Vulnerability Scanner Defender . If you suspect that your device may have malware you should have microsoft defender run a scan. Decide which network devices are. Here's how to do that on windows, mac, or android. Vulnerability assessment scanning for containers, powered by microsoft defender vulnerability management (mdvm), is an integrated solution that empowers security teams to. Snmp traffic between the defender for endpoint scanning device and the targeted network devices must be allowed (for example, by the firewall).
from learn.microsoft.com
If you suspect that your device may have malware you should have microsoft defender run a scan. Here's how to do that on windows, mac, or android. Decide which network devices are. Vulnerability assessment scanning for containers, powered by microsoft defender vulnerability management (mdvm), is an integrated solution that empowers security teams to. Snmp traffic between the defender for endpoint scanning device and the targeted network devices must be allowed (for example, by the firewall).
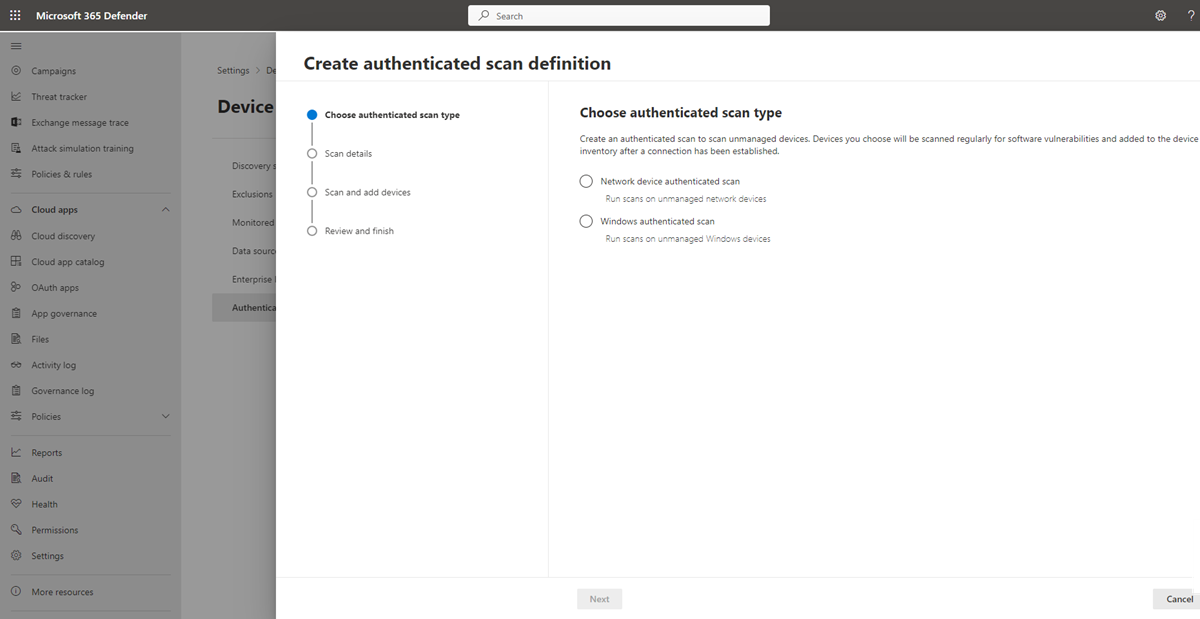
Authenticated scan for Windows in Defender Vulnerability Management
Vulnerability Scanner Defender Snmp traffic between the defender for endpoint scanning device and the targeted network devices must be allowed (for example, by the firewall). Here's how to do that on windows, mac, or android. Decide which network devices are. Snmp traffic between the defender for endpoint scanning device and the targeted network devices must be allowed (for example, by the firewall). If you suspect that your device may have malware you should have microsoft defender run a scan. Vulnerability assessment scanning for containers, powered by microsoft defender vulnerability management (mdvm), is an integrated solution that empowers security teams to.
