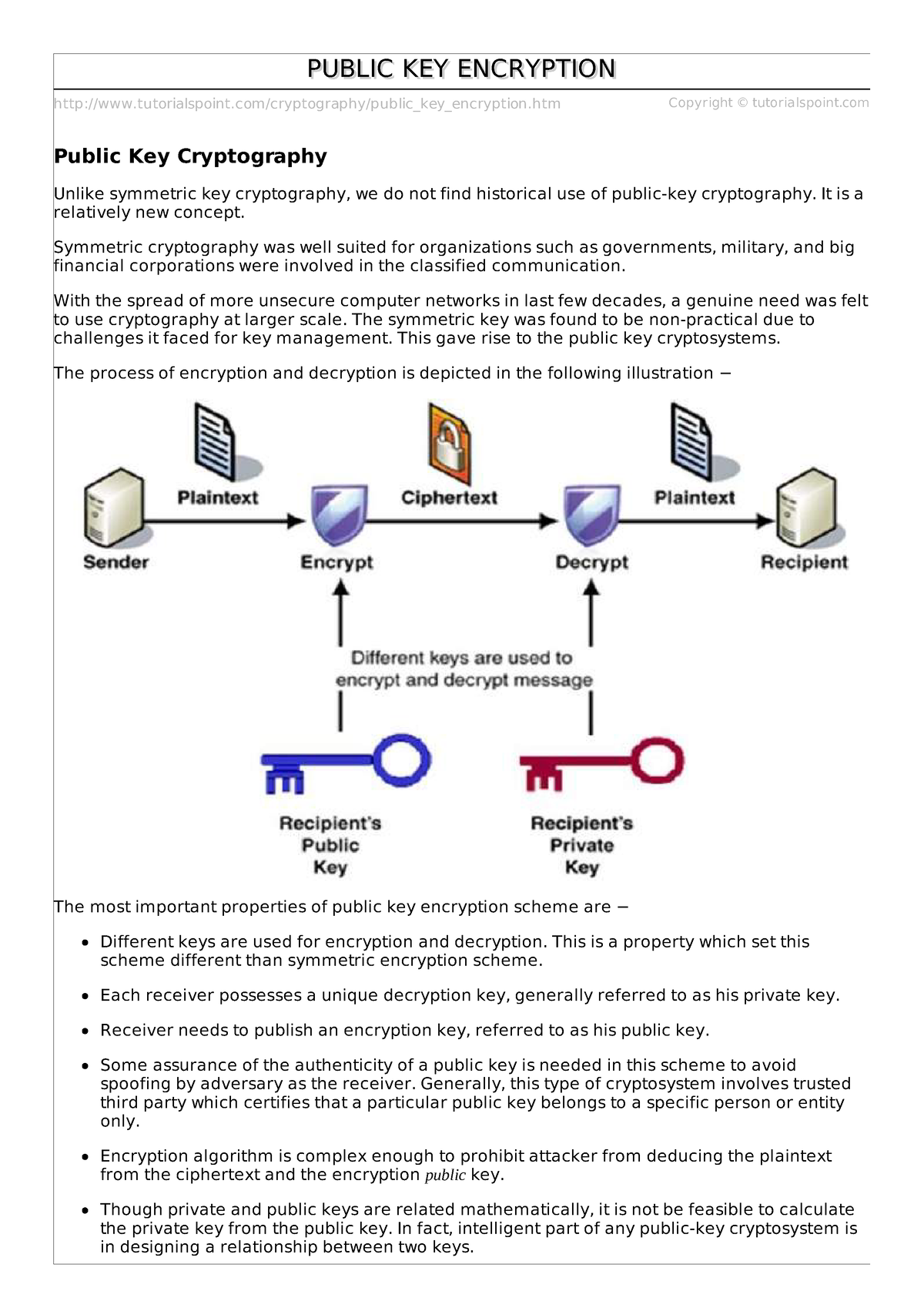
Purpose Of Key Encryption . encryption is the process of transforming readable plaintext into unreadable ciphertext to mask sensitive information from. the encryption algorithm is simply a mathematical formula designed to scramble data, while the key is used as. the public key is typically stored on a public key infrastructure server and is used to encrypt data securely before it is sent. public key cryptography is a method of encrypting or signing data with two different keys and making one of the keys, the. an encryption key is a piece of data utilized in cryptography to transform plaintext into ciphertext (encryption) and vice versa.
