What Are The Key Principles On Which Access Control Is Founded . Of course, we’re talking in terms of it security here, but the same. access control is a method of guaranteeing that users are who they say they are and that they have the appropriate access to. access control is a method of restricting access to sensitive data. controlling who has access to a system and the breadth of access a user has is vital to ensure the security of systems and data. there are three core elements to access control. This article explores access control, its importance in cybersecurity,. Access control consists of data and physical access protections that strengthen cybersecurity by managing users’ authentication to systems. what is access control? types, importance & best practices. Only those that have had their identity verified can access.
from arkit.co.in
Of course, we’re talking in terms of it security here, but the same. controlling who has access to a system and the breadth of access a user has is vital to ensure the security of systems and data. This article explores access control, its importance in cybersecurity,. there are three core elements to access control. types, importance & best practices. Only those that have had their identity verified can access. what is access control? access control is a method of guaranteeing that users are who they say they are and that they have the appropriate access to. access control is a method of restricting access to sensitive data. Access control consists of data and physical access protections that strengthen cybersecurity by managing users’ authentication to systems.
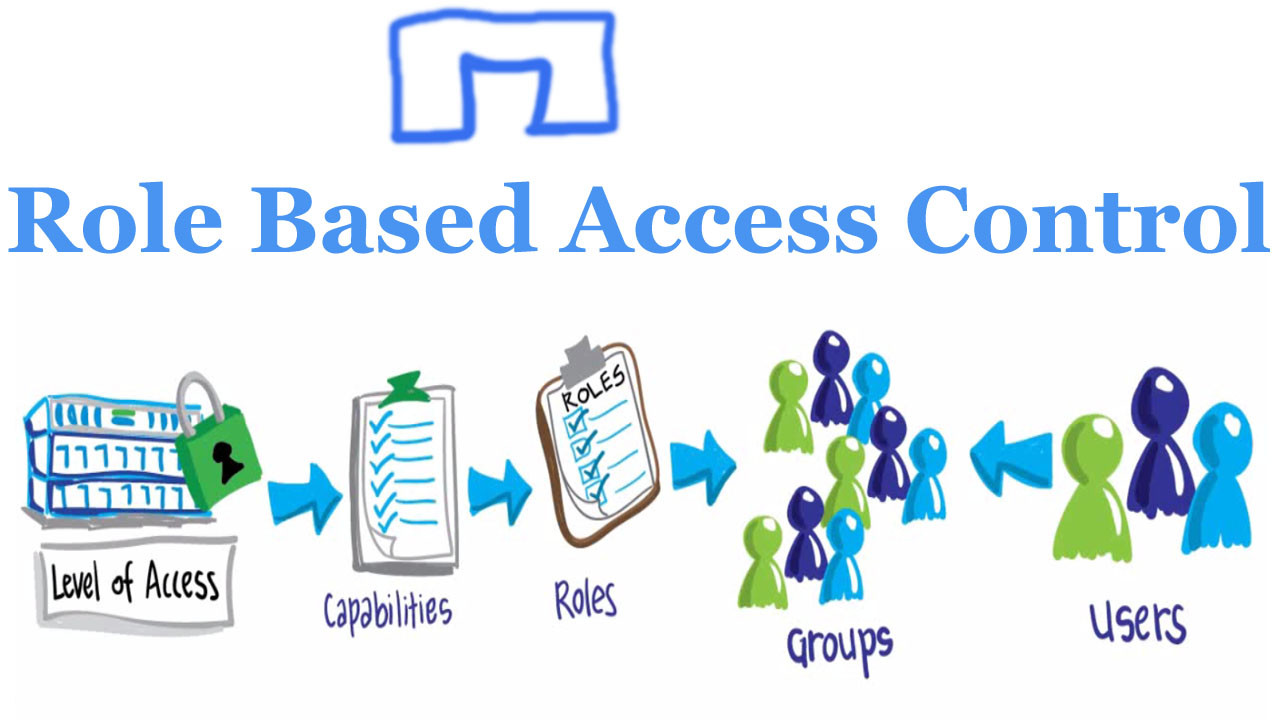
Role Based Access Control RBAC Netapp Cluster Mode application
What Are The Key Principles On Which Access Control Is Founded types, importance & best practices. Access control consists of data and physical access protections that strengthen cybersecurity by managing users’ authentication to systems. This article explores access control, its importance in cybersecurity,. what is access control? Only those that have had their identity verified can access. access control is a method of restricting access to sensitive data. controlling who has access to a system and the breadth of access a user has is vital to ensure the security of systems and data. access control is a method of guaranteeing that users are who they say they are and that they have the appropriate access to. Of course, we’re talking in terms of it security here, but the same. there are three core elements to access control. types, importance & best practices.
