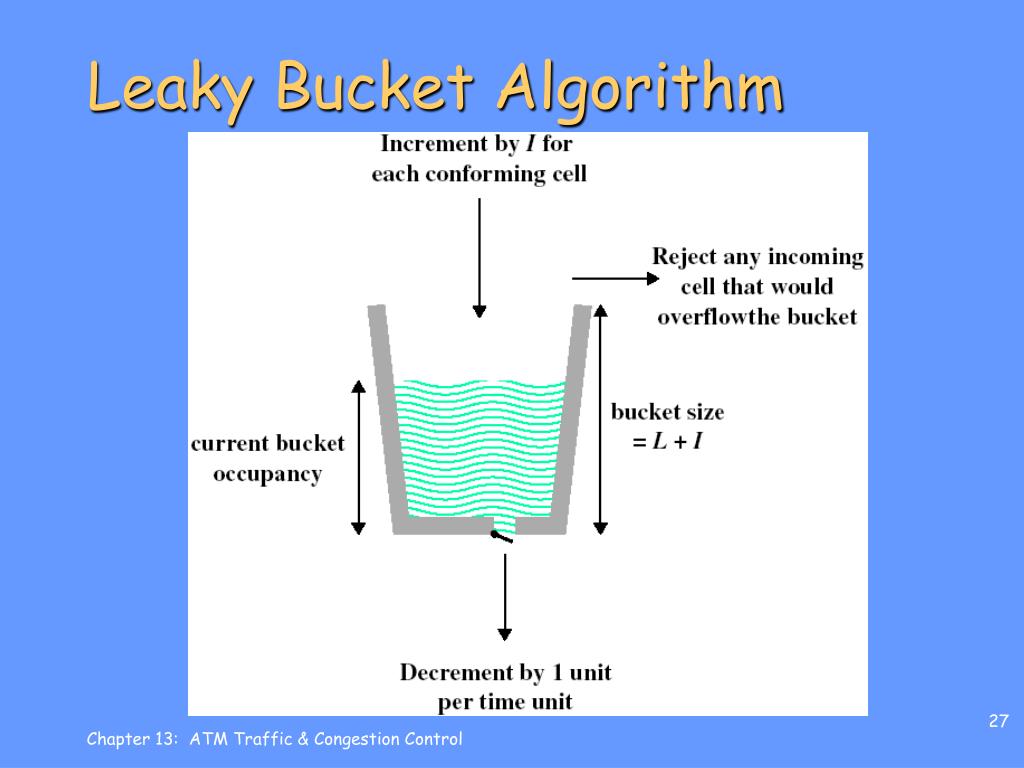
Leaky-Bucket Rate Limit Algorithm . One popular algorithm for rate limiting is the leaky bucket algorithm. Picture a bucket with a tiny hole at its. This article will guide you through implementing the leaky. The approach of using a leaky bucket is where the bucket size is constant and has a leak that allows it to shrink in size progressively. The leaky bucket algorithm simulates a leaky bucket that can hold a fixed number of requests. The leaky bucket algorithm metaphorically allows requests to drip out of a bucket at a constant rate. New incoming requests are acumulated into the bucket, and if this one is full, requests are rejected. If you’re studying for gate or want to. The leaky bucket algorithm is a simple yet effective way to control data flow and prevent congestion. Fixed window rate limiting works by. If the bucket (buffer) overflows, new requests are discarded. Different algorithms can be used to implement rate limiting. Let's review the most common types in this section.
from www.slideserve.com
Fixed window rate limiting works by. New incoming requests are acumulated into the bucket, and if this one is full, requests are rejected. Different algorithms can be used to implement rate limiting. One popular algorithm for rate limiting is the leaky bucket algorithm. The leaky bucket algorithm simulates a leaky bucket that can hold a fixed number of requests. The leaky bucket algorithm is a simple yet effective way to control data flow and prevent congestion. Picture a bucket with a tiny hole at its. This article will guide you through implementing the leaky. If you’re studying for gate or want to. The approach of using a leaky bucket is where the bucket size is constant and has a leak that allows it to shrink in size progressively.
