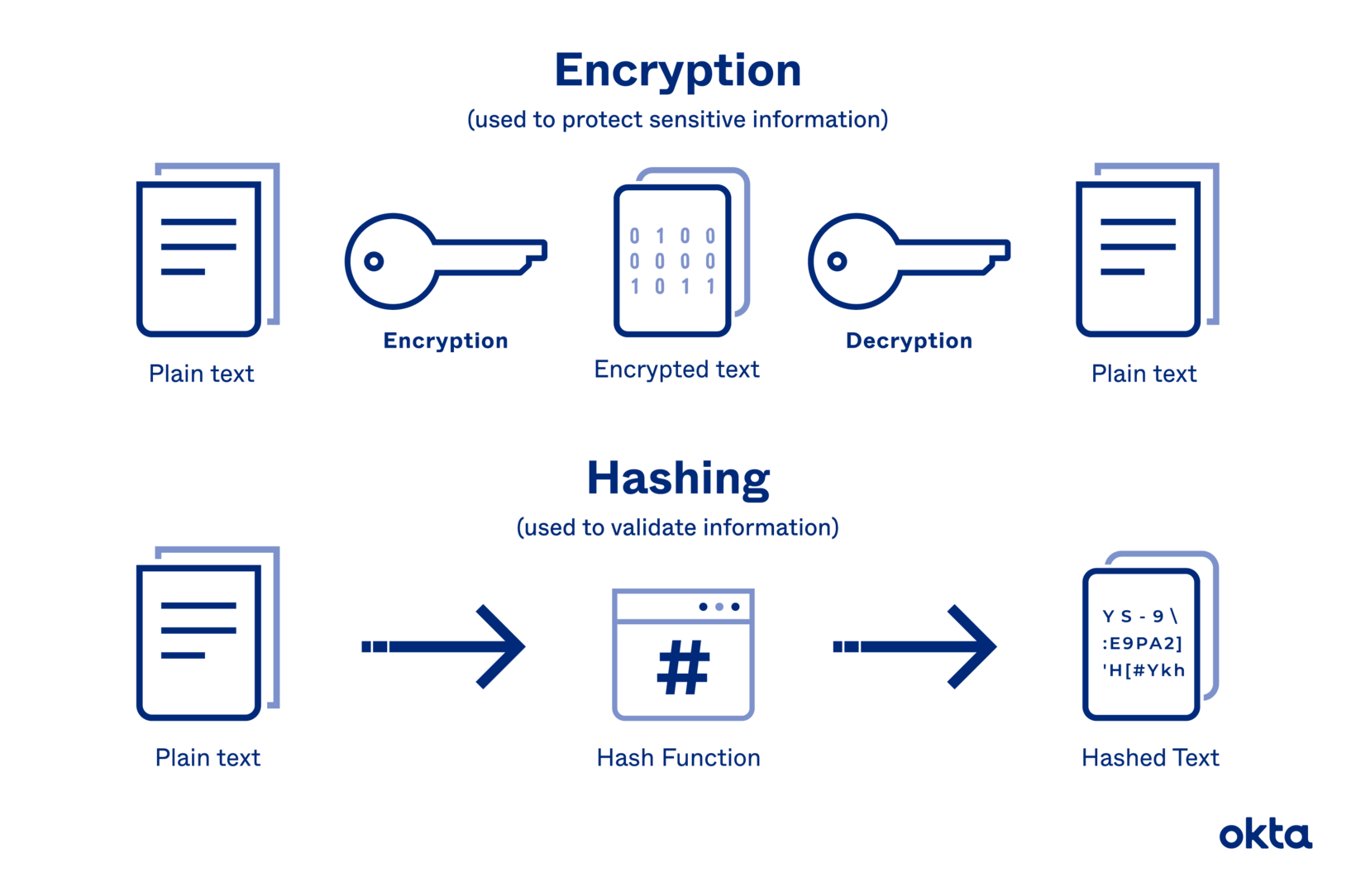
Computer Hashing . Hashing in data structures refers to the process of transforming a given key to another value. Dive deeply into the topic of hashing: Unlike standard encryption, hashing is always. It involves mapping data to a specific index in a hash table using a hash. How it works, hash functions, algorithms, and potential attacks. Hashing is an improvement technique over the direct access table. Hashing is the practice of transforming a given key or string of characters into another value for the purpose of security. The idea is to use a hash function that converts a given phone number or any other key to a smaller. Our guide explores the principles of hashing, explaining how cryptographic hash functions work and their importance in protecting sensitive data. The primary goal of hashing is to ensure data integrity and validate the original data.
from www.okta.com
Unlike standard encryption, hashing is always. Hashing is an improvement technique over the direct access table. Dive deeply into the topic of hashing: How it works, hash functions, algorithms, and potential attacks. Hashing is the practice of transforming a given key or string of characters into another value for the purpose of security. Our guide explores the principles of hashing, explaining how cryptographic hash functions work and their importance in protecting sensitive data. It involves mapping data to a specific index in a hash table using a hash. The idea is to use a hash function that converts a given phone number or any other key to a smaller. The primary goal of hashing is to ensure data integrity and validate the original data. Hashing in data structures refers to the process of transforming a given key to another value.
