Manually Trusted Key Verification Strategy . Manually trusted key verification strategy reads: Click on add credentials and select ssh username with the private key. Checks the key provided by the remote host matches the key set by the. In slave configuration, select no verifying verification strategy for host key verification strategy. — manually provided key verification strategy : A host key verification strategy that works in a similar way to host key verification on unix/linux this host (depending on how this strategy has. Checks the remote key matches the key currently marked as trusted for this. For host key verification strategy, it’s easier to choose ‘manually trusted key verification strategy’, and then check the box for ‘require manual verification of initial. Under host key verification strategy, select manually trusted key verification strategy. For host, provide the ip address or hostname of the vm. This will allow master to connect with slave and host will also be remembered. Manually trusted verification strategy (this feature is stable starting from version 1.16 of the ssh build agents plugin) with this. For launch method, select launch agent agents via ssh. In the bitvise client software, host key verification window shows public key information not generated by me
from www.outsourcestrategies.com
Manually trusted key verification strategy reads: Checks the remote key matches the key currently marked as trusted for this. A host key verification strategy that works in a similar way to host key verification on unix/linux this host (depending on how this strategy has. In slave configuration, select no verifying verification strategy for host key verification strategy. For host, provide the ip address or hostname of the vm. This will allow master to connect with slave and host will also be remembered. Checks the key provided by the remote host matches the key set by the. In the bitvise client software, host key verification window shows public key information not generated by me — manually provided key verification strategy : For launch method, select launch agent agents via ssh.
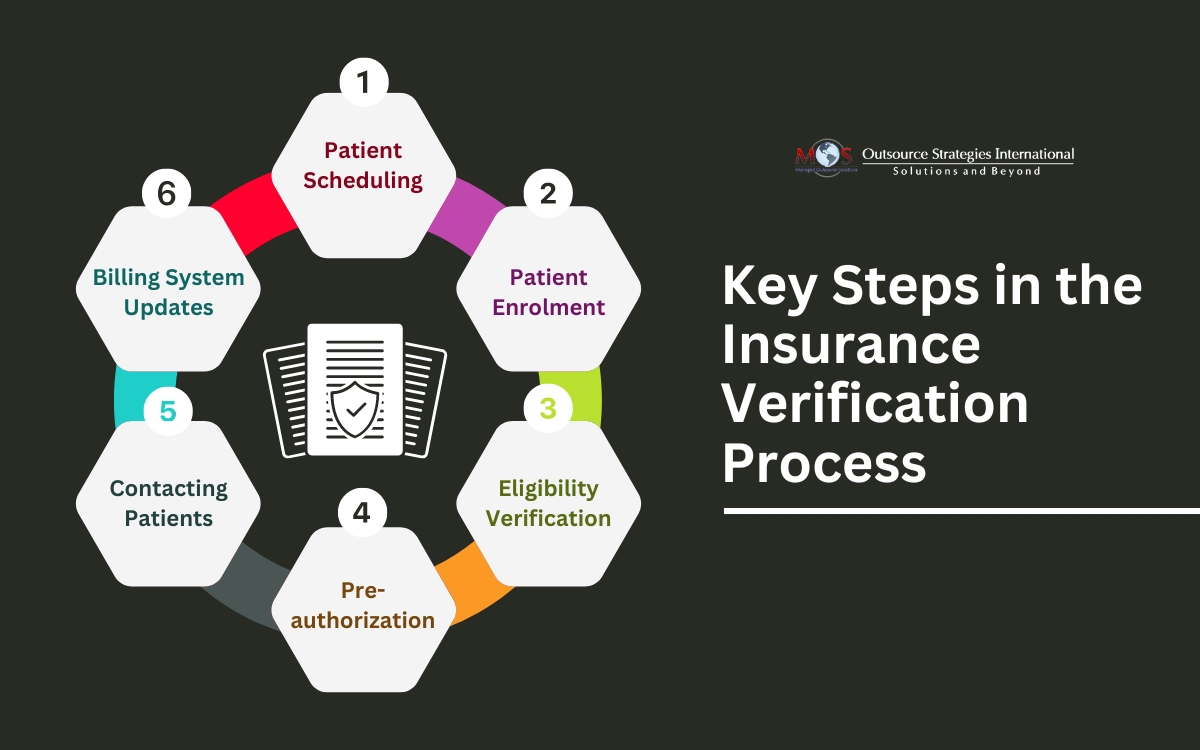
Key Features of the Insurance Verification Process
Manually Trusted Key Verification Strategy Manually trusted verification strategy (this feature is stable starting from version 1.16 of the ssh build agents plugin) with this. Checks the remote key matches the key currently marked as trusted for this. Checks the key provided by the remote host matches the key set by the. For host key verification strategy, it’s easier to choose ‘manually trusted key verification strategy’, and then check the box for ‘require manual verification of initial. — manually provided key verification strategy : Manually trusted key verification strategy reads: Click on add credentials and select ssh username with the private key. A host key verification strategy that works in a similar way to host key verification on unix/linux this host (depending on how this strategy has. Manually trusted verification strategy (this feature is stable starting from version 1.16 of the ssh build agents plugin) with this. In slave configuration, select no verifying verification strategy for host key verification strategy. For launch method, select launch agent agents via ssh. This will allow master to connect with slave and host will also be remembered. In the bitvise client software, host key verification window shows public key information not generated by me Under host key verification strategy, select manually trusted key verification strategy. For host, provide the ip address or hostname of the vm.
