Aws Hardware Key . Choose your free security key from the available options. Aws cloudhsm gives you full control of the algorithms and keys you. Full control of your keys, algorithms, and application development. Provide your email address for order confirmation and your shipping address. In cloud security, one crucial component that often comes up in discussions is the hardware security module (hsm). In this article, i have demonstrated how to secure your aws sso log in. Designed to augment your security plan and protect your most sensitive assets, the free mfa security key adds an additional layer of security to protect you online. By using a hardware security key, you can make log in to and securing your aws account much easier. You can enable a hardware totp token for an iam user from the aws management console, the command line, or the iam api.
from www.aboutamazon.com
You can enable a hardware totp token for an iam user from the aws management console, the command line, or the iam api. By using a hardware security key, you can make log in to and securing your aws account much easier. Designed to augment your security plan and protect your most sensitive assets, the free mfa security key adds an additional layer of security to protect you online. In cloud security, one crucial component that often comes up in discussions is the hardware security module (hsm). Provide your email address for order confirmation and your shipping address. Full control of your keys, algorithms, and application development. Aws cloudhsm gives you full control of the algorithms and keys you. In this article, i have demonstrated how to secure your aws sso log in. Choose your free security key from the available options.
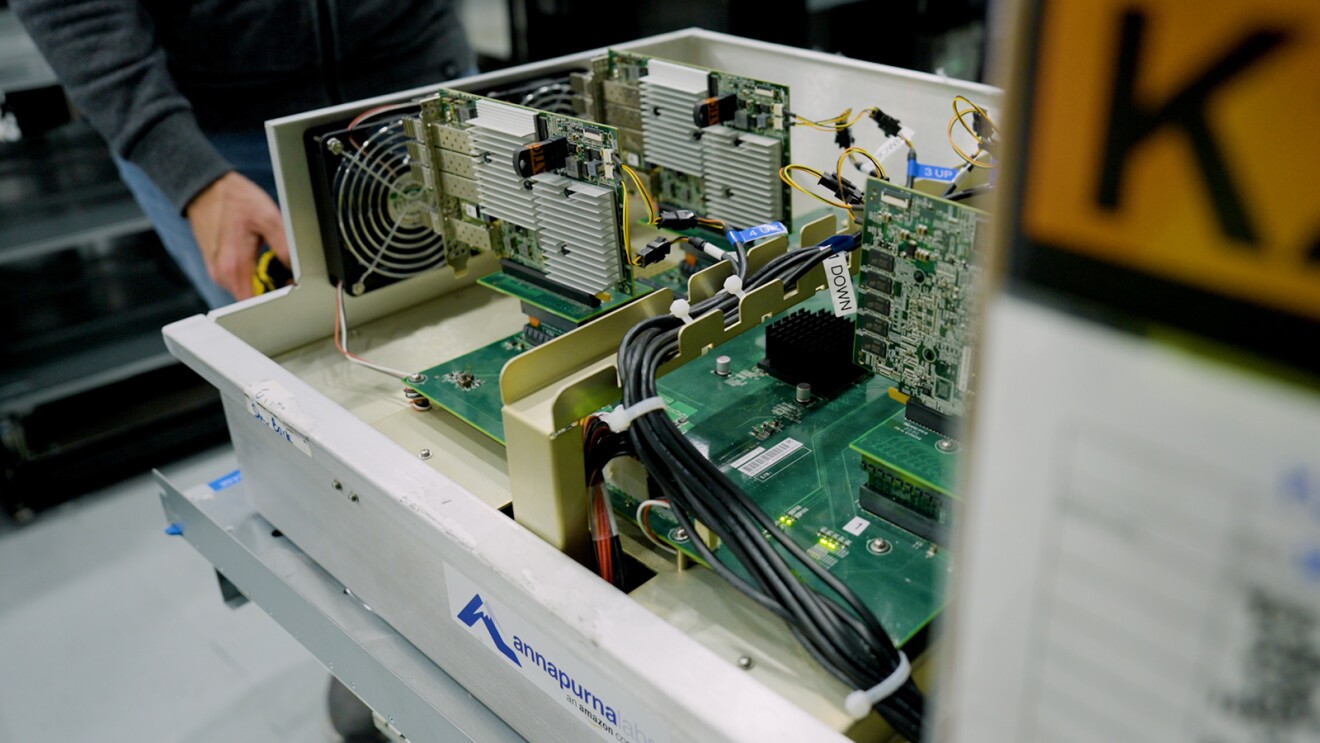
How AWS data centers reuse retired hardware
Aws Hardware Key Choose your free security key from the available options. Aws cloudhsm gives you full control of the algorithms and keys you. Full control of your keys, algorithms, and application development. In this article, i have demonstrated how to secure your aws sso log in. You can enable a hardware totp token for an iam user from the aws management console, the command line, or the iam api. Provide your email address for order confirmation and your shipping address. Designed to augment your security plan and protect your most sensitive assets, the free mfa security key adds an additional layer of security to protect you online. Choose your free security key from the available options. In cloud security, one crucial component that often comes up in discussions is the hardware security module (hsm). By using a hardware security key, you can make log in to and securing your aws account much easier.
