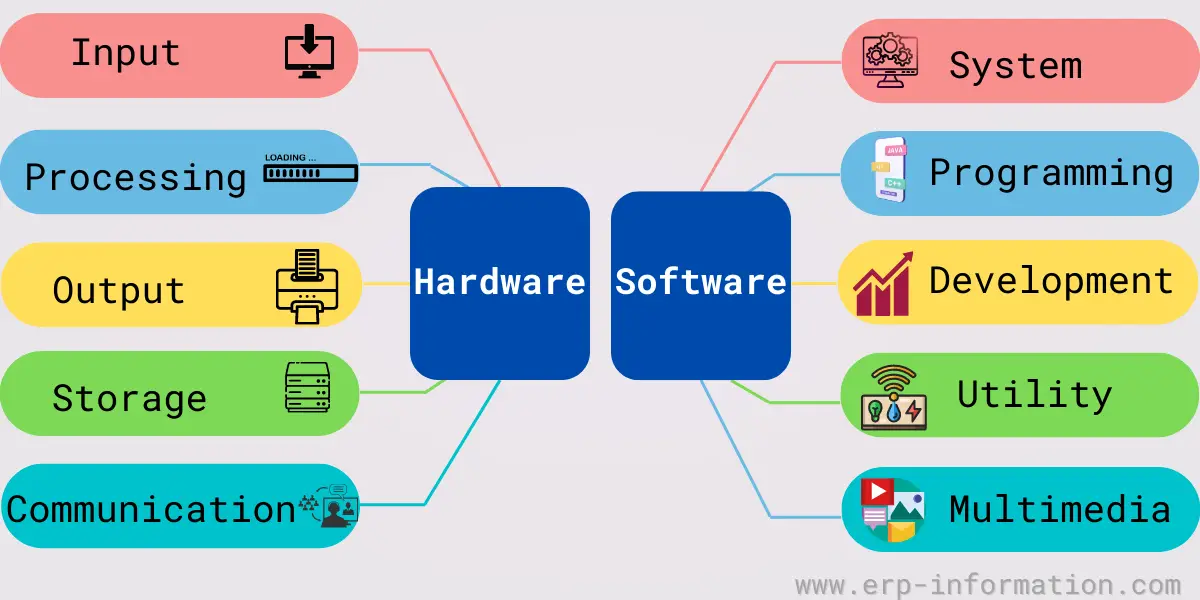
Hardware Vs Software Encryption . Software encryption uses encryption algorithms to encrypt data during transfer or storage. It is more secure than other methods as it allows for the encryption process to occur away from the main hardware. Hardware encryption uses an onboarding device algorithm for encryption and decryption. Ontrack discusses the pros and cons of software v hardware encryption, and the challenges around data recovery of both. Discover the unparalleled advantages it offers and how. Hardware encryption uses physical devices to encrypt data, which is typically faster and more secure but can come at a higher cost. Unveil the robust strength of hardware encryption, showcasing why it is the cornerstone of formidable data protection. But software encryption uses symmetric cryptography that involves using the same key for data encryption and decryption. Therefore, deciding between hardware and software encryption is a crucial step in vulnerability management. Software and hardware encryption are two main methods of data protection. Learn the differences, benefits, and limitations of hardware encryption and software encryption, two main methods for safeguarding.
from www.erp-information.com
Hardware encryption uses an onboarding device algorithm for encryption and decryption. Unveil the robust strength of hardware encryption, showcasing why it is the cornerstone of formidable data protection. It is more secure than other methods as it allows for the encryption process to occur away from the main hardware. Software encryption uses encryption algorithms to encrypt data during transfer or storage. Software and hardware encryption are two main methods of data protection. Therefore, deciding between hardware and software encryption is a crucial step in vulnerability management. Ontrack discusses the pros and cons of software v hardware encryption, and the challenges around data recovery of both. But software encryption uses symmetric cryptography that involves using the same key for data encryption and decryption. Learn the differences, benefits, and limitations of hardware encryption and software encryption, two main methods for safeguarding. Hardware encryption uses physical devices to encrypt data, which is typically faster and more secure but can come at a higher cost.
