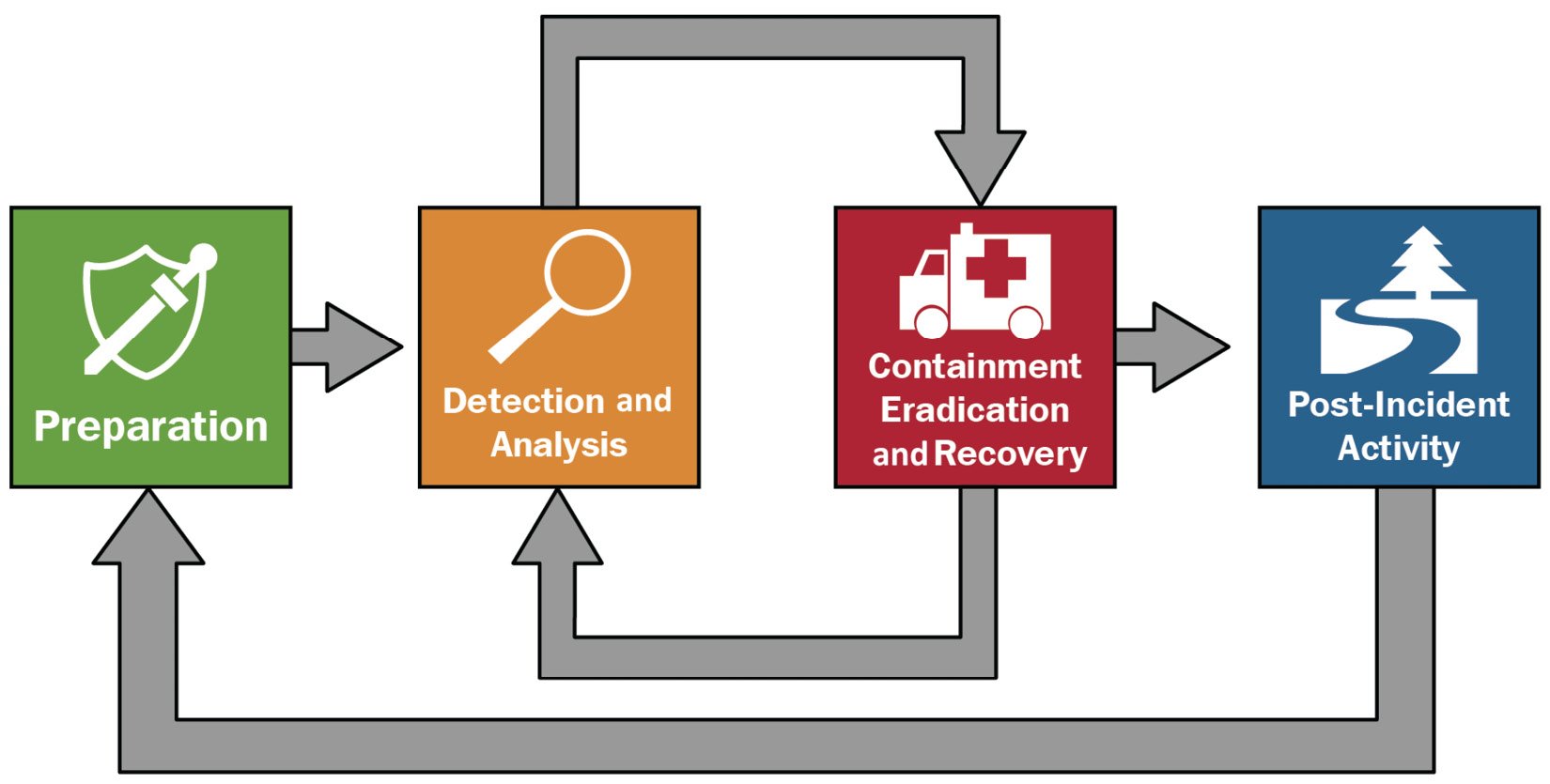
Threat Hunting Process Flow . Your practical guide to threat hunting. Threat hunting refers to the process of actively seeking potential threats and malicious activity in order to eliminate them from your network. Threat hunting is the proactive process of identifying and eliminating cyber threats before they cause damage. Here's how you can do it too. There are three phases in a proactive threat hunting process: A trigger, an investigation and a resolution. The process of proactive cyber threat hunting typically involves three steps: Includes checklist, scorecard and examples. An initial trigger phase, followed by an investigation,. It encompasses a combination of manual techniques and automated processes, such as employing code scanning tools and analyzing system logs. A threat hunting process is an active approach where security analysts, including cyber threat hunters, systematically search through network, cloud, and.