From www.vrogue.co
Types Of Access Control System Infographics Access Control System Vrogue What Are The Key Principles On Which Access Control Is Founded there are three core elements to access control. Of course, we’re talking in terms of it security here, but the same. access control is a method of guaranteeing that users are who they say they are and that they have the appropriate access to. This article explores access control, its importance in cybersecurity,. controlling who has access. What Are The Key Principles On Which Access Control Is Founded.
From its-physec.com
Access Control Physical Security Solutions ITS Physec What Are The Key Principles On Which Access Control Is Founded Access control consists of data and physical access protections that strengthen cybersecurity by managing users’ authentication to systems. types, importance & best practices. This article explores access control, its importance in cybersecurity,. Of course, we’re talking in terms of it security here, but the same. there are three core elements to access control. access control is a. What Are The Key Principles On Which Access Control Is Founded.
From www.youtube.com
Access Control Principles YouTube What Are The Key Principles On Which Access Control Is Founded there are three core elements to access control. types, importance & best practices. access control is a method of guaranteeing that users are who they say they are and that they have the appropriate access to. what is access control? Only those that have had their identity verified can access. controlling who has access to. What Are The Key Principles On Which Access Control Is Founded.
From solatatech.com
What is RoleBased Access Control (RBAC)? (2022) What Are The Key Principles On Which Access Control Is Founded there are three core elements to access control. access control is a method of guaranteeing that users are who they say they are and that they have the appropriate access to. access control is a method of restricting access to sensitive data. types, importance & best practices. Only those that have had their identity verified can. What Are The Key Principles On Which Access Control Is Founded.
From courses.lumenlearning.com
The Control Process Principles of Management What Are The Key Principles On Which Access Control Is Founded access control is a method of guaranteeing that users are who they say they are and that they have the appropriate access to. what is access control? there are three core elements to access control. Of course, we’re talking in terms of it security here, but the same. access control is a method of restricting access. What Are The Key Principles On Which Access Control Is Founded.
From arkit.co.in
Role Based Access Control RBAC Netapp Cluster Mode application What Are The Key Principles On Which Access Control Is Founded Only those that have had their identity verified can access. access control is a method of restricting access to sensitive data. This article explores access control, its importance in cybersecurity,. types, importance & best practices. what is access control? there are three core elements to access control. Access control consists of data and physical access protections. What Are The Key Principles On Which Access Control Is Founded.
From www.horangi.com
Identity & Access Management (IAM) for Dummies What Are The Key Principles On Which Access Control Is Founded This article explores access control, its importance in cybersecurity,. access control is a method of restricting access to sensitive data. controlling who has access to a system and the breadth of access a user has is vital to ensure the security of systems and data. access control is a method of guaranteeing that users are who they. What Are The Key Principles On Which Access Control Is Founded.
From solatatech.com
What is RoleBased Access Control (RBAC)? (2022) What Are The Key Principles On Which Access Control Is Founded what is access control? there are three core elements to access control. types, importance & best practices. Only those that have had their identity verified can access. access control is a method of restricting access to sensitive data. access control is a method of guaranteeing that users are who they say they are and that. What Are The Key Principles On Which Access Control Is Founded.
From mech4study.blogspot.com
mech4study Centrifugal Pump Principle, Parts, Working, Types What Are The Key Principles On Which Access Control Is Founded controlling who has access to a system and the breadth of access a user has is vital to ensure the security of systems and data. Access control consists of data and physical access protections that strengthen cybersecurity by managing users’ authentication to systems. what is access control? Only those that have had their identity verified can access. . What Are The Key Principles On Which Access Control Is Founded.
From ccqm.ch
ISO/IEC Information Security Management System Con Cert Quality What Are The Key Principles On Which Access Control Is Founded Access control consists of data and physical access protections that strengthen cybersecurity by managing users’ authentication to systems. This article explores access control, its importance in cybersecurity,. what is access control? access control is a method of guaranteeing that users are who they say they are and that they have the appropriate access to. Only those that have. What Are The Key Principles On Which Access Control Is Founded.
From amazonia.fiocruz.br
Online Essay Help amazonia.fiocruz.br What Are The Key Principles On Which Access Control Is Founded Of course, we’re talking in terms of it security here, but the same. Access control consists of data and physical access protections that strengthen cybersecurity by managing users’ authentication to systems. types, importance & best practices. access control is a method of restricting access to sensitive data. This article explores access control, its importance in cybersecurity,. controlling. What Are The Key Principles On Which Access Control Is Founded.
From www.slideshare.net
Access Control Principles and Practice What Are The Key Principles On Which Access Control Is Founded controlling who has access to a system and the breadth of access a user has is vital to ensure the security of systems and data. Only those that have had their identity verified can access. access control is a method of guaranteeing that users are who they say they are and that they have the appropriate access to.. What Are The Key Principles On Which Access Control Is Founded.
