secure the wired (ethernet) network against wireless threats. An overview of wireless wan. Enlist. Wireless Access Point Hardening.
From www.fastcabling.com
Effective Ways to Install Outdoor Access Points for Best WiFi Wireless Access Point Hardening Wireless network capacity planning and requirements. This blog focuses on best practices for securing the wireless access point to which all wireless devices connect in the enterprise environment. Enlist employees in safeguarding the network. Ideally, we secure our wireless networks to keep off disgusting freeloaders who use up our bandwidth and slow down internet speeds, all for free. This paper. Wireless Access Point Hardening.
From www.fastcabling.com
StepbyStep Installation Guide for Wireless Access Points in SMBs Wireless Access Point Hardening While there are many different steps that can be taken to secure a wireless network, these 12 best practices are essential for ensuring that your data and devices are safe from malicious actors. Wireless network capacity planning and requirements. This blog focuses on best practices for securing the wireless access point to which all wireless devices connect in the enterprise. Wireless Access Point Hardening.
From www.youtube.com
Installing Outdoor Wireless Access Points YouTube Wireless Access Point Hardening The security of each wlan is heavily dependent on how well each wlan component—including client devices, access. Defend the organization from external threats. Ideally, we secure our wireless networks to keep off disgusting freeloaders who use up our bandwidth and slow down internet speeds, all for free. While there are many different steps that can be taken to secure a. Wireless Access Point Hardening.
From www.residentialsystems.com
Snap One Launches WiFi 6 Wireless Access Points from Araknis and Wireless Access Point Hardening Defend the organization from external threats. While there are many different steps that can be taken to secure a wireless network, these 12 best practices are essential for ensuring that your data and devices are safe from malicious actors. Secure the wired (ethernet) network against wireless threats. Wireless network capacity planning and requirements. Enlist employees in safeguarding the network. This. Wireless Access Point Hardening.
From gogyluw.initiativeblog.com
Hooking Up Multiple Wireless Access Points Wireless Access Point Hardening Secure the wired (ethernet) network against wireless threats. Wireless network capacity planning and requirements. An overview of wireless wan. The security of each wlan is heavily dependent on how well each wlan component—including client devices, access. Enlist employees in safeguarding the network. Ideally, we secure our wireless networks to keep off disgusting freeloaders who use up our bandwidth and slow. Wireless Access Point Hardening.
From central.toasttab.com
PoE's Explained Wireless Access Point Hardening This paper discusses best practices in all five areas to. Defend the organization from external threats. Enlist employees in safeguarding the network. The security of each wlan is heavily dependent on how well each wlan component—including client devices, access. Secure the wired (ethernet) network against wireless threats. This blog focuses on best practices for securing the wireless access point to. Wireless Access Point Hardening.
From dxohinwej.blob.core.windows.net
How To Access Wireless Access Point at Jeanne Buckle blog Wireless Access Point Hardening Defend the organization from external threats. Wireless network capacity planning and requirements. This blog focuses on best practices for securing the wireless access point to which all wireless devices connect in the enterprise environment. Enlist employees in safeguarding the network. An overview of wireless wan. The security of each wlan is heavily dependent on how well each wlan component—including client. Wireless Access Point Hardening.
From www.youtube.com
WIRELESS ACCESS POINTS INSTALLATION BASICS HOME NETWORKING 101 YouTube Wireless Access Point Hardening This blog focuses on best practices for securing the wireless access point to which all wireless devices connect in the enterprise environment. Defend the organization from external threats. The security of each wlan is heavily dependent on how well each wlan component—including client devices, access. Wireless network capacity planning and requirements. Enlist employees in safeguarding the network. Secure the wired. Wireless Access Point Hardening.
From www.bhphotovideo.com
TPLink TLWA3001 AX3000 Wireless DualBand Gigabit TLWA3001 Wireless Access Point Hardening Wireless network capacity planning and requirements. Ideally, we secure our wireless networks to keep off disgusting freeloaders who use up our bandwidth and slow down internet speeds, all for free. Secure the wired (ethernet) network against wireless threats. While there are many different steps that can be taken to secure a wireless network, these 12 best practices are essential for. Wireless Access Point Hardening.
