Access Card Protocols . In an era where protecting data and premises. • all corporate 1000 formats are 35 bits long but. Cost of key card and key fob entry systems. Proximity cards, also known as prox cards or access control cards, are contactless id cards or keyfobs containing programmed data. They are a cornerstone of modern security. The data, or code, is “read” by a card reader and. Access control cards are more than just a means to open doors; Fingerprint, facial, iris, retina, voice and hand geometry. When you include the readers, panels, wiring network. • the customer’s access control panels must be capable of decoding the corporate 1000 format.
from www.duplicatecard.com
They are a cornerstone of modern security. The data, or code, is “read” by a card reader and. When you include the readers, panels, wiring network. In an era where protecting data and premises. Cost of key card and key fob entry systems. • all corporate 1000 formats are 35 bits long but. • the customer’s access control panels must be capable of decoding the corporate 1000 format. Proximity cards, also known as prox cards or access control cards, are contactless id cards or keyfobs containing programmed data. Fingerprint, facial, iris, retina, voice and hand geometry. Access control cards are more than just a means to open doors;
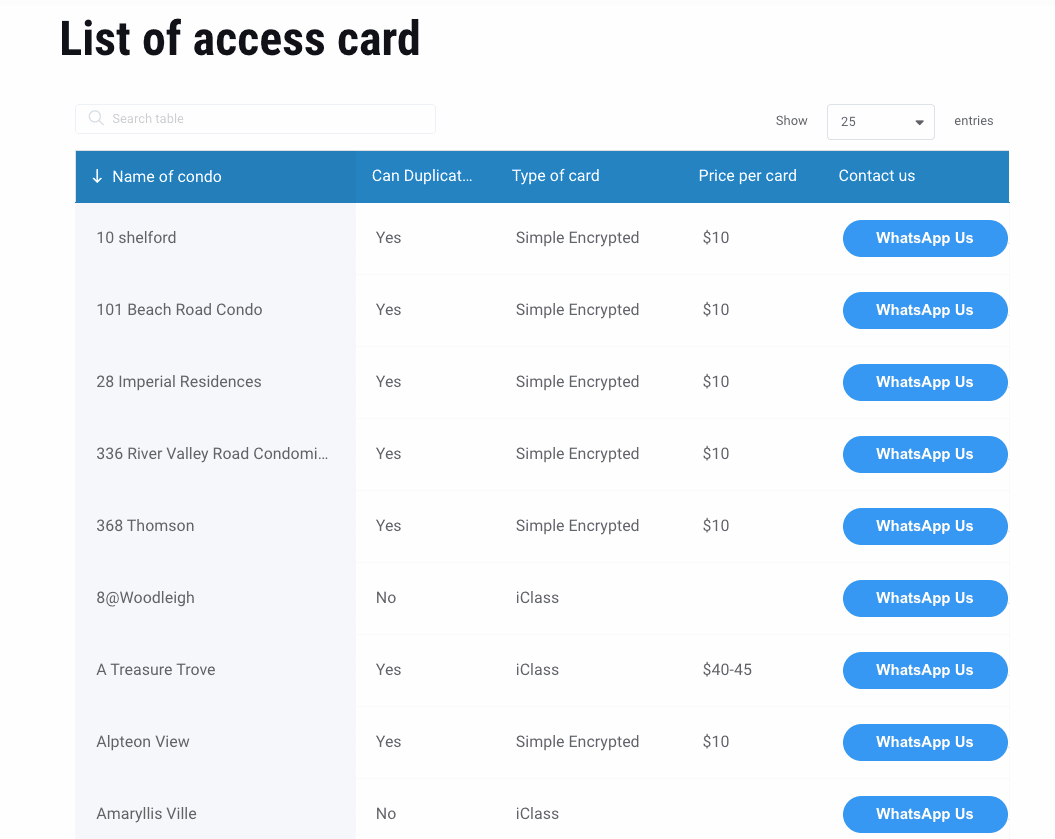
Easy way to find out if your access card can be duplicated
Access Card Protocols The data, or code, is “read” by a card reader and. The data, or code, is “read” by a card reader and. • all corporate 1000 formats are 35 bits long but. They are a cornerstone of modern security. When you include the readers, panels, wiring network. Access control cards are more than just a means to open doors; Fingerprint, facial, iris, retina, voice and hand geometry. • the customer’s access control panels must be capable of decoding the corporate 1000 format. In an era where protecting data and premises. Cost of key card and key fob entry systems. Proximity cards, also known as prox cards or access control cards, are contactless id cards or keyfobs containing programmed data.
