Endpoint Security In A Network . Endpoint security helps businesses keep the devices that connect to a network secure. Endpoint security refers to the act of preventing, detecting and remediating cyberattacks for any device, whether it is connected to a traditional. Endpoint security, a network's critical first line of cybersecurity defense, protects end users and endpoint devices—desktops, laptops, mobile. Endpoint security or endpoint protection is the process of defending endpoints — devices that connect to a network, like laptops and. By making endpoints the new network perimeter, organizations can prevent risks and detect.
from docs.blackberry.com
Endpoint security helps businesses keep the devices that connect to a network secure. Endpoint security or endpoint protection is the process of defending endpoints — devices that connect to a network, like laptops and. Endpoint security, a network's critical first line of cybersecurity defense, protects end users and endpoint devices—desktops, laptops, mobile. By making endpoints the new network perimeter, organizations can prevent risks and detect. Endpoint security refers to the act of preventing, detecting and remediating cyberattacks for any device, whether it is connected to a traditional.
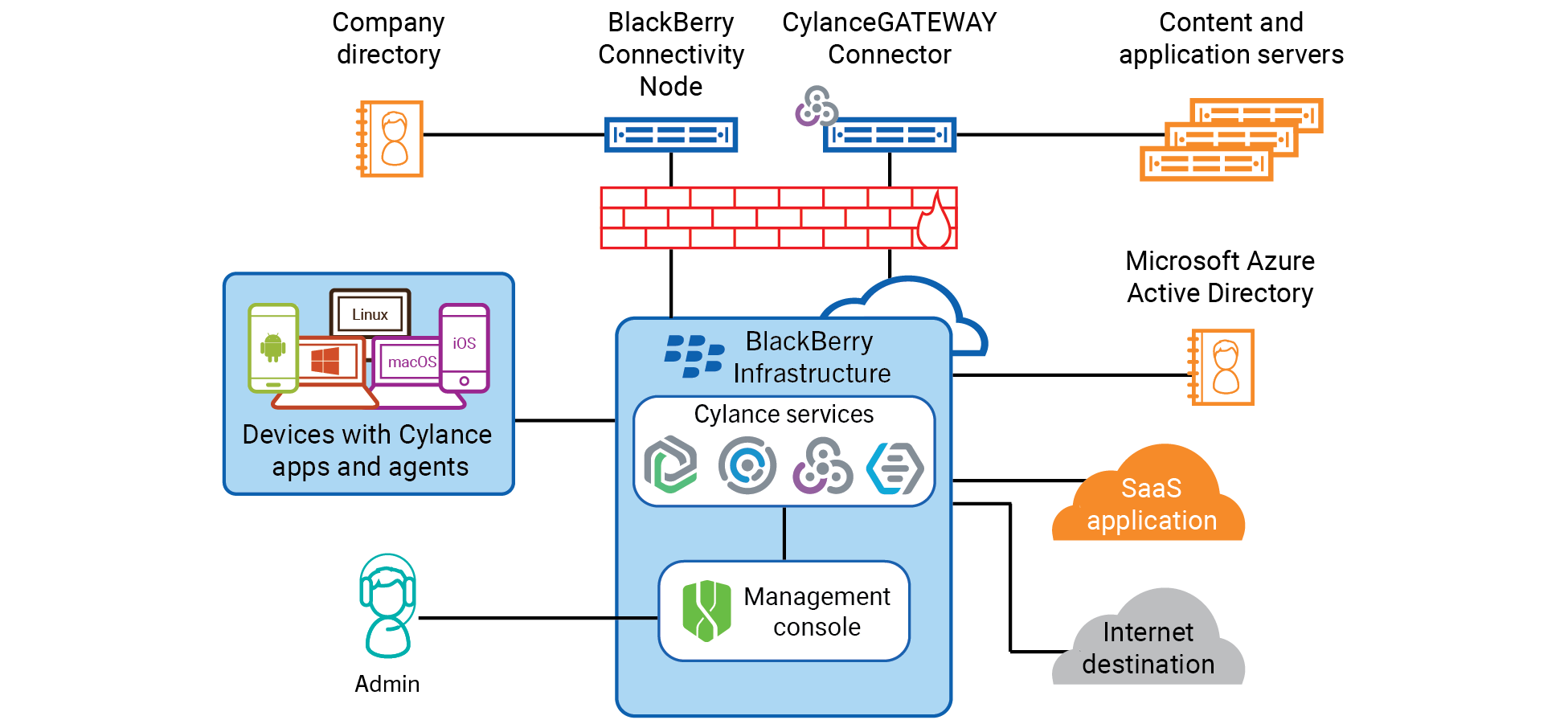
Cylance Endpoint Security architecture
Endpoint Security In A Network Endpoint security helps businesses keep the devices that connect to a network secure. Endpoint security refers to the act of preventing, detecting and remediating cyberattacks for any device, whether it is connected to a traditional. Endpoint security, a network's critical first line of cybersecurity defense, protects end users and endpoint devices—desktops, laptops, mobile. Endpoint security or endpoint protection is the process of defending endpoints — devices that connect to a network, like laptops and. Endpoint security helps businesses keep the devices that connect to a network secure. By making endpoints the new network perimeter, organizations can prevent risks and detect.
