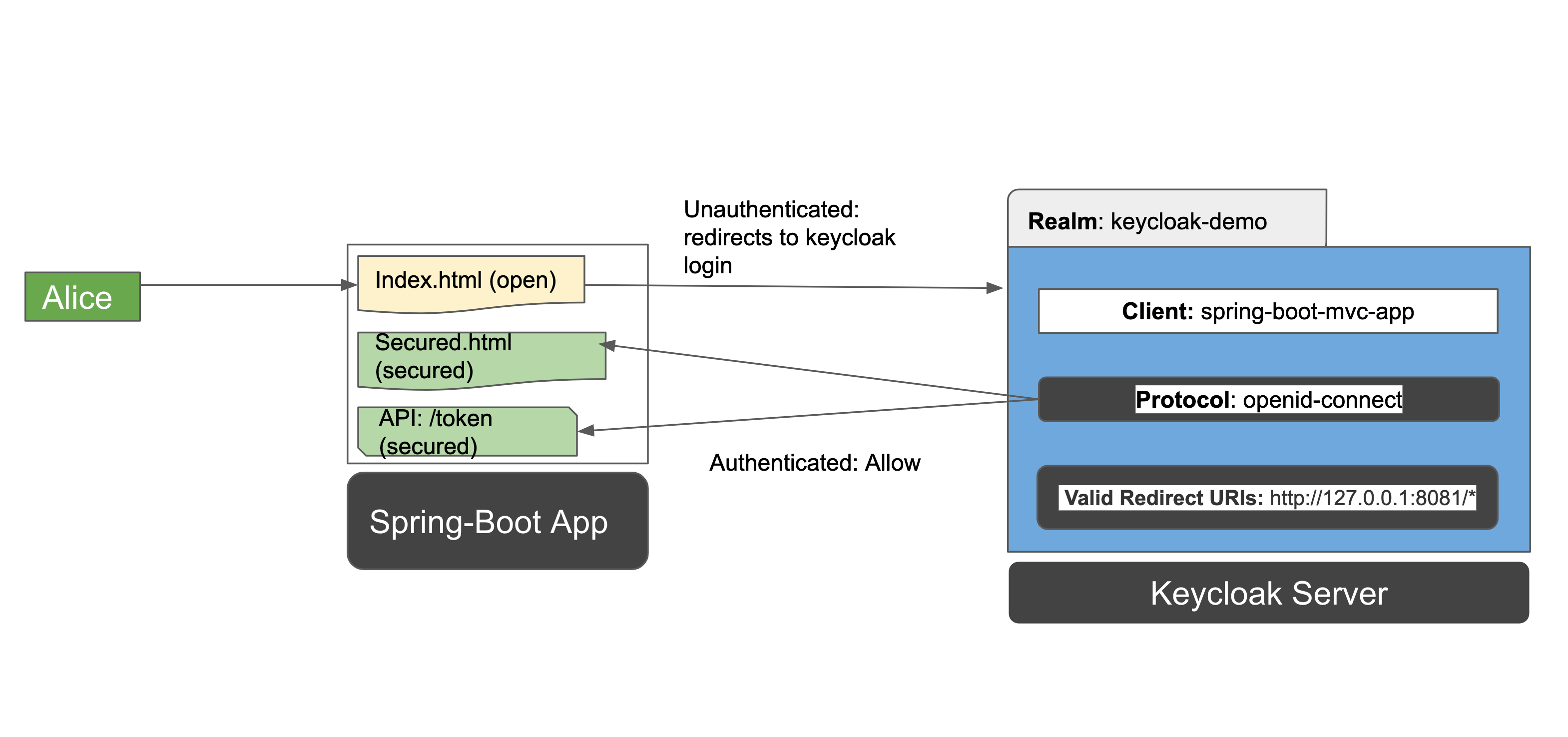
Keycloak Authentication Spring Boot . In this article, i will discuss how to implement keycloak with spring boot to secure user access to endpoints using tokens. Learn how to create a java application on top of spring boot 3 and protect it by using spring security and keycloak—without having to rely on keycloak adapters. However, with the deprecation of websecurityconfigureradapter and the migration of spring. This spring security tutorial will explore how to use keycloak and spring security oauth2 module to implement authentication and authorization in a spring boot. Learn how to authenticate a spring boot app. In today’s landscape of developing secure applications, implementing a robust authentication solution is an essential foundation. This article will explore setting up robust. Keycloak makes it easy to work with many applications, not just spring boot projects. Overview of keycloak's main concepts. We saw in this article how to deploy and configure a keycloak server and then secure a spring boot app, first by using java ee security constraints and then by. Detailed guide on how to set up a keycloak server using a docker image.
