Network Infrastructure Vulnerabilities . These voluntary assessments assist cisa and its partners—federal, state, tribal, territorial governments and private industry—in better. Network security vulnerability protocols and testing finds security threats to the network. This guidance focuses on the design and configurations that protect against common vulnerabilities and weaknesses on existing networks. Common types of network vulnerabilities include unpatched software flaws, weak passwords, and open ports. Learn how to prevent network security threats,. To address threats to network infrastructure devices, this alert provides information on recent vectors of attack that. Guidance for securing networks continues to evolve as adversaries exploit new vulnerabilities, new security features are.
from www.enterprisenetworkingplanet.com
Guidance for securing networks continues to evolve as adversaries exploit new vulnerabilities, new security features are. To address threats to network infrastructure devices, this alert provides information on recent vectors of attack that. Learn how to prevent network security threats,. Common types of network vulnerabilities include unpatched software flaws, weak passwords, and open ports. This guidance focuses on the design and configurations that protect against common vulnerabilities and weaknesses on existing networks. Network security vulnerability protocols and testing finds security threats to the network. These voluntary assessments assist cisa and its partners—federal, state, tribal, territorial governments and private industry—in better.
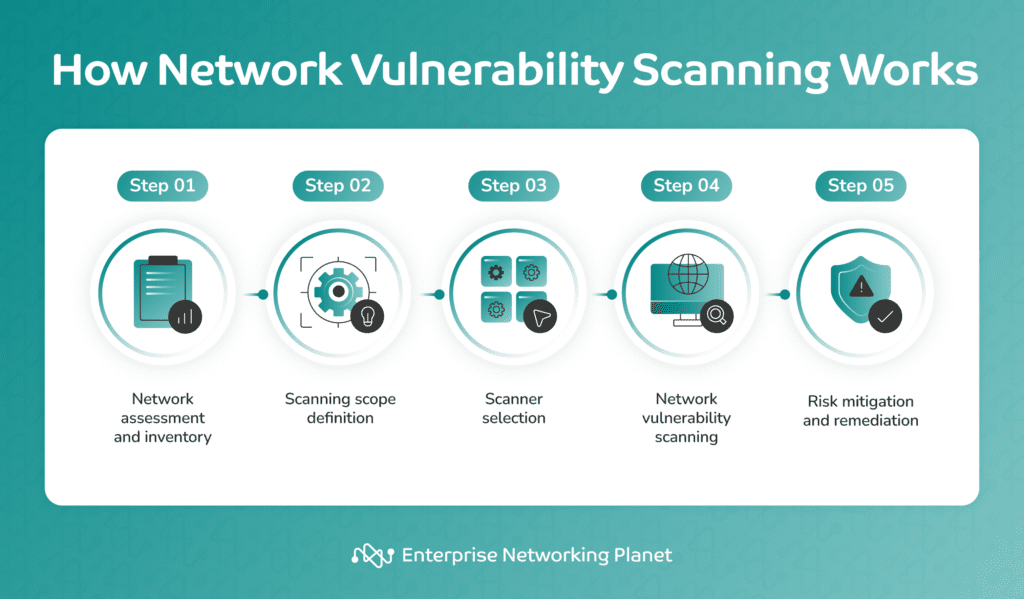
What Is Network Vulnerability Scanning? Complete Guide
Network Infrastructure Vulnerabilities To address threats to network infrastructure devices, this alert provides information on recent vectors of attack that. To address threats to network infrastructure devices, this alert provides information on recent vectors of attack that. Common types of network vulnerabilities include unpatched software flaws, weak passwords, and open ports. These voluntary assessments assist cisa and its partners—federal, state, tribal, territorial governments and private industry—in better. Network security vulnerability protocols and testing finds security threats to the network. This guidance focuses on the design and configurations that protect against common vulnerabilities and weaknesses on existing networks. Guidance for securing networks continues to evolve as adversaries exploit new vulnerabilities, new security features are. Learn how to prevent network security threats,.
From ipwithease.com
Network Vulnerabilities and the OSI Model IP With Ease Network Infrastructure Vulnerabilities Network security vulnerability protocols and testing finds security threats to the network. Guidance for securing networks continues to evolve as adversaries exploit new vulnerabilities, new security features are. Learn how to prevent network security threats,. This guidance focuses on the design and configurations that protect against common vulnerabilities and weaknesses on existing networks. These voluntary assessments assist cisa and its. Network Infrastructure Vulnerabilities.