from www.packtpub.com
Threat hunting is the proactive process of identifying and eliminating cyber threats before they cause damage. Here's how you can do it too. Your practical guide to threat hunting. There are three phases in a proactive threat hunting process: The process of proactive cyber threat hunting typically involves three steps: It encompasses a combination of manual techniques and automated processes, such as employing code scanning tools and analyzing system logs. Threat hunting refers to the process of actively seeking potential threats and malicious activity in order to eliminate them from your network. An initial trigger phase, followed by an investigation,. A trigger, an investigation and a resolution. A threat hunting process is an active approach where security analysts, including cyber threat hunters, systematically search through network, cloud, and.
The Foundations of Threat Hunting Packt
Threat Hunting Process Flow Threat hunting refers to the process of actively seeking potential threats and malicious activity in order to eliminate them from your network. A threat hunting process is an active approach where security analysts, including cyber threat hunters, systematically search through network, cloud, and. There are three phases in a proactive threat hunting process: Your practical guide to threat hunting. Includes checklist, scorecard and examples. Threat hunting refers to the process of actively seeking potential threats and malicious activity in order to eliminate them from your network. A trigger, an investigation and a resolution. Threat hunting is the proactive process of identifying and eliminating cyber threats before they cause damage. The process of proactive cyber threat hunting typically involves three steps: It encompasses a combination of manual techniques and automated processes, such as employing code scanning tools and analyzing system logs. Here's how you can do it too. An initial trigger phase, followed by an investigation,.
From www.dts-solution.com
A Threat Hunt tale Threat Hunting Process Flow Threat hunting refers to the process of actively seeking potential threats and malicious activity in order to eliminate them from your network. It encompasses a combination of manual techniques and automated processes, such as employing code scanning tools and analyzing system logs. Your practical guide to threat hunting. Includes checklist, scorecard and examples. Here's how you can do it too.. Threat Hunting Process Flow.
From www.cyberproof.com
What is threat hunting? CyberProof Threat Hunting Process Flow An initial trigger phase, followed by an investigation,. Threat hunting is the proactive process of identifying and eliminating cyber threats before they cause damage. The process of proactive cyber threat hunting typically involves three steps: A threat hunting process is an active approach where security analysts, including cyber threat hunters, systematically search through network, cloud, and. There are three phases. Threat Hunting Process Flow.
From www.logpoint.com
What is Cyber Threat Hunting? A simple guide to Threat Hunting Threat Hunting Process Flow It encompasses a combination of manual techniques and automated processes, such as employing code scanning tools and analyzing system logs. An initial trigger phase, followed by an investigation,. There are three phases in a proactive threat hunting process: Here's how you can do it too. Includes checklist, scorecard and examples. The process of proactive cyber threat hunting typically involves three. Threat Hunting Process Flow.
From www.cyberdna.com.au
A Visual Guide on Cyber Threat Hunting CyberDNA Threat Hunting Process Flow Here's how you can do it too. There are three phases in a proactive threat hunting process: Your practical guide to threat hunting. Includes checklist, scorecard and examples. A trigger, an investigation and a resolution. A threat hunting process is an active approach where security analysts, including cyber threat hunters, systematically search through network, cloud, and. An initial trigger phase,. Threat Hunting Process Flow.
From www.zippyops.com
5Step Cyber Threat Hunting Process Threat Hunting Process Flow An initial trigger phase, followed by an investigation,. Threat hunting is the proactive process of identifying and eliminating cyber threats before they cause damage. Threat hunting refers to the process of actively seeking potential threats and malicious activity in order to eliminate them from your network. A trigger, an investigation and a resolution. Your practical guide to threat hunting. Here's. Threat Hunting Process Flow.
From www.dts-solution.com
The Basics of Threat Hunting Threat Hunting Process Flow The process of proactive cyber threat hunting typically involves three steps: A threat hunting process is an active approach where security analysts, including cyber threat hunters, systematically search through network, cloud, and. Includes checklist, scorecard and examples. Here's how you can do it too. Threat hunting refers to the process of actively seeking potential threats and malicious activity in order. Threat Hunting Process Flow.