from www.studocu.com
an encryption key is a piece of data utilized in cryptography to transform plaintext into ciphertext (encryption) and vice versa. the public key is typically stored on a public key infrastructure server and is used to encrypt data securely before it is sent. encryption is the process of transforming readable plaintext into unreadable ciphertext to mask sensitive information from. the encryption algorithm is simply a mathematical formula designed to scramble data, while the key is used as. public key cryptography is a method of encrypting or signing data with two different keys and making one of the keys, the.
Public key encryption Cryptography and network security notes Studocu
Purpose Of Key Encryption an encryption key is a piece of data utilized in cryptography to transform plaintext into ciphertext (encryption) and vice versa. encryption is the process of transforming readable plaintext into unreadable ciphertext to mask sensitive information from. an encryption key is a piece of data utilized in cryptography to transform plaintext into ciphertext (encryption) and vice versa. the encryption algorithm is simply a mathematical formula designed to scramble data, while the key is used as. the public key is typically stored on a public key infrastructure server and is used to encrypt data securely before it is sent. public key cryptography is a method of encrypting or signing data with two different keys and making one of the keys, the.
From www.okta.com
Hashing vs. Encryption Definitions & Differences Okta Purpose Of Key Encryption an encryption key is a piece of data utilized in cryptography to transform plaintext into ciphertext (encryption) and vice versa. the encryption algorithm is simply a mathematical formula designed to scramble data, while the key is used as. the public key is typically stored on a public key infrastructure server and is used to encrypt data securely. Purpose Of Key Encryption.
From atos.net
Protecting your sensitive data with double key encryption Atos Purpose Of Key Encryption an encryption key is a piece of data utilized in cryptography to transform plaintext into ciphertext (encryption) and vice versa. the public key is typically stored on a public key infrastructure server and is used to encrypt data securely before it is sent. the encryption algorithm is simply a mathematical formula designed to scramble data, while the. Purpose Of Key Encryption.
From learn.g2.com
How Public Key Encryption Ensures Data Integrity Purpose Of Key Encryption the encryption algorithm is simply a mathematical formula designed to scramble data, while the key is used as. encryption is the process of transforming readable plaintext into unreadable ciphertext to mask sensitive information from. an encryption key is a piece of data utilized in cryptography to transform plaintext into ciphertext (encryption) and vice versa. public key. Purpose Of Key Encryption.
From www.okta.com
Public Key Encryption What Is Public Cryptography? Okta AU & NZ Purpose Of Key Encryption encryption is the process of transforming readable plaintext into unreadable ciphertext to mask sensitive information from. an encryption key is a piece of data utilized in cryptography to transform plaintext into ciphertext (encryption) and vice versa. the encryption algorithm is simply a mathematical formula designed to scramble data, while the key is used as. public key. Purpose Of Key Encryption.
From www.vrogue.co
Encryption Algorithms Explained With Examples vrogue.co Purpose Of Key Encryption the encryption algorithm is simply a mathematical formula designed to scramble data, while the key is used as. encryption is the process of transforming readable plaintext into unreadable ciphertext to mask sensitive information from. public key cryptography is a method of encrypting or signing data with two different keys and making one of the keys, the. . Purpose Of Key Encryption.
From securityboulevard.com
Symmetric Encryption Algorithms Live Long & Encrypt Security Boulevard Purpose Of Key Encryption an encryption key is a piece of data utilized in cryptography to transform plaintext into ciphertext (encryption) and vice versa. encryption is the process of transforming readable plaintext into unreadable ciphertext to mask sensitive information from. the public key is typically stored on a public key infrastructure server and is used to encrypt data securely before it. Purpose Of Key Encryption.
