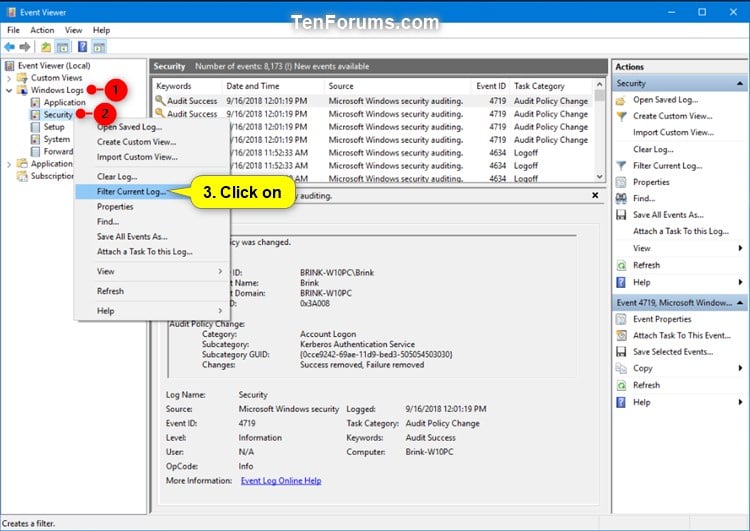
Windows Event Viewer Ids . Here is a list of the most common / useful windows event ids of active directory and other useful event ids of windows servers. Filter the windows event logs: Which event ids should you watch? You can also list every event id available for all providers on your system doing something like this: These are the most important. In the following table, the current windows event id column lists the event id as it is implemented in versions of windows and. Once the logs are imported, filter the logs for the specific event ids or event sources that you. Monitoring windows 10 event logs is one of the best ways to detect malicious activity on your network. If you are not able to use a siem, you can generate alerts by attaching tasks to custom views in event viewer. %2 instance(s) of event id %1 occurred. Look out for ntlm logon type 3 event ids 4624 (failure) and 4625 (success). 6406 %1 registered to windows firewall to control filtering for the.
from www.tenforums.com
If you are not able to use a siem, you can generate alerts by attaching tasks to custom views in event viewer. Monitoring windows 10 event logs is one of the best ways to detect malicious activity on your network. Here is a list of the most common / useful windows event ids of active directory and other useful event ids of windows servers. Filter the windows event logs: These are the most important. 6406 %1 registered to windows firewall to control filtering for the. Look out for ntlm logon type 3 event ids 4624 (failure) and 4625 (success). %2 instance(s) of event id %1 occurred. Which event ids should you watch? In the following table, the current windows event id column lists the event id as it is implemented in versions of windows and.
Read Logoff and Sign Out Logs in Event Viewer in Windows Tutorials
Windows Event Viewer Ids Monitoring windows 10 event logs is one of the best ways to detect malicious activity on your network. If you are not able to use a siem, you can generate alerts by attaching tasks to custom views in event viewer. Look out for ntlm logon type 3 event ids 4624 (failure) and 4625 (success). Which event ids should you watch? Filter the windows event logs: In the following table, the current windows event id column lists the event id as it is implemented in versions of windows and. %2 instance(s) of event id %1 occurred. 6406 %1 registered to windows firewall to control filtering for the. Monitoring windows 10 event logs is one of the best ways to detect malicious activity on your network. You can also list every event id available for all providers on your system doing something like this: Here is a list of the most common / useful windows event ids of active directory and other useful event ids of windows servers. These are the most important. Once the logs are imported, filter the logs for the specific event ids or event sources that you.
From www.tenforums.com
Read Logoff and Sign Out Logs in Event Viewer in Windows Tutorials Windows Event Viewer Ids Look out for ntlm logon type 3 event ids 4624 (failure) and 4625 (success). These are the most important. You can also list every event id available for all providers on your system doing something like this: Here is a list of the most common / useful windows event ids of active directory and other useful event ids of windows. Windows Event Viewer Ids.
From techsbucket.com
TechsBucket Windows Security Event Log IDs Windows Event Viewer Ids Look out for ntlm logon type 3 event ids 4624 (failure) and 4625 (success). You can also list every event id available for all providers on your system doing something like this: In the following table, the current windows event id column lists the event id as it is implemented in versions of windows and. Which event ids should you. Windows Event Viewer Ids.