From appcheck-ng.com
An Introduction to Infrastructure Vulnerability Scanning Network Infrastructure Vulnerabilities Guidance for securing networks continues to evolve as adversaries exploit new vulnerabilities, new security features are. Network security vulnerability protocols and testing finds security threats to the network. Learn how to prevent network security threats,. This guidance focuses on the design and configurations that protect against common vulnerabilities and weaknesses on existing networks. To address threats to network infrastructure devices,. Network Infrastructure Vulnerabilities.
From www.gkseries.com
What are some of the most common vulnerabilities that exist in a Network Infrastructure Vulnerabilities Guidance for securing networks continues to evolve as adversaries exploit new vulnerabilities, new security features are. Network security vulnerability protocols and testing finds security threats to the network. This guidance focuses on the design and configurations that protect against common vulnerabilities and weaknesses on existing networks. These voluntary assessments assist cisa and its partners—federal, state, tribal, territorial governments and private. Network Infrastructure Vulnerabilities.
From www.manageengine.com
Vulnerability Management Wan Architecture Network Infrastructure Vulnerabilities Guidance for securing networks continues to evolve as adversaries exploit new vulnerabilities, new security features are. This guidance focuses on the design and configurations that protect against common vulnerabilities and weaknesses on existing networks. Common types of network vulnerabilities include unpatched software flaws, weak passwords, and open ports. These voluntary assessments assist cisa and its partners—federal, state, tribal, territorial governments. Network Infrastructure Vulnerabilities.
From securityintelligence.com
Identify Vulnerabilities in Your IT Infrastructure, Policies and Network Infrastructure Vulnerabilities Network security vulnerability protocols and testing finds security threats to the network. Common types of network vulnerabilities include unpatched software flaws, weak passwords, and open ports. To address threats to network infrastructure devices, this alert provides information on recent vectors of attack that. These voluntary assessments assist cisa and its partners—federal, state, tribal, territorial governments and private industry—in better. This. Network Infrastructure Vulnerabilities.
From privacy108.com.au
New security obligations for Australian Critical Infrastructure Network Infrastructure Vulnerabilities To address threats to network infrastructure devices, this alert provides information on recent vectors of attack that. Common types of network vulnerabilities include unpatched software flaws, weak passwords, and open ports. This guidance focuses on the design and configurations that protect against common vulnerabilities and weaknesses on existing networks. Guidance for securing networks continues to evolve as adversaries exploit new. Network Infrastructure Vulnerabilities.
From studyhippo.com
Identify Threats and Vulnerabilities in an IT Infrastructure Essay Network Infrastructure Vulnerabilities Common types of network vulnerabilities include unpatched software flaws, weak passwords, and open ports. Learn how to prevent network security threats,. These voluntary assessments assist cisa and its partners—federal, state, tribal, territorial governments and private industry—in better. To address threats to network infrastructure devices, this alert provides information on recent vectors of attack that. This guidance focuses on the design. Network Infrastructure Vulnerabilities.
From appsecphoenix.com
Vulnerability timelines, SLA, Measurement and prioritization the how Network Infrastructure Vulnerabilities Network security vulnerability protocols and testing finds security threats to the network. Common types of network vulnerabilities include unpatched software flaws, weak passwords, and open ports. These voluntary assessments assist cisa and its partners—federal, state, tribal, territorial governments and private industry—in better. Guidance for securing networks continues to evolve as adversaries exploit new vulnerabilities, new security features are. To address. Network Infrastructure Vulnerabilities.
From www.sapphire.net
Network Vulnerability Scanning Types & Tools Sapphire Network Infrastructure Vulnerabilities Guidance for securing networks continues to evolve as adversaries exploit new vulnerabilities, new security features are. These voluntary assessments assist cisa and its partners—federal, state, tribal, territorial governments and private industry—in better. This guidance focuses on the design and configurations that protect against common vulnerabilities and weaknesses on existing networks. Common types of network vulnerabilities include unpatched software flaws, weak. Network Infrastructure Vulnerabilities.
