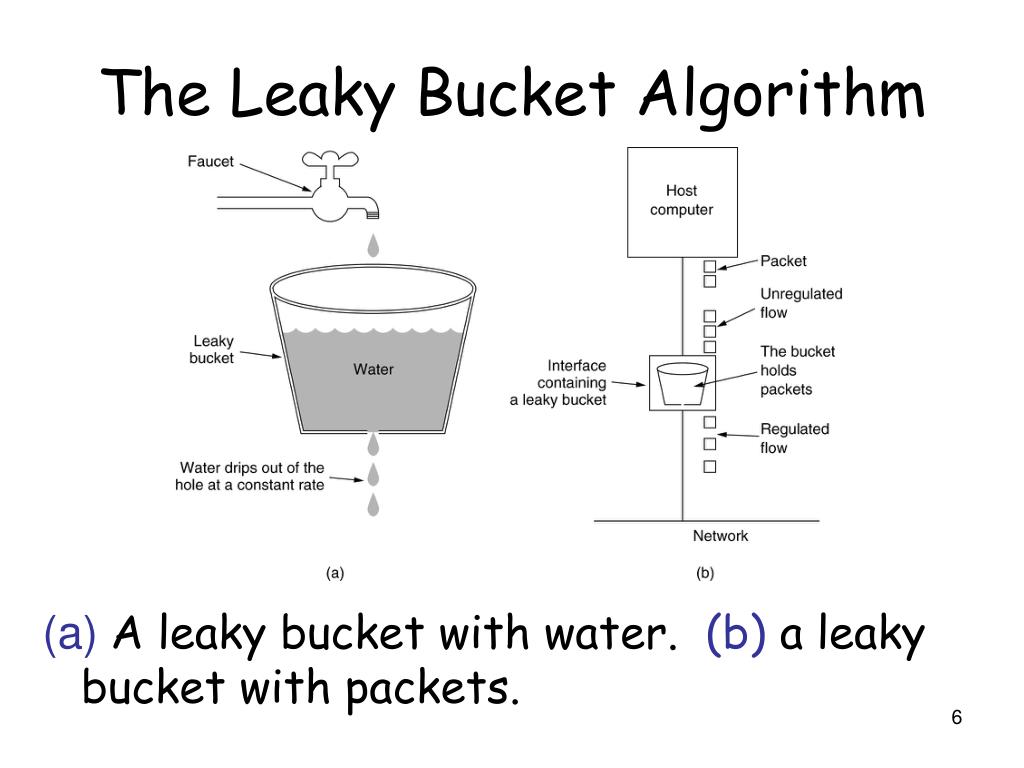
Leaky Bucket Algorithm Packets . A fifo queue holds the packets. A simple leaky bucket algorithm can be implemented using fifo queue. If the bucket becomes full, the. Step 1 − let us imagine a. A leaky bucket algorithm is a method used in computer networks to control the rate of incoming traffic. Picture a bucket with a leak at the bottom. The leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. The leaky bucket is a traffic shaping algorithm used to control the flow of data in a network, ensuring that data packets are transmitted at a steady rate. Leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. Data symbolized as water, enters the bucket. The rate at which water leaks (called the leak rate) is independent of the amount of water inside the bucket. It ensures that the flow of packets entering.
from www.slideserve.com
Data symbolized as water, enters the bucket. A fifo queue holds the packets. Leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. The rate at which water leaks (called the leak rate) is independent of the amount of water inside the bucket. The leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. Picture a bucket with a leak at the bottom. A leaky bucket algorithm is a method used in computer networks to control the rate of incoming traffic. A simple leaky bucket algorithm can be implemented using fifo queue. If the bucket becomes full, the. Step 1 − let us imagine a.
PPT Packet Switches with Output and Shared Buffer PowerPoint
Leaky Bucket Algorithm Packets Data symbolized as water, enters the bucket. A fifo queue holds the packets. If the bucket becomes full, the. The leaky bucket is a traffic shaping algorithm used to control the flow of data in a network, ensuring that data packets are transmitted at a steady rate. The leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. Step 1 − let us imagine a. A leaky bucket algorithm is a method used in computer networks to control the rate of incoming traffic. A simple leaky bucket algorithm can be implemented using fifo queue. It ensures that the flow of packets entering. Picture a bucket with a leak at the bottom. Leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. The rate at which water leaks (called the leak rate) is independent of the amount of water inside the bucket. Data symbolized as water, enters the bucket.
From www.slideserve.com
PPT Communication Networks PowerPoint Presentation, free download Leaky Bucket Algorithm Packets Picture a bucket with a leak at the bottom. The rate at which water leaks (called the leak rate) is independent of the amount of water inside the bucket. It ensures that the flow of packets entering. Data symbolized as water, enters the bucket. A leaky bucket algorithm is a method used in computer networks to control the rate of. Leaky Bucket Algorithm Packets.
