Network Access Control Example . Network access control helps overburdened security groups level the playing field. What is network access control (nac)? Here's how to get started protecting your. Network access control (nac) is an approach to computer security that attempts to unify endpoint security technology (such as antivirus, host. Network control (nac) is the process of leveraging security protocols such as endpoint monitoring and identity and access management (iam) to. Network access control (nac), also known as network admission control, is the process of restricting unauthorized users and devices from. Threat monitoring and incident response. Network access control, also called network admission control, is a method to bolster the security, visibility and access management of a proprietary. Network access control (nac) is a security solution that enforces policy on devices that access networks to increase network visibility and reduce risk.
from www.juniper.net
Network access control helps overburdened security groups level the playing field. Here's how to get started protecting your. Network control (nac) is the process of leveraging security protocols such as endpoint monitoring and identity and access management (iam) to. Network access control (nac) is an approach to computer security that attempts to unify endpoint security technology (such as antivirus, host. Network access control, also called network admission control, is a method to bolster the security, visibility and access management of a proprietary. What is network access control (nac)? Network access control (nac), also known as network admission control, is the process of restricting unauthorized users and devices from. Threat monitoring and incident response. Network access control (nac) is a security solution that enforces policy on devices that access networks to increase network visibility and reduce risk.
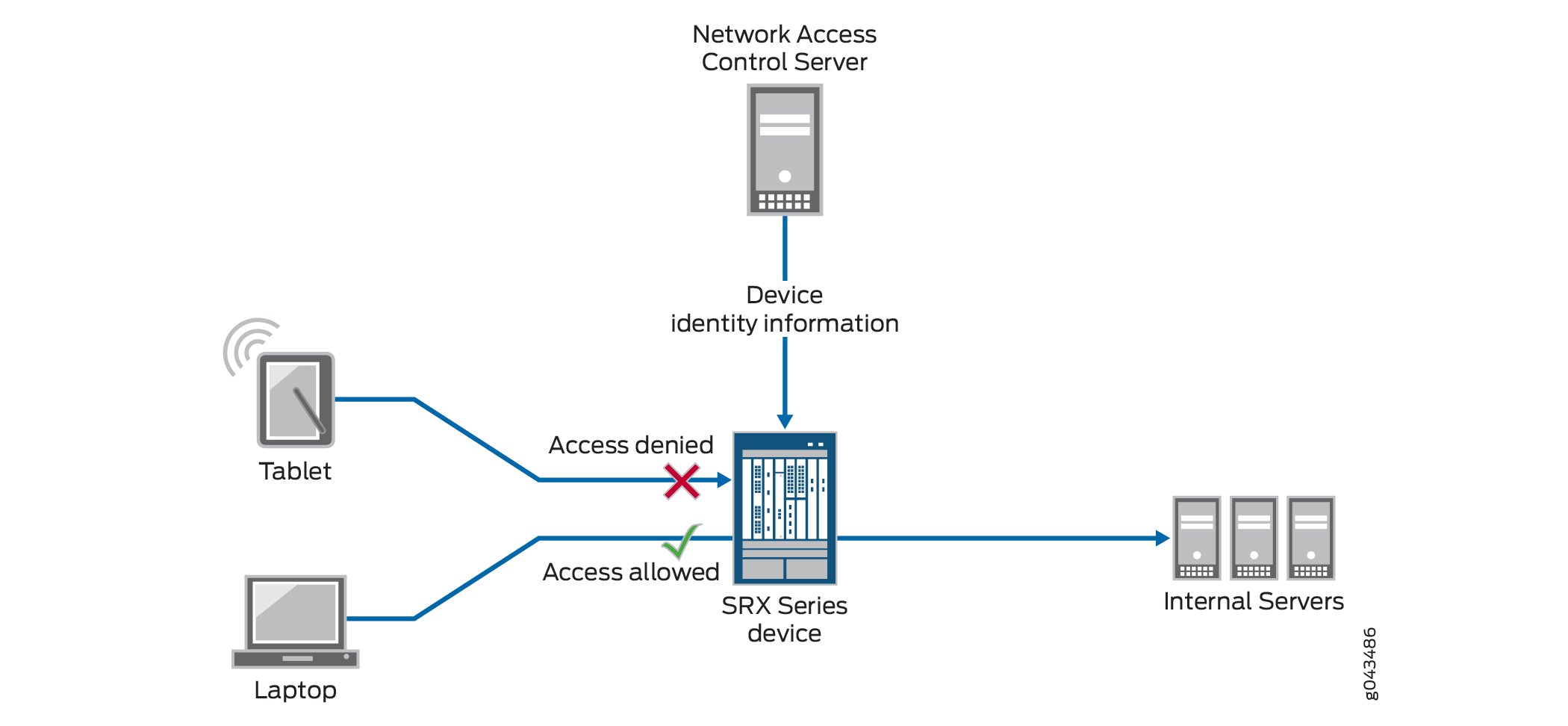
Control Network Access Using Device Identity Authentication Juniper
Network Access Control Example Network control (nac) is the process of leveraging security protocols such as endpoint monitoring and identity and access management (iam) to. Here's how to get started protecting your. What is network access control (nac)? Network control (nac) is the process of leveraging security protocols such as endpoint monitoring and identity and access management (iam) to. Network access control (nac) is an approach to computer security that attempts to unify endpoint security technology (such as antivirus, host. Threat monitoring and incident response. Network access control, also called network admission control, is a method to bolster the security, visibility and access management of a proprietary. Network access control helps overburdened security groups level the playing field. Network access control (nac), also known as network admission control, is the process of restricting unauthorized users and devices from. Network access control (nac) is a security solution that enforces policy on devices that access networks to increase network visibility and reduce risk.