PPT Chapter 13 PowerPoint Presentation, free download ID569119
Leaky-Bucket Rate Limit Algorithm The leaky bucket algorithm is a simple yet effective way to control data flow and prevent congestion. The leaky bucket algorithm simulates a leaky bucket that can hold a fixed number of requests. New incoming requests are acumulated into the bucket, and if this one is full, requests are rejected. If the bucket (buffer) overflows, new requests are discarded. Picture a bucket with a tiny hole at its. Let's review the most common types in this section. If you’re studying for gate or want to. The leaky bucket algorithm metaphorically allows requests to drip out of a bucket at a constant rate. Different algorithms can be used to implement rate limiting. Fixed window rate limiting works by. One popular algorithm for rate limiting is the leaky bucket algorithm. The leaky bucket algorithm is a simple yet effective way to control data flow and prevent congestion. This article will guide you through implementing the leaky. The approach of using a leaky bucket is where the bucket size is constant and has a leak that allows it to shrink in size progressively.
From www.youtube.com
Mastering the Leaky Bucket Algorithm A StepbyStep Guide? algorithm Leaky-Bucket Rate Limit Algorithm Fixed window rate limiting works by. Let's review the most common types in this section. The leaky bucket algorithm metaphorically allows requests to drip out of a bucket at a constant rate. If the bucket (buffer) overflows, new requests are discarded. This article will guide you through implementing the leaky. The leaky bucket algorithm is a simple yet effective way. Leaky-Bucket Rate Limit Algorithm.
From www.eraser.io
API Rate Limiting Strategies Token Bucket vs. Leaky Bucket Decision Node Leaky-Bucket Rate Limit Algorithm The approach of using a leaky bucket is where the bucket size is constant and has a leak that allows it to shrink in size progressively. The leaky bucket algorithm simulates a leaky bucket that can hold a fixed number of requests. Let's review the most common types in this section. This article will guide you through implementing the leaky.. Leaky-Bucket Rate Limit Algorithm.
From medium.com
Token Bucket Algorithm (Rate Limiting) by Suraj Shende Medium Leaky-Bucket Rate Limit Algorithm Different algorithms can be used to implement rate limiting. One popular algorithm for rate limiting is the leaky bucket algorithm. This article will guide you through implementing the leaky. If the bucket (buffer) overflows, new requests are discarded. The leaky bucket algorithm metaphorically allows requests to drip out of a bucket at a constant rate. Fixed window rate limiting works. Leaky-Bucket Rate Limit Algorithm.
From towardsdev.com
Leaky Bucket vs Token Bucket in Rate Limiting Algorithms by David Lee Leaky-Bucket Rate Limit Algorithm The approach of using a leaky bucket is where the bucket size is constant and has a leak that allows it to shrink in size progressively. The leaky bucket algorithm simulates a leaky bucket that can hold a fixed number of requests. This article will guide you through implementing the leaky. If you’re studying for gate or want to. The. Leaky-Bucket Rate Limit Algorithm.
From giacomomaire.com
Step by step rate limiting with NodeJS and Express (full code included) Leaky-Bucket Rate Limit Algorithm One popular algorithm for rate limiting is the leaky bucket algorithm. This article will guide you through implementing the leaky. The leaky bucket algorithm simulates a leaky bucket that can hold a fixed number of requests. Fixed window rate limiting works by. Different algorithms can be used to implement rate limiting. The approach of using a leaky bucket is where. Leaky-Bucket Rate Limit Algorithm.
From www.researchgate.net
Leaky bucket algorithm Download Scientific Diagram Leaky-Bucket Rate Limit Algorithm The approach of using a leaky bucket is where the bucket size is constant and has a leak that allows it to shrink in size progressively. The leaky bucket algorithm simulates a leaky bucket that can hold a fixed number of requests. The leaky bucket algorithm metaphorically allows requests to drip out of a bucket at a constant rate. Picture. Leaky-Bucket Rate Limit Algorithm.
From www.youtube.com
Leaky Bucket Algorithm Rate Limiting System Design YouTube Leaky-Bucket Rate Limit Algorithm If the bucket (buffer) overflows, new requests are discarded. If you’re studying for gate or want to. Fixed window rate limiting works by. One popular algorithm for rate limiting is the leaky bucket algorithm. The leaky bucket algorithm is a simple yet effective way to control data flow and prevent congestion. This article will guide you through implementing the leaky.. Leaky-Bucket Rate Limit Algorithm.