From people.eecs.berkeley.edu
Public Key Cryptography Purpose Of Key Encryption the public key is typically stored on a public key infrastructure server and is used to encrypt data securely before it is sent. an encryption key is a piece of data utilized in cryptography to transform plaintext into ciphertext (encryption) and vice versa. public key cryptography is a method of encrypting or signing data with two different. Purpose Of Key Encryption.
From sectigo.com
Public Key vs Private Key Public Key Cryptography Explained Sectigo Purpose Of Key Encryption encryption is the process of transforming readable plaintext into unreadable ciphertext to mask sensitive information from. an encryption key is a piece of data utilized in cryptography to transform plaintext into ciphertext (encryption) and vice versa. public key cryptography is a method of encrypting or signing data with two different keys and making one of the keys,. Purpose Of Key Encryption.
From www.cisco.com
What Is Encryption? Explanation and Types Cisco Purpose Of Key Encryption encryption is the process of transforming readable plaintext into unreadable ciphertext to mask sensitive information from. an encryption key is a piece of data utilized in cryptography to transform plaintext into ciphertext (encryption) and vice versa. the encryption algorithm is simply a mathematical formula designed to scramble data, while the key is used as. public key. Purpose Of Key Encryption.
From research.aimultiple.com
Encryption Key Management Benefits, Tools & Best Practices in 2024 Purpose Of Key Encryption public key cryptography is a method of encrypting or signing data with two different keys and making one of the keys, the. the public key is typically stored on a public key infrastructure server and is used to encrypt data securely before it is sent. an encryption key is a piece of data utilized in cryptography to. Purpose Of Key Encryption.
From www.vrogue.co
Symmetric Vs Asymmetric Encryption What Are The Diffe vrogue.co Purpose Of Key Encryption encryption is the process of transforming readable plaintext into unreadable ciphertext to mask sensitive information from. an encryption key is a piece of data utilized in cryptography to transform plaintext into ciphertext (encryption) and vice versa. the public key is typically stored on a public key infrastructure server and is used to encrypt data securely before it. Purpose Of Key Encryption.
From bitcoinik.com
Cryptography Simply Explained Bitcoinik Purpose Of Key Encryption encryption is the process of transforming readable plaintext into unreadable ciphertext to mask sensitive information from. public key cryptography is a method of encrypting or signing data with two different keys and making one of the keys, the. an encryption key is a piece of data utilized in cryptography to transform plaintext into ciphertext (encryption) and vice. Purpose Of Key Encryption.
From chandabdulsalam.medium.com
AES Symmetric Encryption with ClientServer Model (Typescript — C Purpose Of Key Encryption an encryption key is a piece of data utilized in cryptography to transform plaintext into ciphertext (encryption) and vice versa. encryption is the process of transforming readable plaintext into unreadable ciphertext to mask sensitive information from. the encryption algorithm is simply a mathematical formula designed to scramble data, while the key is used as. public key. Purpose Of Key Encryption.
From computer-trickster.blogspot.com
Encryption TRICKSTER Purpose Of Key Encryption the encryption algorithm is simply a mathematical formula designed to scramble data, while the key is used as. encryption is the process of transforming readable plaintext into unreadable ciphertext to mask sensitive information from. public key cryptography is a method of encrypting or signing data with two different keys and making one of the keys, the. . Purpose Of Key Encryption.
From techhyme.com
Public Key Cryptography A Brief Guide Tech Hyme Purpose Of Key Encryption the public key is typically stored on a public key infrastructure server and is used to encrypt data securely before it is sent. public key cryptography is a method of encrypting or signing data with two different keys and making one of the keys, the. an encryption key is a piece of data utilized in cryptography to. Purpose Of Key Encryption.
