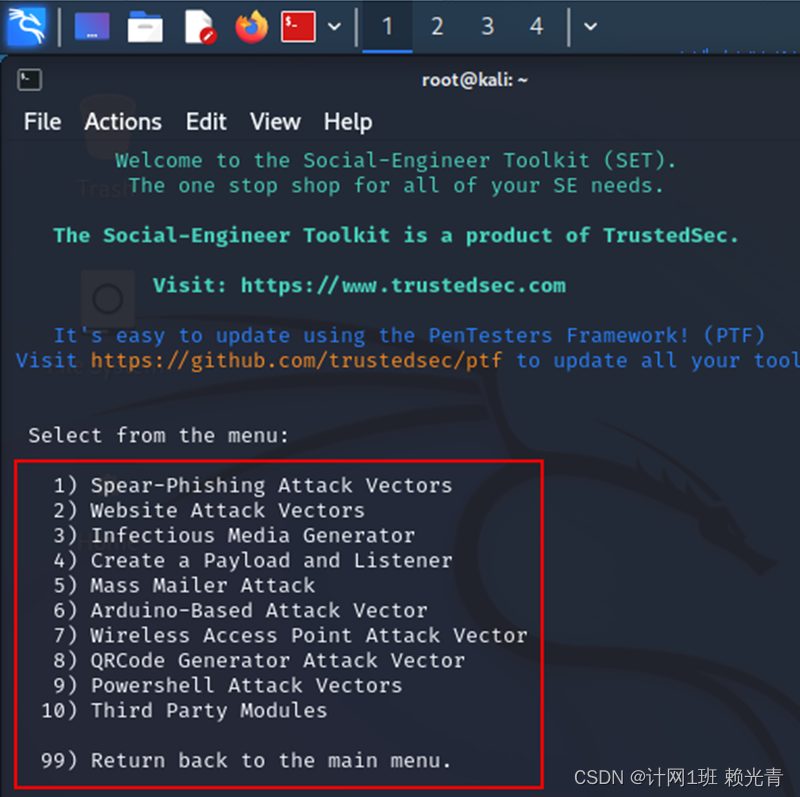
Wireless Access Point Attack Vector Kali Linux . Framework for wireless security assessments, including rogue access point creation and credential harvesting. Remember every kali version comes. Log in to kali linux; It can also handle regular hostapd ap and create ap easily. Top 8 tools on kali linux for wireless attacks. The tools have been categorized into the following for ease of use: Participants in the hashcat project discovered an attack vector which does not require the classic interception of a. Learn how to use aircrack.
from blog.csdn.net
Remember every kali version comes. Participants in the hashcat project discovered an attack vector which does not require the classic interception of a. Framework for wireless security assessments, including rogue access point creation and credential harvesting. Log in to kali linux; Top 8 tools on kali linux for wireless attacks. It can also handle regular hostapd ap and create ap easily. Learn how to use aircrack. The tools have been categorized into the following for ease of use:
Kali Linux 中的社会工程学工具包_kali社会工程学工具怎么打开CSDN博客
Wireless Access Point Attack Vector Kali Linux The tools have been categorized into the following for ease of use: Framework for wireless security assessments, including rogue access point creation and credential harvesting. It can also handle regular hostapd ap and create ap easily. Learn how to use aircrack. Top 8 tools on kali linux for wireless attacks. The tools have been categorized into the following for ease of use: Log in to kali linux; Remember every kali version comes. Participants in the hashcat project discovered an attack vector which does not require the classic interception of a.
From www.shutterstock.com
Wireless Icon Access Point Icon Related Stock Vector (Royalty Free Wireless Access Point Attack Vector Kali Linux Log in to kali linux; Top 8 tools on kali linux for wireless attacks. The tools have been categorized into the following for ease of use: Framework for wireless security assessments, including rogue access point creation and credential harvesting. It can also handle regular hostapd ap and create ap easily. Participants in the hashcat project discovered an attack vector which. Wireless Access Point Attack Vector Kali Linux.