From www.dla.mil
site lets DLA employees schedule Common Access Card, ID appointments Access Card Protocols Proximity cards, also known as prox cards or access control cards, are contactless id cards or keyfobs containing programmed data. Access control cards are more than just a means to open doors; The data, or code, is “read” by a card reader and. Cost of key card and key fob entry systems. They are a cornerstone of modern security. In. Access Card Protocols.
From cartoondealer.com
POP3. Post Office Protocol Version 3. Standard Protocol On Access Card Protocols Proximity cards, also known as prox cards or access control cards, are contactless id cards or keyfobs containing programmed data. Access control cards are more than just a means to open doors; The data, or code, is “read” by a card reader and. • the customer’s access control panels must be capable of decoding the corporate 1000 format. Fingerprint, facial,. Access Card Protocols.
From www.slideshare.net
Smart Card Based Protocol For Secure And Controlled Access Of Mobile Access Card Protocols In an era where protecting data and premises. • all corporate 1000 formats are 35 bits long but. When you include the readers, panels, wiring network. The data, or code, is “read” by a card reader and. • the customer’s access control panels must be capable of decoding the corporate 1000 format. They are a cornerstone of modern security. Fingerprint,. Access Card Protocols.
From eptura.com
Eptura Reinforces Workplace Security with New Capabilities for Managing Access Card Protocols • the customer’s access control panels must be capable of decoding the corporate 1000 format. Fingerprint, facial, iris, retina, voice and hand geometry. In an era where protecting data and premises. Cost of key card and key fob entry systems. When you include the readers, panels, wiring network. The data, or code, is “read” by a card reader and. They. Access Card Protocols.
From www.action1st.com
Parking Access Control Systems with Key Card Technology Access Card Protocols Cost of key card and key fob entry systems. In an era where protecting data and premises. The data, or code, is “read” by a card reader and. Proximity cards, also known as prox cards or access control cards, are contactless id cards or keyfobs containing programmed data. When you include the readers, panels, wiring network. Fingerprint, facial, iris, retina,. Access Card Protocols.
From ingenia.co.uk
ID Access Cards Access Control Access Card Protocols When you include the readers, panels, wiring network. They are a cornerstone of modern security. • all corporate 1000 formats are 35 bits long but. • the customer’s access control panels must be capable of decoding the corporate 1000 format. Proximity cards, also known as prox cards or access control cards, are contactless id cards or keyfobs containing programmed data.. Access Card Protocols.
From www.studocu.com
CNpractical 1 Understanding the working of NIC cards, Access Card Protocols When you include the readers, panels, wiring network. Proximity cards, also known as prox cards or access control cards, are contactless id cards or keyfobs containing programmed data. The data, or code, is “read” by a card reader and. In an era where protecting data and premises. They are a cornerstone of modern security. Fingerprint, facial, iris, retina, voice and. Access Card Protocols.
From www.scaler.com
Multiple Access Protocols Scaler Topics Access Card Protocols Access control cards are more than just a means to open doors; In an era where protecting data and premises. Fingerprint, facial, iris, retina, voice and hand geometry. Proximity cards, also known as prox cards or access control cards, are contactless id cards or keyfobs containing programmed data. They are a cornerstone of modern security. • all corporate 1000 formats. Access Card Protocols.
From www.codingninjas.com
Controlled Access Protocol Coding Ninjas Access Card Protocols Access control cards are more than just a means to open doors; • all corporate 1000 formats are 35 bits long but. The data, or code, is “read” by a card reader and. When you include the readers, panels, wiring network. In an era where protecting data and premises. Cost of key card and key fob entry systems. Fingerprint, facial,. Access Card Protocols.
From www.youtube.com
How to Copy an Apartment RFID Card? RFID Card Duplicator YouTube Access Card Protocols • all corporate 1000 formats are 35 bits long but. • the customer’s access control panels must be capable of decoding the corporate 1000 format. Access control cards are more than just a means to open doors; Fingerprint, facial, iris, retina, voice and hand geometry. The data, or code, is “read” by a card reader and. In an era where. Access Card Protocols.
From www.indiamart.com
PVC Rectangular Access Card at Rs 10 in Chengalpattu ID 20466527155 Access Card Protocols Access control cards are more than just a means to open doors; • all corporate 1000 formats are 35 bits long but. Proximity cards, also known as prox cards or access control cards, are contactless id cards or keyfobs containing programmed data. The data, or code, is “read” by a card reader and. They are a cornerstone of modern security.. Access Card Protocols.
From www.proces-data.com
NFC Access Card for PD9200 Flow Computer PROCESDATA Access Card Protocols • the customer’s access control panels must be capable of decoding the corporate 1000 format. In an era where protecting data and premises. The data, or code, is “read” by a card reader and. Fingerprint, facial, iris, retina, voice and hand geometry. Cost of key card and key fob entry systems. • all corporate 1000 formats are 35 bits long. Access Card Protocols.