From o3schools.com
Ultimate Guide to Understanding What Symmetric Key Cryptography is 2023 Purpose Of Key Encryption an encryption key is a piece of data utilized in cryptography to transform plaintext into ciphertext (encryption) and vice versa. the public key is typically stored on a public key infrastructure server and is used to encrypt data securely before it is sent. the encryption algorithm is simply a mathematical formula designed to scramble data, while the. Purpose Of Key Encryption.
From www.studocu.com
Public key encryption Cryptography and network security notes Studocu Purpose Of Key Encryption the public key is typically stored on a public key infrastructure server and is used to encrypt data securely before it is sent. public key cryptography is a method of encrypting or signing data with two different keys and making one of the keys, the. encryption is the process of transforming readable plaintext into unreadable ciphertext to. Purpose Of Key Encryption.
From carreersupport.com
What is Symmetric Key Encryption? A Simple Explanation Purpose Of Key Encryption the public key is typically stored on a public key infrastructure server and is used to encrypt data securely before it is sent. the encryption algorithm is simply a mathematical formula designed to scramble data, while the key is used as. public key cryptography is a method of encrypting or signing data with two different keys and. Purpose Of Key Encryption.
From www.proofpoint.com
What is Encryption? Definition, Types & More Proofpoint US Purpose Of Key Encryption the encryption algorithm is simply a mathematical formula designed to scramble data, while the key is used as. the public key is typically stored on a public key infrastructure server and is used to encrypt data securely before it is sent. an encryption key is a piece of data utilized in cryptography to transform plaintext into ciphertext. Purpose Of Key Encryption.
From sectigostore.com
What Is Asymmetric Encryption & How Does It Work? InfoSec Insights Purpose Of Key Encryption encryption is the process of transforming readable plaintext into unreadable ciphertext to mask sensitive information from. the public key is typically stored on a public key infrastructure server and is used to encrypt data securely before it is sent. the encryption algorithm is simply a mathematical formula designed to scramble data, while the key is used as.. Purpose Of Key Encryption.
From www.ntirawen.com
Public Key Cryptography Decoded What is Cryptography? Ntirawen Purpose Of Key Encryption an encryption key is a piece of data utilized in cryptography to transform plaintext into ciphertext (encryption) and vice versa. the public key is typically stored on a public key infrastructure server and is used to encrypt data securely before it is sent. public key cryptography is a method of encrypting or signing data with two different. Purpose Of Key Encryption.
From www.clickssl.net
What is Public Key Encryption and How Does It Works? Purpose Of Key Encryption the public key is typically stored on a public key infrastructure server and is used to encrypt data securely before it is sent. the encryption algorithm is simply a mathematical formula designed to scramble data, while the key is used as. an encryption key is a piece of data utilized in cryptography to transform plaintext into ciphertext. Purpose Of Key Encryption.
From blog.4d.com
CryptoKey Encrypt, Decrypt, Sign, and Verify! 4D Blog Purpose Of Key Encryption an encryption key is a piece of data utilized in cryptography to transform plaintext into ciphertext (encryption) and vice versa. the public key is typically stored on a public key infrastructure server and is used to encrypt data securely before it is sent. the encryption algorithm is simply a mathematical formula designed to scramble data, while the. Purpose Of Key Encryption.
From www.kruptos2.co.uk
Commonly used Encryption Algorithms Kruptos Security Blog Purpose Of Key Encryption an encryption key is a piece of data utilized in cryptography to transform plaintext into ciphertext (encryption) and vice versa. public key cryptography is a method of encrypting or signing data with two different keys and making one of the keys, the. encryption is the process of transforming readable plaintext into unreadable ciphertext to mask sensitive information. Purpose Of Key Encryption.
From www.techicy.com
Common Key Purposes of Cryptographic Keys Techicy Purpose Of Key Encryption an encryption key is a piece of data utilized in cryptography to transform plaintext into ciphertext (encryption) and vice versa. the encryption algorithm is simply a mathematical formula designed to scramble data, while the key is used as. public key cryptography is a method of encrypting or signing data with two different keys and making one of. Purpose Of Key Encryption.