From slideplayer.com
Congestion Control Algorithms ppt download Leaky Bucket Algorithm Packets A fifo queue holds the packets. Step 1 − let us imagine a. A leaky bucket algorithm is a method used in computer networks to control the rate of incoming traffic. Data symbolized as water, enters the bucket. If the bucket becomes full, the. The rate at which water leaks (called the leak rate) is independent of the amount of. Leaky Bucket Algorithm Packets.
From www.scribd.com
Network Based Packet Transmission Congestion Control Using Enhanced Leaky Bucket Algorithm Packets The leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. Picture a bucket with a leak at the bottom. Step 1 − let us imagine a. A fifo queue holds the packets. Data symbolized as water, enters the bucket. A simple leaky bucket algorithm can be implemented using fifo queue. Leaky bucket algorithm mainly controls the. Leaky Bucket Algorithm Packets.
From itnext.io
Rate limiting with leaky bucket algorithm by Codejitsu ITNEXT Leaky Bucket Algorithm Packets It ensures that the flow of packets entering. Leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. The leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. If the bucket becomes full, the. A fifo queue holds the packets. Step 1 − let us imagine a. Data. Leaky Bucket Algorithm Packets.
From www.researchgate.net
Flowchart of the conventional leaky bucket algorithm. Download Leaky Bucket Algorithm Packets Data symbolized as water, enters the bucket. A simple leaky bucket algorithm can be implemented using fifo queue. Step 1 − let us imagine a. A fifo queue holds the packets. The rate at which water leaks (called the leak rate) is independent of the amount of water inside the bucket. Leaky bucket algorithm mainly controls the total amount and. Leaky Bucket Algorithm Packets.
From www.youtube.com
Leaky bucket and Token bucket with GATE PYQs. Clear Explanation YouTube Leaky Bucket Algorithm Packets The rate at which water leaks (called the leak rate) is independent of the amount of water inside the bucket. It ensures that the flow of packets entering. A simple leaky bucket algorithm can be implemented using fifo queue. If the bucket becomes full, the. Data symbolized as water, enters the bucket. Step 1 − let us imagine a. A. Leaky Bucket Algorithm Packets.
From www.slideserve.com
PPT Chapter 13 PowerPoint Presentation, free download ID4138688 Leaky Bucket Algorithm Packets Leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. The rate at which water leaks (called the leak rate) is independent of the amount of water inside the bucket. Step 1 − let us imagine a. Picture a bucket with a leak at the bottom. A simple leaky bucket algorithm can. Leaky Bucket Algorithm Packets.
From slideplayer.com
UNIT 3 NETWORK LAYER ppt download Leaky Bucket Algorithm Packets The leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. Data symbolized as water, enters the bucket. It ensures that the flow of packets entering. Picture a bucket with a leak at the bottom. If the bucket becomes full, the. A simple leaky bucket algorithm can be implemented using fifo queue. The leaky bucket is a. Leaky Bucket Algorithm Packets.
From www.slideserve.com
PPT The Network Layer PowerPoint Presentation, free download ID5320728 Leaky Bucket Algorithm Packets A leaky bucket algorithm is a method used in computer networks to control the rate of incoming traffic. A simple leaky bucket algorithm can be implemented using fifo queue. The leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. If the bucket becomes full, the. Picture a bucket with a leak at the bottom. The leaky. Leaky Bucket Algorithm Packets.
From www.studypool.com
SOLUTION Leaky Bucket Algorithm C Program Studypool Leaky Bucket Algorithm Packets The leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. A simple leaky bucket algorithm can be implemented using fifo queue. A leaky bucket algorithm is a method used in computer networks to control the rate of incoming traffic. A fifo queue holds the packets. If the bucket becomes full, the. Data symbolized as water, enters. Leaky Bucket Algorithm Packets.
From songhayoung.github.io
[System Design] Leaky bucket / token bucket SUMFIのBlog Leaky Bucket Algorithm Packets A leaky bucket algorithm is a method used in computer networks to control the rate of incoming traffic. Leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. A simple leaky bucket algorithm can be implemented using fifo queue. The leaky bucket algorithm provides an elegant solution to the problem of unpredictable. Leaky Bucket Algorithm Packets.
From www.slideserve.com
PPT Packet Switches with Output and Shared Buffer PowerPoint Leaky Bucket Algorithm Packets The leaky bucket is a traffic shaping algorithm used to control the flow of data in a network, ensuring that data packets are transmitted at a steady rate. It ensures that the flow of packets entering. Step 1 − let us imagine a. Data symbolized as water, enters the bucket. The leaky bucket algorithm provides an elegant solution to the. Leaky Bucket Algorithm Packets.
