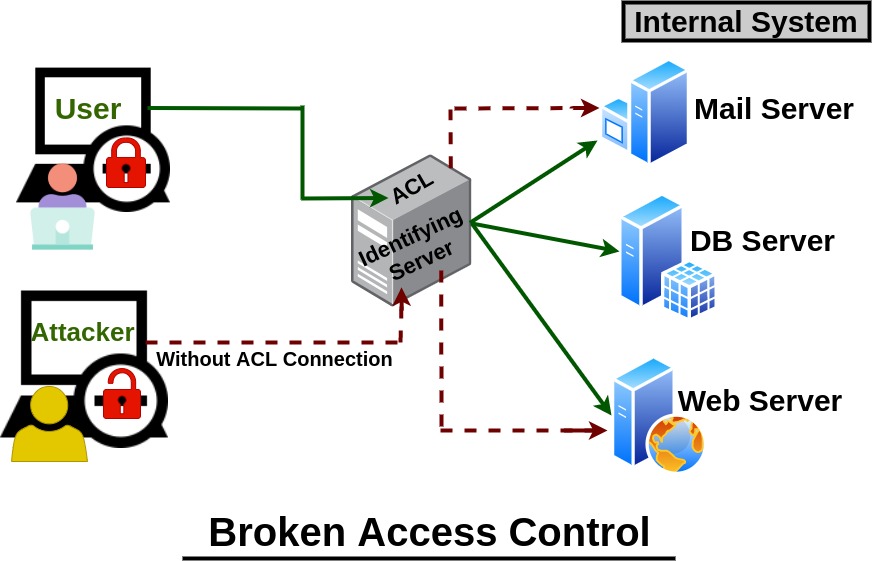
Broken Access Control Attack Example . Rate limit api and controller access to minimize the harm from automated attack tooling. Broken access control vulnerabilities exist when a user can access resources or perform actions that they are not. What is owasp broken access control? Examples of broken access controls. Examples of broken access control attacks. 4 owasp broken access control attack examples. Broken access control vulnerabilities refer to situations where access control mechanisms fail to enforce proper restrictions on user access to resources or data. Stateful session identifiers should be invalidated on the server after logout. What is broken access control? Types and causes of broken access control. Log access control failures, alert admins when appropriate (e.g., repeated failures).
from cloudkul.com
Examples of broken access controls. Broken access control vulnerabilities exist when a user can access resources or perform actions that they are not. Log access control failures, alert admins when appropriate (e.g., repeated failures). 4 owasp broken access control attack examples. Examples of broken access control attacks. Stateful session identifiers should be invalidated on the server after logout. Rate limit api and controller access to minimize the harm from automated attack tooling. Broken access control vulnerabilities refer to situations where access control mechanisms fail to enforce proper restrictions on user access to resources or data. What is broken access control? What is owasp broken access control?
Comprehension The Risk of "Broken Authentication & Broken Access
Broken Access Control Attack Example Rate limit api and controller access to minimize the harm from automated attack tooling. Types and causes of broken access control. Examples of broken access controls. Broken access control vulnerabilities refer to situations where access control mechanisms fail to enforce proper restrictions on user access to resources or data. Stateful session identifiers should be invalidated on the server after logout. Rate limit api and controller access to minimize the harm from automated attack tooling. Log access control failures, alert admins when appropriate (e.g., repeated failures). What is owasp broken access control? 4 owasp broken access control attack examples. What is broken access control? Broken access control vulnerabilities exist when a user can access resources or perform actions that they are not. Examples of broken access control attacks.
From www.immunebytes.com
Broken Access Control Vulnerability All You Need to Know Broken Access Control Attack Example Examples of broken access controls. What is owasp broken access control? 4 owasp broken access control attack examples. Broken access control vulnerabilities exist when a user can access resources or perform actions that they are not. What is broken access control? Log access control failures, alert admins when appropriate (e.g., repeated failures). Broken access control vulnerabilities refer to situations where. Broken Access Control Attack Example.
From www.immunebytes.com
Broken Access Control Vulnerability All You Need to Know Broken Access Control Attack Example What is broken access control? Broken access control vulnerabilities refer to situations where access control mechanisms fail to enforce proper restrictions on user access to resources or data. Examples of broken access controls. Types and causes of broken access control. Log access control failures, alert admins when appropriate (e.g., repeated failures). Broken access control vulnerabilities exist when a user can. Broken Access Control Attack Example.
From www.youtube.com
PART 1 BROKEN ACCESS CONTROL VULNERABILITY ATTACK 2023 bugbounty Broken Access Control Attack Example Examples of broken access controls. Log access control failures, alert admins when appropriate (e.g., repeated failures). What is owasp broken access control? Rate limit api and controller access to minimize the harm from automated attack tooling. What is broken access control? 4 owasp broken access control attack examples. Broken access control vulnerabilities refer to situations where access control mechanisms fail. Broken Access Control Attack Example.