From dev.to
Rate Limiter in System Design. Part 2 Commonly Used Algorithms DEV Leaky-Bucket Rate Limit Algorithm New incoming requests are acumulated into the bucket, and if this one is full, requests are rejected. If you’re studying for gate or want to. The leaky bucket algorithm simulates a leaky bucket that can hold a fixed number of requests. If the bucket (buffer) overflows, new requests are discarded. The leaky bucket algorithm metaphorically allows requests to drip out. Leaky-Bucket Rate Limit Algorithm.
From medium.com
Understanding Rate Limiting with Token Bucket Algorithm A Practical Leaky-Bucket Rate Limit Algorithm The leaky bucket algorithm metaphorically allows requests to drip out of a bucket at a constant rate. Different algorithms can be used to implement rate limiting. Fixed window rate limiting works by. If you’re studying for gate or want to. The leaky bucket algorithm is a simple yet effective way to control data flow and prevent congestion. The approach of. Leaky-Bucket Rate Limit Algorithm.
From hechao.li
Rate Limiting Part 1 Leaky-Bucket Rate Limit Algorithm The approach of using a leaky bucket is where the bucket size is constant and has a leak that allows it to shrink in size progressively. Different algorithms can be used to implement rate limiting. The leaky bucket algorithm is a simple yet effective way to control data flow and prevent congestion. Fixed window rate limiting works by. New incoming. Leaky-Bucket Rate Limit Algorithm.
From www.youtube.com
congestion control algorithm Leaky Bucket Algorithm (open loop and Leaky-Bucket Rate Limit Algorithm Let's review the most common types in this section. New incoming requests are acumulated into the bucket, and if this one is full, requests are rejected. One popular algorithm for rate limiting is the leaky bucket algorithm. The leaky bucket algorithm metaphorically allows requests to drip out of a bucket at a constant rate. Different algorithms can be used to. Leaky-Bucket Rate Limit Algorithm.
From www.rdiachenko.com
Token Bucket Rate Limiting Algorithm Leaky-Bucket Rate Limit Algorithm If the bucket (buffer) overflows, new requests are discarded. Fixed window rate limiting works by. One popular algorithm for rate limiting is the leaky bucket algorithm. The leaky bucket algorithm metaphorically allows requests to drip out of a bucket at a constant rate. Picture a bucket with a tiny hole at its. The leaky bucket algorithm simulates a leaky bucket. Leaky-Bucket Rate Limit Algorithm.
From www.researchgate.net
Intelligent leaky bucket algorithm. Download Scientific Diagram Leaky-Bucket Rate Limit Algorithm Picture a bucket with a tiny hole at its. The approach of using a leaky bucket is where the bucket size is constant and has a leak that allows it to shrink in size progressively. If you’re studying for gate or want to. Fixed window rate limiting works by. If the bucket (buffer) overflows, new requests are discarded. This article. Leaky-Bucket Rate Limit Algorithm.
From www.youtube.com
System Design Rate Limiter Leaky Bucket Implementation System Leaky-Bucket Rate Limit Algorithm The leaky bucket algorithm is a simple yet effective way to control data flow and prevent congestion. Fixed window rate limiting works by. The leaky bucket algorithm metaphorically allows requests to drip out of a bucket at a constant rate. Picture a bucket with a tiny hole at its. Let's review the most common types in this section. If the. Leaky-Bucket Rate Limit Algorithm.
From www.code4it.dev
Davide's Code and Architecture Notes 4 algorithms to implement Rate Leaky-Bucket Rate Limit Algorithm This article will guide you through implementing the leaky. The leaky bucket algorithm simulates a leaky bucket that can hold a fixed number of requests. One popular algorithm for rate limiting is the leaky bucket algorithm. New incoming requests are acumulated into the bucket, and if this one is full, requests are rejected. Picture a bucket with a tiny hole. Leaky-Bucket Rate Limit Algorithm.
From bhargav-journal.blogspot.com
Rate Limiter Implementation — Token Bucket Algorithm Leaky-Bucket Rate Limit Algorithm Different algorithms can be used to implement rate limiting. This article will guide you through implementing the leaky. The leaky bucket algorithm simulates a leaky bucket that can hold a fixed number of requests. New incoming requests are acumulated into the bucket, and if this one is full, requests are rejected. If the bucket (buffer) overflows, new requests are discarded.. Leaky-Bucket Rate Limit Algorithm.