from medium.com
Detailed guide on how to set up a keycloak server using a docker image. In today’s landscape of developing secure applications, implementing a robust authentication solution is an essential foundation. This spring security tutorial will explore how to use keycloak and spring security oauth2 module to implement authentication and authorization in a spring boot. Overview of keycloak's main concepts. Learn how to authenticate a spring boot app. This article will explore setting up robust. Learn how to create a java application on top of spring boot 3 and protect it by using spring security and keycloak—without having to rely on keycloak adapters. In this article, i will discuss how to implement keycloak with spring boot to secure user access to endpoints using tokens. We saw in this article how to deploy and configure a keycloak server and then secure a spring boot app, first by using java ee security constraints and then by. However, with the deprecation of websecurityconfigureradapter and the migration of spring.
Secure springboot 2 using Keycloak by Abhishek koserwal Keycloak
Keycloak Authentication Spring Boot We saw in this article how to deploy and configure a keycloak server and then secure a spring boot app, first by using java ee security constraints and then by. Learn how to create a java application on top of spring boot 3 and protect it by using spring security and keycloak—without having to rely on keycloak adapters. Overview of keycloak's main concepts. This article will explore setting up robust. We saw in this article how to deploy and configure a keycloak server and then secure a spring boot app, first by using java ee security constraints and then by. Detailed guide on how to set up a keycloak server using a docker image. Learn how to authenticate a spring boot app. In this article, i will discuss how to implement keycloak with spring boot to secure user access to endpoints using tokens. Keycloak makes it easy to work with many applications, not just spring boot projects. This spring security tutorial will explore how to use keycloak and spring security oauth2 module to implement authentication and authorization in a spring boot. However, with the deprecation of websecurityconfigureradapter and the migration of spring. In today’s landscape of developing secure applications, implementing a robust authentication solution is an essential foundation.
From betterprogramming.pub
How to Authenticate a Spring Boot App With Keycloak Better Programming Keycloak Authentication Spring Boot We saw in this article how to deploy and configure a keycloak server and then secure a spring boot app, first by using java ee security constraints and then by. This article will explore setting up robust. Overview of keycloak's main concepts. Learn how to create a java application on top of spring boot 3 and protect it by using. Keycloak Authentication Spring Boot.
From morioh.com
How To Authenticate Your Spring Boot Application With Keycloak Keycloak Authentication Spring Boot This spring security tutorial will explore how to use keycloak and spring security oauth2 module to implement authentication and authorization in a spring boot. This article will explore setting up robust. We saw in this article how to deploy and configure a keycloak server and then secure a spring boot app, first by using java ee security constraints and then. Keycloak Authentication Spring Boot.
From www.springcloud.io
Protecting Your Spring Boot Applications with the Keycloak Keycloak Authentication Spring Boot Detailed guide on how to set up a keycloak server using a docker image. In this article, i will discuss how to implement keycloak with spring boot to secure user access to endpoints using tokens. We saw in this article how to deploy and configure a keycloak server and then secure a spring boot app, first by using java ee. Keycloak Authentication Spring Boot.
From www.mdpi.com
Sensors Free FullText Applying Spring Security Framework with Keycloak Authentication Spring Boot Learn how to authenticate a spring boot app. Detailed guide on how to set up a keycloak server using a docker image. Learn how to create a java application on top of spring boot 3 and protect it by using spring security and keycloak—without having to rely on keycloak adapters. In this article, i will discuss how to implement keycloak. Keycloak Authentication Spring Boot.
From medium.com
Securing Spring Boot Application with Keycloak Access Token, Login Keycloak Authentication Spring Boot In this article, i will discuss how to implement keycloak with spring boot to secure user access to endpoints using tokens. However, with the deprecation of websecurityconfigureradapter and the migration of spring. This spring security tutorial will explore how to use keycloak and spring security oauth2 module to implement authentication and authorization in a spring boot. This article will explore. Keycloak Authentication Spring Boot.
