Transmission Security Examples . Idirect has provided enhanced transmission security (transec) capabilities within our evolution defense software. Information technology organizations across all. Prevents the interception or disruption of any transmissions occurring over a communications network. Transmission security • transmission security standard “implement technical security measures to guard against unauthorized access to electronic protected health information. Transmission security (transec) is the process of securing data transmissions from being infiltrated, exploited or intercepted.
from www.educba.com
Idirect has provided enhanced transmission security (transec) capabilities within our evolution defense software. Transmission security • transmission security standard “implement technical security measures to guard against unauthorized access to electronic protected health information. Prevents the interception or disruption of any transmissions occurring over a communications network. Information technology organizations across all. Transmission security (transec) is the process of securing data transmissions from being infiltrated, exploited or intercepted.
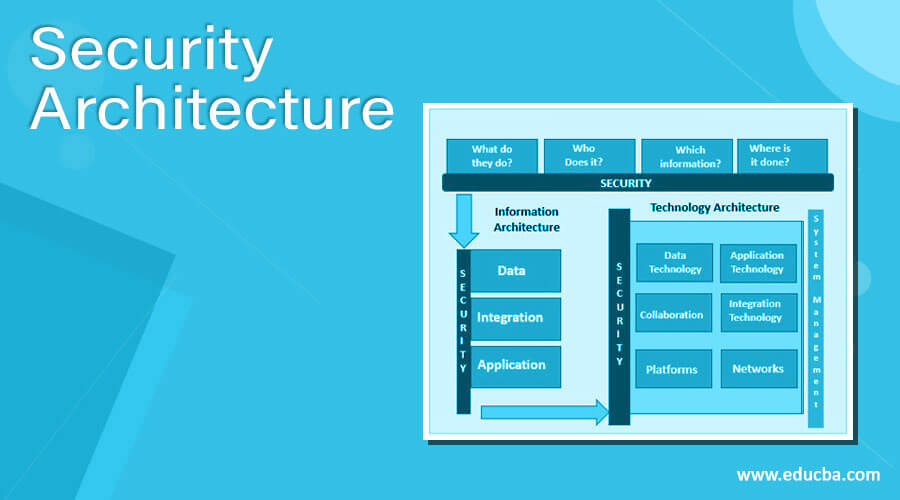
Security Architecture Components of Security Architecture
Transmission Security Examples Idirect has provided enhanced transmission security (transec) capabilities within our evolution defense software. Information technology organizations across all. Idirect has provided enhanced transmission security (transec) capabilities within our evolution defense software. Transmission security (transec) is the process of securing data transmissions from being infiltrated, exploited or intercepted. Prevents the interception or disruption of any transmissions occurring over a communications network. Transmission security • transmission security standard “implement technical security measures to guard against unauthorized access to electronic protected health information.
From www.freepik.com
Premium AI Image Absolute Data Transmission Security Achieved with Transmission Security Examples Transmission security (transec) is the process of securing data transmissions from being infiltrated, exploited or intercepted. Information technology organizations across all. Transmission security • transmission security standard “implement technical security measures to guard against unauthorized access to electronic protected health information. Idirect has provided enhanced transmission security (transec) capabilities within our evolution defense software. Prevents the interception or disruption of. Transmission Security Examples.
From cpanell.niloblog.com
Automatic (secure) transmission taking the pain out of origin Transmission Security Examples Prevents the interception or disruption of any transmissions occurring over a communications network. Transmission security (transec) is the process of securing data transmissions from being infiltrated, exploited or intercepted. Transmission security • transmission security standard “implement technical security measures to guard against unauthorized access to electronic protected health information. Idirect has provided enhanced transmission security (transec) capabilities within our evolution. Transmission Security Examples.
From www.vecteezy.com
Data transmission security 5647907 Vector Art at Vecteezy Transmission Security Examples Idirect has provided enhanced transmission security (transec) capabilities within our evolution defense software. Transmission security • transmission security standard “implement technical security measures to guard against unauthorized access to electronic protected health information. Prevents the interception or disruption of any transmissions occurring over a communications network. Information technology organizations across all. Transmission security (transec) is the process of securing data. Transmission Security Examples.
From cyberwiedza.pl
Transmission Security CyberWiedza.pl Cyberbezpieczeństwo bez tajemnic Transmission Security Examples Transmission security • transmission security standard “implement technical security measures to guard against unauthorized access to electronic protected health information. Idirect has provided enhanced transmission security (transec) capabilities within our evolution defense software. Information technology organizations across all. Transmission security (transec) is the process of securing data transmissions from being infiltrated, exploited or intercepted. Prevents the interception or disruption of. Transmission Security Examples.