From www.vrogue.co
The Hierarchy Of Hazard Control Safety Fabrications vrogue.co What Are The Key Principles On Which Access Control Is Founded This article explores access control, its importance in cybersecurity,. access control is a method of guaranteeing that users are who they say they are and that they have the appropriate access to. controlling who has access to a system and the breadth of access a user has is vital to ensure the security of systems and data. . What Are The Key Principles On Which Access Control Is Founded.
From www.slideserve.com
PPT Lecture 7 Access Control PowerPoint Presentation, free download What Are The Key Principles On Which Access Control Is Founded there are three core elements to access control. This article explores access control, its importance in cybersecurity,. types, importance & best practices. controlling who has access to a system and the breadth of access a user has is vital to ensure the security of systems and data. Of course, we’re talking in terms of it security here,. What Are The Key Principles On Which Access Control Is Founded.
From www.slideserve.com
PPT Access Control, Operating System Security, and Security System What Are The Key Principles On Which Access Control Is Founded Access control consists of data and physical access protections that strengthen cybersecurity by managing users’ authentication to systems. controlling who has access to a system and the breadth of access a user has is vital to ensure the security of systems and data. This article explores access control, its importance in cybersecurity,. access control is a method of. What Are The Key Principles On Which Access Control Is Founded.
From www.smashingmagazine.com
State Of GDPR In 2021 Key Updates And What They Mean — Smashing Magazine What Are The Key Principles On Which Access Control Is Founded Access control consists of data and physical access protections that strengthen cybersecurity by managing users’ authentication to systems. controlling who has access to a system and the breadth of access a user has is vital to ensure the security of systems and data. what is access control? Only those that have had their identity verified can access. This. What Are The Key Principles On Which Access Control Is Founded.
From www.slideshare.net
Access Control Principles and Practice What Are The Key Principles On Which Access Control Is Founded what is access control? there are three core elements to access control. access control is a method of restricting access to sensitive data. access control is a method of guaranteeing that users are who they say they are and that they have the appropriate access to. Access control consists of data and physical access protections that. What Are The Key Principles On Which Access Control Is Founded.
From www.okta.com
What Is RoleBased Access Control (RBAC)? Okta What Are The Key Principles On Which Access Control Is Founded access control is a method of restricting access to sensitive data. types, importance & best practices. Only those that have had their identity verified can access. This article explores access control, its importance in cybersecurity,. Access control consists of data and physical access protections that strengthen cybersecurity by managing users’ authentication to systems. controlling who has access. What Are The Key Principles On Which Access Control Is Founded.
From www.xorlogics.com
3 Basic A’s of Identity and Access Management Authentication What Are The Key Principles On Which Access Control Is Founded This article explores access control, its importance in cybersecurity,. there are three core elements to access control. types, importance & best practices. controlling who has access to a system and the breadth of access a user has is vital to ensure the security of systems and data. what is access control? Access control consists of data. What Are The Key Principles On Which Access Control Is Founded.
From www.masterkeysystems.co.uk
Master Key System Vs Access Control Key Card Systems What Are The Key Principles On Which Access Control Is Founded Access control consists of data and physical access protections that strengthen cybersecurity by managing users’ authentication to systems. This article explores access control, its importance in cybersecurity,. Of course, we’re talking in terms of it security here, but the same. types, importance & best practices. Only those that have had their identity verified can access. controlling who has. What Are The Key Principles On Which Access Control Is Founded.
From www.slideshare.net
Access Control Principles and Practice What Are The Key Principles On Which Access Control Is Founded access control is a method of restricting access to sensitive data. Only those that have had their identity verified can access. types, importance & best practices. what is access control? access control is a method of guaranteeing that users are who they say they are and that they have the appropriate access to. controlling who. What Are The Key Principles On Which Access Control Is Founded.
From www.slideshare.net
Access Control Principles and Practice What Are The Key Principles On Which Access Control Is Founded access control is a method of guaranteeing that users are who they say they are and that they have the appropriate access to. This article explores access control, its importance in cybersecurity,. access control is a method of restricting access to sensitive data. what is access control? Of course, we’re talking in terms of it security here,. What Are The Key Principles On Which Access Control Is Founded.
From www.slideshare.net
Access Control Principles and Practice What Are The Key Principles On Which Access Control Is Founded Access control consists of data and physical access protections that strengthen cybersecurity by managing users’ authentication to systems. Only those that have had their identity verified can access. Of course, we’re talking in terms of it security here, but the same. there are three core elements to access control. access control is a method of restricting access to. What Are The Key Principles On Which Access Control Is Founded.