From learn.microsoft.com
Find software and vulnerabilities with agentless scanning Microsoft Vulnerability Scanner Defender Here's how to do that on windows, mac, or android. If you suspect that your device may have malware you should have microsoft defender run a scan. Vulnerability assessment scanning for containers, powered by microsoft defender vulnerability management (mdvm), is an integrated solution that empowers security teams to. Decide which network devices are. Snmp traffic between the defender for endpoint. Vulnerability Scanner Defender.
From jeffreyappel.nl
How works Microsoft Defender Vulnerability Management (MDVM) Vulnerability Scanner Defender Vulnerability assessment scanning for containers, powered by microsoft defender vulnerability management (mdvm), is an integrated solution that empowers security teams to. Decide which network devices are. If you suspect that your device may have malware you should have microsoft defender run a scan. Here's how to do that on windows, mac, or android. Snmp traffic between the defender for endpoint. Vulnerability Scanner Defender.
From gbhackers.com
10 Best Vulnerability Scanner Tools 2024 (Updated) Vulnerability Scanner Defender Here's how to do that on windows, mac, or android. Decide which network devices are. Snmp traffic between the defender for endpoint scanning device and the targeted network devices must be allowed (for example, by the firewall). If you suspect that your device may have malware you should have microsoft defender run a scan. Vulnerability assessment scanning for containers, powered. Vulnerability Scanner Defender.
From learn.microsoft.com
Microsoft Defender Vulnerability Management dashboard Microsoft Learn Vulnerability Scanner Defender Vulnerability assessment scanning for containers, powered by microsoft defender vulnerability management (mdvm), is an integrated solution that empowers security teams to. Snmp traffic between the defender for endpoint scanning device and the targeted network devices must be allowed (for example, by the firewall). If you suspect that your device may have malware you should have microsoft defender run a scan.. Vulnerability Scanner Defender.
From www.g2.com
Microsoft Defender Vulnerability Management Features G2 Vulnerability Scanner Defender Here's how to do that on windows, mac, or android. If you suspect that your device may have malware you should have microsoft defender run a scan. Vulnerability assessment scanning for containers, powered by microsoft defender vulnerability management (mdvm), is an integrated solution that empowers security teams to. Decide which network devices are. Snmp traffic between the defender for endpoint. Vulnerability Scanner Defender.
From blog.cloudnative.co.jp
Microsoft Defender Vulnerability Management addonを試してみた CloudNative Vulnerability Scanner Defender Vulnerability assessment scanning for containers, powered by microsoft defender vulnerability management (mdvm), is an integrated solution that empowers security teams to. Here's how to do that on windows, mac, or android. Decide which network devices are. If you suspect that your device may have malware you should have microsoft defender run a scan. Snmp traffic between the defender for endpoint. Vulnerability Scanner Defender.
From thalpius.com
Microsoft Defender Vulnerability Management Authenticated Scan Security Vulnerability Scanner Defender Decide which network devices are. Here's how to do that on windows, mac, or android. Snmp traffic between the defender for endpoint scanning device and the targeted network devices must be allowed (for example, by the firewall). If you suspect that your device may have malware you should have microsoft defender run a scan. Vulnerability assessment scanning for containers, powered. Vulnerability Scanner Defender.
From learn.microsoft.com
Microsoft Defender Vulnerability Management Microsoft Learn Vulnerability Scanner Defender Snmp traffic between the defender for endpoint scanning device and the targeted network devices must be allowed (for example, by the firewall). Decide which network devices are. Here's how to do that on windows, mac, or android. If you suspect that your device may have malware you should have microsoft defender run a scan. Vulnerability assessment scanning for containers, powered. Vulnerability Scanner Defender.
From thalpius.com
Microsoft Defender Vulnerability Management Authenticated Scan Security Vulnerability Scanner Defender Snmp traffic between the defender for endpoint scanning device and the targeted network devices must be allowed (for example, by the firewall). If you suspect that your device may have malware you should have microsoft defender run a scan. Decide which network devices are. Here's how to do that on windows, mac, or android. Vulnerability assessment scanning for containers, powered. Vulnerability Scanner Defender.