From www.youtube.com
Part 5 Create Spring boot client in Keycloak authentication server Keycloak Authentication Spring Boot Detailed guide on how to set up a keycloak server using a docker image. In this article, i will discuss how to implement keycloak with spring boot to secure user access to endpoints using tokens. Learn how to create a java application on top of spring boot 3 and protect it by using spring security and keycloak—without having to rely. Keycloak Authentication Spring Boot.
From howtodoinjava.com
OAuth2 Login with Keycloak and Spring Boot Security 3 Keycloak Authentication Spring Boot Overview of keycloak's main concepts. In this article, i will discuss how to implement keycloak with spring boot to secure user access to endpoints using tokens. Keycloak makes it easy to work with many applications, not just spring boot projects. In today’s landscape of developing secure applications, implementing a robust authentication solution is an essential foundation. Detailed guide on how. Keycloak Authentication Spring Boot.
From docs.spring.io
Spring Security Reference Keycloak Authentication Spring Boot Detailed guide on how to set up a keycloak server using a docker image. In today’s landscape of developing secure applications, implementing a robust authentication solution is an essential foundation. This article will explore setting up robust. In this article, i will discuss how to implement keycloak with spring boot to secure user access to endpoints using tokens. Overview of. Keycloak Authentication Spring Boot.
From stackoverflow.com
java Spring boot user authenticate with keycloak (microservices Keycloak Authentication Spring Boot This spring security tutorial will explore how to use keycloak and spring security oauth2 module to implement authentication and authorization in a spring boot. This article will explore setting up robust. Keycloak makes it easy to work with many applications, not just spring boot projects. In today’s landscape of developing secure applications, implementing a robust authentication solution is an essential. Keycloak Authentication Spring Boot.
From betterprogramming.pub
How to Authenticate a Spring Boot App With Keycloak Better Programming Keycloak Authentication Spring Boot Learn how to authenticate a spring boot app. Keycloak makes it easy to work with many applications, not just spring boot projects. In this article, i will discuss how to implement keycloak with spring boot to secure user access to endpoints using tokens. In today’s landscape of developing secure applications, implementing a robust authentication solution is an essential foundation. We. Keycloak Authentication Spring Boot.
From github.com
GitHub mamadaliev/springbootreactkeycloak Demonstration of Keycloak Authentication Spring Boot Learn how to authenticate a spring boot app. In this article, i will discuss how to implement keycloak with spring boot to secure user access to endpoints using tokens. Keycloak makes it easy to work with many applications, not just spring boot projects. Learn how to create a java application on top of spring boot 3 and protect it by. Keycloak Authentication Spring Boot.
From www.bezkoder.com
Spring Boot + React JWT Authentication with Spring Security BezKoder Keycloak Authentication Spring Boot Learn how to authenticate a spring boot app. Overview of keycloak's main concepts. This article will explore setting up robust. Learn how to create a java application on top of spring boot 3 and protect it by using spring security and keycloak—without having to rely on keycloak adapters. Detailed guide on how to set up a keycloak server using a. Keycloak Authentication Spring Boot.
From gauthier-cassany.com
Implement Rolebased authorization in Spring Boot with Keycloak Keycloak Authentication Spring Boot We saw in this article how to deploy and configure a keycloak server and then secure a spring boot app, first by using java ee security constraints and then by. This article will explore setting up robust. This spring security tutorial will explore how to use keycloak and spring security oauth2 module to implement authentication and authorization in a spring. Keycloak Authentication Spring Boot.
From medium.com
Secure springboot 2 using Keycloak by Abhishek koserwal Keycloak Keycloak Authentication Spring Boot In this article, i will discuss how to implement keycloak with spring boot to secure user access to endpoints using tokens. In today’s landscape of developing secure applications, implementing a robust authentication solution is an essential foundation. This article will explore setting up robust. Learn how to create a java application on top of spring boot 3 and protect it. Keycloak Authentication Spring Boot.
From enfuse.io
Method Level Authorization with Spring Boot and Keycloak » D3 Do it Keycloak Authentication Spring Boot In today’s landscape of developing secure applications, implementing a robust authentication solution is an essential foundation. This article will explore setting up robust. However, with the deprecation of websecurityconfigureradapter and the migration of spring. This spring security tutorial will explore how to use keycloak and spring security oauth2 module to implement authentication and authorization in a spring boot. In this. Keycloak Authentication Spring Boot.