From thecscience.com
What is CRYPTOGRAPHY and its Types TheCScience Purpose Of Key Encryption the public key is typically stored on a public key infrastructure server and is used to encrypt data securely before it is sent. public key cryptography is a method of encrypting or signing data with two different keys and making one of the keys, the. encryption is the process of transforming readable plaintext into unreadable ciphertext to. Purpose Of Key Encryption.
From blog.quickapi.cloud
加密初学者指南。 Beginners Guide to Cryptography. Quick博客 Purpose Of Key Encryption an encryption key is a piece of data utilized in cryptography to transform plaintext into ciphertext (encryption) and vice versa. the public key is typically stored on a public key infrastructure server and is used to encrypt data securely before it is sent. the encryption algorithm is simply a mathematical formula designed to scramble data, while the. Purpose Of Key Encryption.
From www.epsprogramming.com
Encryption Symmetric and Asymmetric Keys Purpose Of Key Encryption public key cryptography is a method of encrypting or signing data with two different keys and making one of the keys, the. an encryption key is a piece of data utilized in cryptography to transform plaintext into ciphertext (encryption) and vice versa. encryption is the process of transforming readable plaintext into unreadable ciphertext to mask sensitive information. Purpose Of Key Encryption.
From justcryptography.com
AES and GOST Modern Symmetric Cryptography Just Cryptography Purpose Of Key Encryption the public key is typically stored on a public key infrastructure server and is used to encrypt data securely before it is sent. encryption is the process of transforming readable plaintext into unreadable ciphertext to mask sensitive information from. an encryption key is a piece of data utilized in cryptography to transform plaintext into ciphertext (encryption) and. Purpose Of Key Encryption.
From misterjasela.weebly.com
Types Of Encryption Keys misterjasela Purpose Of Key Encryption the encryption algorithm is simply a mathematical formula designed to scramble data, while the key is used as. public key cryptography is a method of encrypting or signing data with two different keys and making one of the keys, the. an encryption key is a piece of data utilized in cryptography to transform plaintext into ciphertext (encryption). Purpose Of Key Encryption.
From www.sandfield.co.nz
Cryptography 101 Sandfield Purpose Of Key Encryption the public key is typically stored on a public key infrastructure server and is used to encrypt data securely before it is sent. an encryption key is a piece of data utilized in cryptography to transform plaintext into ciphertext (encryption) and vice versa. public key cryptography is a method of encrypting or signing data with two different. Purpose Of Key Encryption.
From m2pfintech.com
Cryptographic Keys and Hardware Security Modules An IntroductionM2P Purpose Of Key Encryption the public key is typically stored on a public key infrastructure server and is used to encrypt data securely before it is sent. an encryption key is a piece of data utilized in cryptography to transform plaintext into ciphertext (encryption) and vice versa. public key cryptography is a method of encrypting or signing data with two different. Purpose Of Key Encryption.
From divyendra.com
Public Key Cryptography Basics Site Reliability Engineering Purpose Of Key Encryption encryption is the process of transforming readable plaintext into unreadable ciphertext to mask sensitive information from. public key cryptography is a method of encrypting or signing data with two different keys and making one of the keys, the. the encryption algorithm is simply a mathematical formula designed to scramble data, while the key is used as. . Purpose Of Key Encryption.
From learn.g2.com
What Does Encryption Mean and Why Is It Important? Purpose Of Key Encryption public key cryptography is a method of encrypting or signing data with two different keys and making one of the keys, the. encryption is the process of transforming readable plaintext into unreadable ciphertext to mask sensitive information from. the public key is typically stored on a public key infrastructure server and is used to encrypt data securely. Purpose Of Key Encryption.
From slideplayer.com
Cryptography An Introduction Continued… ppt download Purpose Of Key Encryption encryption is the process of transforming readable plaintext into unreadable ciphertext to mask sensitive information from. the encryption algorithm is simply a mathematical formula designed to scramble data, while the key is used as. the public key is typically stored on a public key infrastructure server and is used to encrypt data securely before it is sent.. Purpose Of Key Encryption.