From learn.microsoft.com
Find software and vulnerabilities with agentless scanning Microsoft Vulnerability Scanner Defender If you suspect that your device may have malware you should have microsoft defender run a scan. Decide which network devices are. Here's how to do that on windows, mac, or android. Vulnerability assessment scanning for containers, powered by microsoft defender vulnerability management (mdvm), is an integrated solution that empowers security teams to. Snmp traffic between the defender for endpoint. Vulnerability Scanner Defender.
From gbhackers.com
10 Best Vulnerability Scanner Tools 2023 (Updated) Vulnerability Scanner Defender Decide which network devices are. Vulnerability assessment scanning for containers, powered by microsoft defender vulnerability management (mdvm), is an integrated solution that empowers security teams to. Snmp traffic between the defender for endpoint scanning device and the targeted network devices must be allowed (for example, by the firewall). Here's how to do that on windows, mac, or android. If you. Vulnerability Scanner Defender.
From learn.microsoft.com
Enable vulnerability scanning with the integrated Qualys scanner Vulnerability Scanner Defender Snmp traffic between the defender for endpoint scanning device and the targeted network devices must be allowed (for example, by the firewall). Decide which network devices are. Here's how to do that on windows, mac, or android. Vulnerability assessment scanning for containers, powered by microsoft defender vulnerability management (mdvm), is an integrated solution that empowers security teams to. If you. Vulnerability Scanner Defender.
From joeho.xyz
Vulnerability Scanning in Microsoft Defender For Server Joe Ho Blog Vulnerability Scanner Defender If you suspect that your device may have malware you should have microsoft defender run a scan. Here's how to do that on windows, mac, or android. Decide which network devices are. Snmp traffic between the defender for endpoint scanning device and the targeted network devices must be allowed (for example, by the firewall). Vulnerability assessment scanning for containers, powered. Vulnerability Scanner Defender.
From jeffreyappel.nl
How works Microsoft Defender Vulnerability Management (MDVM) Vulnerability Scanner Defender If you suspect that your device may have malware you should have microsoft defender run a scan. Decide which network devices are. Here's how to do that on windows, mac, or android. Vulnerability assessment scanning for containers, powered by microsoft defender vulnerability management (mdvm), is an integrated solution that empowers security teams to. Snmp traffic between the defender for endpoint. Vulnerability Scanner Defender.
From learn.microsoft.com
Enable vulnerability scanning with the integrated Qualys scanner Vulnerability Scanner Defender If you suspect that your device may have malware you should have microsoft defender run a scan. Snmp traffic between the defender for endpoint scanning device and the targeted network devices must be allowed (for example, by the firewall). Decide which network devices are. Here's how to do that on windows, mac, or android. Vulnerability assessment scanning for containers, powered. Vulnerability Scanner Defender.
From m365maps.com
Microsoft Defender Vulnerability Management M365 Maps Vulnerability Scanner Defender Decide which network devices are. If you suspect that your device may have malware you should have microsoft defender run a scan. Snmp traffic between the defender for endpoint scanning device and the targeted network devices must be allowed (for example, by the firewall). Here's how to do that on windows, mac, or android. Vulnerability assessment scanning for containers, powered. Vulnerability Scanner Defender.
From techcommunity.microsoft.com
Builtin vulnerability assessment for VMs in Microsoft Defender for Vulnerability Scanner Defender If you suspect that your device may have malware you should have microsoft defender run a scan. Vulnerability assessment scanning for containers, powered by microsoft defender vulnerability management (mdvm), is an integrated solution that empowers security teams to. Here's how to do that on windows, mac, or android. Snmp traffic between the defender for endpoint scanning device and the targeted. Vulnerability Scanner Defender.
From techcommunity.microsoft.com
Microsoft vulnerability management integrates with ServiceNow VR Vulnerability Scanner Defender If you suspect that your device may have malware you should have microsoft defender run a scan. Decide which network devices are. Vulnerability assessment scanning for containers, powered by microsoft defender vulnerability management (mdvm), is an integrated solution that empowers security teams to. Snmp traffic between the defender for endpoint scanning device and the targeted network devices must be allowed. Vulnerability Scanner Defender.