From medium.com
A Comprehensive Guide to Broken Access Control PurpleBox Security Broken Access Control Attack Example What is owasp broken access control? Broken access control vulnerabilities exist when a user can access resources or perform actions that they are not. Stateful session identifiers should be invalidated on the server after logout. What is broken access control? Log access control failures, alert admins when appropriate (e.g., repeated failures). Examples of broken access control attacks. Broken access control. Broken Access Control Attack Example.
From nordlayer.com
What is Broken Access Control? NordLayer Learn Broken Access Control Attack Example Rate limit api and controller access to minimize the harm from automated attack tooling. 4 owasp broken access control attack examples. Broken access control vulnerabilities refer to situations where access control mechanisms fail to enforce proper restrictions on user access to resources or data. Stateful session identifiers should be invalidated on the server after logout. Types and causes of broken. Broken Access Control Attack Example.
From prophaze.com
What Is Meant By Broken Access Control? Cloud WAF Broken Access Control Attack Example What is owasp broken access control? Examples of broken access control attacks. Examples of broken access controls. Log access control failures, alert admins when appropriate (e.g., repeated failures). Rate limit api and controller access to minimize the harm from automated attack tooling. Stateful session identifiers should be invalidated on the server after logout. Broken access control vulnerabilities exist when a. Broken Access Control Attack Example.
From www.immunebytes.com
Broken Access Control Vulnerability All You Need to Know Broken Access Control Attack Example What is broken access control? Broken access control vulnerabilities refer to situations where access control mechanisms fail to enforce proper restrictions on user access to resources or data. Examples of broken access controls. Log access control failures, alert admins when appropriate (e.g., repeated failures). Rate limit api and controller access to minimize the harm from automated attack tooling. What is. Broken Access Control Attack Example.
From www.pullrequest.com
How to Catch Broken Access Control Security Vulnerabilities in Code Broken Access Control Attack Example Examples of broken access control attacks. Broken access control vulnerabilities refer to situations where access control mechanisms fail to enforce proper restrictions on user access to resources or data. What is owasp broken access control? Broken access control vulnerabilities exist when a user can access resources or perform actions that they are not. Stateful session identifiers should be invalidated on. Broken Access Control Attack Example.
From xcalibyte.com
OWASP 5 Broken Access Control Xcalibyte Software Application Broken Access Control Attack Example Examples of broken access control attacks. Stateful session identifiers should be invalidated on the server after logout. What is broken access control? Broken access control vulnerabilities refer to situations where access control mechanisms fail to enforce proper restrictions on user access to resources or data. Log access control failures, alert admins when appropriate (e.g., repeated failures). Types and causes of. Broken Access Control Attack Example.
From www.polar.security
A StepbyStep Guide To Broken Access Control Attacks Polar Security Broken Access Control Attack Example Log access control failures, alert admins when appropriate (e.g., repeated failures). Broken access control vulnerabilities refer to situations where access control mechanisms fail to enforce proper restrictions on user access to resources or data. 4 owasp broken access control attack examples. What is owasp broken access control? Types and causes of broken access control. Examples of broken access controls. Rate. Broken Access Control Attack Example.
From themindstudios.com
How to Secure a site from Hackers Vulnerabilities + List of Tips Broken Access Control Attack Example 4 owasp broken access control attack examples. Examples of broken access controls. Rate limit api and controller access to minimize the harm from automated attack tooling. Stateful session identifiers should be invalidated on the server after logout. What is broken access control? Types and causes of broken access control. Log access control failures, alert admins when appropriate (e.g., repeated failures).. Broken Access Control Attack Example.
From cheapsslsecurity.com
What Are the OWASP Top 10 Vulnerabilities (And How to Mitigate Them)? Broken Access Control Attack Example What is owasp broken access control? Log access control failures, alert admins when appropriate (e.g., repeated failures). What is broken access control? Examples of broken access controls. Examples of broken access control attacks. Types and causes of broken access control. Broken access control vulnerabilities exist when a user can access resources or perform actions that they are not. Broken access. Broken Access Control Attack Example.
From brightsec.com
Broken Access Control Attack Examples and 4 Defensive Measures Broken Access Control Attack Example Broken access control vulnerabilities refer to situations where access control mechanisms fail to enforce proper restrictions on user access to resources or data. Rate limit api and controller access to minimize the harm from automated attack tooling. What is broken access control? Stateful session identifiers should be invalidated on the server after logout. Types and causes of broken access control.. Broken Access Control Attack Example.