From www.youtube.com
10 Network access control RADIUS YouTube Network Access Control Example Network access control helps overburdened security groups level the playing field. Threat monitoring and incident response. Network access control, also called network admission control, is a method to bolster the security, visibility and access management of a proprietary. Network access control (nac) is an approach to computer security that attempts to unify endpoint security technology (such as antivirus, host. Network. Network Access Control Example.
From www.thesecuritybuddy.com
What is Network Access Control (NAC) and how does it work? The Network Access Control Example What is network access control (nac)? Network control (nac) is the process of leveraging security protocols such as endpoint monitoring and identity and access management (iam) to. Network access control (nac) is a security solution that enforces policy on devices that access networks to increase network visibility and reduce risk. Here's how to get started protecting your. Threat monitoring and. Network Access Control Example.
From www.conceptdraw.com
Network Security Model Network Access Control Example Network access control (nac) is an approach to computer security that attempts to unify endpoint security technology (such as antivirus, host. Network control (nac) is the process of leveraging security protocols such as endpoint monitoring and identity and access management (iam) to. Network access control (nac) is a security solution that enforces policy on devices that access networks to increase. Network Access Control Example.
From sssengineeringbd.com
Access Control System with all type of Hardware and Software Solution Network Access Control Example Network access control helps overburdened security groups level the playing field. What is network access control (nac)? Threat monitoring and incident response. Network access control, also called network admission control, is a method to bolster the security, visibility and access management of a proprietary. Here's how to get started protecting your. Network access control (nac) is a security solution that. Network Access Control Example.
From getsafeandsound.com
Access Control Systems The Complete Guide for 2023 Network Access Control Example Network access control helps overburdened security groups level the playing field. Network access control, also called network admission control, is a method to bolster the security, visibility and access management of a proprietary. Network access control (nac), also known as network admission control, is the process of restricting unauthorized users and devices from. Threat monitoring and incident response. Network control. Network Access Control Example.
From tech-bridge.biz
Network Access Control TechBridge Network Access Control Example Network access control (nac), also known as network admission control, is the process of restricting unauthorized users and devices from. Threat monitoring and incident response. Network access control, also called network admission control, is a method to bolster the security, visibility and access management of a proprietary. What is network access control (nac)? Network access control (nac) is a security. Network Access Control Example.
From www.fingerprint-access-control.com
Office Building Access Control using Biometrics Fingerprint Access Network Access Control Example What is network access control (nac)? Network access control (nac), also known as network admission control, is the process of restricting unauthorized users and devices from. Network access control (nac) is a security solution that enforces policy on devices that access networks to increase network visibility and reduce risk. Network access control (nac) is an approach to computer security that. Network Access Control Example.
From gomindsight.com
Network Access Controls (NAC) And Why You Need Them A Cybersecurity Network Access Control Example Network access control (nac), also known as network admission control, is the process of restricting unauthorized users and devices from. Threat monitoring and incident response. Network access control, also called network admission control, is a method to bolster the security, visibility and access management of a proprietary. Here's how to get started protecting your. Network access control helps overburdened security. Network Access Control Example.
From www.genians.com
Introducing Zero Trust Network Access Control (ZTNAC) Genians Network Access Control Example Network access control, also called network admission control, is a method to bolster the security, visibility and access management of a proprietary. Threat monitoring and incident response. Network access control (nac) is a security solution that enforces policy on devices that access networks to increase network visibility and reduce risk. Network access control (nac) is an approach to computer security. Network Access Control Example.
From www.juniper.net
Control Network Access Using Device Identity Authentication Juniper Network Access Control Example Threat monitoring and incident response. Network access control (nac), also known as network admission control, is the process of restricting unauthorized users and devices from. Here's how to get started protecting your. Network access control, also called network admission control, is a method to bolster the security, visibility and access management of a proprietary. Network access control (nac) is a. Network Access Control Example.