From elliit.se
Protocol security verification using dynamic key structures ELLIIT Manually Trusted Key Verification Strategy For host key verification strategy, it’s easier to choose ‘manually trusted key verification strategy’, and then check the box for ‘require manual verification of initial. For host, provide the ip address or hostname of the vm. Click on add credentials and select ssh username with the private key. — manually provided key verification strategy : In slave configuration, select no. Manually Trusted Key Verification Strategy.
From ciqa.net
How to create a Validation Master Plan in 5 steps. Templates & more Manually Trusted Key Verification Strategy — manually provided key verification strategy : Manually trusted verification strategy (this feature is stable starting from version 1.16 of the ssh build agents plugin) with this. For host, provide the ip address or hostname of the vm. Under host key verification strategy, select manually trusted key verification strategy. Checks the key provided by the remote host matches the key. Manually Trusted Key Verification Strategy.
From docs.cloudbees.com
Managing agents Manually Trusted Key Verification Strategy For launch method, select launch agent agents via ssh. Under host key verification strategy, select manually trusted key verification strategy. In slave configuration, select no verifying verification strategy for host key verification strategy. Manually trusted verification strategy (this feature is stable starting from version 1.16 of the ssh build agents plugin) with this. For host, provide the ip address or. Manually Trusted Key Verification Strategy.
From rtfm.co.ua
Jenkins запуск Jenkins в Docker и подключение SSH Slave Manually Trusted Key Verification Strategy — manually provided key verification strategy : For host, provide the ip address or hostname of the vm. In the bitvise client software, host key verification window shows public key information not generated by me This will allow master to connect with slave and host will also be remembered. Checks the remote key matches the key currently marked as trusted. Manually Trusted Key Verification Strategy.
From blog.csdn.net
Jenkins配置从节点问题:ssh slave known_hosts [SSH]与Slave JVM has terminated Manually Trusted Key Verification Strategy Checks the key provided by the remote host matches the key set by the. For launch method, select launch agent agents via ssh. Click on add credentials and select ssh username with the private key. Checks the remote key matches the key currently marked as trusted for this. — manually provided key verification strategy : A host key verification strategy. Manually Trusted Key Verification Strategy.
From github.com
Unable to create New Node on Jenkins · Issue 593 · QTDevOps Manually Trusted Key Verification Strategy A host key verification strategy that works in a similar way to host key verification on unix/linux this host (depending on how this strategy has. For host, provide the ip address or hostname of the vm. For launch method, select launch agent agents via ssh. — manually provided key verification strategy : Click on add credentials and select ssh username. Manually Trusted Key Verification Strategy.