From vulners.com
Internal Vulnerability Scanner What is and Usage Vulners Vulnerability Scanner Defender Decide which network devices are. If you suspect that your device may have malware you should have microsoft defender run a scan. Snmp traffic between the defender for endpoint scanning device and the targeted network devices must be allowed (for example, by the firewall). Here's how to do that on windows, mac, or android. Vulnerability assessment scanning for containers, powered. Vulnerability Scanner Defender.
From www.scappman.com
Microsoft releases a New Defender Vulnerability Management tool Vulnerability Scanner Defender Vulnerability assessment scanning for containers, powered by microsoft defender vulnerability management (mdvm), is an integrated solution that empowers security teams to. Snmp traffic between the defender for endpoint scanning device and the targeted network devices must be allowed (for example, by the firewall). Decide which network devices are. Here's how to do that on windows, mac, or android. If you. Vulnerability Scanner Defender.
From joeho.xyz
Vulnerability Scanning in Microsoft Defender For Server Joe Ho Blog Vulnerability Scanner Defender Decide which network devices are. Here's how to do that on windows, mac, or android. Snmp traffic between the defender for endpoint scanning device and the targeted network devices must be allowed (for example, by the firewall). Vulnerability assessment scanning for containers, powered by microsoft defender vulnerability management (mdvm), is an integrated solution that empowers security teams to. If you. Vulnerability Scanner Defender.
From nordicdefender.com
What is Vulnerability Scanning in Cybersecurity? Nordic Defender 1 Vulnerability Scanner Defender Decide which network devices are. Here's how to do that on windows, mac, or android. If you suspect that your device may have malware you should have microsoft defender run a scan. Vulnerability assessment scanning for containers, powered by microsoft defender vulnerability management (mdvm), is an integrated solution that empowers security teams to. Snmp traffic between the defender for endpoint. Vulnerability Scanner Defender.
From www.youtube.com
Threat and Vulnerability Management Dashboard Microsoft Defender Vulnerability Scanner Defender If you suspect that your device may have malware you should have microsoft defender run a scan. Vulnerability assessment scanning for containers, powered by microsoft defender vulnerability management (mdvm), is an integrated solution that empowers security teams to. Snmp traffic between the defender for endpoint scanning device and the targeted network devices must be allowed (for example, by the firewall).. Vulnerability Scanner Defender.
From learn.microsoft.com
Scan for vulnerabilities on SQL servers Microsoft Defender for Cloud Vulnerability Scanner Defender Vulnerability assessment scanning for containers, powered by microsoft defender vulnerability management (mdvm), is an integrated solution that empowers security teams to. Snmp traffic between the defender for endpoint scanning device and the targeted network devices must be allowed (for example, by the firewall). Decide which network devices are. If you suspect that your device may have malware you should have. Vulnerability Scanner Defender.
From learn.microsoft.com
Enable vulnerability scanning with the integrated Qualys scanner Vulnerability Scanner Defender Snmp traffic between the defender for endpoint scanning device and the targeted network devices must be allowed (for example, by the firewall). If you suspect that your device may have malware you should have microsoft defender run a scan. Vulnerability assessment scanning for containers, powered by microsoft defender vulnerability management (mdvm), is an integrated solution that empowers security teams to.. Vulnerability Scanner Defender.
From blog.securelayer7.net
Automated Vulnerability Scanning Tools Security Solutions Vulnerability Scanner Defender Here's how to do that on windows, mac, or android. Vulnerability assessment scanning for containers, powered by microsoft defender vulnerability management (mdvm), is an integrated solution that empowers security teams to. Decide which network devices are. If you suspect that your device may have malware you should have microsoft defender run a scan. Snmp traffic between the defender for endpoint. Vulnerability Scanner Defender.