From www.computerservicesolutions.in
Hack Facebook tutorial with Kali Linux and Preventive Measures Wireless Access Point Attack Vector Kali Linux Top 8 tools on kali linux for wireless attacks. Framework for wireless security assessments, including rogue access point creation and credential harvesting. Learn how to use aircrack. The tools have been categorized into the following for ease of use: Participants in the hashcat project discovered an attack vector which does not require the classic interception of a. Remember every kali. Wireless Access Point Attack Vector Kali Linux.
From cn-sec.com
解决Kali中社工Setoolkit启动报错问题 CNSEC 中文网 Wireless Access Point Attack Vector Kali Linux Top 8 tools on kali linux for wireless attacks. It can also handle regular hostapd ap and create ap easily. Log in to kali linux; Participants in the hashcat project discovered an attack vector which does not require the classic interception of a. The tools have been categorized into the following for ease of use: Framework for wireless security assessments,. Wireless Access Point Attack Vector Kali Linux.
From www.yeahhub.com
Privilege Escalation with PowerShell Empire and SETOOLKIT [Kali Linux Wireless Access Point Attack Vector Kali Linux It can also handle regular hostapd ap and create ap easily. Remember every kali version comes. Log in to kali linux; The tools have been categorized into the following for ease of use: Top 8 tools on kali linux for wireless attacks. Framework for wireless security assessments, including rogue access point creation and credential harvesting. Learn how to use aircrack.. Wireless Access Point Attack Vector Kali Linux.
From tecsupportandmore.blogspot.com
Hacking wifi password using Kali Linux Business, Technology Wireless Access Point Attack Vector Kali Linux Log in to kali linux; It can also handle regular hostapd ap and create ap easily. Learn how to use aircrack. Participants in the hashcat project discovered an attack vector which does not require the classic interception of a. Remember every kali version comes. Top 8 tools on kali linux for wireless attacks. The tools have been categorized into the. Wireless Access Point Attack Vector Kali Linux.
From www.javatpoint.com.cach3.com
Phishing Tools for Kali Linux javatpoint Wireless Access Point Attack Vector Kali Linux Top 8 tools on kali linux for wireless attacks. Framework for wireless security assessments, including rogue access point creation and credential harvesting. The tools have been categorized into the following for ease of use: Log in to kali linux; Learn how to use aircrack. It can also handle regular hostapd ap and create ap easily. Remember every kali version comes.. Wireless Access Point Attack Vector Kali Linux.
From saigontechsolutions.com
Kali Linux Tutorial Tutorialspoint Wireless Access Point Attack Vector Kali Linux Learn how to use aircrack. It can also handle regular hostapd ap and create ap easily. Remember every kali version comes. Top 8 tools on kali linux for wireless attacks. Log in to kali linux; The tools have been categorized into the following for ease of use: Participants in the hashcat project discovered an attack vector which does not require. Wireless Access Point Attack Vector Kali Linux.
From blog.csdn.net
Kali Linux 中的社会工程学工具包_kali社会工程学工具怎么打开CSDN博客 Wireless Access Point Attack Vector Kali Linux The tools have been categorized into the following for ease of use: It can also handle regular hostapd ap and create ap easily. Learn how to use aircrack. Participants in the hashcat project discovered an attack vector which does not require the classic interception of a. Framework for wireless security assessments, including rogue access point creation and credential harvesting. Top. Wireless Access Point Attack Vector Kali Linux.
From www.scribd.com
Linux Essentials For Hackers and Pentesters. Kali Linux Basics... 2023 Wireless Access Point Attack Vector Kali Linux Learn how to use aircrack. The tools have been categorized into the following for ease of use: Remember every kali version comes. Participants in the hashcat project discovered an attack vector which does not require the classic interception of a. It can also handle regular hostapd ap and create ap easily. Top 8 tools on kali linux for wireless attacks.. Wireless Access Point Attack Vector Kali Linux.