From purplesec.us
How Often Should You Perform A Network Vulnerability Scan? Network Infrastructure Vulnerabilities Learn how to prevent network security threats,. These voluntary assessments assist cisa and its partners—federal, state, tribal, territorial governments and private industry—in better. To address threats to network infrastructure devices, this alert provides information on recent vectors of attack that. Guidance for securing networks continues to evolve as adversaries exploit new vulnerabilities, new security features are. Network security vulnerability protocols. Network Infrastructure Vulnerabilities.
From www.slideshare.net
Infrastructure Vulnerability Issues, Impacts, and Solutions with RackN Network Infrastructure Vulnerabilities This guidance focuses on the design and configurations that protect against common vulnerabilities and weaknesses on existing networks. Learn how to prevent network security threats,. To address threats to network infrastructure devices, this alert provides information on recent vectors of attack that. Network security vulnerability protocols and testing finds security threats to the network. These voluntary assessments assist cisa and. Network Infrastructure Vulnerabilities.
From boltonshield.com
Uncovering Network Vulnerabilities How Cyber Security Enhances Network Infrastructure Vulnerabilities Common types of network vulnerabilities include unpatched software flaws, weak passwords, and open ports. This guidance focuses on the design and configurations that protect against common vulnerabilities and weaknesses on existing networks. To address threats to network infrastructure devices, this alert provides information on recent vectors of attack that. Learn how to prevent network security threats,. These voluntary assessments assist. Network Infrastructure Vulnerabilities.
From www.researchgate.net
(PDF) Assessing Network Infrastructure Vulnerabilities to Physical Network Infrastructure Vulnerabilities Common types of network vulnerabilities include unpatched software flaws, weak passwords, and open ports. This guidance focuses on the design and configurations that protect against common vulnerabilities and weaknesses on existing networks. These voluntary assessments assist cisa and its partners—federal, state, tribal, territorial governments and private industry—in better. Learn how to prevent network security threats,. Guidance for securing networks continues. Network Infrastructure Vulnerabilities.
From www.ceotodaymagazine.com
Do Faster Patch Releases Help Security? Network Infrastructure Vulnerabilities Guidance for securing networks continues to evolve as adversaries exploit new vulnerabilities, new security features are. This guidance focuses on the design and configurations that protect against common vulnerabilities and weaknesses on existing networks. These voluntary assessments assist cisa and its partners—federal, state, tribal, territorial governments and private industry—in better. Network security vulnerability protocols and testing finds security threats to. Network Infrastructure Vulnerabilities.
From querensics.com
Threats found in LANT0WAN Domain in Typical IT Infrasstructure The Network Infrastructure Vulnerabilities Network security vulnerability protocols and testing finds security threats to the network. Guidance for securing networks continues to evolve as adversaries exploit new vulnerabilities, new security features are. Learn how to prevent network security threats,. This guidance focuses on the design and configurations that protect against common vulnerabilities and weaknesses on existing networks. Common types of network vulnerabilities include unpatched. Network Infrastructure Vulnerabilities.
From reciprocity.com
What is a Network Vulnerability Assessment? — ZenGRC Network Infrastructure Vulnerabilities Network security vulnerability protocols and testing finds security threats to the network. Learn how to prevent network security threats,. Common types of network vulnerabilities include unpatched software flaws, weak passwords, and open ports. These voluntary assessments assist cisa and its partners—federal, state, tribal, territorial governments and private industry—in better. This guidance focuses on the design and configurations that protect against. Network Infrastructure Vulnerabilities.
From www.infosectrain.com
Common Security Attacks in the OSI Layer Model Network Infrastructure Vulnerabilities Network security vulnerability protocols and testing finds security threats to the network. To address threats to network infrastructure devices, this alert provides information on recent vectors of attack that. Learn how to prevent network security threats,. Common types of network vulnerabilities include unpatched software flaws, weak passwords, and open ports. These voluntary assessments assist cisa and its partners—federal, state, tribal,. Network Infrastructure Vulnerabilities.
From www.conceptdraw.com
How to Create a Network Security Diagram Using ConceptDraw PRO Network Infrastructure Vulnerabilities These voluntary assessments assist cisa and its partners—federal, state, tribal, territorial governments and private industry—in better. This guidance focuses on the design and configurations that protect against common vulnerabilities and weaknesses on existing networks. Network security vulnerability protocols and testing finds security threats to the network. Guidance for securing networks continues to evolve as adversaries exploit new vulnerabilities, new security. Network Infrastructure Vulnerabilities.