From www.newsoftwares.net
How To Secure Data Transmission? Blog Transmission Security Examples Information technology organizations across all. Idirect has provided enhanced transmission security (transec) capabilities within our evolution defense software. Transmission security (transec) is the process of securing data transmissions from being infiltrated, exploited or intercepted. Prevents the interception or disruption of any transmissions occurring over a communications network. Transmission security • transmission security standard “implement technical security measures to guard against. Transmission Security Examples.
From www.slideserve.com
PPT COMSEC Security) PowerPoint Presentation, free Transmission Security Examples Transmission security • transmission security standard “implement technical security measures to guard against unauthorized access to electronic protected health information. Transmission security (transec) is the process of securing data transmissions from being infiltrated, exploited or intercepted. Information technology organizations across all. Prevents the interception or disruption of any transmissions occurring over a communications network. Idirect has provided enhanced transmission security. Transmission Security Examples.
From www.slideserve.com
PPT ENRICHING THE ‘INTEGRATION AS A SERVICE’ PARADIGM FOR THE CLOUD Transmission Security Examples Transmission security • transmission security standard “implement technical security measures to guard against unauthorized access to electronic protected health information. Idirect has provided enhanced transmission security (transec) capabilities within our evolution defense software. Information technology organizations across all. Prevents the interception or disruption of any transmissions occurring over a communications network. Transmission security (transec) is the process of securing data. Transmission Security Examples.
From eureka.patsnap.com
Secure transmission system and method Eureka Patsnap develop Transmission Security Examples Information technology organizations across all. Prevents the interception or disruption of any transmissions occurring over a communications network. Transmission security (transec) is the process of securing data transmissions from being infiltrated, exploited or intercepted. Transmission security • transmission security standard “implement technical security measures to guard against unauthorized access to electronic protected health information. Idirect has provided enhanced transmission security. Transmission Security Examples.
From www.slideserve.com
PPT Mobile Security and Payment PowerPoint Presentation, free Transmission Security Examples Idirect has provided enhanced transmission security (transec) capabilities within our evolution defense software. Prevents the interception or disruption of any transmissions occurring over a communications network. Transmission security (transec) is the process of securing data transmissions from being infiltrated, exploited or intercepted. Transmission security • transmission security standard “implement technical security measures to guard against unauthorized access to electronic protected. Transmission Security Examples.
From noise.getoto.net
Automatic (secure) transmission taking the pain out of origin Transmission Security Examples Idirect has provided enhanced transmission security (transec) capabilities within our evolution defense software. Information technology organizations across all. Prevents the interception or disruption of any transmissions occurring over a communications network. Transmission security • transmission security standard “implement technical security measures to guard against unauthorized access to electronic protected health information. Transmission security (transec) is the process of securing data. Transmission Security Examples.
From www.slideserve.com
PPT Topic 6 Security Enabling Objectives PowerPoint Presentation Transmission Security Examples Idirect has provided enhanced transmission security (transec) capabilities within our evolution defense software. Transmission security • transmission security standard “implement technical security measures to guard against unauthorized access to electronic protected health information. Prevents the interception or disruption of any transmissions occurring over a communications network. Information technology organizations across all. Transmission security (transec) is the process of securing data. Transmission Security Examples.
From www.youtube.com
Unit 1 Secure Communication Transmission Security YouTube Transmission Security Examples Idirect has provided enhanced transmission security (transec) capabilities within our evolution defense software. Transmission security (transec) is the process of securing data transmissions from being infiltrated, exploited or intercepted. Transmission security • transmission security standard “implement technical security measures to guard against unauthorized access to electronic protected health information. Prevents the interception or disruption of any transmissions occurring over a. Transmission Security Examples.
From www.dreamstime.com
Secure Data Transmission Concept. Access Right. Safe File Sharing Transmission Security Examples Information technology organizations across all. Transmission security (transec) is the process of securing data transmissions from being infiltrated, exploited or intercepted. Idirect has provided enhanced transmission security (transec) capabilities within our evolution defense software. Prevents the interception or disruption of any transmissions occurring over a communications network. Transmission security • transmission security standard “implement technical security measures to guard against. Transmission Security Examples.
From www.conceptdraw.com
Network Security Transmission Security Examples Transmission security • transmission security standard “implement technical security measures to guard against unauthorized access to electronic protected health information. Idirect has provided enhanced transmission security (transec) capabilities within our evolution defense software. Transmission security (transec) is the process of securing data transmissions from being infiltrated, exploited or intercepted. Information technology organizations across all. Prevents the interception or disruption of. Transmission Security Examples.