From slideplayer.com
Lecture 20 DNS Sec Slides adapted from Olag Kampman ppt download Manually Trusted Key Verification Strategy In slave configuration, select no verifying verification strategy for host key verification strategy. Under host key verification strategy, select manually trusted key verification strategy. A host key verification strategy that works in a similar way to host key verification on unix/linux this host (depending on how this strategy has. Checks the remote key matches the key currently marked as trusted. Manually Trusted Key Verification Strategy.
From blog.rohaanjoshi.com
How to configure agents in Jenkins master Manually Trusted Key Verification Strategy — manually provided key verification strategy : Under host key verification strategy, select manually trusted key verification strategy. Click on add credentials and select ssh username with the private key. This will allow master to connect with slave and host will also be remembered. In slave configuration, select no verifying verification strategy for host key verification strategy. Manually trusted key. Manually Trusted Key Verification Strategy.
From www.yubico.com
What is CertificateBased Authentication Yubico Manually Trusted Key Verification Strategy A host key verification strategy that works in a similar way to host key verification on unix/linux this host (depending on how this strategy has. Checks the remote key matches the key currently marked as trusted for this. In slave configuration, select no verifying verification strategy for host key verification strategy. For launch method, select launch agent agents via ssh.. Manually Trusted Key Verification Strategy.
From codingtricks.io
How to configure Jenkins master and slave CodingtricksTechnology for Manually Trusted Key Verification Strategy Manually trusted verification strategy (this feature is stable starting from version 1.16 of the ssh build agents plugin) with this. For host, provide the ip address or hostname of the vm. This will allow master to connect with slave and host will also be remembered. Checks the remote key matches the key currently marked as trusted for this. — manually. Manually Trusted Key Verification Strategy.
From artemis-platform.readthedocs.io
Setup for Programming Exercises with Jenkins and GitLab — Artemis Manually Trusted Key Verification Strategy Checks the remote key matches the key currently marked as trusted for this. Manually trusted key verification strategy reads: Click on add credentials and select ssh username with the private key. In the bitvise client software, host key verification window shows public key information not generated by me — manually provided key verification strategy : Checks the key provided by. Manually Trusted Key Verification Strategy.
From developers.redhat.com
Automate your Git host key verification setup in Jenkins Red Hat Manually Trusted Key Verification Strategy Under host key verification strategy, select manually trusted key verification strategy. Checks the key provided by the remote host matches the key set by the. Click on add credentials and select ssh username with the private key. Checks the remote key matches the key currently marked as trusted for this. Manually trusted key verification strategy reads: Manually trusted verification strategy. Manually Trusted Key Verification Strategy.
From zhuanlan.zhihu.com
jenkins使用 知乎 Manually Trusted Key Verification Strategy — manually provided key verification strategy : Under host key verification strategy, select manually trusted key verification strategy. Checks the remote key matches the key currently marked as trusted for this. Manually trusted key verification strategy reads: This will allow master to connect with slave and host will also be remembered. A host key verification strategy that works in a. Manually Trusted Key Verification Strategy.
From testsigma.com
Verification vs Validation Testing Key Differences Manually Trusted Key Verification Strategy In the bitvise client software, host key verification window shows public key information not generated by me Manually trusted verification strategy (this feature is stable starting from version 1.16 of the ssh build agents plugin) with this. For launch method, select launch agent agents via ssh. For host, provide the ip address or hostname of the vm. Checks the remote. Manually Trusted Key Verification Strategy.
From yoonjk.github.io
Jenkins master/slave 구성 Cloud Native Journey Manually Trusted Key Verification Strategy In slave configuration, select no verifying verification strategy for host key verification strategy. Under host key verification strategy, select manually trusted key verification strategy. Manually trusted verification strategy (this feature is stable starting from version 1.16 of the ssh build agents plugin) with this. In the bitvise client software, host key verification window shows public key information not generated by. Manually Trusted Key Verification Strategy.
From docs.cloudbees.com
Managing agents Manually Trusted Key Verification Strategy A host key verification strategy that works in a similar way to host key verification on unix/linux this host (depending on how this strategy has. Checks the key provided by the remote host matches the key set by the. For host key verification strategy, it’s easier to choose ‘manually trusted key verification strategy’, and then check the box for ‘require. Manually Trusted Key Verification Strategy.