From www.slideserve.com
PPT Bandwidth Management PowerPoint Presentation, free download ID Leaky Bucket Algorithm Packets A leaky bucket algorithm is a method used in computer networks to control the rate of incoming traffic. Step 1 − let us imagine a. If the bucket becomes full, the. A simple leaky bucket algorithm can be implemented using fifo queue. Picture a bucket with a leak at the bottom. A fifo queue holds the packets. The leaky bucket. Leaky Bucket Algorithm Packets.
From www.pinterest.com
This sample shows the Leaky Bucket Algorithm that is widely used in Leaky Bucket Algorithm Packets A simple leaky bucket algorithm can be implemented using fifo queue. The rate at which water leaks (called the leak rate) is independent of the amount of water inside the bucket. It ensures that the flow of packets entering. The leaky bucket is a traffic shaping algorithm used to control the flow of data in a network, ensuring that data. Leaky Bucket Algorithm Packets.
From www.slideserve.com
PPT Improving QOS in IP Networks PowerPoint Presentation, free Leaky Bucket Algorithm Packets It ensures that the flow of packets entering. Leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. The leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. Data symbolized as water, enters the bucket. Picture a bucket with a leak at the bottom. Step 1 − let. Leaky Bucket Algorithm Packets.
From www.slideserve.com
PPT Packet Switches with Output and Shared Buffer PowerPoint Leaky Bucket Algorithm Packets A leaky bucket algorithm is a method used in computer networks to control the rate of incoming traffic. A fifo queue holds the packets. Picture a bucket with a leak at the bottom. The rate at which water leaks (called the leak rate) is independent of the amount of water inside the bucket. Step 1 − let us imagine a.. Leaky Bucket Algorithm Packets.
From www.researchgate.net
Leaky bucket algorithm Download Scientific Diagram Leaky Bucket Algorithm Packets The rate at which water leaks (called the leak rate) is independent of the amount of water inside the bucket. Picture a bucket with a leak at the bottom. A fifo queue holds the packets. If the bucket becomes full, the. It ensures that the flow of packets entering. The leaky bucket is a traffic shaping algorithm used to control. Leaky Bucket Algorithm Packets.
From www.researchgate.net
Intelligent leaky bucket algorithm. Download Scientific Diagram Leaky Bucket Algorithm Packets A leaky bucket algorithm is a method used in computer networks to control the rate of incoming traffic. Data symbolized as water, enters the bucket. The rate at which water leaks (called the leak rate) is independent of the amount of water inside the bucket. A fifo queue holds the packets. A simple leaky bucket algorithm can be implemented using. Leaky Bucket Algorithm Packets.
From www.scaler.com
Leaky Bucket Algorithm Scalar Topics Leaky Bucket Algorithm Packets A fifo queue holds the packets. Leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. A simple leaky bucket algorithm can be implemented using fifo queue. Picture a bucket with a leak at the bottom. A leaky bucket algorithm is a method used in computer networks to control the rate of. Leaky Bucket Algorithm Packets.
From www.linqz.io
Leaky/Token bucket algorithm for flow control Learn INQuiZitively Leaky Bucket Algorithm Packets Data symbolized as water, enters the bucket. Leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. The rate at which water leaks (called the leak rate) is independent of the amount of water inside the bucket. Picture a bucket with a leak at the bottom. It ensures that the flow of. Leaky Bucket Algorithm Packets.
From www.researchgate.net
The Packet leaky Bucket Algorithm marked with low priority (maximum Leaky Bucket Algorithm Packets If the bucket becomes full, the. Leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. The leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. The leaky bucket is a traffic shaping algorithm used to control the flow of data in a network, ensuring that data packets. Leaky Bucket Algorithm Packets.
From www.youtube.com
Mastering the Leaky Bucket Algorithm A StepbyStep Guide? algorithm Leaky Bucket Algorithm Packets Data symbolized as water, enters the bucket. The rate at which water leaks (called the leak rate) is independent of the amount of water inside the bucket. The leaky bucket is a traffic shaping algorithm used to control the flow of data in a network, ensuring that data packets are transmitted at a steady rate. The leaky bucket algorithm provides. Leaky Bucket Algorithm Packets.
From www.slideserve.com
PPT The Network Layer PowerPoint Presentation ID3653615 Leaky Bucket Algorithm Packets Leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. A simple leaky bucket algorithm can be implemented using fifo queue. Picture a bucket with a leak at the bottom. Step 1 − let us imagine a. Data symbolized as water, enters the bucket. If the bucket becomes full, the. The rate. Leaky Bucket Algorithm Packets.
From www.youtube.com
congestion control algorithm Leaky Bucket Algorithm (open loop and Leaky Bucket Algorithm Packets A simple leaky bucket algorithm can be implemented using fifo queue. The leaky bucket is a traffic shaping algorithm used to control the flow of data in a network, ensuring that data packets are transmitted at a steady rate. The rate at which water leaks (called the leak rate) is independent of the amount of water inside the bucket. Step. Leaky Bucket Algorithm Packets.