From www.arista.com
Wireless Intrusion Prevention System (WIPS) Arista Wireless Access Point Hardening This paper discusses best practices in all five areas to. While there are many different steps that can be taken to secure a wireless network, these 12 best practices are essential for ensuring that your data and devices are safe from malicious actors. An overview of wireless wan. Wireless network capacity planning and requirements. Ideally, we secure our wireless networks. Wireless Access Point Hardening.
From www.fastcabling.com
StepbyStep Installation Guide for Wireless Access Points in SMBs Wireless Access Point Hardening While there are many different steps that can be taken to secure a wireless network, these 12 best practices are essential for ensuring that your data and devices are safe from malicious actors. This blog focuses on best practices for securing the wireless access point to which all wireless devices connect in the enterprise environment. Ideally, we secure our wireless. Wireless Access Point Hardening.
From www.slideserve.com
PPT ITIS 3110 Network Hardening PowerPoint Presentation, free Wireless Access Point Hardening While there are many different steps that can be taken to secure a wireless network, these 12 best practices are essential for ensuring that your data and devices are safe from malicious actors. Wireless network capacity planning and requirements. Ideally, we secure our wireless networks to keep off disgusting freeloaders who use up our bandwidth and slow down internet speeds,. Wireless Access Point Hardening.
From www.fastcabling.com
StepbyStep Installation Guide for Wireless Access Points in SMBs Wireless Access Point Hardening Enlist employees in safeguarding the network. Wireless network capacity planning and requirements. An overview of wireless wan. This blog focuses on best practices for securing the wireless access point to which all wireless devices connect in the enterprise environment. While there are many different steps that can be taken to secure a wireless network, these 12 best practices are essential. Wireless Access Point Hardening.
From www.fasystem.se
IAP2400AX Industrial 5GHz 802.11ax 2400Mbps Wireless Access Point Wireless Access Point Hardening Wireless network capacity planning and requirements. This blog focuses on best practices for securing the wireless access point to which all wireless devices connect in the enterprise environment. An overview of wireless wan. The security of each wlan is heavily dependent on how well each wlan component—including client devices, access. Enlist employees in safeguarding the network. Secure the wired (ethernet). Wireless Access Point Hardening.
From linuxsecurityblog.com
Router Hardening Checklist ls /blog Wireless Access Point Hardening The security of each wlan is heavily dependent on how well each wlan component—including client devices, access. While there are many different steps that can be taken to secure a wireless network, these 12 best practices are essential for ensuring that your data and devices are safe from malicious actors. Secure the wired (ethernet) network against wireless threats. Ideally, we. Wireless Access Point Hardening.
From www.impulse-embedded.co.uk
EKI6333AC2GD Industrial Wireless Access Point · Impulse Embedded Limited Wireless Access Point Hardening This blog focuses on best practices for securing the wireless access point to which all wireless devices connect in the enterprise environment. The security of each wlan is heavily dependent on how well each wlan component—including client devices, access. Enlist employees in safeguarding the network. Defend the organization from external threats. This paper discusses best practices in all five areas. Wireless Access Point Hardening.
From www.fastcabling.com
StepbyStep Installation Guide for Wireless Access Points in SMBs Wireless Access Point Hardening This blog focuses on best practices for securing the wireless access point to which all wireless devices connect in the enterprise environment. This paper discusses best practices in all five areas to. Enlist employees in safeguarding the network. An overview of wireless wan. Ideally, we secure our wireless networks to keep off disgusting freeloaders who use up our bandwidth and. Wireless Access Point Hardening.
From www.expertnetworkconsultant.com
How to Connect a Wireless Access Point to a Wired Network Expert Wireless Access Point Hardening This paper discusses best practices in all five areas to. This blog focuses on best practices for securing the wireless access point to which all wireless devices connect in the enterprise environment. Ideally, we secure our wireless networks to keep off disgusting freeloaders who use up our bandwidth and slow down internet speeds, all for free. Enlist employees in safeguarding. Wireless Access Point Hardening.
From diagramlibvina37960rc.z13.web.core.windows.net
How To Setup A Wifi Access Point Wireless Access Point Hardening While there are many different steps that can be taken to secure a wireless network, these 12 best practices are essential for ensuring that your data and devices are safe from malicious actors. Defend the organization from external threats. An overview of wireless wan. The security of each wlan is heavily dependent on how well each wlan component—including client devices,. Wireless Access Point Hardening.