From www.alamy.com
Endpoint Security Endpoint Protection Concept Multiple Devices Endpoint Security In A Network Endpoint security refers to the act of preventing, detecting and remediating cyberattacks for any device, whether it is connected to a traditional. By making endpoints the new network perimeter, organizations can prevent risks and detect. Endpoint security or endpoint protection is the process of defending endpoints — devices that connect to a network, like laptops and. Endpoint security helps businesses. Endpoint Security In A Network.
From blogs.manageengine.com
The role of endpoints in the security of your network ManageEngine Blog Endpoint Security In A Network Endpoint security helps businesses keep the devices that connect to a network secure. Endpoint security, a network's critical first line of cybersecurity defense, protects end users and endpoint devices—desktops, laptops, mobile. Endpoint security refers to the act of preventing, detecting and remediating cyberattacks for any device, whether it is connected to a traditional. Endpoint security or endpoint protection is the. Endpoint Security In A Network.
From absbuzz.com
Protect Your Endpoints Against Evolving Threats Absbuzz Endpoint Security In A Network Endpoint security helps businesses keep the devices that connect to a network secure. By making endpoints the new network perimeter, organizations can prevent risks and detect. Endpoint security or endpoint protection is the process of defending endpoints — devices that connect to a network, like laptops and. Endpoint security, a network's critical first line of cybersecurity defense, protects end users. Endpoint Security In A Network.
From vpn.surf
What is Endpoint Security? Endpoint Security In A Network Endpoint security helps businesses keep the devices that connect to a network secure. Endpoint security, a network's critical first line of cybersecurity defense, protects end users and endpoint devices—desktops, laptops, mobile. By making endpoints the new network perimeter, organizations can prevent risks and detect. Endpoint security refers to the act of preventing, detecting and remediating cyberattacks for any device, whether. Endpoint Security In A Network.
From bulldurhamtech.com
Reasons To Integrate Both Endpoint And Network Security » Bull Durham Endpoint Security In A Network Endpoint security or endpoint protection is the process of defending endpoints — devices that connect to a network, like laptops and. Endpoint security helps businesses keep the devices that connect to a network secure. Endpoint security, a network's critical first line of cybersecurity defense, protects end users and endpoint devices—desktops, laptops, mobile. Endpoint security refers to the act of preventing,. Endpoint Security In A Network.
From ipsystems.ph
Network & Endpoint Security IPSYSTEMS, Inc. Endpoint Security In A Network Endpoint security refers to the act of preventing, detecting and remediating cyberattacks for any device, whether it is connected to a traditional. Endpoint security, a network's critical first line of cybersecurity defense, protects end users and endpoint devices—desktops, laptops, mobile. Endpoint security or endpoint protection is the process of defending endpoints — devices that connect to a network, like laptops. Endpoint Security In A Network.
From iemlabs.com
Endpoint Security Keeping Network Endpoints Safe IEMLabs Blog Endpoint Security In A Network Endpoint security refers to the act of preventing, detecting and remediating cyberattacks for any device, whether it is connected to a traditional. Endpoint security or endpoint protection is the process of defending endpoints — devices that connect to a network, like laptops and. Endpoint security helps businesses keep the devices that connect to a network secure. By making endpoints the. Endpoint Security In A Network.