From www.slideserve.com
PPT The Network Layer PowerPoint Presentation, free download ID3653615 Leaky Bucket Algorithm Packets Picture a bucket with a leak at the bottom. Data symbolized as water, enters the bucket. The rate at which water leaks (called the leak rate) is independent of the amount of water inside the bucket. A fifo queue holds the packets. Leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network.. Leaky Bucket Algorithm Packets.
From www.researchgate.net
4) A leaky bucket with packets [1] Download Scientific Diagram Leaky Bucket Algorithm Packets A simple leaky bucket algorithm can be implemented using fifo queue. The leaky bucket is a traffic shaping algorithm used to control the flow of data in a network, ensuring that data packets are transmitted at a steady rate. Data symbolized as water, enters the bucket. The rate at which water leaks (called the leak rate) is independent of the. Leaky Bucket Algorithm Packets.
From www.researchgate.net
(PDF) Performance Characteristics of a PacketBased LeakyBucket Leaky Bucket Algorithm Packets The leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. Leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. The rate at which water leaks (called the leak rate) is independent of the amount of water inside the bucket. Step 1 − let us imagine a. Picture. Leaky Bucket Algorithm Packets.
From www.researchgate.net
The Packet leaky Bucket Algorithm marked with low priority (maximum Leaky Bucket Algorithm Packets A fifo queue holds the packets. Step 1 − let us imagine a. The leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. The leaky bucket is a traffic shaping algorithm used to control the flow of data in a network, ensuring that data packets are transmitted at a steady rate. Data symbolized as water, enters. Leaky Bucket Algorithm Packets.
From www.semanticscholar.org
[PDF] Leaky Bucket Algorithm for Congestion Control Semantic Scholar Leaky Bucket Algorithm Packets Step 1 − let us imagine a. It ensures that the flow of packets entering. If the bucket becomes full, the. The rate at which water leaks (called the leak rate) is independent of the amount of water inside the bucket. A leaky bucket algorithm is a method used in computer networks to control the rate of incoming traffic. The. Leaky Bucket Algorithm Packets.
From www.youtube.com
Leaky Bucket Algorithm YouTube Leaky Bucket Algorithm Packets It ensures that the flow of packets entering. Leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. Step 1 − let us imagine a. Picture a bucket with a leak at the bottom. A simple leaky bucket algorithm can be implemented using fifo queue. A fifo queue holds the packets. The. Leaky Bucket Algorithm Packets.
From www.slideserve.com
PPT The Network Layer PowerPoint Presentation, free download ID5856654 Leaky Bucket Algorithm Packets Picture a bucket with a leak at the bottom. A leaky bucket algorithm is a method used in computer networks to control the rate of incoming traffic. The leaky bucket is a traffic shaping algorithm used to control the flow of data in a network, ensuring that data packets are transmitted at a steady rate. A simple leaky bucket algorithm. Leaky Bucket Algorithm Packets.
From www.slideserve.com
PPT QoS & Queuing Theory PowerPoint Presentation, free download ID Leaky Bucket Algorithm Packets A leaky bucket algorithm is a method used in computer networks to control the rate of incoming traffic. Data symbolized as water, enters the bucket. Step 1 − let us imagine a. Leaky bucket algorithm mainly controls the total amount and the rate of the traffic sent to the network. It ensures that the flow of packets entering. The leaky. Leaky Bucket Algorithm Packets.
From www.slideshare.net
Leaky bucket algorithm Leaky Bucket Algorithm Packets Picture a bucket with a leak at the bottom. If the bucket becomes full, the. A simple leaky bucket algorithm can be implemented using fifo queue. It ensures that the flow of packets entering. A leaky bucket algorithm is a method used in computer networks to control the rate of incoming traffic. Leaky bucket algorithm mainly controls the total amount. Leaky Bucket Algorithm Packets.
From www.slideshare.net
Chap24 Leaky Bucket Algorithm Packets A simple leaky bucket algorithm can be implemented using fifo queue. Data symbolized as water, enters the bucket. Step 1 − let us imagine a. The leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. If the bucket becomes full, the. Picture a bucket with a leak at the bottom. Leaky bucket algorithm mainly controls the. Leaky Bucket Algorithm Packets.
From www.techtarget.com
What is the leaky bucket algorithm? TechTarget Definition Leaky Bucket Algorithm Packets The leaky bucket algorithm provides an elegant solution to the problem of unpredictable traffic. The leaky bucket is a traffic shaping algorithm used to control the flow of data in a network, ensuring that data packets are transmitted at a steady rate. If the bucket becomes full, the. Step 1 − let us imagine a. A leaky bucket algorithm is. Leaky Bucket Algorithm Packets.