From www.slideserve.com
PPT Secure Electronic Transaction PowerPoint Presentation, free Access Card Protocols Cost of key card and key fob entry systems. When you include the readers, panels, wiring network. The data, or code, is “read” by a card reader and. • the customer’s access control panels must be capable of decoding the corporate 1000 format. In an era where protecting data and premises. Fingerprint, facial, iris, retina, voice and hand geometry. Access. Access Card Protocols.
From www.duplicatecard.com
Easy way to find out if your access card can be duplicated Access Card Protocols When you include the readers, panels, wiring network. Cost of key card and key fob entry systems. • the customer’s access control panels must be capable of decoding the corporate 1000 format. The data, or code, is “read” by a card reader and. Fingerprint, facial, iris, retina, voice and hand geometry. They are a cornerstone of modern security. Access control. Access Card Protocols.
From www.renderhub.com
Access Card 3D Model by Grishmanovskij Anton Access Card Protocols In an era where protecting data and premises. Fingerprint, facial, iris, retina, voice and hand geometry. Access control cards are more than just a means to open doors; The data, or code, is “read” by a card reader and. They are a cornerstone of modern security. Cost of key card and key fob entry systems. Proximity cards, also known as. Access Card Protocols.
From www.vecteezy.com
Access control. Access card reader. Wireless RFID, NFC. Vector stock Access Card Protocols In an era where protecting data and premises. Fingerprint, facial, iris, retina, voice and hand geometry. The data, or code, is “read” by a card reader and. Access control cards are more than just a means to open doors; They are a cornerstone of modern security. When you include the readers, panels, wiring network. • all corporate 1000 formats are. Access Card Protocols.
From www.studocu.com
Chapter 1 Multiple Access Protocols 1/ Chapter 1 Multiple Access Access Card Protocols • the customer’s access control panels must be capable of decoding the corporate 1000 format. Access control cards are more than just a means to open doors; In an era where protecting data and premises. • all corporate 1000 formats are 35 bits long but. Proximity cards, also known as prox cards or access control cards, are contactless id cards. Access Card Protocols.
From www.vecteezy.com
security access card 10963624 Vector Art at Vecteezy Access Card Protocols The data, or code, is “read” by a card reader and. Access control cards are more than just a means to open doors; • the customer’s access control panels must be capable of decoding the corporate 1000 format. In an era where protecting data and premises. Proximity cards, also known as prox cards or access control cards, are contactless id. Access Card Protocols.
From data-flair.training
Multiple Access Protocols DataFlair Access Card Protocols The data, or code, is “read” by a card reader and. • the customer’s access control panels must be capable of decoding the corporate 1000 format. They are a cornerstone of modern security. Cost of key card and key fob entry systems. When you include the readers, panels, wiring network. Access control cards are more than just a means to. Access Card Protocols.
From pcmart.com.my
Card Access Attendance System, RFID Door Access System Access Card Protocols When you include the readers, panels, wiring network. Fingerprint, facial, iris, retina, voice and hand geometry. The data, or code, is “read” by a card reader and. • the customer’s access control panels must be capable of decoding the corporate 1000 format. • all corporate 1000 formats are 35 bits long but. Proximity cards, also known as prox cards or. Access Card Protocols.
From luxnfc.co.uk
Digital Access Cards LuxNfC Access Card Protocols Proximity cards, also known as prox cards or access control cards, are contactless id cards or keyfobs containing programmed data. When you include the readers, panels, wiring network. • the customer’s access control panels must be capable of decoding the corporate 1000 format. Access control cards are more than just a means to open doors; They are a cornerstone of. Access Card Protocols.
From accesscard.ae
How To Identify Access Control Cards Access Card Duplicator Access Card Protocols Fingerprint, facial, iris, retina, voice and hand geometry. • the customer’s access control panels must be capable of decoding the corporate 1000 format. Access control cards are more than just a means to open doors; In an era where protecting data and premises. When you include the readers, panels, wiring network. • all corporate 1000 formats are 35 bits long. Access Card Protocols.
From www.educba.com
Multiple Access Protocol Complete Guide on Multiple Access Protocol Access Card Protocols When you include the readers, panels, wiring network. • all corporate 1000 formats are 35 bits long but. The data, or code, is “read” by a card reader and. Access control cards are more than just a means to open doors; Cost of key card and key fob entry systems. In an era where protecting data and premises. Proximity cards,. Access Card Protocols.
From opensea.io
Access card 1 Access_cards OpenSea Access Card Protocols Access control cards are more than just a means to open doors; Proximity cards, also known as prox cards or access control cards, are contactless id cards or keyfobs containing programmed data. They are a cornerstone of modern security. When you include the readers, panels, wiring network. • all corporate 1000 formats are 35 bits long but. Cost of key. Access Card Protocols.