From www.xda-developers.com
How to use Event Viewer to check for errors on Windows 11 Windows Event Viewer Ids Which event ids should you watch? Once the logs are imported, filter the logs for the specific event ids or event sources that you. Look out for ntlm logon type 3 event ids 4624 (failure) and 4625 (success). 6406 %1 registered to windows firewall to control filtering for the. Filter the windows event logs: If you are not able to. Windows Event Viewer Ids.
From www.reviversoft.com
What is Event Viewer and what information does it tell me? Windows Event Viewer Ids These are the most important. In the following table, the current windows event id column lists the event id as it is implemented in versions of windows and. Monitoring windows 10 event logs is one of the best ways to detect malicious activity on your network. You can also list every event id available for all providers on your system. Windows Event Viewer Ids.
From www.windowscentral.com
How to use Event Viewer on Windows 10 Windows Central Windows Event Viewer Ids Here is a list of the most common / useful windows event ids of active directory and other useful event ids of windows servers. Which event ids should you watch? If you are not able to use a siem, you can generate alerts by attaching tasks to custom views in event viewer. These are the most important. Monitoring windows 10. Windows Event Viewer Ids.
From www.windowserrorhelp.com
The Event Viewer Windows Error Help Windows Event Viewer Ids Monitoring windows 10 event logs is one of the best ways to detect malicious activity on your network. In the following table, the current windows event id column lists the event id as it is implemented in versions of windows and. 6406 %1 registered to windows firewall to control filtering for the. Which event ids should you watch? Filter the. Windows Event Viewer Ids.
From www.tenforums.com
Read Shutdown Logs in Event Viewer in Windows Tutorials Windows Event Viewer Ids %2 instance(s) of event id %1 occurred. If you are not able to use a siem, you can generate alerts by attaching tasks to custom views in event viewer. Filter the windows event logs: In the following table, the current windows event id column lists the event id as it is implemented in versions of windows and. You can also. Windows Event Viewer Ids.
From www.freecodecamp.org
Event Viewer How to Access the Windows 10 Activity Log Windows Event Viewer Ids These are the most important. In the following table, the current windows event id column lists the event id as it is implemented in versions of windows and. If you are not able to use a siem, you can generate alerts by attaching tasks to custom views in event viewer. Which event ids should you watch? Monitoring windows 10 event. Windows Event Viewer Ids.
From www.lifewire.com
How to Use Event Viewer in Windows 10 Windows Event Viewer Ids These are the most important. Which event ids should you watch? You can also list every event id available for all providers on your system doing something like this: %2 instance(s) of event id %1 occurred. Here is a list of the most common / useful windows event ids of active directory and other useful event ids of windows servers.. Windows Event Viewer Ids.
From superuser.com
windows 10 How do I locate the actual log and disable events by event Windows Event Viewer Ids If you are not able to use a siem, you can generate alerts by attaching tasks to custom views in event viewer. Once the logs are imported, filter the logs for the specific event ids or event sources that you. In the following table, the current windows event id column lists the event id as it is implemented in versions. Windows Event Viewer Ids.
From www.digitalcitizen.life
How to work with the Event Viewer in Windows Digital Citizen Windows Event Viewer Ids You can also list every event id available for all providers on your system doing something like this: %2 instance(s) of event id %1 occurred. These are the most important. In the following table, the current windows event id column lists the event id as it is implemented in versions of windows and. If you are not able to use. Windows Event Viewer Ids.
From www.terminalworks.com
Terminalworks Blog How to Use Windows Event Viewer Effectively Windows Event Viewer Ids These are the most important. If you are not able to use a siem, you can generate alerts by attaching tasks to custom views in event viewer. You can also list every event id available for all providers on your system doing something like this: Filter the windows event logs: Once the logs are imported, filter the logs for the. Windows Event Viewer Ids.
From davescomputertips.com
Windows 10 Quick Tips Event Viewer Daves Computer Tips Windows Event Viewer Ids You can also list every event id available for all providers on your system doing something like this: If you are not able to use a siem, you can generate alerts by attaching tasks to custom views in event viewer. Once the logs are imported, filter the logs for the specific event ids or event sources that you. Monitoring windows. Windows Event Viewer Ids.