From socradar.io
Step by Step Threat Hunting SOCRadar® Cyber Intelligence Inc. Threat Hunting Process Flow Threat hunting is the proactive process of identifying and eliminating cyber threats before they cause damage. Here's how you can do it too. A threat hunting process is an active approach where security analysts, including cyber threat hunters, systematically search through network, cloud, and. A trigger, an investigation and a resolution. An initial trigger phase, followed by an investigation,. There. Threat Hunting Process Flow.
From sharkstriker.com
Cyber Threat Hunting What it is, Methodologies, Types, and Examples Threat Hunting Process Flow There are three phases in a proactive threat hunting process: Threat hunting refers to the process of actively seeking potential threats and malicious activity in order to eliminate them from your network. An initial trigger phase, followed by an investigation,. A trigger, an investigation and a resolution. It encompasses a combination of manual techniques and automated processes, such as employing. Threat Hunting Process Flow.
From blog.gigamon.com
threathuntingframework_diagram01 Gigamon Blog Threat Hunting Process Flow A trigger, an investigation and a resolution. It encompasses a combination of manual techniques and automated processes, such as employing code scanning tools and analyzing system logs. Threat hunting is the proactive process of identifying and eliminating cyber threats before they cause damage. Here's how you can do it too. Threat hunting refers to the process of actively seeking potential. Threat Hunting Process Flow.
From heimdalsecurity.com
Managed Threat Hunting The Next Step from Traditional Cybersecurity Threat Hunting Process Flow There are three phases in a proactive threat hunting process: A threat hunting process is an active approach where security analysts, including cyber threat hunters, systematically search through network, cloud, and. Threat hunting refers to the process of actively seeking potential threats and malicious activity in order to eliminate them from your network. Includes checklist, scorecard and examples. It encompasses. Threat Hunting Process Flow.
From www.crowdstrike.com
What is Cyber Threat Hunting? [Proactive Guide] CrowdStrike Threat Hunting Process Flow A trigger, an investigation and a resolution. It encompasses a combination of manual techniques and automated processes, such as employing code scanning tools and analyzing system logs. The process of proactive cyber threat hunting typically involves three steps: A threat hunting process is an active approach where security analysts, including cyber threat hunters, systematically search through network, cloud, and. Your. Threat Hunting Process Flow.
From www.sangfor.com
Cyber Threat Hunting Definition, Techniques, and Solutions Threat Hunting Process Flow There are three phases in a proactive threat hunting process: Threat hunting refers to the process of actively seeking potential threats and malicious activity in order to eliminate them from your network. Your practical guide to threat hunting. A threat hunting process is an active approach where security analysts, including cyber threat hunters, systematically search through network, cloud, and. Threat. Threat Hunting Process Flow.
From www.crowdstrike.com
What is Cyber Threat Hunting? [Proactive Guide] CrowdStrike Threat Hunting Process Flow An initial trigger phase, followed by an investigation,. It encompasses a combination of manual techniques and automated processes, such as employing code scanning tools and analyzing system logs. Here's how you can do it too. Threat hunting is the proactive process of identifying and eliminating cyber threats before they cause damage. A trigger, an investigation and a resolution. There are. Threat Hunting Process Flow.
From www.bankinfosecurity.com
An Inside Look at a Level 4 Threat Hunting Program Threat Hunting Process Flow Threat hunting refers to the process of actively seeking potential threats and malicious activity in order to eliminate them from your network. The process of proactive cyber threat hunting typically involves three steps: Here's how you can do it too. Your practical guide to threat hunting. An initial trigger phase, followed by an investigation,. There are three phases in a. Threat Hunting Process Flow.
From www.researchgate.net
Threat Hunting Solution Steps Download Scientific Diagram Threat Hunting Process Flow Here's how you can do it too. Threat hunting refers to the process of actively seeking potential threats and malicious activity in order to eliminate them from your network. It encompasses a combination of manual techniques and automated processes, such as employing code scanning tools and analyzing system logs. Threat hunting is the proactive process of identifying and eliminating cyber. Threat Hunting Process Flow.
From www.cyberdna.com.au
A Visual Guide on Cyber Threat Hunting CyberDNA Threat Hunting Process Flow A threat hunting process is an active approach where security analysts, including cyber threat hunters, systematically search through network, cloud, and. Includes checklist, scorecard and examples. An initial trigger phase, followed by an investigation,. A trigger, an investigation and a resolution. There are three phases in a proactive threat hunting process: Threat hunting refers to the process of actively seeking. Threat Hunting Process Flow.