From www.nffinc.com
Network & Endpoint Security Networking For Future, Inc. (NFF) Endpoint Security In A Network By making endpoints the new network perimeter, organizations can prevent risks and detect. Endpoint security refers to the act of preventing, detecting and remediating cyberattacks for any device, whether it is connected to a traditional. Endpoint security, a network's critical first line of cybersecurity defense, protects end users and endpoint devices—desktops, laptops, mobile. Endpoint security or endpoint protection is the. Endpoint Security In A Network.
From www.gotyoursixcyber.com
ENDPOINT (DESKTOP & SERVER) SECURITY Got Your Six Cybersecurity Endpoint Security In A Network By making endpoints the new network perimeter, organizations can prevent risks and detect. Endpoint security, a network's critical first line of cybersecurity defense, protects end users and endpoint devices—desktops, laptops, mobile. Endpoint security helps businesses keep the devices that connect to a network secure. Endpoint security refers to the act of preventing, detecting and remediating cyberattacks for any device, whether. Endpoint Security In A Network.
From www.spiceworks.com
What Is Endpoint Security? Definition, Key Components, and Best Endpoint Security In A Network Endpoint security or endpoint protection is the process of defending endpoints — devices that connect to a network, like laptops and. Endpoint security, a network's critical first line of cybersecurity defense, protects end users and endpoint devices—desktops, laptops, mobile. Endpoint security helps businesses keep the devices that connect to a network secure. Endpoint security refers to the act of preventing,. Endpoint Security In A Network.
From blog.cspire.com
7 Layers of Data Security Endpoint Endpoint Security In A Network Endpoint security, a network's critical first line of cybersecurity defense, protects end users and endpoint devices—desktops, laptops, mobile. Endpoint security helps businesses keep the devices that connect to a network secure. Endpoint security refers to the act of preventing, detecting and remediating cyberattacks for any device, whether it is connected to a traditional. By making endpoints the new network perimeter,. Endpoint Security In A Network.
From blazenetworks.co.uk
Endpoint Security Blaze Networks Endpoint Security In A Network Endpoint security helps businesses keep the devices that connect to a network secure. Endpoint security refers to the act of preventing, detecting and remediating cyberattacks for any device, whether it is connected to a traditional. Endpoint security, a network's critical first line of cybersecurity defense, protects end users and endpoint devices—desktops, laptops, mobile. By making endpoints the new network perimeter,. Endpoint Security In A Network.
From www.manageengine.com
Endpoint security software Endpoint security management Endpoint Security In A Network Endpoint security, a network's critical first line of cybersecurity defense, protects end users and endpoint devices—desktops, laptops, mobile. By making endpoints the new network perimeter, organizations can prevent risks and detect. Endpoint security refers to the act of preventing, detecting and remediating cyberattacks for any device, whether it is connected to a traditional. Endpoint security or endpoint protection is the. Endpoint Security In A Network.
From techgenix.com
What Is EDR Security and Why Is It Important? Endpoint Security In A Network Endpoint security, a network's critical first line of cybersecurity defense, protects end users and endpoint devices—desktops, laptops, mobile. Endpoint security refers to the act of preventing, detecting and remediating cyberattacks for any device, whether it is connected to a traditional. Endpoint security or endpoint protection is the process of defending endpoints — devices that connect to a network, like laptops. Endpoint Security In A Network.
From datalocker.com
Endpoint Security & Control DataLocker Inc. Endpoint Security In A Network Endpoint security or endpoint protection is the process of defending endpoints — devices that connect to a network, like laptops and. Endpoint security helps businesses keep the devices that connect to a network secure. Endpoint security refers to the act of preventing, detecting and remediating cyberattacks for any device, whether it is connected to a traditional. By making endpoints the. Endpoint Security In A Network.
From afinety.com
What Endpoints Are and Why They Need to be Secured Endpoint Security In A Network Endpoint security helps businesses keep the devices that connect to a network secure. Endpoint security or endpoint protection is the process of defending endpoints — devices that connect to a network, like laptops and. Endpoint security, a network's critical first line of cybersecurity defense, protects end users and endpoint devices—desktops, laptops, mobile. By making endpoints the new network perimeter, organizations. Endpoint Security In A Network.