From www.newsoftwares.net
The Ultimate Guide To Secure Data Transmission Which Protocol Should Transmission Security Examples Idirect has provided enhanced transmission security (transec) capabilities within our evolution defense software. Transmission security (transec) is the process of securing data transmissions from being infiltrated, exploited or intercepted. Information technology organizations across all. Transmission security • transmission security standard “implement technical security measures to guard against unauthorized access to electronic protected health information. Prevents the interception or disruption of. Transmission Security Examples.
From peerj.com
Efficient data transmission on wireless communication through a privacy Transmission Security Examples Transmission security (transec) is the process of securing data transmissions from being infiltrated, exploited or intercepted. Information technology organizations across all. Transmission security • transmission security standard “implement technical security measures to guard against unauthorized access to electronic protected health information. Prevents the interception or disruption of any transmissions occurring over a communications network. Idirect has provided enhanced transmission security. Transmission Security Examples.
From energyinfo.oregon.gov
Transmission & Distribution 2020 — Energy Info Transmission Security Examples Information technology organizations across all. Prevents the interception or disruption of any transmissions occurring over a communications network. Idirect has provided enhanced transmission security (transec) capabilities within our evolution defense software. Transmission security (transec) is the process of securing data transmissions from being infiltrated, exploited or intercepted. Transmission security • transmission security standard “implement technical security measures to guard against. Transmission Security Examples.
From www.slideserve.com
PPT Android Security Basics PowerPoint Presentation, free download Transmission Security Examples Transmission security • transmission security standard “implement technical security measures to guard against unauthorized access to electronic protected health information. Transmission security (transec) is the process of securing data transmissions from being infiltrated, exploited or intercepted. Information technology organizations across all. Prevents the interception or disruption of any transmissions occurring over a communications network. Idirect has provided enhanced transmission security. Transmission Security Examples.
From docs.zoloz.com
Message transmission security API Reference Transmission Security Examples Transmission security • transmission security standard “implement technical security measures to guard against unauthorized access to electronic protected health information. Idirect has provided enhanced transmission security (transec) capabilities within our evolution defense software. Prevents the interception or disruption of any transmissions occurring over a communications network. Transmission security (transec) is the process of securing data transmissions from being infiltrated, exploited. Transmission Security Examples.
From thevallettagroup.com
HIPAA Compliance The Valletta Group Transmission Security Examples Prevents the interception or disruption of any transmissions occurring over a communications network. Transmission security • transmission security standard “implement technical security measures to guard against unauthorized access to electronic protected health information. Idirect has provided enhanced transmission security (transec) capabilities within our evolution defense software. Information technology organizations across all. Transmission security (transec) is the process of securing data. Transmission Security Examples.
From www.slideserve.com
PPT Confidentiality/HIPPA PowerPoint Presentation, free download ID Transmission Security Examples Transmission security • transmission security standard “implement technical security measures to guard against unauthorized access to electronic protected health information. Idirect has provided enhanced transmission security (transec) capabilities within our evolution defense software. Transmission security (transec) is the process of securing data transmissions from being infiltrated, exploited or intercepted. Information technology organizations across all. Prevents the interception or disruption of. Transmission Security Examples.
From www.researchgate.net
Secure transmission as a service examples. Download Scientific Diagram Transmission Security Examples Transmission security (transec) is the process of securing data transmissions from being infiltrated, exploited or intercepted. Prevents the interception or disruption of any transmissions occurring over a communications network. Transmission security • transmission security standard “implement technical security measures to guard against unauthorized access to electronic protected health information. Idirect has provided enhanced transmission security (transec) capabilities within our evolution. Transmission Security Examples.
From www.nationalretail.org.au
National Retail's Timely Collaboration with Ignite Systems Amidst Cyber Transmission Security Examples Prevents the interception or disruption of any transmissions occurring over a communications network. Information technology organizations across all. Transmission security (transec) is the process of securing data transmissions from being infiltrated, exploited or intercepted. Idirect has provided enhanced transmission security (transec) capabilities within our evolution defense software. Transmission security • transmission security standard “implement technical security measures to guard against. Transmission Security Examples.
From www.conceptdraw.com
Network Security Tips Transmission Security Examples Information technology organizations across all. Transmission security • transmission security standard “implement technical security measures to guard against unauthorized access to electronic protected health information. Prevents the interception or disruption of any transmissions occurring over a communications network. Idirect has provided enhanced transmission security (transec) capabilities within our evolution defense software. Transmission security (transec) is the process of securing data. Transmission Security Examples.
From gotowebsecurity.com
Different Types Of Cyber Attack You Should Be Aware Off Transmission Security Examples Prevents the interception or disruption of any transmissions occurring over a communications network. Transmission security • transmission security standard “implement technical security measures to guard against unauthorized access to electronic protected health information. Idirect has provided enhanced transmission security (transec) capabilities within our evolution defense software. Transmission security (transec) is the process of securing data transmissions from being infiltrated, exploited. Transmission Security Examples.