From socprime.com
Threat Hunting Maturity Model Explained With Examples SOC Prime Threat Hunting Process Flow The process of proactive cyber threat hunting typically involves three steps: Your practical guide to threat hunting. Includes checklist, scorecard and examples. An initial trigger phase, followed by an investigation,. A threat hunting process is an active approach where security analysts, including cyber threat hunters, systematically search through network, cloud, and. There are three phases in a proactive threat hunting. Threat Hunting Process Flow.
From thecyphere.com
Threat Hunting Process, Methodologies, Tools And Tips Threat Hunting Process Flow Here's how you can do it too. A threat hunting process is an active approach where security analysts, including cyber threat hunters, systematically search through network, cloud, and. A trigger, an investigation and a resolution. There are three phases in a proactive threat hunting process: An initial trigger phase, followed by an investigation,. Your practical guide to threat hunting. The. Threat Hunting Process Flow.
From www.packtpub.com
The Foundations of Threat Hunting Packt Threat Hunting Process Flow Threat hunting refers to the process of actively seeking potential threats and malicious activity in order to eliminate them from your network. It encompasses a combination of manual techniques and automated processes, such as employing code scanning tools and analyzing system logs. Includes checklist, scorecard and examples. There are three phases in a proactive threat hunting process: The process of. Threat Hunting Process Flow.
From www.slideteam.net
Cyber Threat Hunting Program With Process And Tools Presentation Threat Hunting Process Flow There are three phases in a proactive threat hunting process: Threat hunting refers to the process of actively seeking potential threats and malicious activity in order to eliminate them from your network. A trigger, an investigation and a resolution. The process of proactive cyber threat hunting typically involves three steps: It encompasses a combination of manual techniques and automated processes,. Threat Hunting Process Flow.
From gcore.com
Cyberthreat Hunting Threat Hunting Gcore Threat Hunting Process Flow The process of proactive cyber threat hunting typically involves three steps: Threat hunting refers to the process of actively seeking potential threats and malicious activity in order to eliminate them from your network. An initial trigger phase, followed by an investigation,. It encompasses a combination of manual techniques and automated processes, such as employing code scanning tools and analyzing system. Threat Hunting Process Flow.
From www.reliaquest.com
StepbyStep Process to Build a Cyber Threat Hunting Plan Threat Hunting Process Flow Includes checklist, scorecard and examples. An initial trigger phase, followed by an investigation,. The process of proactive cyber threat hunting typically involves three steps: A threat hunting process is an active approach where security analysts, including cyber threat hunters, systematically search through network, cloud, and. Here's how you can do it too. Your practical guide to threat hunting. There are. Threat Hunting Process Flow.
From proinf.com
Cyber Threat Hunting 101 Guide Methods, Tools, Techniques & Frameworks Threat Hunting Process Flow Here's how you can do it too. An initial trigger phase, followed by an investigation,. Threat hunting refers to the process of actively seeking potential threats and malicious activity in order to eliminate them from your network. The process of proactive cyber threat hunting typically involves three steps: Threat hunting is the proactive process of identifying and eliminating cyber threats. Threat Hunting Process Flow.
From blog.apnic.net
How to Threat hunting and threat intelligence APNIC Blog Threat Hunting Process Flow It encompasses a combination of manual techniques and automated processes, such as employing code scanning tools and analyzing system logs. Threat hunting refers to the process of actively seeking potential threats and malicious activity in order to eliminate them from your network. There are three phases in a proactive threat hunting process: The process of proactive cyber threat hunting typically. Threat Hunting Process Flow.
From www.blusapphire.com
The Complete Guide To Threat Hunting Threat Hunting Process Flow A trigger, an investigation and a resolution. An initial trigger phase, followed by an investigation,. Threat hunting is the proactive process of identifying and eliminating cyber threats before they cause damage. There are three phases in a proactive threat hunting process: A threat hunting process is an active approach where security analysts, including cyber threat hunters, systematically search through network,. Threat Hunting Process Flow.