From docs.cloudbees.com
Managing agents Manually Trusted Key Verification Strategy Checks the key provided by the remote host matches the key set by the. For host, provide the ip address or hostname of the vm. Manually trusted key verification strategy reads: In the bitvise client software, host key verification window shows public key information not generated by me — manually provided key verification strategy : Under host key verification strategy,. Manually Trusted Key Verification Strategy.
From www.ssl.com
Browsers and Certificate Validation Manually Trusted Key Verification Strategy Checks the key provided by the remote host matches the key set by the. Manually trusted key verification strategy reads: For host, provide the ip address or hostname of the vm. For host key verification strategy, it’s easier to choose ‘manually trusted key verification strategy’, and then check the box for ‘require manual verification of initial. For launch method, select. Manually Trusted Key Verification Strategy.
From docs.pexip.com
Managing TLS and trusted CA certificates Pexip Infinity Docs Manually Trusted Key Verification Strategy — manually provided key verification strategy : Checks the key provided by the remote host matches the key set by the. For launch method, select launch agent agents via ssh. In the bitvise client software, host key verification window shows public key information not generated by me Click on add credentials and select ssh username with the private key. Manually. Manually Trusted Key Verification Strategy.
From middlewaretechnologies.in
How to setup and connect an agent node to jenkins controller Manually Trusted Key Verification Strategy In the bitvise client software, host key verification window shows public key information not generated by me For launch method, select launch agent agents via ssh. Manually trusted key verification strategy reads: A host key verification strategy that works in a similar way to host key verification on unix/linux this host (depending on how this strategy has. For host key. Manually Trusted Key Verification Strategy.
From aws.gunkao.com
Unify your iOS mobile app CI/CD pipeline with Gunkao EC2 Mac Instances Manually Trusted Key Verification Strategy In slave configuration, select no verifying verification strategy for host key verification strategy. This will allow master to connect with slave and host will also be remembered. In the bitvise client software, host key verification window shows public key information not generated by me — manually provided key verification strategy : For launch method, select launch agent agents via ssh.. Manually Trusted Key Verification Strategy.
From middlewaretechnologies.in
How to setup and connect an agent node to jenkins controller Manually Trusted Key Verification Strategy For host key verification strategy, it’s easier to choose ‘manually trusted key verification strategy’, and then check the box for ‘require manual verification of initial. This will allow master to connect with slave and host will also be remembered. Manually trusted key verification strategy reads: Click on add credentials and select ssh username with the private key. For launch method,. Manually Trusted Key Verification Strategy.
From artemis-platform.readthedocs.io
Jenkins and LocalVC Setup — Artemis documentation Manually Trusted Key Verification Strategy — manually provided key verification strategy : For host, provide the ip address or hostname of the vm. For launch method, select launch agent agents via ssh. Under host key verification strategy, select manually trusted key verification strategy. In the bitvise client software, host key verification window shows public key information not generated by me Checks the key provided by. Manually Trusted Key Verification Strategy.
From medium.com
Electronic Verification Systems — A Key Strategy to Combat Identity Manually Trusted Key Verification Strategy Click on add credentials and select ssh username with the private key. For host, provide the ip address or hostname of the vm. This will allow master to connect with slave and host will also be remembered. — manually provided key verification strategy : In slave configuration, select no verifying verification strategy for host key verification strategy. A host key. Manually Trusted Key Verification Strategy.
From www.militaryaerospace.com
Trusted boot a key strategy for ensuring the trustworthiness of an Manually Trusted Key Verification Strategy Checks the remote key matches the key currently marked as trusted for this. — manually provided key verification strategy : For host key verification strategy, it’s easier to choose ‘manually trusted key verification strategy’, and then check the box for ‘require manual verification of initial. In slave configuration, select no verifying verification strategy for host key verification strategy. In the. Manually Trusted Key Verification Strategy.
From slideplayer.com
Cryptography & Security ppt download Manually Trusted Key Verification Strategy Under host key verification strategy, select manually trusted key verification strategy. For host key verification strategy, it’s easier to choose ‘manually trusted key verification strategy’, and then check the box for ‘require manual verification of initial. Checks the remote key matches the key currently marked as trusted for this. Checks the key provided by the remote host matches the key. Manually Trusted Key Verification Strategy.