Hashing vs. Encryption Definitions & Differences Okta
Computer Hashing Unlike standard encryption, hashing is always. Dive deeply into the topic of hashing: Hashing in data structures refers to the process of transforming a given key to another value. Hashing is an improvement technique over the direct access table. The primary goal of hashing is to ensure data integrity and validate the original data. How it works, hash functions, algorithms, and potential attacks. Unlike standard encryption, hashing is always. Hashing is the practice of transforming a given key or string of characters into another value for the purpose of security. Our guide explores the principles of hashing, explaining how cryptographic hash functions work and their importance in protecting sensitive data. It involves mapping data to a specific index in a hash table using a hash. The idea is to use a hash function that converts a given phone number or any other key to a smaller.
From notlaura.com
hashtable Lara Schenck Computer Hashing How it works, hash functions, algorithms, and potential attacks. The idea is to use a hash function that converts a given phone number or any other key to a smaller. Hashing is an improvement technique over the direct access table. It involves mapping data to a specific index in a hash table using a hash. Our guide explores the principles. Computer Hashing.
From www.geeksforgeeks.org
Hashing Data Structure Computer Hashing How it works, hash functions, algorithms, and potential attacks. Dive deeply into the topic of hashing: Hashing is the practice of transforming a given key or string of characters into another value for the purpose of security. The idea is to use a hash function that converts a given phone number or any other key to a smaller. Hashing in. Computer Hashing.
From pcforum.hu
A Windowst másolhatja majd az Android az alkalmazások kezelésében PC Computer Hashing Our guide explores the principles of hashing, explaining how cryptographic hash functions work and their importance in protecting sensitive data. Hashing is the practice of transforming a given key or string of characters into another value for the purpose of security. Unlike standard encryption, hashing is always. The primary goal of hashing is to ensure data integrity and validate the. Computer Hashing.
From 101blockchains.com
Cryptographic Hashing A Beginner’s Guide 101 Blockchains Computer Hashing The idea is to use a hash function that converts a given phone number or any other key to a smaller. Hashing is an improvement technique over the direct access table. The primary goal of hashing is to ensure data integrity and validate the original data. It involves mapping data to a specific index in a hash table using a. Computer Hashing.
From blockgeeks.com
Video Guide What is Hashing? Blockgeeks Computer Hashing How it works, hash functions, algorithms, and potential attacks. The idea is to use a hash function that converts a given phone number or any other key to a smaller. The primary goal of hashing is to ensure data integrity and validate the original data. Hashing in data structures refers to the process of transforming a given key to another. Computer Hashing.
From xeushack.com
What Is a Hash? Hacking Tutorials by Xeus Computer Hashing Our guide explores the principles of hashing, explaining how cryptographic hash functions work and their importance in protecting sensitive data. It involves mapping data to a specific index in a hash table using a hash. Hashing is an improvement technique over the direct access table. Dive deeply into the topic of hashing: Hashing is the practice of transforming a given. Computer Hashing.
From www.thesslstore.com
What Is a Hash Function in Cryptography? A Beginner’s Guide Hashed Computer Hashing Our guide explores the principles of hashing, explaining how cryptographic hash functions work and their importance in protecting sensitive data. It involves mapping data to a specific index in a hash table using a hash. Dive deeply into the topic of hashing: Hashing in data structures refers to the process of transforming a given key to another value. The idea. Computer Hashing.
From www.youtube.com
Hash Tables Explained in Simple Terms YouTube Computer Hashing How it works, hash functions, algorithms, and potential attacks. Dive deeply into the topic of hashing: The idea is to use a hash function that converts a given phone number or any other key to a smaller. Hashing is an improvement technique over the direct access table. Our guide explores the principles of hashing, explaining how cryptographic hash functions work. Computer Hashing.
From www.youtube.com
How to type the (hash) sign with a UK keyboard YouTube Computer Hashing It involves mapping data to a specific index in a hash table using a hash. The idea is to use a hash function that converts a given phone number or any other key to a smaller. Hashing is the practice of transforming a given key or string of characters into another value for the purpose of security. How it works,. Computer Hashing.
From www.youtube.com
Hashing Explained YouTube Computer Hashing Hashing in data structures refers to the process of transforming a given key to another value. How it works, hash functions, algorithms, and potential attacks. Hashing is the practice of transforming a given key or string of characters into another value for the purpose of security. Unlike standard encryption, hashing is always. Dive deeply into the topic of hashing: It. Computer Hashing.