From flatworldknowledge.lardbucket.org
Where Are Vulnerabilities? Understanding the Weaknesses Network Infrastructure Vulnerabilities Common types of network vulnerabilities include unpatched software flaws, weak passwords, and open ports. Learn how to prevent network security threats,. To address threats to network infrastructure devices, this alert provides information on recent vectors of attack that. Network security vulnerability protocols and testing finds security threats to the network. Guidance for securing networks continues to evolve as adversaries exploit. Network Infrastructure Vulnerabilities.
From hub.frost.com
Vulnerability Management Keystone of Cybersecurity Infrastructure Network Infrastructure Vulnerabilities Common types of network vulnerabilities include unpatched software flaws, weak passwords, and open ports. To address threats to network infrastructure devices, this alert provides information on recent vectors of attack that. Network security vulnerability protocols and testing finds security threats to the network. These voluntary assessments assist cisa and its partners—federal, state, tribal, territorial governments and private industry—in better. Guidance. Network Infrastructure Vulnerabilities.
From www.manageengine.com
Vulnerability Assessment Tools & Checklists ManageEngine Network Infrastructure Vulnerabilities Network security vulnerability protocols and testing finds security threats to the network. Common types of network vulnerabilities include unpatched software flaws, weak passwords, and open ports. Guidance for securing networks continues to evolve as adversaries exploit new vulnerabilities, new security features are. Learn how to prevent network security threats,. To address threats to network infrastructure devices, this alert provides information. Network Infrastructure Vulnerabilities.
From www.gao.gov
Protecting our Critical Infrastructure U.S. GAO Network Infrastructure Vulnerabilities Learn how to prevent network security threats,. Guidance for securing networks continues to evolve as adversaries exploit new vulnerabilities, new security features are. Common types of network vulnerabilities include unpatched software flaws, weak passwords, and open ports. These voluntary assessments assist cisa and its partners—federal, state, tribal, territorial governments and private industry—in better. This guidance focuses on the design and. Network Infrastructure Vulnerabilities.
From www.enterprisenetworkingplanet.com
What Is Network Vulnerability Scanning? Complete Guide Network Infrastructure Vulnerabilities To address threats to network infrastructure devices, this alert provides information on recent vectors of attack that. Common types of network vulnerabilities include unpatched software flaws, weak passwords, and open ports. Guidance for securing networks continues to evolve as adversaries exploit new vulnerabilities, new security features are. These voluntary assessments assist cisa and its partners—federal, state, tribal, territorial governments and. Network Infrastructure Vulnerabilities.
From amsat.pk
An Overview of Infrastructure Vulnerability Management Amsat Network Infrastructure Vulnerabilities Learn how to prevent network security threats,. To address threats to network infrastructure devices, this alert provides information on recent vectors of attack that. Common types of network vulnerabilities include unpatched software flaws, weak passwords, and open ports. This guidance focuses on the design and configurations that protect against common vulnerabilities and weaknesses on existing networks. These voluntary assessments assist. Network Infrastructure Vulnerabilities.
From blog.radware.com
Network Security in an AppDriven World Radware Blog Network Infrastructure Vulnerabilities Learn how to prevent network security threats,. This guidance focuses on the design and configurations that protect against common vulnerabilities and weaknesses on existing networks. Network security vulnerability protocols and testing finds security threats to the network. Common types of network vulnerabilities include unpatched software flaws, weak passwords, and open ports. To address threats to network infrastructure devices, this alert. Network Infrastructure Vulnerabilities.
From www.scribd.com
Network Infrastructure Vulnerabilities PDF Malware Computer Virus Network Infrastructure Vulnerabilities These voluntary assessments assist cisa and its partners—federal, state, tribal, territorial governments and private industry—in better. Common types of network vulnerabilities include unpatched software flaws, weak passwords, and open ports. This guidance focuses on the design and configurations that protect against common vulnerabilities and weaknesses on existing networks. To address threats to network infrastructure devices, this alert provides information on. Network Infrastructure Vulnerabilities.