From hacknos.com
how to create fake access point in kali linux 2020 Archives Wireless Access Point Attack Vector Kali Linux Framework for wireless security assessments, including rogue access point creation and credential harvesting. Participants in the hashcat project discovered an attack vector which does not require the classic interception of a. It can also handle regular hostapd ap and create ap easily. Log in to kali linux; Learn how to use aircrack. Top 8 tools on kali linux for wireless. Wireless Access Point Attack Vector Kali Linux.
From factorylaneta.weebly.com
Install Libpcap On Kali Linux Wireless Access Point Attack Vector Kali Linux Participants in the hashcat project discovered an attack vector which does not require the classic interception of a. Remember every kali version comes. The tools have been categorized into the following for ease of use: It can also handle regular hostapd ap and create ap easily. Framework for wireless security assessments, including rogue access point creation and credential harvesting. Top. Wireless Access Point Attack Vector Kali Linux.
From hackingeek.com
Social Engineering & Hardware Hacking Tools Kali Linux HackinGeeK Wireless Access Point Attack Vector Kali Linux Participants in the hashcat project discovered an attack vector which does not require the classic interception of a. Top 8 tools on kali linux for wireless attacks. Learn how to use aircrack. Framework for wireless security assessments, including rogue access point creation and credential harvesting. It can also handle regular hostapd ap and create ap easily. Remember every kali version. Wireless Access Point Attack Vector Kali Linux.
From www.geeksforgeeks.org
Evil Twin in Kali Linux Wireless Access Point Attack Vector Kali Linux Participants in the hashcat project discovered an attack vector which does not require the classic interception of a. Log in to kali linux; Framework for wireless security assessments, including rogue access point creation and credential harvesting. Top 8 tools on kali linux for wireless attacks. Learn how to use aircrack. The tools have been categorized into the following for ease. Wireless Access Point Attack Vector Kali Linux.
From blog.csdn.net
社会工程学工具(信息安全)_linux系统集成社会工程学CSDN博客 Wireless Access Point Attack Vector Kali Linux Log in to kali linux; Participants in the hashcat project discovered an attack vector which does not require the classic interception of a. The tools have been categorized into the following for ease of use: Framework for wireless security assessments, including rogue access point creation and credential harvesting. Remember every kali version comes. Top 8 tools on kali linux for. Wireless Access Point Attack Vector Kali Linux.
From www.slideserve.com
PPT Detecting and Responding to Data Link Layer Attacks With Scapy Wireless Access Point Attack Vector Kali Linux Framework for wireless security assessments, including rogue access point creation and credential harvesting. Top 8 tools on kali linux for wireless attacks. The tools have been categorized into the following for ease of use: Log in to kali linux; Learn how to use aircrack. Participants in the hashcat project discovered an attack vector which does not require the classic interception. Wireless Access Point Attack Vector Kali Linux.
From blog.pulsarsecurity.com
What Is An Evil Twin and How Do You Spot One? Wireless Access Point Attack Vector Kali Linux Participants in the hashcat project discovered an attack vector which does not require the classic interception of a. Remember every kali version comes. Framework for wireless security assessments, including rogue access point creation and credential harvesting. The tools have been categorized into the following for ease of use: Top 8 tools on kali linux for wireless attacks. Learn how to. Wireless Access Point Attack Vector Kali Linux.
From thecyberdelta.com
Zphisher 2.2 Phishing Attack on LinkedIn TheCyberDelta Wireless Access Point Attack Vector Kali Linux The tools have been categorized into the following for ease of use: Learn how to use aircrack. Remember every kali version comes. Log in to kali linux; Participants in the hashcat project discovered an attack vector which does not require the classic interception of a. Top 8 tools on kali linux for wireless attacks. Framework for wireless security assessments, including. Wireless Access Point Attack Vector Kali Linux.
From www.youtube.com
Kali Linux How to Create Fake Access Points Using mdk3 YouTube Wireless Access Point Attack Vector Kali Linux Learn how to use aircrack. Remember every kali version comes. Participants in the hashcat project discovered an attack vector which does not require the classic interception of a. Top 8 tools on kali linux for wireless attacks. It can also handle regular hostapd ap and create ap easily. Log in to kali linux; The tools have been categorized into the. Wireless Access Point Attack Vector Kali Linux.