From auth0.com
How to Hash Passwords OneWay Road to Enhanced Security Computer Hashing Hashing is an improvement technique over the direct access table. It involves mapping data to a specific index in a hash table using a hash. Unlike standard encryption, hashing is always. Hashing in data structures refers to the process of transforming a given key to another value. Dive deeply into the topic of hashing: Our guide explores the principles of. Computer Hashing.
From www.wisegeek.com
What are Hash Files? (with picture) Computer Hashing It involves mapping data to a specific index in a hash table using a hash. Our guide explores the principles of hashing, explaining how cryptographic hash functions work and their importance in protecting sensitive data. Hashing is the practice of transforming a given key or string of characters into another value for the purpose of security. How it works, hash. Computer Hashing.
From medium.com
How to implement a HashTable using Swift Flawless iOS Medium Computer Hashing The primary goal of hashing is to ensure data integrity and validate the original data. Hashing is an improvement technique over the direct access table. Dive deeply into the topic of hashing: How it works, hash functions, algorithms, and potential attacks. Unlike standard encryption, hashing is always. Hashing is the practice of transforming a given key or string of characters. Computer Hashing.
From mavink.com
Types Of Hashing Computer Hashing Dive deeply into the topic of hashing: Our guide explores the principles of hashing, explaining how cryptographic hash functions work and their importance in protecting sensitive data. Hashing in data structures refers to the process of transforming a given key to another value. How it works, hash functions, algorithms, and potential attacks. The idea is to use a hash function. Computer Hashing.
From www.ionos.com
Hash functions definition, usage, and examples IONOS Computer Hashing How it works, hash functions, algorithms, and potential attacks. Our guide explores the principles of hashing, explaining how cryptographic hash functions work and their importance in protecting sensitive data. Dive deeply into the topic of hashing: The primary goal of hashing is to ensure data integrity and validate the original data. Hashing is the practice of transforming a given key. Computer Hashing.
From javachallengers.com
Master the Fundamentals of Hashing and Ace the Systems Design Interview Computer Hashing It involves mapping data to a specific index in a hash table using a hash. Dive deeply into the topic of hashing: Our guide explores the principles of hashing, explaining how cryptographic hash functions work and their importance in protecting sensitive data. The idea is to use a hash function that converts a given phone number or any other key. Computer Hashing.
From techvidvan.com
Hash Table Hashing in Data Structure TechVidvan Computer Hashing Hashing is an improvement technique over the direct access table. It involves mapping data to a specific index in a hash table using a hash. Hashing in data structures refers to the process of transforming a given key to another value. Hashing is the practice of transforming a given key or string of characters into another value for the purpose. Computer Hashing.
From www.dreamstime.com
Computer desktop hash sign stock photo. Image of communication 105060038 Computer Hashing Unlike standard encryption, hashing is always. Hashing is an improvement technique over the direct access table. Hashing is the practice of transforming a given key or string of characters into another value for the purpose of security. Our guide explores the principles of hashing, explaining how cryptographic hash functions work and their importance in protecting sensitive data. How it works,. Computer Hashing.
From indodax.com
Mengapa Hashing Penting? Pahami Konsep dan Manfaatnya Computer Hashing How it works, hash functions, algorithms, and potential attacks. Our guide explores the principles of hashing, explaining how cryptographic hash functions work and their importance in protecting sensitive data. Hashing is an improvement technique over the direct access table. Hashing in data structures refers to the process of transforming a given key to another value. Hashing is the practice of. Computer Hashing.
From www.youtube.com
Hash Algorithms A Level Computer Science YouTube Computer Hashing Our guide explores the principles of hashing, explaining how cryptographic hash functions work and their importance in protecting sensitive data. Unlike standard encryption, hashing is always. How it works, hash functions, algorithms, and potential attacks. Hashing is an improvement technique over the direct access table. The idea is to use a hash function that converts a given phone number or. Computer Hashing.
From codeahoy.com
Hash Functions CodeAhoy Computer Hashing Unlike standard encryption, hashing is always. Hashing in data structures refers to the process of transforming a given key to another value. Dive deeply into the topic of hashing: Hashing is an improvement technique over the direct access table. Our guide explores the principles of hashing, explaining how cryptographic hash functions work and their importance in protecting sensitive data. The. Computer Hashing.
From www.dreamstime.com
Hash sign on computer stock photo. Image of followers 105060010 Computer Hashing Hashing is an improvement technique over the direct access table. The primary goal of hashing is to ensure data integrity and validate the original data. Unlike standard encryption, hashing is always. Hashing in data structures refers to the process of transforming a given key to another value. How it works, hash functions, algorithms, and potential attacks. Dive deeply into the. Computer Hashing.