From www.coretechnologies.com
How to use the Event Viewer to troubleshoot Windows Services The Core Windows Event Viewer Ids 6406 %1 registered to windows firewall to control filtering for the. Filter the windows event logs: Monitoring windows 10 event logs is one of the best ways to detect malicious activity on your network. %2 instance(s) of event id %1 occurred. In the following table, the current windows event id column lists the event id as it is implemented in. Windows Event Viewer Ids.
From www.windowscentral.com
How to use Event Viewer on Windows 10 Windows Central Windows Event Viewer Ids Once the logs are imported, filter the logs for the specific event ids or event sources that you. %2 instance(s) of event id %1 occurred. These are the most important. Which event ids should you watch? If you are not able to use a siem, you can generate alerts by attaching tasks to custom views in event viewer. You can. Windows Event Viewer Ids.
From www.windowscentral.com
How to use Event Viewer on Windows 10 Windows Central Windows Event Viewer Ids If you are not able to use a siem, you can generate alerts by attaching tasks to custom views in event viewer. Here is a list of the most common / useful windows event ids of active directory and other useful event ids of windows servers. In the following table, the current windows event id column lists the event id. Windows Event Viewer Ids.
From www.faqforge.com
What is Event Viewer and How to Use it in Windows 10 Windows Event Viewer Ids Which event ids should you watch? Here is a list of the most common / useful windows event ids of active directory and other useful event ids of windows servers. In the following table, the current windows event id column lists the event id as it is implemented in versions of windows and. You can also list every event id. Windows Event Viewer Ids.
From support.industry.siemens.com
SIOS Windows Event Viewer Ids These are the most important. Once the logs are imported, filter the logs for the specific event ids or event sources that you. If you are not able to use a siem, you can generate alerts by attaching tasks to custom views in event viewer. Look out for ntlm logon type 3 event ids 4624 (failure) and 4625 (success). Filter. Windows Event Viewer Ids.
From www.windowscentral.com
How to get started with Event Viewer on Windows 11 Windows Central Windows Event Viewer Ids In the following table, the current windows event id column lists the event id as it is implemented in versions of windows and. These are the most important. 6406 %1 registered to windows firewall to control filtering for the. Look out for ntlm logon type 3 event ids 4624 (failure) and 4625 (success). %2 instance(s) of event id %1 occurred.. Windows Event Viewer Ids.
From grandbrown.weebly.com
Microsoft Windows Event Id List grandbrown Windows Event Viewer Ids Look out for ntlm logon type 3 event ids 4624 (failure) and 4625 (success). Filter the windows event logs: Monitoring windows 10 event logs is one of the best ways to detect malicious activity on your network. Which event ids should you watch? These are the most important. %2 instance(s) of event id %1 occurred. Here is a list of. Windows Event Viewer Ids.
From www.beyondtrust.com
Important Windows Event IDs Which Events You Should… BeyondTrust Windows Event Viewer Ids Look out for ntlm logon type 3 event ids 4624 (failure) and 4625 (success). In the following table, the current windows event id column lists the event id as it is implemented in versions of windows and. Filter the windows event logs: You can also list every event id available for all providers on your system doing something like this:. Windows Event Viewer Ids.
From www.thetechedvocate.org
What Is the Windows Event Viewer, and How Is It Useful? The Tech Edvocate Windows Event Viewer Ids If you are not able to use a siem, you can generate alerts by attaching tasks to custom views in event viewer. Monitoring windows 10 event logs is one of the best ways to detect malicious activity on your network. You can also list every event id available for all providers on your system doing something like this: %2 instance(s). Windows Event Viewer Ids.
From mysupport.razer.com
How to export Windows Event Logs Windows Event Viewer Ids You can also list every event id available for all providers on your system doing something like this: Monitoring windows 10 event logs is one of the best ways to detect malicious activity on your network. Here is a list of the most common / useful windows event ids of active directory and other useful event ids of windows servers.. Windows Event Viewer Ids.
From www.howtogeek.com
Look Up Event IDs from the Event Viewer Using a Free Tool Windows Event Viewer Ids Monitoring windows 10 event logs is one of the best ways to detect malicious activity on your network. These are the most important. Here is a list of the most common / useful windows event ids of active directory and other useful event ids of windows servers. Look out for ntlm logon type 3 event ids 4624 (failure) and 4625. Windows Event Viewer Ids.