From eshoptrip.se
OWASP Top 10 1 Broken Access Control and 2 Cryptographic Failures Broken Access Control Attack Example Broken access control vulnerabilities exist when a user can access resources or perform actions that they are not. What is broken access control? Log access control failures, alert admins when appropriate (e.g., repeated failures). Broken access control vulnerabilities refer to situations where access control mechanisms fail to enforce proper restrictions on user access to resources or data. Examples of broken. Broken Access Control Attack Example.
From www.youtube.com
Broken Access Control Explained YouTube Broken Access Control Attack Example What is owasp broken access control? Broken access control vulnerabilities refer to situations where access control mechanisms fail to enforce proper restrictions on user access to resources or data. Examples of broken access controls. What is broken access control? 4 owasp broken access control attack examples. Broken access control vulnerabilities exist when a user can access resources or perform actions. Broken Access Control Attack Example.
From sucuri.net
What is Broken Access Control Sucuri Broken Access Control Attack Example Log access control failures, alert admins when appropriate (e.g., repeated failures). What is broken access control? 4 owasp broken access control attack examples. Broken access control vulnerabilities refer to situations where access control mechanisms fail to enforce proper restrictions on user access to resources or data. Broken access control vulnerabilities exist when a user can access resources or perform actions. Broken Access Control Attack Example.
From www.codelivly.com
Securing Your Digital Assets A Step by Step Guide To Broken Access Broken Access Control Attack Example What is owasp broken access control? Stateful session identifiers should be invalidated on the server after logout. Examples of broken access control attacks. Broken access control vulnerabilities exist when a user can access resources or perform actions that they are not. What is broken access control? Rate limit api and controller access to minimize the harm from automated attack tooling.. Broken Access Control Attack Example.
From yunusemresert.com
A Comprehensive Guide to Broken Access Control YUNUS EMRE SERT Broken Access Control Attack Example Log access control failures, alert admins when appropriate (e.g., repeated failures). Stateful session identifiers should be invalidated on the server after logout. Examples of broken access controls. Examples of broken access control attacks. What is owasp broken access control? 4 owasp broken access control attack examples. What is broken access control? Broken access control vulnerabilities refer to situations where access. Broken Access Control Attack Example.
From www.authgear.com
What is Broken Access Control Vulnerability And How to Prevent it Broken Access Control Attack Example Examples of broken access controls. Stateful session identifiers should be invalidated on the server after logout. Types and causes of broken access control. Rate limit api and controller access to minimize the harm from automated attack tooling. 4 owasp broken access control attack examples. Log access control failures, alert admins when appropriate (e.g., repeated failures). Examples of broken access control. Broken Access Control Attack Example.
From www.youtube.com
broken access control attack LAB شرح ثغره YouTube Broken Access Control Attack Example What is broken access control? Log access control failures, alert admins when appropriate (e.g., repeated failures). What is owasp broken access control? Types and causes of broken access control. Broken access control vulnerabilities exist when a user can access resources or perform actions that they are not. Rate limit api and controller access to minimize the harm from automated attack. Broken Access Control Attack Example.
From www.thecybersploit.com
OWASP Broken access control attack The Cybersploit Broken Access Control Attack Example Broken access control vulnerabilities exist when a user can access resources or perform actions that they are not. What is owasp broken access control? Examples of broken access control attacks. 4 owasp broken access control attack examples. Stateful session identifiers should be invalidated on the server after logout. Examples of broken access controls. Broken access control vulnerabilities refer to situations. Broken Access Control Attack Example.
From theos-cyber.com
Deep Dive Guide to Broken Access Control Delivering Cyber Resilience Broken Access Control Attack Example Broken access control vulnerabilities refer to situations where access control mechanisms fail to enforce proper restrictions on user access to resources or data. What is owasp broken access control? Types and causes of broken access control. 4 owasp broken access control attack examples. Stateful session identifiers should be invalidated on the server after logout. What is broken access control? Log. Broken Access Control Attack Example.
From www.thecybersploit.com
OWASP Broken access control attack The Cybersploit Broken Access Control Attack Example Broken access control vulnerabilities refer to situations where access control mechanisms fail to enforce proper restrictions on user access to resources or data. 4 owasp broken access control attack examples. What is owasp broken access control? Types and causes of broken access control. Broken access control vulnerabilities exist when a user can access resources or perform actions that they are. Broken Access Control Attack Example.
From www.immunebytes.com
Broken Access Control Vulnerability All You Need to Know Broken Access Control Attack Example Log access control failures, alert admins when appropriate (e.g., repeated failures). What is owasp broken access control? Broken access control vulnerabilities exist when a user can access resources or perform actions that they are not. 4 owasp broken access control attack examples. Stateful session identifiers should be invalidated on the server after logout. Types and causes of broken access control.. Broken Access Control Attack Example.