From cip.gmu.edu
Understanding Physical Infrastructure Vulnerabilities Center Network Infrastructure Vulnerabilities This guidance focuses on the design and configurations that protect against common vulnerabilities and weaknesses on existing networks. These voluntary assessments assist cisa and its partners—federal, state, tribal, territorial governments and private industry—in better. To address threats to network infrastructure devices, this alert provides information on recent vectors of attack that. Network security vulnerability protocols and testing finds security threats. Network Infrastructure Vulnerabilities.
From www.slideserve.com
PPT Network Vulnerability Scanning PowerPoint Presentation, free Network Infrastructure Vulnerabilities Common types of network vulnerabilities include unpatched software flaws, weak passwords, and open ports. To address threats to network infrastructure devices, this alert provides information on recent vectors of attack that. These voluntary assessments assist cisa and its partners—federal, state, tribal, territorial governments and private industry—in better. This guidance focuses on the design and configurations that protect against common vulnerabilities. Network Infrastructure Vulnerabilities.
From purplesec.us
How To Perform A Network Vulnerability Assessment (With Examples Network Infrastructure Vulnerabilities Common types of network vulnerabilities include unpatched software flaws, weak passwords, and open ports. This guidance focuses on the design and configurations that protect against common vulnerabilities and weaknesses on existing networks. Learn how to prevent network security threats,. To address threats to network infrastructure devices, this alert provides information on recent vectors of attack that. Network security vulnerability protocols. Network Infrastructure Vulnerabilities.
From www.cipherex.com
Network Infrastructure Hardening Definition and Benefits Network Infrastructure Vulnerabilities Network security vulnerability protocols and testing finds security threats to the network. Common types of network vulnerabilities include unpatched software flaws, weak passwords, and open ports. These voluntary assessments assist cisa and its partners—federal, state, tribal, territorial governments and private industry—in better. This guidance focuses on the design and configurations that protect against common vulnerabilities and weaknesses on existing networks.. Network Infrastructure Vulnerabilities.
From appcheck-ng.com
An Introduction to Infrastructure Vulnerability Scanning AppCheck Network Infrastructure Vulnerabilities Common types of network vulnerabilities include unpatched software flaws, weak passwords, and open ports. Network security vulnerability protocols and testing finds security threats to the network. Guidance for securing networks continues to evolve as adversaries exploit new vulnerabilities, new security features are. This guidance focuses on the design and configurations that protect against common vulnerabilities and weaknesses on existing networks.. Network Infrastructure Vulnerabilities.
From www.sapphire.net
Network Vulnerability Scanning Types & Tools Sapphire Network Infrastructure Vulnerabilities These voluntary assessments assist cisa and its partners—federal, state, tribal, territorial governments and private industry—in better. To address threats to network infrastructure devices, this alert provides information on recent vectors of attack that. This guidance focuses on the design and configurations that protect against common vulnerabilities and weaknesses on existing networks. Guidance for securing networks continues to evolve as adversaries. Network Infrastructure Vulnerabilities.
From ocd-tech.com
Critical Infrastructure Vulnerabilities Firewall Misconfiguration Network Infrastructure Vulnerabilities To address threats to network infrastructure devices, this alert provides information on recent vectors of attack that. Network security vulnerability protocols and testing finds security threats to the network. Learn how to prevent network security threats,. This guidance focuses on the design and configurations that protect against common vulnerabilities and weaknesses on existing networks. These voluntary assessments assist cisa and. Network Infrastructure Vulnerabilities.
From www.lanworks.com
Vulnerability Assessment Lanworks Network Infrastructure Vulnerabilities Learn how to prevent network security threats,. To address threats to network infrastructure devices, this alert provides information on recent vectors of attack that. Guidance for securing networks continues to evolve as adversaries exploit new vulnerabilities, new security features are. These voluntary assessments assist cisa and its partners—federal, state, tribal, territorial governments and private industry—in better. Network security vulnerability protocols. Network Infrastructure Vulnerabilities.
From www.slideserve.com
PPT Network Protocols and Vulnerabilities PowerPoint Presentation Network Infrastructure Vulnerabilities These voluntary assessments assist cisa and its partners—federal, state, tribal, territorial governments and private industry—in better. Network security vulnerability protocols and testing finds security threats to the network. To address threats to network infrastructure devices, this alert provides information on recent vectors of attack that. Common types of network vulnerabilities include unpatched software flaws, weak passwords, and open ports. Guidance. Network Infrastructure Vulnerabilities.