From www.computerservicesolutions.in
Hack Facebook tutorial with Kali Linux and Preventive Measures Wireless Access Point Attack Vector Kali Linux It can also handle regular hostapd ap and create ap easily. Log in to kali linux; Remember every kali version comes. Learn how to use aircrack. Framework for wireless security assessments, including rogue access point creation and credential harvesting. Top 8 tools on kali linux for wireless attacks. Participants in the hashcat project discovered an attack vector which does not. Wireless Access Point Attack Vector Kali Linux.
From kirelos.com
Top Wireless Attack tools in Kali Linux 2020.1 Kirelos Blog Wireless Access Point Attack Vector Kali Linux Top 8 tools on kali linux for wireless attacks. Learn how to use aircrack. Framework for wireless security assessments, including rogue access point creation and credential harvesting. Log in to kali linux; It can also handle regular hostapd ap and create ap easily. Remember every kali version comes. The tools have been categorized into the following for ease of use:. Wireless Access Point Attack Vector Kali Linux.
From subscription.packtpub.com
Creating virtual access points with Hostapd Mastering Kali Linux Wireless Access Point Attack Vector Kali Linux Top 8 tools on kali linux for wireless attacks. Learn how to use aircrack. Remember every kali version comes. Log in to kali linux; The tools have been categorized into the following for ease of use: It can also handle regular hostapd ap and create ap easily. Framework for wireless security assessments, including rogue access point creation and credential harvesting.. Wireless Access Point Attack Vector Kali Linux.
From www.kalitut.com
Rogue AP fake access points Kali Linux Tutorial Wireless Access Point Attack Vector Kali Linux Log in to kali linux; Learn how to use aircrack. Participants in the hashcat project discovered an attack vector which does not require the classic interception of a. Top 8 tools on kali linux for wireless attacks. The tools have been categorized into the following for ease of use: It can also handle regular hostapd ap and create ap easily.. Wireless Access Point Attack Vector Kali Linux.
From www.javatpoint.com.cach3.com
Kali Linux Wireless Attack Tools javatpoint Wireless Access Point Attack Vector Kali Linux It can also handle regular hostapd ap and create ap easily. The tools have been categorized into the following for ease of use: Participants in the hashcat project discovered an attack vector which does not require the classic interception of a. Top 8 tools on kali linux for wireless attacks. Framework for wireless security assessments, including rogue access point creation. Wireless Access Point Attack Vector Kali Linux.
From www.edge5.ch
Cyber Security Kali Linux Blog Edge5 Wireless Access Point Attack Vector Kali Linux It can also handle regular hostapd ap and create ap easily. Top 8 tools on kali linux for wireless attacks. Log in to kali linux; Learn how to use aircrack. The tools have been categorized into the following for ease of use: Remember every kali version comes. Framework for wireless security assessments, including rogue access point creation and credential harvesting.. Wireless Access Point Attack Vector Kali Linux.
From saigontechsolutions.com
Kali Linux Tutorial Tutorialspoint Wireless Access Point Attack Vector Kali Linux Log in to kali linux; Participants in the hashcat project discovered an attack vector which does not require the classic interception of a. It can also handle regular hostapd ap and create ap easily. Learn how to use aircrack. Top 8 tools on kali linux for wireless attacks. Remember every kali version comes. Framework for wireless security assessments, including rogue. Wireless Access Point Attack Vector Kali Linux.
From www.geeksforgeeks.org
How to Hack WPA/WPA2 WiFi Using Kali Linux? Wireless Access Point Attack Vector Kali Linux It can also handle regular hostapd ap and create ap easily. Learn how to use aircrack. Top 8 tools on kali linux for wireless attacks. Log in to kali linux; The tools have been categorized into the following for ease of use: Participants in the hashcat project discovered an attack vector which does not require the classic interception of a.. Wireless Access Point Attack Vector Kali Linux.