Hardware vs Software (Features, Examples, and Types)
Hardware Vs Software Encryption Learn the differences, benefits, and limitations of hardware encryption and software encryption, two main methods for safeguarding. It is more secure than other methods as it allows for the encryption process to occur away from the main hardware. Hardware encryption uses an onboarding device algorithm for encryption and decryption. Therefore, deciding between hardware and software encryption is a crucial step in vulnerability management. Software encryption uses encryption algorithms to encrypt data during transfer or storage. Software and hardware encryption are two main methods of data protection. Discover the unparalleled advantages it offers and how. Learn the differences, benefits, and limitations of hardware encryption and software encryption, two main methods for safeguarding. But software encryption uses symmetric cryptography that involves using the same key for data encryption and decryption. Ontrack discusses the pros and cons of software v hardware encryption, and the challenges around data recovery of both. Hardware encryption uses physical devices to encrypt data, which is typically faster and more secure but can come at a higher cost. Unveil the robust strength of hardware encryption, showcasing why it is the cornerstone of formidable data protection.
From www.slideshare.net
Sans Tech Paper Hardware Vs Software Encryption Hardware Vs Software Encryption But software encryption uses symmetric cryptography that involves using the same key for data encryption and decryption. Therefore, deciding between hardware and software encryption is a crucial step in vulnerability management. Discover the unparalleled advantages it offers and how. Software and hardware encryption are two main methods of data protection. Ontrack discusses the pros and cons of software v hardware. Hardware Vs Software Encryption.
From jms-securedata.co.uk
Encryption Software JMS Secure Data Hardware Vs Software Encryption Software and hardware encryption are two main methods of data protection. Unveil the robust strength of hardware encryption, showcasing why it is the cornerstone of formidable data protection. It is more secure than other methods as it allows for the encryption process to occur away from the main hardware. But software encryption uses symmetric cryptography that involves using the same. Hardware Vs Software Encryption.
From playnoevil.com
Software Encryption vs. Hardware Encryption Ultimate Guide Hardware Vs Software Encryption Software encryption uses encryption algorithms to encrypt data during transfer or storage. Unveil the robust strength of hardware encryption, showcasing why it is the cornerstone of formidable data protection. Software and hardware encryption are two main methods of data protection. Hardware encryption uses an onboarding device algorithm for encryption and decryption. Discover the unparalleled advantages it offers and how. Hardware. Hardware Vs Software Encryption.
From www.slideshare.net
Hardware Vs Software Encryption Comparison Hardware Vs Software Encryption Ontrack discusses the pros and cons of software v hardware encryption, and the challenges around data recovery of both. It is more secure than other methods as it allows for the encryption process to occur away from the main hardware. But software encryption uses symmetric cryptography that involves using the same key for data encryption and decryption. Learn the differences,. Hardware Vs Software Encryption.
From www.linkedin.com
Hardware vs Software Encryption Which One to Choose? Hardware Vs Software Encryption It is more secure than other methods as it allows for the encryption process to occur away from the main hardware. Learn the differences, benefits, and limitations of hardware encryption and software encryption, two main methods for safeguarding. Therefore, deciding between hardware and software encryption is a crucial step in vulnerability management. Hardware encryption uses an onboarding device algorithm for. Hardware Vs Software Encryption.
From www.kingston.com
Infographic Software vs Hardware Encryption in Client SSD and USB Hardware Vs Software Encryption Therefore, deciding between hardware and software encryption is a crucial step in vulnerability management. Hardware encryption uses an onboarding device algorithm for encryption and decryption. But software encryption uses symmetric cryptography that involves using the same key for data encryption and decryption. Learn the differences, benefits, and limitations of hardware encryption and software encryption, two main methods for safeguarding. Ontrack. Hardware Vs Software Encryption.
From geekflare.com
Hardware Encryption What It Is and Why You Need It Geekflare Hardware Vs Software Encryption Hardware encryption uses physical devices to encrypt data, which is typically faster and more secure but can come at a higher cost. Discover the unparalleled advantages it offers and how. Ontrack discusses the pros and cons of software v hardware encryption, and the challenges around data recovery of both. Learn the differences, benefits, and limitations of hardware encryption and software. Hardware Vs Software Encryption.
From intechhouse.com
Software vs Hardware INTechHouse Blog Hardware Vs Software Encryption Hardware encryption uses physical devices to encrypt data, which is typically faster and more secure but can come at a higher cost. Hardware encryption uses an onboarding device algorithm for encryption and decryption. Software and hardware encryption are two main methods of data protection. Therefore, deciding between hardware and software encryption is a crucial step in vulnerability management. But software. Hardware Vs Software Encryption.