From innovatecybersecurity.com
A Threat Hunting Primer Innovate Cybersecurity Threat Advisory Threat Hunting Process Flow Threat hunting is the proactive process of identifying and eliminating cyber threats before they cause damage. There are three phases in a proactive threat hunting process: Includes checklist, scorecard and examples. It encompasses a combination of manual techniques and automated processes, such as employing code scanning tools and analyzing system logs. A threat hunting process is an active approach where. Threat Hunting Process Flow.
From www.atatus.com
Threat Hunting Definition, Process, Methodologies, and More Threat Hunting Process Flow A trigger, an investigation and a resolution. Your practical guide to threat hunting. It encompasses a combination of manual techniques and automated processes, such as employing code scanning tools and analyzing system logs. Here's how you can do it too. A threat hunting process is an active approach where security analysts, including cyber threat hunters, systematically search through network, cloud,. Threat Hunting Process Flow.
From www.cyberproof.com
What is threat hunting? CyberProof Threat Hunting Process Flow A threat hunting process is an active approach where security analysts, including cyber threat hunters, systematically search through network, cloud, and. A trigger, an investigation and a resolution. Includes checklist, scorecard and examples. An initial trigger phase, followed by an investigation,. Threat hunting is the proactive process of identifying and eliminating cyber threats before they cause damage. The process of. Threat Hunting Process Flow.
From www.socinvestigation.com
Cyber Threat Hunting Proactive Intrusion Detection Security Threat Hunting Process Flow Your practical guide to threat hunting. The process of proactive cyber threat hunting typically involves three steps: Here's how you can do it too. Threat hunting refers to the process of actively seeking potential threats and malicious activity in order to eliminate them from your network. Includes checklist, scorecard and examples. A threat hunting process is an active approach where. Threat Hunting Process Flow.
From www.cyberdna.com.au
A Visual Guide on Cyber Threat Hunting CyberDNA Threat Hunting Process Flow It encompasses a combination of manual techniques and automated processes, such as employing code scanning tools and analyzing system logs. Includes checklist, scorecard and examples. A threat hunting process is an active approach where security analysts, including cyber threat hunters, systematically search through network, cloud, and. An initial trigger phase, followed by an investigation,. Threat hunting is the proactive process. Threat Hunting Process Flow.
From www.activecountermeasures.com
Tightly Defining Cyber Threat Hunting Active Countermeasures Threat Hunting Process Flow An initial trigger phase, followed by an investigation,. Your practical guide to threat hunting. A trigger, an investigation and a resolution. A threat hunting process is an active approach where security analysts, including cyber threat hunters, systematically search through network, cloud, and. It encompasses a combination of manual techniques and automated processes, such as employing code scanning tools and analyzing. Threat Hunting Process Flow.
From www.researchgate.net
Threat Hunting Process from Scratch Download Scientific Diagram Threat Hunting Process Flow A threat hunting process is an active approach where security analysts, including cyber threat hunters, systematically search through network, cloud, and. A trigger, an investigation and a resolution. Your practical guide to threat hunting. Includes checklist, scorecard and examples. An initial trigger phase, followed by an investigation,. It encompasses a combination of manual techniques and automated processes, such as employing. Threat Hunting Process Flow.
From proinf.com
Cyber Threat Hunting 101 Guide Methods, Tools, Techniques & Frameworks Threat Hunting Process Flow It encompasses a combination of manual techniques and automated processes, such as employing code scanning tools and analyzing system logs. Threat hunting is the proactive process of identifying and eliminating cyber threats before they cause damage. A trigger, an investigation and a resolution. Here's how you can do it too. Includes checklist, scorecard and examples. There are three phases in. Threat Hunting Process Flow.
From thecyphere.com
Threat Hunting Process, Methodologies, Tools And Tips Threat Hunting Process Flow Threat hunting refers to the process of actively seeking potential threats and malicious activity in order to eliminate them from your network. Here's how you can do it too. It encompasses a combination of manual techniques and automated processes, such as employing code scanning tools and analyzing system logs. The process of proactive cyber threat hunting typically involves three steps:. Threat Hunting Process Flow.
From www.slideteam.net
Five Step Process Of Cyber Threat Hunting Threat Hunting Process Flow Threat hunting refers to the process of actively seeking potential threats and malicious activity in order to eliminate them from your network. Here's how you can do it too. A trigger, an investigation and a resolution. Includes checklist, scorecard and examples. There are three phases in a proactive threat hunting process: An initial trigger phase, followed by an investigation,. It. Threat Hunting Process Flow.