From www.immunebytes.com
Broken Access Control Vulnerability All You Need to Know Broken Access Control Attack Example Examples of broken access control attacks. Broken access control vulnerabilities refer to situations where access control mechanisms fail to enforce proper restrictions on user access to resources or data. Types and causes of broken access control. What is owasp broken access control? Broken access control vulnerabilities exist when a user can access resources or perform actions that they are not.. Broken Access Control Attack Example.
From www.immunebytes.com
Broken Access Control Vulnerability All You Need to Know Broken Access Control Attack Example Broken access control vulnerabilities refer to situations where access control mechanisms fail to enforce proper restrictions on user access to resources or data. What is owasp broken access control? Log access control failures, alert admins when appropriate (e.g., repeated failures). Stateful session identifiers should be invalidated on the server after logout. What is broken access control? Rate limit api and. Broken Access Control Attack Example.
From www.eccouncil.org
How to Prevent Broken Access Control Vulnerability Broken Access Control Attack Example Types and causes of broken access control. Stateful session identifiers should be invalidated on the server after logout. Log access control failures, alert admins when appropriate (e.g., repeated failures). Examples of broken access controls. Broken access control vulnerabilities refer to situations where access control mechanisms fail to enforce proper restrictions on user access to resources or data. 4 owasp broken. Broken Access Control Attack Example.
From aspiainfotech.com
Broken Access Control ASPIA Infotech Blog Broken Access Control Attack Example Broken access control vulnerabilities refer to situations where access control mechanisms fail to enforce proper restrictions on user access to resources or data. Broken access control vulnerabilities exist when a user can access resources or perform actions that they are not. Examples of broken access controls. Stateful session identifiers should be invalidated on the server after logout. Examples of broken. Broken Access Control Attack Example.
From practonet.com
Broken Access Control Cyber Security, Networking, Technology Courses Broken Access Control Attack Example Log access control failures, alert admins when appropriate (e.g., repeated failures). Broken access control vulnerabilities exist when a user can access resources or perform actions that they are not. Broken access control vulnerabilities refer to situations where access control mechanisms fail to enforce proper restrictions on user access to resources or data. Examples of broken access control attacks. What is. Broken Access Control Attack Example.
From sucuri.net
What is Broken Access Control Sucuri Broken Access Control Attack Example Broken access control vulnerabilities exist when a user can access resources or perform actions that they are not. Log access control failures, alert admins when appropriate (e.g., repeated failures). Examples of broken access controls. Types and causes of broken access control. Stateful session identifiers should be invalidated on the server after logout. What is owasp broken access control? Broken access. Broken Access Control Attack Example.
From www.immunebytes.com
Broken Access Control Vulnerability All You Need to Know Broken Access Control Attack Example Broken access control vulnerabilities exist when a user can access resources or perform actions that they are not. 4 owasp broken access control attack examples. What is broken access control? Rate limit api and controller access to minimize the harm from automated attack tooling. Broken access control vulnerabilities refer to situations where access control mechanisms fail to enforce proper restrictions. Broken Access Control Attack Example.
From learn.snyk.io
Broken Access Control Tutorials & Examples Snyk Learn Broken Access Control Attack Example Types and causes of broken access control. What is owasp broken access control? Examples of broken access control attacks. What is broken access control? Stateful session identifiers should be invalidated on the server after logout. Log access control failures, alert admins when appropriate (e.g., repeated failures). Rate limit api and controller access to minimize the harm from automated attack tooling.. Broken Access Control Attack Example.
From www.youtube.com
Broken Access Control Vulnerability Attack 2023 owasptop10 Broken Access Control Attack Example What is broken access control? Log access control failures, alert admins when appropriate (e.g., repeated failures). Types and causes of broken access control. What is owasp broken access control? 4 owasp broken access control attack examples. Examples of broken access control attacks. Stateful session identifiers should be invalidated on the server after logout. Examples of broken access controls. Rate limit. Broken Access Control Attack Example.
From hackernoon.com
What is Broken Access Control and Why Should You Care? HackerNoon Broken Access Control Attack Example Broken access control vulnerabilities refer to situations where access control mechanisms fail to enforce proper restrictions on user access to resources or data. Rate limit api and controller access to minimize the harm from automated attack tooling. Stateful session identifiers should be invalidated on the server after logout. Examples of broken access control attacks. 4 owasp broken access control attack. Broken Access Control Attack Example.
From cloudkul.com
Comprehension The Risk of "Broken Authentication & Broken Access Broken Access Control Attack Example Broken access control vulnerabilities refer to situations where access control mechanisms fail to enforce proper restrictions on user access to resources or data. 4 owasp broken access control attack examples. Rate limit api and controller access to minimize the harm from automated attack tooling. What is owasp broken access control? Examples of broken access control attacks. Types and causes of. Broken Access Control Attack Example.