From docs.blackberry.com
Cylance Endpoint Security architecture Endpoint Security In A Network By making endpoints the new network perimeter, organizations can prevent risks and detect. Endpoint security helps businesses keep the devices that connect to a network secure. Endpoint security, a network's critical first line of cybersecurity defense, protects end users and endpoint devices—desktops, laptops, mobile. Endpoint security or endpoint protection is the process of defending endpoints — devices that connect to. Endpoint Security In A Network.
From www.bitlyft.com
Endpoint Security Protecting Your Network from the Inside Out Endpoint Security In A Network Endpoint security refers to the act of preventing, detecting and remediating cyberattacks for any device, whether it is connected to a traditional. Endpoint security or endpoint protection is the process of defending endpoints — devices that connect to a network, like laptops and. Endpoint security helps businesses keep the devices that connect to a network secure. By making endpoints the. Endpoint Security In A Network.
From uniserveit.com
The Goal Of Endpoint Security Uniserve IT Solutions Endpoint Security In A Network By making endpoints the new network perimeter, organizations can prevent risks and detect. Endpoint security or endpoint protection is the process of defending endpoints — devices that connect to a network, like laptops and. Endpoint security refers to the act of preventing, detecting and remediating cyberattacks for any device, whether it is connected to a traditional. Endpoint security, a network's. Endpoint Security In A Network.
From www.esds.co.in
What is Endpoint Security? Needs, Benefits, Challenges Endpoint Security In A Network Endpoint security helps businesses keep the devices that connect to a network secure. Endpoint security, a network's critical first line of cybersecurity defense, protects end users and endpoint devices—desktops, laptops, mobile. By making endpoints the new network perimeter, organizations can prevent risks and detect. Endpoint security refers to the act of preventing, detecting and remediating cyberattacks for any device, whether. Endpoint Security In A Network.
From gogeekz.com
4 Endpoint Protection Tips for Better Network GoGeekz Endpoint Security In A Network Endpoint security refers to the act of preventing, detecting and remediating cyberattacks for any device, whether it is connected to a traditional. Endpoint security, a network's critical first line of cybersecurity defense, protects end users and endpoint devices—desktops, laptops, mobile. By making endpoints the new network perimeter, organizations can prevent risks and detect. Endpoint security helps businesses keep the devices. Endpoint Security In A Network.
From www.analyticsvidhya.com
How Endpoint Security in a Cloudbased System Works? Endpoint Security In A Network Endpoint security helps businesses keep the devices that connect to a network secure. Endpoint security, a network's critical first line of cybersecurity defense, protects end users and endpoint devices—desktops, laptops, mobile. Endpoint security refers to the act of preventing, detecting and remediating cyberattacks for any device, whether it is connected to a traditional. Endpoint security or endpoint protection is the. Endpoint Security In A Network.
From www.securityhq.com
Managed Endpoint Protection (EPP) Services SecurityHQ Endpoint Security In A Network Endpoint security or endpoint protection is the process of defending endpoints — devices that connect to a network, like laptops and. Endpoint security refers to the act of preventing, detecting and remediating cyberattacks for any device, whether it is connected to a traditional. Endpoint security, a network's critical first line of cybersecurity defense, protects end users and endpoint devices—desktops, laptops,. Endpoint Security In A Network.
From www.esds.co.in
What is an Endpoint & How Endpoint Security Works ESDS Endpoint Security In A Network Endpoint security or endpoint protection is the process of defending endpoints — devices that connect to a network, like laptops and. By making endpoints the new network perimeter, organizations can prevent risks and detect. Endpoint security refers to the act of preventing, detecting and remediating cyberattacks for any device, whether it is connected to a traditional. Endpoint security helps businesses. Endpoint Security In A Network.
From www.vecteezy.com
Endpoint security server network isometric flat 3d illustration concept Endpoint Security In A Network Endpoint security refers to the act of preventing, detecting and remediating cyberattacks for any device, whether it is connected to a traditional. Endpoint security helps businesses keep the devices that connect to a network secure. By making endpoints the new network perimeter, organizations can prevent risks and detect. Endpoint security or endpoint protection is the process of defending endpoints —. Endpoint Security In A Network.