From kacfg.com
【AWS】EC2のDockerでJenkins(Master+Slave)導入 ふにノート Manually Trusted Key Verification Strategy Under host key verification strategy, select manually trusted key verification strategy. — manually provided key verification strategy : For host key verification strategy, it’s easier to choose ‘manually trusted key verification strategy’, and then check the box for ‘require manual verification of initial. In slave configuration, select no verifying verification strategy for host key verification strategy. Checks the remote key. Manually Trusted Key Verification Strategy.
From www.redhat.com
How to use a VM as a Jenkins agent Enable Sysadmin Manually Trusted Key Verification Strategy For host, provide the ip address or hostname of the vm. This will allow master to connect with slave and host will also be remembered. — manually provided key verification strategy : A host key verification strategy that works in a similar way to host key verification on unix/linux this host (depending on how this strategy has. For host key. Manually Trusted Key Verification Strategy.
From www.geeksforgeeks.org
Jenkins Master And Slave Configuration Using AWS EC2 Instance Manually Trusted Key Verification Strategy In slave configuration, select no verifying verification strategy for host key verification strategy. Manually trusted key verification strategy reads: Under host key verification strategy, select manually trusted key verification strategy. In the bitvise client software, host key verification window shows public key information not generated by me For host key verification strategy, it’s easier to choose ‘manually trusted key verification. Manually Trusted Key Verification Strategy.
From www.vrogue.co
What Is Kyc Verification vrogue.co Manually Trusted Key Verification Strategy In slave configuration, select no verifying verification strategy for host key verification strategy. For launch method, select launch agent agents via ssh. Manually trusted verification strategy (this feature is stable starting from version 1.16 of the ssh build agents plugin) with this. For host key verification strategy, it’s easier to choose ‘manually trusted key verification strategy’, and then check the. Manually Trusted Key Verification Strategy.
From support.microfocus.com
How to manually create a Trusted Application Key for a GWAVA POA interface Manually Trusted Key Verification Strategy — manually provided key verification strategy : Checks the key provided by the remote host matches the key set by the. Manually trusted key verification strategy reads: Checks the remote key matches the key currently marked as trusted for this. For host key verification strategy, it’s easier to choose ‘manually trusted key verification strategy’, and then check the box for. Manually Trusted Key Verification Strategy.
From yoonjk.github.io
Jenkins master/slave 구성 Cloud Native Journey Manually Trusted Key Verification Strategy Checks the remote key matches the key currently marked as trusted for this. This will allow master to connect with slave and host will also be remembered. — manually provided key verification strategy : Manually trusted verification strategy (this feature is stable starting from version 1.16 of the ssh build agents plugin) with this. For launch method, select launch agent. Manually Trusted Key Verification Strategy.
From www.outsourcestrategies.com
Key Features of the Insurance Verification Process Manually Trusted Key Verification Strategy A host key verification strategy that works in a similar way to host key verification on unix/linux this host (depending on how this strategy has. Click on add credentials and select ssh username with the private key. Checks the key provided by the remote host matches the key set by the. Manually trusted key verification strategy reads: For host, provide. Manually Trusted Key Verification Strategy.
From blog.csdn.net
Jenkins安装_manually provided key verification strategyCSDN博客 Manually Trusted Key Verification Strategy Checks the key provided by the remote host matches the key set by the. For launch method, select launch agent agents via ssh. In slave configuration, select no verifying verification strategy for host key verification strategy. Manually trusted verification strategy (this feature is stable starting from version 1.16 of the ssh build agents plugin) with this. A host key verification. Manually Trusted Key Verification Strategy.
From www.imooc.com
Jenkins 集群搭建_慕课手记 Manually Trusted Key Verification Strategy In slave configuration, select no verifying verification strategy for host key verification strategy. For launch method, select launch agent agents via ssh. This will allow master to connect with slave and host will also be remembered. For host key verification strategy, it’s easier to choose ‘manually trusted key verification strategy’, and then check the box for ‘require manual verification of. Manually Trusted Key Verification Strategy.