From infosyte.com
AWS Technical Essentials Infosyte Aws Hardware Key Designed to augment your security plan and protect your most sensitive assets, the free mfa security key adds an additional layer of security to protect you online. Aws cloudhsm gives you full control of the algorithms and keys you. Full control of your keys, algorithms, and application development. You can enable a hardware totp token for an iam user from. Aws Hardware Key.
From www.codeproject.com
AWS Key Management System ( AWS KMS) to Encrypt and Decrypt Using the Aws Hardware Key Choose your free security key from the available options. Designed to augment your security plan and protect your most sensitive assets, the free mfa security key adds an additional layer of security to protect you online. You can enable a hardware totp token for an iam user from the aws management console, the command line, or the iam api. In. Aws Hardware Key.
From laptrinhx.com
Introducing Amazon ECR serverside encryption using AWS Key Management Aws Hardware Key Full control of your keys, algorithms, and application development. Choose your free security key from the available options. By using a hardware security key, you can make log in to and securing your aws account much easier. Provide your email address for order confirmation and your shipping address. In this article, i have demonstrated how to secure your aws sso. Aws Hardware Key.
From blog.jetbrains.com
AWS in IntelliJ IDEA The IntelliJ IDEA Blog Aws Hardware Key You can enable a hardware totp token for an iam user from the aws management console, the command line, or the iam api. Choose your free security key from the available options. Aws cloudhsm gives you full control of the algorithms and keys you. Designed to augment your security plan and protect your most sensitive assets, the free mfa security. Aws Hardware Key.
From www.codingninjas.com
AWS Storage Gateway Coding Ninjas Aws Hardware Key In this article, i have demonstrated how to secure your aws sso log in. Full control of your keys, algorithms, and application development. You can enable a hardware totp token for an iam user from the aws management console, the command line, or the iam api. Choose your free security key from the available options. By using a hardware security. Aws Hardware Key.
From jayendrapatil.com
AWS S3 Encryption Aws Hardware Key Choose your free security key from the available options. Aws cloudhsm gives you full control of the algorithms and keys you. Provide your email address for order confirmation and your shipping address. In cloud security, one crucial component that often comes up in discussions is the hardware security module (hsm). Designed to augment your security plan and protect your most. Aws Hardware Key.
From docs.opsramp.com
AWS MQ Broker OpsRamp Documentation Aws Hardware Key Provide your email address for order confirmation and your shipping address. Choose your free security key from the available options. In this article, i have demonstrated how to secure your aws sso log in. By using a hardware security key, you can make log in to and securing your aws account much easier. In cloud security, one crucial component that. Aws Hardware Key.
From mindmajix.com
What Is AWS KMS Functions Of AWS Key Management Service Aws Hardware Key In this article, i have demonstrated how to secure your aws sso log in. In cloud security, one crucial component that often comes up in discussions is the hardware security module (hsm). Full control of your keys, algorithms, and application development. Choose your free security key from the available options. Aws cloudhsm gives you full control of the algorithms and. Aws Hardware Key.
From sagarraodonthineni.medium.com
AWS Workspaces Overview — Part1. to my blog series on AWS Aws Hardware Key By using a hardware security key, you can make log in to and securing your aws account much easier. Designed to augment your security plan and protect your most sensitive assets, the free mfa security key adds an additional layer of security to protect you online. Provide your email address for order confirmation and your shipping address. Full control of. Aws Hardware Key.
From tutorialsdojo.com
Automatic SSH Key Pair Rotation via AWS Systems Manager Fleet Manager Aws Hardware Key Full control of your keys, algorithms, and application development. Aws cloudhsm gives you full control of the algorithms and keys you. In cloud security, one crucial component that often comes up in discussions is the hardware security module (hsm). You can enable a hardware totp token for an iam user from the aws management console, the command line, or the. Aws Hardware Key.
From infosyte.com
Architecting on AWS Accelerator Infosyte Aws Hardware Key By using a hardware security key, you can make log in to and securing your aws account much easier. Full control of your keys, algorithms, and application development. In cloud security, one crucial component that often comes up in discussions is the hardware security module (hsm). Choose your free security key from the available options. In this article, i have. Aws Hardware Key.
From teachmyselfcloud.com
Teach Myself Cloud AWS VPC Aws Hardware Key In cloud security, one crucial component that often comes up in discussions is the hardware security module (hsm). In this article, i have demonstrated how to secure your aws sso log in. Choose your free security key from the available options. Designed to augment your security plan and protect your most sensitive assets, the free mfa security key adds an. Aws Hardware Key.
From data-flair.training
What is AWS KMS Features of Key Management Services DataFlair Aws Hardware Key Full control of your keys, algorithms, and application development. Aws cloudhsm gives you full control of the algorithms and keys you. In cloud security, one crucial component that often comes up in discussions is the hardware security module (hsm). