Examples Of Security Exploits . We review the 7 most common types of vulnerabilities including: Exploits that target specific vulnerabilities. Further, we will take a look at the most common ones. U.s., australian, canadian, new zealand, and uk cybersecurity authorities assess, in 2021, malicious cyber actors aggressively. A cybercriminal exploiting a vulnerability can perform various malicious actions, such as installing malicious software (malware), running malicious code, and stealing sensitive data. Targets vulnerabilities in wireless networks. Cves are identifiers given to publicly disclosed information security flaws, and attackers can use them to exploit vulnerable systems. Gets physical access to devices or systems. The following cybersecurity agencies coauthored this joint cybersecurity advisory.
from tesrex.com
U.s., australian, canadian, new zealand, and uk cybersecurity authorities assess, in 2021, malicious cyber actors aggressively. Gets physical access to devices or systems. The following cybersecurity agencies coauthored this joint cybersecurity advisory. We review the 7 most common types of vulnerabilities including: Further, we will take a look at the most common ones. Targets vulnerabilities in wireless networks. Cves are identifiers given to publicly disclosed information security flaws, and attackers can use them to exploit vulnerable systems. A cybercriminal exploiting a vulnerability can perform various malicious actions, such as installing malicious software (malware), running malicious code, and stealing sensitive data. Exploits that target specific vulnerabilities.
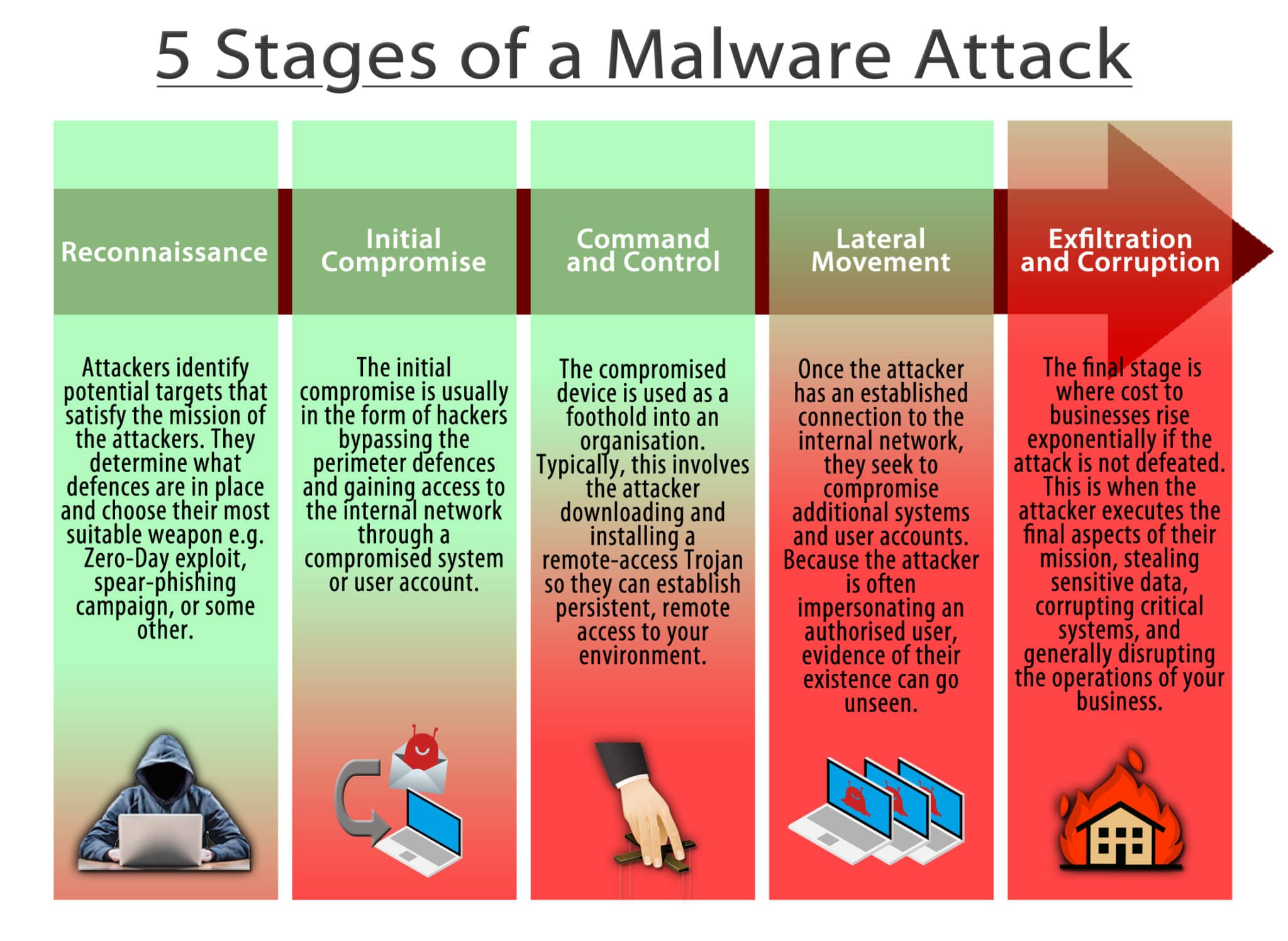
5 Stages Of A Malware Attack Cyber Security Tesrex
Examples Of Security Exploits We review the 7 most common types of vulnerabilities including: The following cybersecurity agencies coauthored this joint cybersecurity advisory. Further, we will take a look at the most common ones. Cves are identifiers given to publicly disclosed information security flaws, and attackers can use them to exploit vulnerable systems. A cybercriminal exploiting a vulnerability can perform various malicious actions, such as installing malicious software (malware), running malicious code, and stealing sensitive data. Gets physical access to devices or systems. Exploits that target specific vulnerabilities. Targets vulnerabilities in wireless networks. We review the 7 most common types of vulnerabilities including: U.s., australian, canadian, new zealand, and uk cybersecurity authorities assess, in 2021, malicious cyber actors aggressively.
From spinbackup.com
Biggest Cybersecurity Threats from Within or Outside? Examples Of Security Exploits Targets vulnerabilities in wireless networks. The following cybersecurity agencies coauthored this joint cybersecurity advisory. U.s., australian, canadian, new zealand, and uk cybersecurity authorities assess, in 2021, malicious cyber actors aggressively. Exploits that target specific vulnerabilities. A cybercriminal exploiting a vulnerability can perform various malicious actions, such as installing malicious software (malware), running malicious code, and stealing sensitive data. Gets physical. Examples Of Security Exploits.
From www.securitysift.com
Windows Exploit Development Part 6 SEH Exploits Security Examples Of Security Exploits The following cybersecurity agencies coauthored this joint cybersecurity advisory. Targets vulnerabilities in wireless networks. Cves are identifiers given to publicly disclosed information security flaws, and attackers can use them to exploit vulnerable systems. We review the 7 most common types of vulnerabilities including: Exploits that target specific vulnerabilities. Further, we will take a look at the most common ones. A. Examples Of Security Exploits.
From www.varonis.com
Government Hacking Exploits, Examples and Prevention Tips Examples Of Security Exploits Exploits that target specific vulnerabilities. We review the 7 most common types of vulnerabilities including: A cybercriminal exploiting a vulnerability can perform various malicious actions, such as installing malicious software (malware), running malicious code, and stealing sensitive data. U.s., australian, canadian, new zealand, and uk cybersecurity authorities assess, in 2021, malicious cyber actors aggressively. Cves are identifiers given to publicly. Examples Of Security Exploits.
From www.techiesline.com
What is Exploit? Types, Hidden Threats and Protection Measures Examples Of Security Exploits Exploits that target specific vulnerabilities. Cves are identifiers given to publicly disclosed information security flaws, and attackers can use them to exploit vulnerable systems. U.s., australian, canadian, new zealand, and uk cybersecurity authorities assess, in 2021, malicious cyber actors aggressively. The following cybersecurity agencies coauthored this joint cybersecurity advisory. A cybercriminal exploiting a vulnerability can perform various malicious actions, such. Examples Of Security Exploits.
From vulners.com
What are Exploits Types & Examples in Cybersecurity Vulners Examples Of Security Exploits U.s., australian, canadian, new zealand, and uk cybersecurity authorities assess, in 2021, malicious cyber actors aggressively. Further, we will take a look at the most common ones. Targets vulnerabilities in wireless networks. The following cybersecurity agencies coauthored this joint cybersecurity advisory. A cybercriminal exploiting a vulnerability can perform various malicious actions, such as installing malicious software (malware), running malicious code,. Examples Of Security Exploits.
From www.trendmicro.fr
Exploit Kit Definition Examples Of Security Exploits Further, we will take a look at the most common ones. Targets vulnerabilities in wireless networks. A cybercriminal exploiting a vulnerability can perform various malicious actions, such as installing malicious software (malware), running malicious code, and stealing sensitive data. We review the 7 most common types of vulnerabilities including: U.s., australian, canadian, new zealand, and uk cybersecurity authorities assess, in. Examples Of Security Exploits.
From howtofix.guide
Exploit Definition What is Exploits in Cyber Security? — How To Fix Guide Examples Of Security Exploits Cves are identifiers given to publicly disclosed information security flaws, and attackers can use them to exploit vulnerable systems. Exploits that target specific vulnerabilities. A cybercriminal exploiting a vulnerability can perform various malicious actions, such as installing malicious software (malware), running malicious code, and stealing sensitive data. U.s., australian, canadian, new zealand, and uk cybersecurity authorities assess, in 2021, malicious. Examples Of Security Exploits.
From www.tenforums.com
Enable or Disable Windows Defender Exploit Protection Settings Tutorials Examples Of Security Exploits Exploits that target specific vulnerabilities. U.s., australian, canadian, new zealand, and uk cybersecurity authorities assess, in 2021, malicious cyber actors aggressively. The following cybersecurity agencies coauthored this joint cybersecurity advisory. A cybercriminal exploiting a vulnerability can perform various malicious actions, such as installing malicious software (malware), running malicious code, and stealing sensitive data. We review the 7 most common types. Examples Of Security Exploits.
From www.youtube.com
PHP Security Tutorial Most Common Vulnerabilities Attackers Can Examples Of Security Exploits U.s., australian, canadian, new zealand, and uk cybersecurity authorities assess, in 2021, malicious cyber actors aggressively. A cybercriminal exploiting a vulnerability can perform various malicious actions, such as installing malicious software (malware), running malicious code, and stealing sensitive data. Exploits that target specific vulnerabilities. Further, we will take a look at the most common ones. Targets vulnerabilities in wireless networks.. Examples Of Security Exploits.
From www.infosectrain.com
Common Security Attacks in the OSI Layer Model Examples Of Security Exploits A cybercriminal exploiting a vulnerability can perform various malicious actions, such as installing malicious software (malware), running malicious code, and stealing sensitive data. Exploits that target specific vulnerabilities. Targets vulnerabilities in wireless networks. U.s., australian, canadian, new zealand, and uk cybersecurity authorities assess, in 2021, malicious cyber actors aggressively. Further, we will take a look at the most common ones.. Examples Of Security Exploits.
From www.wordfence.com
Understanding WordPress Zero Day Exploits WordPress Security Examples Of Security Exploits A cybercriminal exploiting a vulnerability can perform various malicious actions, such as installing malicious software (malware), running malicious code, and stealing sensitive data. We review the 7 most common types of vulnerabilities including: Gets physical access to devices or systems. The following cybersecurity agencies coauthored this joint cybersecurity advisory. Cves are identifiers given to publicly disclosed information security flaws, and. Examples Of Security Exploits.
From www.securitysift.com
Windows Exploit Development Part 6 SEH Exploits Security Examples Of Security Exploits Exploits that target specific vulnerabilities. We review the 7 most common types of vulnerabilities including: U.s., australian, canadian, new zealand, and uk cybersecurity authorities assess, in 2021, malicious cyber actors aggressively. Further, we will take a look at the most common ones. The following cybersecurity agencies coauthored this joint cybersecurity advisory. A cybercriminal exploiting a vulnerability can perform various malicious. Examples Of Security Exploits.
From www.techtarget.com
10 Types of Security Incidents and How to Prevent Them TechTarget Examples Of Security Exploits The following cybersecurity agencies coauthored this joint cybersecurity advisory. A cybercriminal exploiting a vulnerability can perform various malicious actions, such as installing malicious software (malware), running malicious code, and stealing sensitive data. Gets physical access to devices or systems. Further, we will take a look at the most common ones. U.s., australian, canadian, new zealand, and uk cybersecurity authorities assess,. Examples Of Security Exploits.
From heimdalsecurity.com
A Quick Guide to Zero Day Attacks, Exploits, and Vulnerabilities Examples Of Security Exploits Gets physical access to devices or systems. U.s., australian, canadian, new zealand, and uk cybersecurity authorities assess, in 2021, malicious cyber actors aggressively. Targets vulnerabilities in wireless networks. We review the 7 most common types of vulnerabilities including: Cves are identifiers given to publicly disclosed information security flaws, and attackers can use them to exploit vulnerable systems. The following cybersecurity. Examples Of Security Exploits.
From www.akamai.com
What Is Cybersecurity or Cyber Security? Akamai Examples Of Security Exploits A cybercriminal exploiting a vulnerability can perform various malicious actions, such as installing malicious software (malware), running malicious code, and stealing sensitive data. Cves are identifiers given to publicly disclosed information security flaws, and attackers can use them to exploit vulnerable systems. We review the 7 most common types of vulnerabilities including: Gets physical access to devices or systems. Exploits. Examples Of Security Exploits.
From www.comparitech.com
What is an exploit kit (with examples) How do cybercriminals use them? Examples Of Security Exploits Further, we will take a look at the most common ones. Cves are identifiers given to publicly disclosed information security flaws, and attackers can use them to exploit vulnerable systems. Gets physical access to devices or systems. The following cybersecurity agencies coauthored this joint cybersecurity advisory. Targets vulnerabilities in wireless networks. U.s., australian, canadian, new zealand, and uk cybersecurity authorities. Examples Of Security Exploits.
From www.slideserve.com
PPT Chapter 14 Network Security PowerPoint Presentation, free Examples Of Security Exploits Targets vulnerabilities in wireless networks. U.s., australian, canadian, new zealand, and uk cybersecurity authorities assess, in 2021, malicious cyber actors aggressively. Cves are identifiers given to publicly disclosed information security flaws, and attackers can use them to exploit vulnerable systems. We review the 7 most common types of vulnerabilities including: The following cybersecurity agencies coauthored this joint cybersecurity advisory. Further,. Examples Of Security Exploits.
From thecyphere.com
Vulnerability, Threats, Exploits And Their Relationship With Risk Examples Of Security Exploits Targets vulnerabilities in wireless networks. The following cybersecurity agencies coauthored this joint cybersecurity advisory. Cves are identifiers given to publicly disclosed information security flaws, and attackers can use them to exploit vulnerable systems. Further, we will take a look at the most common ones. A cybercriminal exploiting a vulnerability can perform various malicious actions, such as installing malicious software (malware),. Examples Of Security Exploits.
From vulners.com
What are Exploits Types & Examples in Cybersecurity Vulners Examples Of Security Exploits U.s., australian, canadian, new zealand, and uk cybersecurity authorities assess, in 2021, malicious cyber actors aggressively. Further, we will take a look at the most common ones. Cves are identifiers given to publicly disclosed information security flaws, and attackers can use them to exploit vulnerable systems. The following cybersecurity agencies coauthored this joint cybersecurity advisory. A cybercriminal exploiting a vulnerability. Examples Of Security Exploits.
From www.manageengine.com
Zeroday attacks demystified ManageEngine Expert Talks Attack detection Examples Of Security Exploits Gets physical access to devices or systems. The following cybersecurity agencies coauthored this joint cybersecurity advisory. Further, we will take a look at the most common ones. A cybercriminal exploiting a vulnerability can perform various malicious actions, such as installing malicious software (malware), running malicious code, and stealing sensitive data. Exploits that target specific vulnerabilities. We review the 7 most. Examples Of Security Exploits.
From www.trendmicro.com
exploit Definition Trend Micro (US) Examples Of Security Exploits Gets physical access to devices or systems. Cves are identifiers given to publicly disclosed information security flaws, and attackers can use them to exploit vulnerable systems. A cybercriminal exploiting a vulnerability can perform various malicious actions, such as installing malicious software (malware), running malicious code, and stealing sensitive data. We review the 7 most common types of vulnerabilities including: Further,. Examples Of Security Exploits.
From assignmenthelp4me.com
A comprehensive study of Cyber Security and its types Examples Of Security Exploits Exploits that target specific vulnerabilities. U.s., australian, canadian, new zealand, and uk cybersecurity authorities assess, in 2021, malicious cyber actors aggressively. Targets vulnerabilities in wireless networks. Gets physical access to devices or systems. A cybercriminal exploiting a vulnerability can perform various malicious actions, such as installing malicious software (malware), running malicious code, and stealing sensitive data. The following cybersecurity agencies. Examples Of Security Exploits.
From www.scribd.com
cyber law Cybercrime Computer Security Exploits Examples Of Security Exploits Further, we will take a look at the most common ones. Targets vulnerabilities in wireless networks. A cybercriminal exploiting a vulnerability can perform various malicious actions, such as installing malicious software (malware), running malicious code, and stealing sensitive data. Exploits that target specific vulnerabilities. Cves are identifiers given to publicly disclosed information security flaws, and attackers can use them to. Examples Of Security Exploits.
From www.theknowledgeacademy.com
What is Vulnerability in Cyber Security With Example? Examples Of Security Exploits Gets physical access to devices or systems. Targets vulnerabilities in wireless networks. A cybercriminal exploiting a vulnerability can perform various malicious actions, such as installing malicious software (malware), running malicious code, and stealing sensitive data. The following cybersecurity agencies coauthored this joint cybersecurity advisory. U.s., australian, canadian, new zealand, and uk cybersecurity authorities assess, in 2021, malicious cyber actors aggressively.. Examples Of Security Exploits.
From secudemy.com
Common Type of Exploits Examples Of Security Exploits Gets physical access to devices or systems. Exploits that target specific vulnerabilities. The following cybersecurity agencies coauthored this joint cybersecurity advisory. Targets vulnerabilities in wireless networks. Cves are identifiers given to publicly disclosed information security flaws, and attackers can use them to exploit vulnerable systems. U.s., australian, canadian, new zealand, and uk cybersecurity authorities assess, in 2021, malicious cyber actors. Examples Of Security Exploits.
From www.toptal.com
10 Common Security Vulnerabilities Toptal® Examples Of Security Exploits Exploits that target specific vulnerabilities. We review the 7 most common types of vulnerabilities including: A cybercriminal exploiting a vulnerability can perform various malicious actions, such as installing malicious software (malware), running malicious code, and stealing sensitive data. U.s., australian, canadian, new zealand, and uk cybersecurity authorities assess, in 2021, malicious cyber actors aggressively. Further, we will take a look. Examples Of Security Exploits.
From www.spiceworks.com
What Is a Security Vulnerability? Definition, Types, and Best Practices Examples Of Security Exploits Further, we will take a look at the most common ones. Targets vulnerabilities in wireless networks. The following cybersecurity agencies coauthored this joint cybersecurity advisory. U.s., australian, canadian, new zealand, and uk cybersecurity authorities assess, in 2021, malicious cyber actors aggressively. Exploits that target specific vulnerabilities. Cves are identifiers given to publicly disclosed information security flaws, and attackers can use. Examples Of Security Exploits.