From www.scappman.com
Microsoft releases a New Defender Vulnerability Management tool Vulnerability Scanner Defender Decide which network devices are. If you suspect that your device may have malware you should have microsoft defender run a scan. Here's how to do that on windows, mac, or android. Vulnerability assessment scanning for containers, powered by microsoft defender vulnerability management (mdvm), is an integrated solution that empowers security teams to. Snmp traffic between the defender for endpoint. Vulnerability Scanner Defender.
From www.youtube.com
Microsoft Defender for Cloud Qualys Vulnerability Assessment Scanner Vulnerability Scanner Defender Decide which network devices are. If you suspect that your device may have malware you should have microsoft defender run a scan. Vulnerability assessment scanning for containers, powered by microsoft defender vulnerability management (mdvm), is an integrated solution that empowers security teams to. Here's how to do that on windows, mac, or android. Snmp traffic between the defender for endpoint. Vulnerability Scanner Defender.
From thalpius.com
Microsoft Defender Vulnerability Management Authenticated Scan Security Vulnerability Scanner Defender Snmp traffic between the defender for endpoint scanning device and the targeted network devices must be allowed (for example, by the firewall). Vulnerability assessment scanning for containers, powered by microsoft defender vulnerability management (mdvm), is an integrated solution that empowers security teams to. If you suspect that your device may have malware you should have microsoft defender run a scan.. Vulnerability Scanner Defender.
From www.youtube.com
Microsoft Defender for Endpoint Threat and Vulnerability Management Vulnerability Scanner Defender Snmp traffic between the defender for endpoint scanning device and the targeted network devices must be allowed (for example, by the firewall). Here's how to do that on windows, mac, or android. Decide which network devices are. If you suspect that your device may have malware you should have microsoft defender run a scan. Vulnerability assessment scanning for containers, powered. Vulnerability Scanner Defender.
From mortenknudsen.net
How to migrate from Qualys and enable Microsoft Defender Vulnerability Vulnerability Scanner Defender Vulnerability assessment scanning for containers, powered by microsoft defender vulnerability management (mdvm), is an integrated solution that empowers security teams to. Snmp traffic between the defender for endpoint scanning device and the targeted network devices must be allowed (for example, by the firewall). Here's how to do that on windows, mac, or android. If you suspect that your device may. Vulnerability Scanner Defender.
From learn.microsoft.com
Scan for vulnerabilities on SQL servers Microsoft Defender for Cloud Vulnerability Scanner Defender Decide which network devices are. Here's how to do that on windows, mac, or android. If you suspect that your device may have malware you should have microsoft defender run a scan. Snmp traffic between the defender for endpoint scanning device and the targeted network devices must be allowed (for example, by the firewall). Vulnerability assessment scanning for containers, powered. Vulnerability Scanner Defender.
From subscription.packtpub.com
Microsoft Azure Security Technologies Certification and Beyond Vulnerability Scanner Defender Vulnerability assessment scanning for containers, powered by microsoft defender vulnerability management (mdvm), is an integrated solution that empowers security teams to. Snmp traffic between the defender for endpoint scanning device and the targeted network devices must be allowed (for example, by the firewall). Decide which network devices are. Here's how to do that on windows, mac, or android. If you. Vulnerability Scanner Defender.
From learn.microsoft.com
Authenticated scan for Windows in Defender Vulnerability Management Vulnerability Scanner Defender Decide which network devices are. Vulnerability assessment scanning for containers, powered by microsoft defender vulnerability management (mdvm), is an integrated solution that empowers security teams to. Here's how to do that on windows, mac, or android. Snmp traffic between the defender for endpoint scanning device and the targeted network devices must be allowed (for example, by the firewall). If you. Vulnerability Scanner Defender.
From learn.microsoft.com
View your Microsoft Defender Vulnerability Management dashboard in Vulnerability Scanner Defender Snmp traffic between the defender for endpoint scanning device and the targeted network devices must be allowed (for example, by the firewall). Here's how to do that on windows, mac, or android. Decide which network devices are. Vulnerability assessment scanning for containers, powered by microsoft defender vulnerability management (mdvm), is an integrated solution that empowers security teams to. If you. Vulnerability Scanner Defender.