From www.itexperience.net
Windows Event Viewer in Windows 10 How to use it correctly Windows Event Viewer Ids 6406 %1 registered to windows firewall to control filtering for the. Filter the windows event logs: %2 instance(s) of event id %1 occurred. Which event ids should you watch? Once the logs are imported, filter the logs for the specific event ids or event sources that you. Look out for ntlm logon type 3 event ids 4624 (failure) and 4625. Windows Event Viewer Ids.
From www.windowscentral.com
How to use Event Viewer on Windows 10 Windows Central Windows Event Viewer Ids Which event ids should you watch? Filter the windows event logs: Once the logs are imported, filter the logs for the specific event ids or event sources that you. Monitoring windows 10 event logs is one of the best ways to detect malicious activity on your network. You can also list every event id available for all providers on your. Windows Event Viewer Ids.
From www.anoopcnair.com
Various Critical Windows 11 Event ID List HTMD Blog Windows Event Viewer Ids 6406 %1 registered to windows firewall to control filtering for the. If you are not able to use a siem, you can generate alerts by attaching tasks to custom views in event viewer. Look out for ntlm logon type 3 event ids 4624 (failure) and 4625 (success). In the following table, the current windows event id column lists the event. Windows Event Viewer Ids.
From www.minitool.com
[Graphic Guide] How to Open Windows 11 Event Viewer in 7 Methods Windows Event Viewer Ids You can also list every event id available for all providers on your system doing something like this: Here is a list of the most common / useful windows event ids of active directory and other useful event ids of windows servers. In the following table, the current windows event id column lists the event id as it is implemented. Windows Event Viewer Ids.
From howpchub.com
Windows Event ID 100 in the event log HowPChub Windows Event Viewer Ids Once the logs are imported, filter the logs for the specific event ids or event sources that you. Here is a list of the most common / useful windows event ids of active directory and other useful event ids of windows servers. These are the most important. %2 instance(s) of event id %1 occurred. 6406 %1 registered to windows firewall. Windows Event Viewer Ids.
From www.freecodecamp.org
Event Viewer How to Access the Windows 10 Activity Log Windows Event Viewer Ids These are the most important. Here is a list of the most common / useful windows event ids of active directory and other useful event ids of windows servers. Monitoring windows 10 event logs is one of the best ways to detect malicious activity on your network. In the following table, the current windows event id column lists the event. Windows Event Viewer Ids.
From www.esystool.com
How to Track file deletions and permission changes on Windows file Windows Event Viewer Ids If you are not able to use a siem, you can generate alerts by attaching tasks to custom views in event viewer. Which event ids should you watch? These are the most important. Filter the windows event logs: You can also list every event id available for all providers on your system doing something like this: Here is a list. Windows Event Viewer Ids.
From www.windowscentral.com
How to use Event Viewer on Windows 10 Windows Central Windows Event Viewer Ids You can also list every event id available for all providers on your system doing something like this: Monitoring windows 10 event logs is one of the best ways to detect malicious activity on your network. These are the most important. Which event ids should you watch? If you are not able to use a siem, you can generate alerts. Windows Event Viewer Ids.
From forensafe.com
Windows Event Logs Windows Event Viewer Ids Which event ids should you watch? 6406 %1 registered to windows firewall to control filtering for the. %2 instance(s) of event id %1 occurred. Here is a list of the most common / useful windows event ids of active directory and other useful event ids of windows servers. Look out for ntlm logon type 3 event ids 4624 (failure) and. Windows Event Viewer Ids.
From www.manageengine.com
What is Windows Event Log A complete guide from ADAudit Plus Windows Event Viewer Ids %2 instance(s) of event id %1 occurred. These are the most important. 6406 %1 registered to windows firewall to control filtering for the. In the following table, the current windows event id column lists the event id as it is implemented in versions of windows and. Once the logs are imported, filter the logs for the specific event ids or. Windows Event Viewer Ids.
From www.tenforums.com
Read Shutdown Logs in Event Viewer in Windows Tutorials Windows Event Viewer Ids 6406 %1 registered to windows firewall to control filtering for the. Monitoring windows 10 event logs is one of the best ways to detect malicious activity on your network. Once the logs are imported, filter the logs for the specific event ids or event sources that you. You can also list every event id available for all providers on your. Windows Event Viewer Ids.