From awesomeopensource.com
Springboot Kong Keycloak Keycloak Authentication Spring Boot However, with the deprecation of websecurityconfigureradapter and the migration of spring. This spring security tutorial will explore how to use keycloak and spring security oauth2 module to implement authentication and authorization in a spring boot. In today’s landscape of developing secure applications, implementing a robust authentication solution is an essential foundation. This article will explore setting up robust. Learn how. Keycloak Authentication Spring Boot.
From github.com
GitHub shinyay/springkeycloakauthzserver Embedded Keycloak Server Keycloak Authentication Spring Boot Learn how to authenticate a spring boot app. This spring security tutorial will explore how to use keycloak and spring security oauth2 module to implement authentication and authorization in a spring boot. We saw in this article how to deploy and configure a keycloak server and then secure a spring boot app, first by using java ee security constraints and. Keycloak Authentication Spring Boot.
From walkingtree.tech
Securing FullStack Applications with React, Spring Boot, and Keycloak Authentication Spring Boot Overview of keycloak's main concepts. In today’s landscape of developing secure applications, implementing a robust authentication solution is an essential foundation. Learn how to authenticate a spring boot app. Keycloak makes it easy to work with many applications, not just spring boot projects. However, with the deprecation of websecurityconfigureradapter and the migration of spring. We saw in this article how. Keycloak Authentication Spring Boot.
From www.baeldung.com
A Quick Guide to Using Keycloak with Spring Boot Baeldung Keycloak Authentication Spring Boot Learn how to authenticate a spring boot app. This article will explore setting up robust. In this article, i will discuss how to implement keycloak with spring boot to secure user access to endpoints using tokens. However, with the deprecation of websecurityconfigureradapter and the migration of spring. Keycloak makes it easy to work with many applications, not just spring boot. Keycloak Authentication Spring Boot.
From github.com
GitHub HQTTeam/bffspringkeycloakreactdemo Demo BFF Architecture Keycloak Authentication Spring Boot Detailed guide on how to set up a keycloak server using a docker image. We saw in this article how to deploy and configure a keycloak server and then secure a spring boot app, first by using java ee security constraints and then by. Learn how to create a java application on top of spring boot 3 and protect it. Keycloak Authentication Spring Boot.
From github.com
GitHub mamadaliev/springbootreactkeycloak Demonstration of Keycloak Authentication Spring Boot We saw in this article how to deploy and configure a keycloak server and then secure a spring boot app, first by using java ee security constraints and then by. Overview of keycloak's main concepts. Keycloak makes it easy to work with many applications, not just spring boot projects. In this article, i will discuss how to implement keycloak with. Keycloak Authentication Spring Boot.
From stackoverflow.com
java Spring boot user authenticate with keycloak (microservices Keycloak Authentication Spring Boot Learn how to create a java application on top of spring boot 3 and protect it by using spring security and keycloak—without having to rely on keycloak adapters. Detailed guide on how to set up a keycloak server using a docker image. Keycloak makes it easy to work with many applications, not just spring boot projects. We saw in this. Keycloak Authentication Spring Boot.
From refactorfirst.com
Spring Cloud Gateway — Resource Server with Keycloak RBAC RefactorFirst Keycloak Authentication Spring Boot Detailed guide on how to set up a keycloak server using a docker image. This spring security tutorial will explore how to use keycloak and spring security oauth2 module to implement authentication and authorization in a spring boot. Learn how to create a java application on top of spring boot 3 and protect it by using spring security and keycloak—without. Keycloak Authentication Spring Boot.
From velog.io
[Authentication] NextAuth, Keycloak, Spring Boot 삼박자 맞추기 02 JWT, Spring Keycloak Authentication Spring Boot Keycloak makes it easy to work with many applications, not just spring boot projects. We saw in this article how to deploy and configure a keycloak server and then secure a spring boot app, first by using java ee security constraints and then by. This article will explore setting up robust. In today’s landscape of developing secure applications, implementing a. Keycloak Authentication Spring Boot.
From medium.com
OAuth2 and OpenID Authentication with Keycloak and Spring Security Keycloak Authentication Spring Boot Overview of keycloak's main concepts. Keycloak makes it easy to work with many applications, not just spring boot projects. However, with the deprecation of websecurityconfigureradapter and the migration of spring. This spring security tutorial will explore how to use keycloak and spring security oauth2 module to implement authentication and authorization in a spring boot. In today’s landscape of developing secure. Keycloak Authentication Spring Boot.