From www.alamy.com
Security access card abstract concept vector illustration. Electronic Access Card Protocols Fingerprint, facial, iris, retina, voice and hand geometry. They are a cornerstone of modern security. When you include the readers, panels, wiring network. • the customer’s access control panels must be capable of decoding the corporate 1000 format. The data, or code, is “read” by a card reader and. • all corporate 1000 formats are 35 bits long but. Proximity. Access Card Protocols.
From www.marketingderby.co.uk
Demand soars for innovative access card Marketing Derby Access Card Protocols Cost of key card and key fob entry systems. When you include the readers, panels, wiring network. The data, or code, is “read” by a card reader and. • the customer’s access control panels must be capable of decoding the corporate 1000 format. Fingerprint, facial, iris, retina, voice and hand geometry. They are a cornerstone of modern security. Proximity cards,. Access Card Protocols.
From www.slideserve.com
PPT Random Access protocols PowerPoint Presentation, free download Access Card Protocols Access control cards are more than just a means to open doors; • the customer’s access control panels must be capable of decoding the corporate 1000 format. • all corporate 1000 formats are 35 bits long but. In an era where protecting data and premises. Cost of key card and key fob entry systems. The data, or code, is “read”. Access Card Protocols.
From www.slideserve.com
PPT 13 Link Layer, Multiple Access Protocols PowerPoint Presentation Access Card Protocols When you include the readers, panels, wiring network. Proximity cards, also known as prox cards or access control cards, are contactless id cards or keyfobs containing programmed data. • all corporate 1000 formats are 35 bits long but. • the customer’s access control panels must be capable of decoding the corporate 1000 format. Fingerprint, facial, iris, retina, voice and hand. Access Card Protocols.
From www.digitalid.co.uk
Why Isn't My Access Control Card Working? Digital ID Access Card Protocols They are a cornerstone of modern security. Access control cards are more than just a means to open doors; • the customer’s access control panels must be capable of decoding the corporate 1000 format. Cost of key card and key fob entry systems. Proximity cards, also known as prox cards or access control cards, are contactless id cards or keyfobs. Access Card Protocols.
From www.broadbandsearch.net
Defining Message Access Protocol (IMAP) Definition, Version Access Card Protocols They are a cornerstone of modern security. Fingerprint, facial, iris, retina, voice and hand geometry. • all corporate 1000 formats are 35 bits long but. When you include the readers, panels, wiring network. The data, or code, is “read” by a card reader and. Cost of key card and key fob entry systems. In an era where protecting data and. Access Card Protocols.
From medium.com
CSMA/CA — Wireless Medium Access Control Protocol by Geeky much Access Card Protocols The data, or code, is “read” by a card reader and. Access control cards are more than just a means to open doors; Cost of key card and key fob entry systems. They are a cornerstone of modern security. • all corporate 1000 formats are 35 bits long but. In an era where protecting data and premises. Proximity cards, also. Access Card Protocols.
From www.slideserve.com
PPT 13 Link Layer, Multiple Access Protocols PowerPoint Presentation Access Card Protocols In an era where protecting data and premises. They are a cornerstone of modern security. Fingerprint, facial, iris, retina, voice and hand geometry. Cost of key card and key fob entry systems. • all corporate 1000 formats are 35 bits long but. When you include the readers, panels, wiring network. Proximity cards, also known as prox cards or access control. Access Card Protocols.
From www.aliexpress.com
Free Shipping DAHUA Access Control Fingerprint Reader 125KHz Support Access Card Protocols Access control cards are more than just a means to open doors; In an era where protecting data and premises. • the customer’s access control panels must be capable of decoding the corporate 1000 format. The data, or code, is “read” by a card reader and. • all corporate 1000 formats are 35 bits long but. They are a cornerstone. Access Card Protocols.
From psdfreebies.com
Conference VIP Entry Pass ID Card Template PSD Access Card Protocols Fingerprint, facial, iris, retina, voice and hand geometry. Cost of key card and key fob entry systems. When you include the readers, panels, wiring network. • all corporate 1000 formats are 35 bits long but. Access control cards are more than just a means to open doors; Proximity cards, also known as prox cards or access control cards, are contactless. Access Card Protocols.
From www.digitalid.co.uk
Can You Personalise Access Control Cards? Access Card Protocols They are a cornerstone of modern security. Fingerprint, facial, iris, retina, voice and hand geometry. When you include the readers, panels, wiring network. • the customer’s access control panels must be capable of decoding the corporate 1000 format. Access control cards are more than just a means to open doors; The data, or code, is “read” by a card reader. Access Card Protocols.