From eureka.patsnap.com
Data Transmission Security Improvements Eureka Patsnap Transmission Security Examples Transmission security • transmission security standard “implement technical security measures to guard against unauthorized access to electronic protected health information. Information technology organizations across all. Idirect has provided enhanced transmission security (transec) capabilities within our evolution defense software. Prevents the interception or disruption of any transmissions occurring over a communications network. Transmission security (transec) is the process of securing data. Transmission Security Examples.
From www.conceptdraw.com
Using Both Wired and Wireless Connections ConceptDraw DIAGRAM is an Transmission Security Examples Information technology organizations across all. Transmission security (transec) is the process of securing data transmissions from being infiltrated, exploited or intercepted. Idirect has provided enhanced transmission security (transec) capabilities within our evolution defense software. Prevents the interception or disruption of any transmissions occurring over a communications network. Transmission security • transmission security standard “implement technical security measures to guard against. Transmission Security Examples.
From www.slideserve.com
PPT HIPAA Security PowerPoint Presentation, free download ID4068979 Transmission Security Examples Idirect has provided enhanced transmission security (transec) capabilities within our evolution defense software. Transmission security (transec) is the process of securing data transmissions from being infiltrated, exploited or intercepted. Prevents the interception or disruption of any transmissions occurring over a communications network. Information technology organizations across all. Transmission security • transmission security standard “implement technical security measures to guard against. Transmission Security Examples.
From www.freepik.com
Premium Vector Transmission protection and security Transmission Security Examples Information technology organizations across all. Transmission security • transmission security standard “implement technical security measures to guard against unauthorized access to electronic protected health information. Prevents the interception or disruption of any transmissions occurring over a communications network. Idirect has provided enhanced transmission security (transec) capabilities within our evolution defense software. Transmission security (transec) is the process of securing data. Transmission Security Examples.
From www.geeksforgeeks.org
Types of Transmission Media Transmission Security Examples Idirect has provided enhanced transmission security (transec) capabilities within our evolution defense software. Information technology organizations across all. Transmission security (transec) is the process of securing data transmissions from being infiltrated, exploited or intercepted. Transmission security • transmission security standard “implement technical security measures to guard against unauthorized access to electronic protected health information. Prevents the interception or disruption of. Transmission Security Examples.
From www.researchgate.net
Secure Data Transmission through Blockchain and SDN Domain Download Transmission Security Examples Information technology organizations across all. Idirect has provided enhanced transmission security (transec) capabilities within our evolution defense software. Transmission security • transmission security standard “implement technical security measures to guard against unauthorized access to electronic protected health information. Prevents the interception or disruption of any transmissions occurring over a communications network. Transmission security (transec) is the process of securing data. Transmission Security Examples.
From www.slideserve.com
PPT COMSEC Security) PowerPoint Presentation, free Transmission Security Examples Prevents the interception or disruption of any transmissions occurring over a communications network. Transmission security (transec) is the process of securing data transmissions from being infiltrated, exploited or intercepted. Information technology organizations across all. Transmission security • transmission security standard “implement technical security measures to guard against unauthorized access to electronic protected health information. Idirect has provided enhanced transmission security. Transmission Security Examples.
From www.alamy.com
Network data transmission and lock, security protection Stock Photo Alamy Transmission Security Examples Prevents the interception or disruption of any transmissions occurring over a communications network. Transmission security (transec) is the process of securing data transmissions from being infiltrated, exploited or intercepted. Idirect has provided enhanced transmission security (transec) capabilities within our evolution defense software. Information technology organizations across all. Transmission security • transmission security standard “implement technical security measures to guard against. Transmission Security Examples.
From www.educba.com
Security Architecture Components of Security Architecture Transmission Security Examples Transmission security (transec) is the process of securing data transmissions from being infiltrated, exploited or intercepted. Idirect has provided enhanced transmission security (transec) capabilities within our evolution defense software. Prevents the interception or disruption of any transmissions occurring over a communications network. Transmission security • transmission security standard “implement technical security measures to guard against unauthorized access to electronic protected. Transmission Security Examples.
From profentech.com
Transmission Security (TRANSEC) Technology Brief Profen Communication Transmission Security Examples Information technology organizations across all. Transmission security (transec) is the process of securing data transmissions from being infiltrated, exploited or intercepted. Idirect has provided enhanced transmission security (transec) capabilities within our evolution defense software. Transmission security • transmission security standard “implement technical security measures to guard against unauthorized access to electronic protected health information. Prevents the interception or disruption of. Transmission Security Examples.