From manuallistsmugglers.z21.web.core.windows.net
What Is The Function Of The Diagram What Are The Key Principles On Which Access Control Is Founded This article explores access control, its importance in cybersecurity,. types, importance & best practices. Only those that have had their identity verified can access. access control is a method of guaranteeing that users are who they say they are and that they have the appropriate access to. controlling who has access to a system and the breadth. What Are The Key Principles On Which Access Control Is Founded.
From www.slideserve.com
PPT IS3340 Windows Security Unit 2 Setting up Windows Systems with What Are The Key Principles On Which Access Control Is Founded there are three core elements to access control. access control is a method of restricting access to sensitive data. access control is a method of guaranteeing that users are who they say they are and that they have the appropriate access to. what is access control? Only those that have had their identity verified can access.. What Are The Key Principles On Which Access Control Is Founded.
From www.aiophotoz.com
What Is A Zero Trust Model In Cybersecurity And What Does It Mean For What Are The Key Principles On Which Access Control Is Founded types, importance & best practices. access control is a method of guaranteeing that users are who they say they are and that they have the appropriate access to. Of course, we’re talking in terms of it security here, but the same. Only those that have had their identity verified can access. controlling who has access to a. What Are The Key Principles On Which Access Control Is Founded.
From www.slideshare.net
Access Control Principles and Practice What Are The Key Principles On Which Access Control Is Founded access control is a method of guaranteeing that users are who they say they are and that they have the appropriate access to. Access control consists of data and physical access protections that strengthen cybersecurity by managing users’ authentication to systems. controlling who has access to a system and the breadth of access a user has is vital. What Are The Key Principles On Which Access Control Is Founded.
From www.slideserve.com
PPT Computer Security Principles and Practice PowerPoint What Are The Key Principles On Which Access Control Is Founded access control is a method of restricting access to sensitive data. what is access control? controlling who has access to a system and the breadth of access a user has is vital to ensure the security of systems and data. Access control consists of data and physical access protections that strengthen cybersecurity by managing users’ authentication to. What Are The Key Principles On Which Access Control Is Founded.
From www.security-service-edge.org
Access Control Principles in Information Security An Overview What Are The Key Principles On Which Access Control Is Founded types, importance & best practices. Of course, we’re talking in terms of it security here, but the same. there are three core elements to access control. This article explores access control, its importance in cybersecurity,. Only those that have had their identity verified can access. what is access control? controlling who has access to a system. What Are The Key Principles On Which Access Control Is Founded.
From cyberhoot.com
Access Control Mechanism CyberHoot What Are The Key Principles On Which Access Control Is Founded there are three core elements to access control. Only those that have had their identity verified can access. Access control consists of data and physical access protections that strengthen cybersecurity by managing users’ authentication to systems. what is access control? types, importance & best practices. controlling who has access to a system and the breadth of. What Are The Key Principles On Which Access Control Is Founded.
From www.techtarget.com
What is Access Control? What Are The Key Principles On Which Access Control Is Founded This article explores access control, its importance in cybersecurity,. controlling who has access to a system and the breadth of access a user has is vital to ensure the security of systems and data. Access control consists of data and physical access protections that strengthen cybersecurity by managing users’ authentication to systems. access control is a method of. What Are The Key Principles On Which Access Control Is Founded.
From www.nedapsecurity.com
The Ultimate Guide to Physical Access Control Systems in 2023 What Are The Key Principles On Which Access Control Is Founded Of course, we’re talking in terms of it security here, but the same. access control is a method of guaranteeing that users are who they say they are and that they have the appropriate access to. access control is a method of restricting access to sensitive data. controlling who has access to a system and the breadth. What Are The Key Principles On Which Access Control Is Founded.
From www.utsflorida.com
Access Control System Principles Security Camaras Miami Security What Are The Key Principles On Which Access Control Is Founded there are three core elements to access control. what is access control? Of course, we’re talking in terms of it security here, but the same. Only those that have had their identity verified can access. access control is a method of restricting access to sensitive data. This article explores access control, its importance in cybersecurity,. Access control. What Are The Key Principles On Which Access Control Is Founded.
From www.slideshare.net
Access Control Principles and Practice What Are The Key Principles On Which Access Control Is Founded Access control consists of data and physical access protections that strengthen cybersecurity by managing users’ authentication to systems. access control is a method of restricting access to sensitive data. Of course, we’re talking in terms of it security here, but the same. Only those that have had their identity verified can access. there are three core elements to. What Are The Key Principles On Which Access Control Is Founded.
From www.slideserve.com
PPT Lecture 7 Access Control PowerPoint Presentation, free download What Are The Key Principles On Which Access Control Is Founded controlling who has access to a system and the breadth of access a user has is vital to ensure the security of systems and data. there are three core elements to access control. Only those that have had their identity verified can access. what is access control? Access control consists of data and physical access protections that. What Are The Key Principles On Which Access Control Is Founded.