From www.wallarm.com
What is Exploit and How to Protect Your Computer? Examples Of Security Exploits Cves are identifiers given to publicly disclosed information security flaws, and attackers can use them to exploit vulnerable systems. Exploits that target specific vulnerabilities. A cybercriminal exploiting a vulnerability can perform various malicious actions, such as installing malicious software (malware), running malicious code, and stealing sensitive data. The following cybersecurity agencies coauthored this joint cybersecurity advisory. Further, we will take. Examples Of Security Exploits.
From www.adlice.com
Exploits Definition, Exploit Kits (Part 1) • Adlice Software Examples Of Security Exploits Gets physical access to devices or systems. We review the 7 most common types of vulnerabilities including: Exploits that target specific vulnerabilities. U.s., australian, canadian, new zealand, and uk cybersecurity authorities assess, in 2021, malicious cyber actors aggressively. Cves are identifiers given to publicly disclosed information security flaws, and attackers can use them to exploit vulnerable systems. Targets vulnerabilities in. Examples Of Security Exploits.
From www.spiceworks.com
What Is a Security Vulnerability? Definition, Types, and Best Practices Examples Of Security Exploits Targets vulnerabilities in wireless networks. The following cybersecurity agencies coauthored this joint cybersecurity advisory. Cves are identifiers given to publicly disclosed information security flaws, and attackers can use them to exploit vulnerable systems. We review the 7 most common types of vulnerabilities including: U.s., australian, canadian, new zealand, and uk cybersecurity authorities assess, in 2021, malicious cyber actors aggressively. Gets. Examples Of Security Exploits.
From www.cybereason.com
The Security Value of Exploit Protection Examples Of Security Exploits U.s., australian, canadian, new zealand, and uk cybersecurity authorities assess, in 2021, malicious cyber actors aggressively. The following cybersecurity agencies coauthored this joint cybersecurity advisory. Targets vulnerabilities in wireless networks. Further, we will take a look at the most common ones. A cybercriminal exploiting a vulnerability can perform various malicious actions, such as installing malicious software (malware), running malicious code,. Examples Of Security Exploits.
From tesrex.com
5 Stages Of A Malware Attack Cyber Security Tesrex Examples Of Security Exploits We review the 7 most common types of vulnerabilities including: The following cybersecurity agencies coauthored this joint cybersecurity advisory. U.s., australian, canadian, new zealand, and uk cybersecurity authorities assess, in 2021, malicious cyber actors aggressively. Gets physical access to devices or systems. A cybercriminal exploiting a vulnerability can perform various malicious actions, such as installing malicious software (malware), running malicious. Examples Of Security Exploits.
From www.slideserve.com
PPT Malicious Code and Intruders PowerPoint Presentation, free Examples Of Security Exploits Exploits that target specific vulnerabilities. A cybercriminal exploiting a vulnerability can perform various malicious actions, such as installing malicious software (malware), running malicious code, and stealing sensitive data. Cves are identifiers given to publicly disclosed information security flaws, and attackers can use them to exploit vulnerable systems. Gets physical access to devices or systems. The following cybersecurity agencies coauthored this. Examples Of Security Exploits.
From www.varonis.com
Government Hacking Exploits, Examples and Prevention Tips Examples Of Security Exploits We review the 7 most common types of vulnerabilities including: Further, we will take a look at the most common ones. The following cybersecurity agencies coauthored this joint cybersecurity advisory. Cves are identifiers given to publicly disclosed information security flaws, and attackers can use them to exploit vulnerable systems. Targets vulnerabilities in wireless networks. Exploits that target specific vulnerabilities. A. Examples Of Security Exploits.
From es.gridinsoft.com
¿Qué es Exploit? Tipos de exploits y cómo funcionan. Gridinsoft Examples Of Security Exploits We review the 7 most common types of vulnerabilities including: Exploits that target specific vulnerabilities. Further, we will take a look at the most common ones. Targets vulnerabilities in wireless networks. The following cybersecurity agencies coauthored this joint cybersecurity advisory. U.s., australian, canadian, new zealand, and uk cybersecurity authorities assess, in 2021, malicious cyber actors aggressively. Cves are identifiers given. Examples Of Security Exploits.