From mozillazg.com
rate limiting 之 leaky bucket mozillazg's Blog Leaky-Bucket Rate Limit Algorithm The approach of using a leaky bucket is where the bucket size is constant and has a leak that allows it to shrink in size progressively. The leaky bucket algorithm metaphorically allows requests to drip out of a bucket at a constant rate. Let's review the most common types in this section. If you’re studying for gate or want to.. Leaky-Bucket Rate Limit Algorithm.
From blog.cloudflare.com
How we built rate limiting capable of scaling to millions of domains Leaky-Bucket Rate Limit Algorithm New incoming requests are acumulated into the bucket, and if this one is full, requests are rejected. One popular algorithm for rate limiting is the leaky bucket algorithm. Fixed window rate limiting works by. If the bucket (buffer) overflows, new requests are discarded. If you’re studying for gate or want to. Let's review the most common types in this section.. Leaky-Bucket Rate Limit Algorithm.
From www.fatalerrors.org
Go Language Implementation of Current Limiting in Leakage Bucket and Leaky-Bucket Rate Limit Algorithm If the bucket (buffer) overflows, new requests are discarded. The approach of using a leaky bucket is where the bucket size is constant and has a leak that allows it to shrink in size progressively. This article will guide you through implementing the leaky. The leaky bucket algorithm is a simple yet effective way to control data flow and prevent. Leaky-Bucket Rate Limit Algorithm.
From www.scaler.com
Leaky Bucket Algorithm Scalar Topics Leaky-Bucket Rate Limit Algorithm One popular algorithm for rate limiting is the leaky bucket algorithm. The leaky bucket algorithm simulates a leaky bucket that can hold a fixed number of requests. Fixed window rate limiting works by. If the bucket (buffer) overflows, new requests are discarded. If you’re studying for gate or want to. Picture a bucket with a tiny hole at its. The. Leaky-Bucket Rate Limit Algorithm.
From www.youtube.com
Token bucket Algorithm used in amazon and Stripe for rate limiting Leaky-Bucket Rate Limit Algorithm If you’re studying for gate or want to. The leaky bucket algorithm is a simple yet effective way to control data flow and prevent congestion. The leaky bucket algorithm simulates a leaky bucket that can hold a fixed number of requests. The approach of using a leaky bucket is where the bucket size is constant and has a leak that. Leaky-Bucket Rate Limit Algorithm.
From www.rdiachenko.com
Exploring and Implementing the Leaky Bucket Rate Limiting Algorithm Leaky-Bucket Rate Limit Algorithm Different algorithms can be used to implement rate limiting. This article will guide you through implementing the leaky. The approach of using a leaky bucket is where the bucket size is constant and has a leak that allows it to shrink in size progressively. If the bucket (buffer) overflows, new requests are discarded. Fixed window rate limiting works by. The. Leaky-Bucket Rate Limit Algorithm.
From lowleveldesign.io
Design a Distributed Scalable API Rate Limiter Leaky-Bucket Rate Limit Algorithm The leaky bucket algorithm is a simple yet effective way to control data flow and prevent congestion. New incoming requests are acumulated into the bucket, and if this one is full, requests are rejected. Different algorithms can be used to implement rate limiting. If you’re studying for gate or want to. If the bucket (buffer) overflows, new requests are discarded.. Leaky-Bucket Rate Limit Algorithm.
From www.scribd.com
An Overview of the Leaky Bucket Algorithm for Traffic Shaping and Rate Leaky-Bucket Rate Limit Algorithm The leaky bucket algorithm is a simple yet effective way to control data flow and prevent congestion. Picture a bucket with a tiny hole at its. The leaky bucket algorithm metaphorically allows requests to drip out of a bucket at a constant rate. One popular algorithm for rate limiting is the leaky bucket algorithm. This article will guide you through. Leaky-Bucket Rate Limit Algorithm.
From www.researchgate.net
Flowchart of the conventional leaky bucket algorithm. Download Leaky-Bucket Rate Limit Algorithm One popular algorithm for rate limiting is the leaky bucket algorithm. Different algorithms can be used to implement rate limiting. If the bucket (buffer) overflows, new requests are discarded. This article will guide you through implementing the leaky. Let's review the most common types in this section. The leaky bucket algorithm simulates a leaky bucket that can hold a fixed. Leaky-Bucket Rate Limit Algorithm.