From www.slideshare.net
Sans Tech Paper Hardware Vs Software Encryption Hardware Vs Software Encryption Hardware encryption uses an onboarding device algorithm for encryption and decryption. But software encryption uses symmetric cryptography that involves using the same key for data encryption and decryption. Learn the differences, benefits, and limitations of hardware encryption and software encryption, two main methods for safeguarding. Software encryption uses encryption algorithms to encrypt data during transfer or storage. Hardware encryption uses. Hardware Vs Software Encryption.
From www.slideshare.net
Sans Tech Paper Hardware Vs Software Encryption Hardware Vs Software Encryption Unveil the robust strength of hardware encryption, showcasing why it is the cornerstone of formidable data protection. Therefore, deciding between hardware and software encryption is a crucial step in vulnerability management. Hardware encryption uses physical devices to encrypt data, which is typically faster and more secure but can come at a higher cost. Hardware encryption uses an onboarding device algorithm. Hardware Vs Software Encryption.
From www.cit-sys.co.uk
Hardware vs software encryption for encrypted USB flash drives Hardware Vs Software Encryption It is more secure than other methods as it allows for the encryption process to occur away from the main hardware. Unveil the robust strength of hardware encryption, showcasing why it is the cornerstone of formidable data protection. Ontrack discusses the pros and cons of software v hardware encryption, and the challenges around data recovery of both. Discover the unparalleled. Hardware Vs Software Encryption.
From www.slideshare.net
Sans Tech Paper Hardware Vs Software Encryption Hardware Vs Software Encryption Software encryption uses encryption algorithms to encrypt data during transfer or storage. Discover the unparalleled advantages it offers and how. But software encryption uses symmetric cryptography that involves using the same key for data encryption and decryption. Unveil the robust strength of hardware encryption, showcasing why it is the cornerstone of formidable data protection. Hardware encryption uses physical devices to. Hardware Vs Software Encryption.
From www.toptut.com
Software Vs. Hardware Encryption The Pros And Cons Hardware Vs Software Encryption Software and hardware encryption are two main methods of data protection. Unveil the robust strength of hardware encryption, showcasing why it is the cornerstone of formidable data protection. Learn the differences, benefits, and limitations of hardware encryption and software encryption, two main methods for safeguarding. It is more secure than other methods as it allows for the encryption process to. Hardware Vs Software Encryption.
From www.otherarticles.com
Hardware Encryption Vs Software Encryption A Comprehensive Guide Hardware Vs Software Encryption Therefore, deciding between hardware and software encryption is a crucial step in vulnerability management. Unveil the robust strength of hardware encryption, showcasing why it is the cornerstone of formidable data protection. Hardware encryption uses an onboarding device algorithm for encryption and decryption. Software encryption uses encryption algorithms to encrypt data during transfer or storage. Software and hardware encryption are two. Hardware Vs Software Encryption.
From www.youtube.com
Software Vs Hardware Based Encryption DIY in 5 Ep 156 YouTube Hardware Vs Software Encryption Ontrack discusses the pros and cons of software v hardware encryption, and the challenges around data recovery of both. Software and hardware encryption are two main methods of data protection. Learn the differences, benefits, and limitations of hardware encryption and software encryption, two main methods for safeguarding. Discover the unparalleled advantages it offers and how. Therefore, deciding between hardware and. Hardware Vs Software Encryption.
From www.erp-information.com
Hardware vs Software (Features, Examples, and Types) Hardware Vs Software Encryption Software and hardware encryption are two main methods of data protection. Hardware encryption uses an onboarding device algorithm for encryption and decryption. Ontrack discusses the pros and cons of software v hardware encryption, and the challenges around data recovery of both. Unveil the robust strength of hardware encryption, showcasing why it is the cornerstone of formidable data protection. It is. Hardware Vs Software Encryption.
From www.internetsafetystatistics.com
Software Vs Hardware Encryption A Comparative Look Hardware Vs Software Encryption Discover the unparalleled advantages it offers and how. It is more secure than other methods as it allows for the encryption process to occur away from the main hardware. Hardware encryption uses an onboarding device algorithm for encryption and decryption. Unveil the robust strength of hardware encryption, showcasing why it is the cornerstone of formidable data protection. Software encryption uses. Hardware Vs Software Encryption.