From stackoverflow.com
Use Keycloak Spring Adapter with Spring Boot 3 Stack Overflow Keycloak Authentication Spring Boot In this article, i will discuss how to implement keycloak with spring boot to secure user access to endpoints using tokens. Learn how to create a java application on top of spring boot 3 and protect it by using spring security and keycloak—without having to rely on keycloak adapters. Learn how to authenticate a spring boot app. However, with the. Keycloak Authentication Spring Boot.
From www.baeldung.com
A Quick Guide to Using Keycloak with Spring Boot Baeldung Keycloak Authentication Spring Boot We saw in this article how to deploy and configure a keycloak server and then secure a spring boot app, first by using java ee security constraints and then by. In this article, i will discuss how to implement keycloak with spring boot to secure user access to endpoints using tokens. Keycloak makes it easy to work with many applications,. Keycloak Authentication Spring Boot.
From www.baeldung.com
A Quick Guide to Using Keycloak with Spring Boot Baeldung Keycloak Authentication Spring Boot This spring security tutorial will explore how to use keycloak and spring security oauth2 module to implement authentication and authorization in a spring boot. Learn how to create a java application on top of spring boot 3 and protect it by using spring security and keycloak—without having to rely on keycloak adapters. Detailed guide on how to set up a. Keycloak Authentication Spring Boot.
From betterjavacode.com
The Definitive Guide to Use Keycloak With a Spring Boot Application Keycloak Authentication Spring Boot In today’s landscape of developing secure applications, implementing a robust authentication solution is an essential foundation. We saw in this article how to deploy and configure a keycloak server and then secure a spring boot app, first by using java ee security constraints and then by. In this article, i will discuss how to implement keycloak with spring boot to. Keycloak Authentication Spring Boot.
From walkingtree.tech
Securing FullStack Applications with React, Spring Boot, and Keycloak Authentication Spring Boot This spring security tutorial will explore how to use keycloak and spring security oauth2 module to implement authentication and authorization in a spring boot. Learn how to authenticate a spring boot app. Detailed guide on how to set up a keycloak server using a docker image. This article will explore setting up robust. Overview of keycloak's main concepts. Keycloak makes. Keycloak Authentication Spring Boot.
From medium.com
OAuth2 and OpenID Authentication with Keycloak and Spring Security Keycloak Authentication Spring Boot In today’s landscape of developing secure applications, implementing a robust authentication solution is an essential foundation. Learn how to create a java application on top of spring boot 3 and protect it by using spring security and keycloak—without having to rely on keycloak adapters. This article will explore setting up robust. Keycloak makes it easy to work with many applications,. Keycloak Authentication Spring Boot.
From www.youtube.com
Authentication in Spring boot application with Keycloak as OAuth2 Keycloak Authentication Spring Boot In today’s landscape of developing secure applications, implementing a robust authentication solution is an essential foundation. We saw in this article how to deploy and configure a keycloak server and then secure a spring boot app, first by using java ee security constraints and then by. Overview of keycloak's main concepts. Keycloak makes it easy to work with many applications,. Keycloak Authentication Spring Boot.
From github.com
GitHub wiemheni/CamundaSpringBootAngularKeycloakmain Keycloak Authentication Spring Boot Detailed guide on how to set up a keycloak server using a docker image. Overview of keycloak's main concepts. Learn how to authenticate a spring boot app. However, with the deprecation of websecurityconfigureradapter and the migration of spring. In today’s landscape of developing secure applications, implementing a robust authentication solution is an essential foundation. In this article, i will discuss. Keycloak Authentication Spring Boot.
From spring.io
Securing Services with Spring Cloud Gateway Keycloak Authentication Spring Boot Detailed guide on how to set up a keycloak server using a docker image. Overview of keycloak's main concepts. This spring security tutorial will explore how to use keycloak and spring security oauth2 module to implement authentication and authorization in a spring boot. In this article, i will discuss how to implement keycloak with spring boot to secure user access. Keycloak Authentication Spring Boot.
From techgeek628.medium.com
Easily secure your Spring Boot applications with Keycloak by Tech Keycloak Authentication Spring Boot Overview of keycloak's main concepts. However, with the deprecation of websecurityconfigureradapter and the migration of spring. In today’s landscape of developing secure applications, implementing a robust authentication solution is an essential foundation. This spring security tutorial will explore how to use keycloak and spring security oauth2 module to implement authentication and authorization in a spring boot. Learn how to create. Keycloak Authentication Spring Boot.