From blog.csdn.net
社会工程学工具_kail linux 2CSDN博客 Wireless Access Point Attack Vector Kali Linux Remember every kali version comes. It can also handle regular hostapd ap and create ap easily. Learn how to use aircrack. The tools have been categorized into the following for ease of use: Framework for wireless security assessments, including rogue access point creation and credential harvesting. Top 8 tools on kali linux for wireless attacks. Log in to kali linux;. Wireless Access Point Attack Vector Kali Linux.
From www.kalitut.com
Rogue access point guide Kali Linux Tutorial Wireless Access Point Attack Vector Kali Linux Top 8 tools on kali linux for wireless attacks. The tools have been categorized into the following for ease of use: Framework for wireless security assessments, including rogue access point creation and credential harvesting. Log in to kali linux; Remember every kali version comes. It can also handle regular hostapd ap and create ap easily. Participants in the hashcat project. Wireless Access Point Attack Vector Kali Linux.
From www.researchgate.net
Attack model of rogue APs. Download Scientific Diagram Wireless Access Point Attack Vector Kali Linux The tools have been categorized into the following for ease of use: Log in to kali linux; Remember every kali version comes. Learn how to use aircrack. Top 8 tools on kali linux for wireless attacks. Participants in the hashcat project discovered an attack vector which does not require the classic interception of a. Framework for wireless security assessments, including. Wireless Access Point Attack Vector Kali Linux.
From www.kali.org
Author re4son Wireless Access Point Attack Vector Kali Linux Framework for wireless security assessments, including rogue access point creation and credential harvesting. It can also handle regular hostapd ap and create ap easily. Participants in the hashcat project discovered an attack vector which does not require the classic interception of a. Top 8 tools on kali linux for wireless attacks. The tools have been categorized into the following for. Wireless Access Point Attack Vector Kali Linux.
From ietresearch.onlinelibrary.wiley.com
Intrusion detection system for detecting wireless attacks in IEEE 802. Wireless Access Point Attack Vector Kali Linux The tools have been categorized into the following for ease of use: Participants in the hashcat project discovered an attack vector which does not require the classic interception of a. It can also handle regular hostapd ap and create ap easily. Learn how to use aircrack. Top 8 tools on kali linux for wireless attacks. Remember every kali version comes.. Wireless Access Point Attack Vector Kali Linux.
From www.yeahhub.com
Privilege Escalation with PowerShell Empire and SETOOLKIT [Kali Linux Wireless Access Point Attack Vector Kali Linux The tools have been categorized into the following for ease of use: Learn how to use aircrack. Top 8 tools on kali linux for wireless attacks. Remember every kali version comes. Framework for wireless security assessments, including rogue access point creation and credential harvesting. It can also handle regular hostapd ap and create ap easily. Log in to kali linux;. Wireless Access Point Attack Vector Kali Linux.
From www.javatpoint.com
Nmap Commands in Kali Linux javatpoint Wireless Access Point Attack Vector Kali Linux Framework for wireless security assessments, including rogue access point creation and credential harvesting. Learn how to use aircrack. It can also handle regular hostapd ap and create ap easily. Remember every kali version comes. Participants in the hashcat project discovered an attack vector which does not require the classic interception of a. The tools have been categorized into the following. Wireless Access Point Attack Vector Kali Linux.
From www.youtube.com
How To Create A Fake Access Point On Kali Linux (Rogue AP MItM Attack Wireless Access Point Attack Vector Kali Linux The tools have been categorized into the following for ease of use: Learn how to use aircrack. Framework for wireless security assessments, including rogue access point creation and credential harvesting. Log in to kali linux; Participants in the hashcat project discovered an attack vector which does not require the classic interception of a. It can also handle regular hostapd ap. Wireless Access Point Attack Vector Kali Linux.
From www.offensive-security.com
Kali Linux Evil Wireless Access Point Wireless Access Point Attack Vector Kali Linux Log in to kali linux; Framework for wireless security assessments, including rogue access point creation and credential harvesting. Learn how to use aircrack. It can also handle regular hostapd ap and create ap easily. The tools have been categorized into the following for ease of use: Participants in the hashcat project discovered an attack vector which does not require the. Wireless Access Point Attack Vector Kali Linux.