From www.slideserve.com
PPT Data Protection Policy Compliance using Notebook Hard Disk Drive Hardware Vs Software Encryption Learn the differences, benefits, and limitations of hardware encryption and software encryption, two main methods for safeguarding. Unveil the robust strength of hardware encryption, showcasing why it is the cornerstone of formidable data protection. Software encryption uses encryption algorithms to encrypt data during transfer or storage. Hardware encryption uses physical devices to encrypt data, which is typically faster and more. Hardware Vs Software Encryption.
From dxoudcglw.blob.core.windows.net
Hardware Encryption Vs Software Encryption at Erin Kaufman blog Hardware Vs Software Encryption Learn the differences, benefits, and limitations of hardware encryption and software encryption, two main methods for safeguarding. Ontrack discusses the pros and cons of software v hardware encryption, and the challenges around data recovery of both. Hardware encryption uses physical devices to encrypt data, which is typically faster and more secure but can come at a higher cost. Software and. Hardware Vs Software Encryption.
From www.internetsafetystatistics.com
Software Vs Hardware Encryption A Comparative Look Hardware Vs Software Encryption Unveil the robust strength of hardware encryption, showcasing why it is the cornerstone of formidable data protection. Software encryption uses encryption algorithms to encrypt data during transfer or storage. Discover the unparalleled advantages it offers and how. It is more secure than other methods as it allows for the encryption process to occur away from the main hardware. Ontrack discusses. Hardware Vs Software Encryption.
From www.slideshare.net
Sans Tech Paper Hardware Vs Software Encryption Hardware Vs Software Encryption Discover the unparalleled advantages it offers and how. Hardware encryption uses physical devices to encrypt data, which is typically faster and more secure but can come at a higher cost. But software encryption uses symmetric cryptography that involves using the same key for data encryption and decryption. Unveil the robust strength of hardware encryption, showcasing why it is the cornerstone. Hardware Vs Software Encryption.
From www.internetsafetystatistics.com
Software Vs Hardware Encryption A Comparative Look Hardware Vs Software Encryption Therefore, deciding between hardware and software encryption is a crucial step in vulnerability management. But software encryption uses symmetric cryptography that involves using the same key for data encryption and decryption. Software and hardware encryption are two main methods of data protection. Hardware encryption uses physical devices to encrypt data, which is typically faster and more secure but can come. Hardware Vs Software Encryption.
From www.cisco.com
What Is Encryption? Explanation and Types Cisco Hardware Vs Software Encryption Software encryption uses encryption algorithms to encrypt data during transfer or storage. Hardware encryption uses an onboarding device algorithm for encryption and decryption. Therefore, deciding between hardware and software encryption is a crucial step in vulnerability management. Ontrack discusses the pros and cons of software v hardware encryption, and the challenges around data recovery of both. It is more secure. Hardware Vs Software Encryption.
From www.erp-information.com
Hardware vs Software (Features, Examples, and Types) Hardware Vs Software Encryption Software encryption uses encryption algorithms to encrypt data during transfer or storage. Discover the unparalleled advantages it offers and how. Learn the differences, benefits, and limitations of hardware encryption and software encryption, two main methods for safeguarding. Unveil the robust strength of hardware encryption, showcasing why it is the cornerstone of formidable data protection. Therefore, deciding between hardware and software. Hardware Vs Software Encryption.
From www.thecloudxperts.co.uk
Fundamental flaws in the Hardware Encryption system Convert Hardware Hardware Vs Software Encryption Software and hardware encryption are two main methods of data protection. Discover the unparalleled advantages it offers and how. It is more secure than other methods as it allows for the encryption process to occur away from the main hardware. Hardware encryption uses an onboarding device algorithm for encryption and decryption. But software encryption uses symmetric cryptography that involves using. Hardware Vs Software Encryption.
From joievalau.blob.core.windows.net
Best Algorithm For Password Encryption And Decryption at Phillip Hardware Vs Software Encryption Ontrack discusses the pros and cons of software v hardware encryption, and the challenges around data recovery of both. Hardware encryption uses physical devices to encrypt data, which is typically faster and more secure but can come at a higher cost. Hardware encryption uses an onboarding device algorithm for encryption and decryption. Learn the differences, benefits, and limitations of hardware. Hardware Vs Software Encryption.