From heimdalsecurity.com
What Is Network Access Control (NAC)? Network Access Control Example Network control (nac) is the process of leveraging security protocols such as endpoint monitoring and identity and access management (iam) to. Network access control, also called network admission control, is a method to bolster the security, visibility and access management of a proprietary. Threat monitoring and incident response. Network access control (nac) is a security solution that enforces policy on. Network Access Control Example.
From cyberhoot.com
Access Control (Physical and Logical) CyberHoot Network Access Control Example Here's how to get started protecting your. Network access control (nac), also known as network admission control, is the process of restricting unauthorized users and devices from. Network access control (nac) is a security solution that enforces policy on devices that access networks to increase network visibility and reduce risk. Threat monitoring and incident response. What is network access control. Network Access Control Example.
From jaycemeowcunningham.blogspot.com
What Function Describe the Uses of an Access Control List Network Access Control Example Network access control (nac) is an approach to computer security that attempts to unify endpoint security technology (such as antivirus, host. Threat monitoring and incident response. Network access control, also called network admission control, is a method to bolster the security, visibility and access management of a proprietary. Network access control (nac) is a security solution that enforces policy on. Network Access Control Example.
From guidemanualroos.z13.web.core.windows.net
Network Access Control Diagram Network Access Control Example Network access control (nac), also known as network admission control, is the process of restricting unauthorized users and devices from. Here's how to get started protecting your. Network access control (nac) is an approach to computer security that attempts to unify endpoint security technology (such as antivirus, host. Threat monitoring and incident response. What is network access control (nac)? Network. Network Access Control Example.
From www.conceptdraw.com
Network Security Network Access Control Example Network access control (nac) is a security solution that enforces policy on devices that access networks to increase network visibility and reduce risk. Network access control, also called network admission control, is a method to bolster the security, visibility and access management of a proprietary. Network access control (nac), also known as network admission control, is the process of restricting. Network Access Control Example.
From viettuans.vn
Network Access Control là gì? Ứng dụng thực tiễn của Network Access Co Network Access Control Example Network control (nac) is the process of leveraging security protocols such as endpoint monitoring and identity and access management (iam) to. Network access control (nac) is an approach to computer security that attempts to unify endpoint security technology (such as antivirus, host. Network access control (nac) is a security solution that enforces policy on devices that access networks to increase. Network Access Control Example.
From getsafeandsound.com
Access Control System An Overview Network Access Control Example Threat monitoring and incident response. Network access control, also called network admission control, is a method to bolster the security, visibility and access management of a proprietary. Network access control (nac) is an approach to computer security that attempts to unify endpoint security technology (such as antivirus, host. Network access control helps overburdened security groups level the playing field. Network. Network Access Control Example.
From ipsystems.ph
Everything You Need to Know About Network Access Control Solution Network Access Control Example Network access control, also called network admission control, is a method to bolster the security, visibility and access management of a proprietary. Here's how to get started protecting your. What is network access control (nac)? Network access control helps overburdened security groups level the playing field. Network control (nac) is the process of leveraging security protocols such as endpoint monitoring. Network Access Control Example.
From www.ibm.com
Network access control Network Access Control Example Threat monitoring and incident response. Network control (nac) is the process of leveraging security protocols such as endpoint monitoring and identity and access management (iam) to. Network access control (nac) is a security solution that enforces policy on devices that access networks to increase network visibility and reduce risk. Network access control (nac) is an approach to computer security that. Network Access Control Example.
From www.securew2.com
5 Network Access Control (NAC) Best Practices Network Access Control Example Network control (nac) is the process of leveraging security protocols such as endpoint monitoring and identity and access management (iam) to. What is network access control (nac)? Network access control (nac), also known as network admission control, is the process of restricting unauthorized users and devices from. Network access control, also called network admission control, is a method to bolster. Network Access Control Example.
From www.collidu.com
Network Access Control PowerPoint and Google Slides Template PPT Slides Network Access Control Example Network access control, also called network admission control, is a method to bolster the security, visibility and access management of a proprietary. Network access control helps overburdened security groups level the playing field. Network access control (nac) is a security solution that enforces policy on devices that access networks to increase network visibility and reduce risk. Network access control (nac),. Network Access Control Example.
From laptrinhx.com
6 Best Network Access Control Software LaptrinhX / News Network Access Control Example What is network access control (nac)? Network access control (nac) is an approach to computer security that attempts to unify endpoint security technology (such as antivirus, host. Network control (nac) is the process of leveraging security protocols such as endpoint monitoring and identity and access management (iam) to. Network access control helps overburdened security groups level the playing field. Network. Network Access Control Example.
From www.techtarget.com
What is network access control (NAC) and how does it work? Network Access Control Example Network access control (nac) is an approach to computer security that attempts to unify endpoint security technology (such as antivirus, host. Network access control (nac), also known as network admission control, is the process of restricting unauthorized users and devices from. What is network access control (nac)? Network access control helps overburdened security groups level the playing field. Network control. Network Access Control Example.