From www.pinterest.com
md5 Hash Generator Generator, Hashing, call screenshot Computer Hashing Hashing is the practice of transforming a given key or string of characters into another value for the purpose of security. The primary goal of hashing is to ensure data integrity and validate the original data. Dive deeply into the topic of hashing: Hashing is an improvement technique over the direct access table. Hashing in data structures refers to the. Computer Hashing.
From www.scribd.com
HASHING PDF Computer Data Computing Computer Hashing How it works, hash functions, algorithms, and potential attacks. It involves mapping data to a specific index in a hash table using a hash. The idea is to use a hash function that converts a given phone number or any other key to a smaller. Dive deeply into the topic of hashing: Our guide explores the principles of hashing, explaining. Computer Hashing.
From www.thelazyadministrator.com
Get a New Computer’s Auto Pilot Hash Without Going Through the Out of Computer Hashing It involves mapping data to a specific index in a hash table using a hash. The primary goal of hashing is to ensure data integrity and validate the original data. The idea is to use a hash function that converts a given phone number or any other key to a smaller. Hashing is an improvement technique over the direct access. Computer Hashing.
From www.codecademy.com
What Is Hashing, and How Does It Work? Codecademy Blog Computer Hashing Hashing in data structures refers to the process of transforming a given key to another value. The primary goal of hashing is to ensure data integrity and validate the original data. Hashing is the practice of transforming a given key or string of characters into another value for the purpose of security. Dive deeply into the topic of hashing: Unlike. Computer Hashing.
From www.baeldung.com
Hashing Separate Chaining Baeldung on Computer Science Computer Hashing It involves mapping data to a specific index in a hash table using a hash. The primary goal of hashing is to ensure data integrity and validate the original data. How it works, hash functions, algorithms, and potential attacks. Dive deeply into the topic of hashing: The idea is to use a hash function that converts a given phone number. Computer Hashing.
From www.youtube.com
How To Get Windows 10 Hardware Hash Using Powershell Script YouTube Computer Hashing Hashing is an improvement technique over the direct access table. How it works, hash functions, algorithms, and potential attacks. Our guide explores the principles of hashing, explaining how cryptographic hash functions work and their importance in protecting sensitive data. It involves mapping data to a specific index in a hash table using a hash. Dive deeply into the topic of. Computer Hashing.
From thecleverest.com
Understanding MD5 Hashes and Security The Cleverest Computer Hashing How it works, hash functions, algorithms, and potential attacks. Hashing in data structures refers to the process of transforming a given key to another value. The idea is to use a hash function that converts a given phone number or any other key to a smaller. Our guide explores the principles of hashing, explaining how cryptographic hash functions work and. Computer Hashing.
From www.linkedin.com
What is Hashing? Computer Hashing The idea is to use a hash function that converts a given phone number or any other key to a smaller. Unlike standard encryption, hashing is always. How it works, hash functions, algorithms, and potential attacks. Hashing is the practice of transforming a given key or string of characters into another value for the purpose of security. It involves mapping. Computer Hashing.
From www.okta.com
Hashing vs. Encryption Definitions & Differences Okta Computer Hashing It involves mapping data to a specific index in a hash table using a hash. Hashing is the practice of transforming a given key or string of characters into another value for the purpose of security. Hashing is an improvement technique over the direct access table. How it works, hash functions, algorithms, and potential attacks. The idea is to use. Computer Hashing.
From www.youtube.com
Better Hash Functions Intro to Computer Science YouTube Computer Hashing The idea is to use a hash function that converts a given phone number or any other key to a smaller. Dive deeply into the topic of hashing: Hashing is an improvement technique over the direct access table. Hashing in data structures refers to the process of transforming a given key to another value. How it works, hash functions, algorithms,. Computer Hashing.
From cathcartha.co.uk
21 bitcoin computer hash rate testing Computer Hashing Hashing is the practice of transforming a given key or string of characters into another value for the purpose of security. Hashing in data structures refers to the process of transforming a given key to another value. The idea is to use a hash function that converts a given phone number or any other key to a smaller. It involves. Computer Hashing.
From www.dreamstime.com
Desktop computer hash sign stock photo. Image of workspace 105060114 Computer Hashing Unlike standard encryption, hashing is always. Dive deeply into the topic of hashing: Hashing is the practice of transforming a given key or string of characters into another value for the purpose of security. Our guide explores the principles of hashing, explaining how cryptographic hash functions work and their importance in protecting sensitive data. The primary goal of hashing is. Computer Hashing.
From www.saksenengku.com
Apa itu Hashing? Cara kerja, Jenis, dan Pengaplikasiannya Saksenengku Computer Hashing Hashing is the practice of transforming a given key or string of characters into another value for the purpose of security. The primary goal of hashing is to ensure data integrity and validate the original data. Our guide explores the principles of hashing, explaining how cryptographic hash functions work and their importance in protecting sensitive data. The idea is to. Computer Hashing.