From www.slideshare.net
Sans Tech Paper Hardware Vs Software Encryption Hardware Vs Software Encryption But software encryption uses symmetric cryptography that involves using the same key for data encryption and decryption. Software encryption uses encryption algorithms to encrypt data during transfer or storage. Learn the differences, benefits, and limitations of hardware encryption and software encryption, two main methods for safeguarding. Hardware encryption uses physical devices to encrypt data, which is typically faster and more. Hardware Vs Software Encryption.
From dataempires.com
Hardware Encryption VS Software Encryption Hardware Vs Software Encryption Hardware encryption uses physical devices to encrypt data, which is typically faster and more secure but can come at a higher cost. Unveil the robust strength of hardware encryption, showcasing why it is the cornerstone of formidable data protection. Software and hardware encryption are two main methods of data protection. But software encryption uses symmetric cryptography that involves using the. Hardware Vs Software Encryption.
From nextdoorsec.com
Hardware Encryption vs. Software Encryption Safeguarding Data in the Hardware Vs Software Encryption It is more secure than other methods as it allows for the encryption process to occur away from the main hardware. Unveil the robust strength of hardware encryption, showcasing why it is the cornerstone of formidable data protection. Software encryption uses encryption algorithms to encrypt data during transfer or storage. Hardware encryption uses physical devices to encrypt data, which is. Hardware Vs Software Encryption.
From talan-has-gray.blogspot.com
Giving Suitable Examples Explain the Difference Between Hardware and Hardware Vs Software Encryption Hardware encryption uses an onboarding device algorithm for encryption and decryption. Software encryption uses encryption algorithms to encrypt data during transfer or storage. Software and hardware encryption are two main methods of data protection. Unveil the robust strength of hardware encryption, showcasing why it is the cornerstone of formidable data protection. Therefore, deciding between hardware and software encryption is a. Hardware Vs Software Encryption.
From www.slideshare.net
Sans Tech Paper Hardware Vs Software Encryption Hardware Vs Software Encryption Hardware encryption uses an onboarding device algorithm for encryption and decryption. Software and hardware encryption are two main methods of data protection. Unveil the robust strength of hardware encryption, showcasing why it is the cornerstone of formidable data protection. Ontrack discusses the pros and cons of software v hardware encryption, and the challenges around data recovery of both. Software encryption. Hardware Vs Software Encryption.
From www.pinterest.ca
EndToEnd Encryption Explained Infographic Computer security Hardware Vs Software Encryption It is more secure than other methods as it allows for the encryption process to occur away from the main hardware. Discover the unparalleled advantages it offers and how. Software encryption uses encryption algorithms to encrypt data during transfer or storage. Software and hardware encryption are two main methods of data protection. Therefore, deciding between hardware and software encryption is. Hardware Vs Software Encryption.
From www.oactechnology.com
Hardware versus Software Encryption OAC Technology Hardware Vs Software Encryption Hardware encryption uses an onboarding device algorithm for encryption and decryption. It is more secure than other methods as it allows for the encryption process to occur away from the main hardware. Hardware encryption uses physical devices to encrypt data, which is typically faster and more secure but can come at a higher cost. Therefore, deciding between hardware and software. Hardware Vs Software Encryption.
From joiyheobm.blob.core.windows.net
Hardware Level Encryption at Karen Torres blog Hardware Vs Software Encryption Therefore, deciding between hardware and software encryption is a crucial step in vulnerability management. Hardware encryption uses an onboarding device algorithm for encryption and decryption. Ontrack discusses the pros and cons of software v hardware encryption, and the challenges around data recovery of both. Learn the differences, benefits, and limitations of hardware encryption and software encryption, two main methods for. Hardware Vs Software Encryption.
From www.researchgate.net
General block diagram of encryption device (a) Softwarehardware Hardware Vs Software Encryption Discover the unparalleled advantages it offers and how. Therefore, deciding between hardware and software encryption is a crucial step in vulnerability management. Software and hardware encryption are two main methods of data protection. Hardware encryption uses an onboarding device algorithm for encryption and decryption. Ontrack discusses the pros and cons of software v hardware encryption, and the challenges around data. Hardware Vs Software Encryption.