From www.linkedin.com
Comparing Rate Limiting Algorithms Leaky Bucket and Token Bucket Leaky-Bucket Rate Limit Algorithm Let's review the most common types in this section. The leaky bucket algorithm metaphorically allows requests to drip out of a bucket at a constant rate. Picture a bucket with a tiny hole at its. This article will guide you through implementing the leaky. If you’re studying for gate or want to. The leaky bucket algorithm is a simple yet. Leaky-Bucket Rate Limit Algorithm.
From www.rdiachenko.com
Token Bucket Rate Limiting Algorithm Leaky-Bucket Rate Limit Algorithm Let's review the most common types in this section. If you’re studying for gate or want to. Picture a bucket with a tiny hole at its. Fixed window rate limiting works by. The approach of using a leaky bucket is where the bucket size is constant and has a leak that allows it to shrink in size progressively. New incoming. Leaky-Bucket Rate Limit Algorithm.
From www.slideserve.com
PPT Chapter 13 PowerPoint Presentation, free download ID569119 Leaky-Bucket Rate Limit Algorithm Different algorithms can be used to implement rate limiting. The leaky bucket algorithm metaphorically allows requests to drip out of a bucket at a constant rate. Picture a bucket with a tiny hole at its. Fixed window rate limiting works by. The leaky bucket algorithm is a simple yet effective way to control data flow and prevent congestion. The leaky. Leaky-Bucket Rate Limit Algorithm.
From itnext.io
Rate limiting with leaky bucket algorithm by Codejitsu ITNEXT Leaky-Bucket Rate Limit Algorithm The leaky bucket algorithm metaphorically allows requests to drip out of a bucket at a constant rate. If the bucket (buffer) overflows, new requests are discarded. New incoming requests are acumulated into the bucket, and if this one is full, requests are rejected. The approach of using a leaky bucket is where the bucket size is constant and has a. Leaky-Bucket Rate Limit Algorithm.
From designcodesolve.com
Rate Limiting Token and Leaky Bucket Implementation and Explanation Leaky-Bucket Rate Limit Algorithm If you’re studying for gate or want to. This article will guide you through implementing the leaky. Fixed window rate limiting works by. Let's review the most common types in this section. The approach of using a leaky bucket is where the bucket size is constant and has a leak that allows it to shrink in size progressively. The leaky. Leaky-Bucket Rate Limit Algorithm.
From www.geeksforgeeks.org
Rate Limiting Algorithms System Design Leaky-Bucket Rate Limit Algorithm One popular algorithm for rate limiting is the leaky bucket algorithm. If the bucket (buffer) overflows, new requests are discarded. New incoming requests are acumulated into the bucket, and if this one is full, requests are rejected. Fixed window rate limiting works by. Let's review the most common types in this section. Different algorithms can be used to implement rate. Leaky-Bucket Rate Limit Algorithm.
From blog.bytebytego.com
Rate Limiting Fundamentals by Alex Xu Leaky-Bucket Rate Limit Algorithm Fixed window rate limiting works by. If the bucket (buffer) overflows, new requests are discarded. One popular algorithm for rate limiting is the leaky bucket algorithm. The approach of using a leaky bucket is where the bucket size is constant and has a leak that allows it to shrink in size progressively. Different algorithms can be used to implement rate. Leaky-Bucket Rate Limit Algorithm.
From please-sleep.cou929.nu
Nginx の Rate Limit 設定と Leaky Bucket Algorithm Please Sleep Leaky-Bucket Rate Limit Algorithm Let's review the most common types in this section. The leaky bucket algorithm is a simple yet effective way to control data flow and prevent congestion. Fixed window rate limiting works by. Picture a bucket with a tiny hole at its. One popular algorithm for rate limiting is the leaky bucket algorithm. This article will guide you through implementing the. Leaky-Bucket Rate Limit Algorithm.
From www.rdiachenko.com
Exploring and Implementing the Leaky Bucket Rate Limiting Algorithm Leaky-Bucket Rate Limit Algorithm Picture a bucket with a tiny hole at its. If the bucket (buffer) overflows, new requests are discarded. The leaky bucket algorithm simulates a leaky bucket that can hold a fixed number of requests. One popular algorithm for rate limiting is the leaky bucket algorithm. Different algorithms can be used to implement rate limiting. The leaky bucket algorithm metaphorically allows. Leaky-Bucket Rate Limit Algorithm.