From blog.omnetworks.com.np
5 StandOut Features of Endpoint Security You Should Know Endpoint Security In A Network Endpoint security helps businesses keep the devices that connect to a network secure. Endpoint security or endpoint protection is the process of defending endpoints — devices that connect to a network, like laptops and. Endpoint security, a network's critical first line of cybersecurity defense, protects end users and endpoint devices—desktops, laptops, mobile. By making endpoints the new network perimeter, organizations. Endpoint Security In A Network.
From www.atatus.com
Endpoint Security Definition, Features, Benefits and More Endpoint Security In A Network Endpoint security or endpoint protection is the process of defending endpoints — devices that connect to a network, like laptops and. By making endpoints the new network perimeter, organizations can prevent risks and detect. Endpoint security, a network's critical first line of cybersecurity defense, protects end users and endpoint devices—desktops, laptops, mobile. Endpoint security helps businesses keep the devices that. Endpoint Security In A Network.
From www.networkcomputerpros.com
Benefits of Symantec Endpoint Protection Securing your Network Endpoint Security In A Network Endpoint security or endpoint protection is the process of defending endpoints — devices that connect to a network, like laptops and. Endpoint security helps businesses keep the devices that connect to a network secure. By making endpoints the new network perimeter, organizations can prevent risks and detect. Endpoint security, a network's critical first line of cybersecurity defense, protects end users. Endpoint Security In A Network.
From www.itsolutionsnetwork.io
Empowering Your Cybersecurity The Importance of Endpoint Protection Endpoint Security In A Network Endpoint security helps businesses keep the devices that connect to a network secure. Endpoint security or endpoint protection is the process of defending endpoints — devices that connect to a network, like laptops and. Endpoint security, a network's critical first line of cybersecurity defense, protects end users and endpoint devices—desktops, laptops, mobile. By making endpoints the new network perimeter, organizations. Endpoint Security In A Network.
From www.datalinknetworks.net
The Ultimate Guide to Endpoint Security Top Endpoint Security Endpoint Security In A Network Endpoint security helps businesses keep the devices that connect to a network secure. By making endpoints the new network perimeter, organizations can prevent risks and detect. Endpoint security refers to the act of preventing, detecting and remediating cyberattacks for any device, whether it is connected to a traditional. Endpoint security or endpoint protection is the process of defending endpoints —. Endpoint Security In A Network.
From sc1.checkpoint.com
Endpoint Security Introduction Endpoint Security In A Network Endpoint security helps businesses keep the devices that connect to a network secure. Endpoint security or endpoint protection is the process of defending endpoints — devices that connect to a network, like laptops and. Endpoint security, a network's critical first line of cybersecurity defense, protects end users and endpoint devices—desktops, laptops, mobile. Endpoint security refers to the act of preventing,. Endpoint Security In A Network.
From www.varonis.com
What is Endpoint Security? A Complete Guide Endpoint Security In A Network Endpoint security, a network's critical first line of cybersecurity defense, protects end users and endpoint devices—desktops, laptops, mobile. Endpoint security helps businesses keep the devices that connect to a network secure. Endpoint security or endpoint protection is the process of defending endpoints — devices that connect to a network, like laptops and. Endpoint security refers to the act of preventing,. Endpoint Security In A Network.
From socialtechy.com
Endpoint Management To Secure Your Network Connected Devices Social Techy Endpoint Security In A Network Endpoint security or endpoint protection is the process of defending endpoints — devices that connect to a network, like laptops and. Endpoint security refers to the act of preventing, detecting and remediating cyberattacks for any device, whether it is connected to a traditional. Endpoint security helps businesses keep the devices that connect to a network secure. By making endpoints the. Endpoint Security In A Network.
From electronicsguide4u.com
The Ultimate Guide To Endpoint Security Solutions And Tools Endpoint Security In A Network By making endpoints the new network perimeter, organizations can prevent risks and detect. Endpoint security helps businesses keep the devices that connect to a network secure. Endpoint security, a network's critical first line of cybersecurity defense, protects end users and endpoint devices—desktops, laptops, mobile. Endpoint security refers to the act of preventing, detecting and remediating cyberattacks for any device, whether. Endpoint Security In A Network.