From www.slideshare.net
Network access control Network Access Control Example Network access control (nac) is an approach to computer security that attempts to unify endpoint security technology (such as antivirus, host. What is network access control (nac)? Threat monitoring and incident response. Network access control helps overburdened security groups level the playing field. Network access control (nac) is a security solution that enforces policy on devices that access networks to. Network Access Control Example.
From medium.com
Network Policy and Access Services Overview by Adroit Information Network Access Control Example Network control (nac) is the process of leveraging security protocols such as endpoint monitoring and identity and access management (iam) to. Network access control (nac) is a security solution that enforces policy on devices that access networks to increase network visibility and reduce risk. What is network access control (nac)? Threat monitoring and incident response. Here's how to get started. Network Access Control Example.
From searchcloudcomputing.techtarget.com
Secure data in the cloud with encryption and access controls Network Access Control Example Here's how to get started protecting your. What is network access control (nac)? Network access control helps overburdened security groups level the playing field. Network access control, also called network admission control, is a method to bolster the security, visibility and access management of a proprietary. Network access control (nac) is a security solution that enforces policy on devices that. Network Access Control Example.
From cie-group.com
How to design an Access Control system Network Access Control Example Here's how to get started protecting your. What is network access control (nac)? Network control (nac) is the process of leveraging security protocols such as endpoint monitoring and identity and access management (iam) to. Network access control helps overburdened security groups level the playing field. Network access control, also called network admission control, is a method to bolster the security,. Network Access Control Example.
From www.securedgenetworks.com
What is NAC? Network Access Control Explained Network Access Control Example Network control (nac) is the process of leveraging security protocols such as endpoint monitoring and identity and access management (iam) to. Here's how to get started protecting your. Network access control (nac) is a security solution that enforces policy on devices that access networks to increase network visibility and reduce risk. Threat monitoring and incident response. Network access control, also. Network Access Control Example.
From www.genians.com
Introducing Zero Trust Network Access Control (ZTNAC) Genians Network Access Control Example Network control (nac) is the process of leveraging security protocols such as endpoint monitoring and identity and access management (iam) to. Network access control (nac), also known as network admission control, is the process of restricting unauthorized users and devices from. Network access control helps overburdened security groups level the playing field. Network access control, also called network admission control,. Network Access Control Example.
From www.portnox.com
Network Access Control (NAC) by Portnox Network Access Control Example What is network access control (nac)? Network access control helps overburdened security groups level the playing field. Threat monitoring and incident response. Here's how to get started protecting your. Network access control (nac) is an approach to computer security that attempts to unify endpoint security technology (such as antivirus, host. Network access control (nac) is a security solution that enforces. Network Access Control Example.
From www.networkeducator.com
What Is Access Control List (ACL) & How It Works Network Educator Network Access Control Example Network access control (nac) is an approach to computer security that attempts to unify endpoint security technology (such as antivirus, host. What is network access control (nac)? Here's how to get started protecting your. Network access control, also called network admission control, is a method to bolster the security, visibility and access management of a proprietary. Threat monitoring and incident. Network Access Control Example.
From www.juniper.net
What is 802.1X Network Access Control (NAC)? Juniper Networks US Network Access Control Example Network access control, also called network admission control, is a method to bolster the security, visibility and access management of a proprietary. What is network access control (nac)? Network access control (nac) is an approach to computer security that attempts to unify endpoint security technology (such as antivirus, host. Threat monitoring and incident response. Here's how to get started protecting. Network Access Control Example.
From www.sketchbubble.com
Network Access Control PowerPoint and Google Slides Template PPT Slides Network Access Control Example Network access control helps overburdened security groups level the playing field. Network access control (nac), also known as network admission control, is the process of restricting unauthorized users and devices from. Network control (nac) is the process of leveraging security protocols such as endpoint monitoring and identity and access management (iam) to. Network access control (nac) is a security solution. Network Access Control Example.
From www.dts-solution.com
NAC Network Access Control in UAE , Dubai, Abu Dhabi, Bahrain, Saudi Network Access Control Example Network access control, also called network admission control, is a method to bolster the security, visibility and access management of a proprietary. What is network access control (nac)? Network access control (nac), also known as network admission control, is the process of restricting unauthorized users and devices from. Threat monitoring and incident response. Network access control (nac) is a security. Network Access Control Example.
From www.collidu.com
Network Access Control PowerPoint and Google Slides Template PPT Slides Network Access Control Example Network access control (nac) is a security solution that enforces policy on devices that access networks to increase network visibility and reduce risk. Network access control (nac), also known as network admission control, is the process of restricting unauthorized users and devices from. Here's how to get started protecting your. Threat monitoring and incident response. What is network access control. Network Access Control Example.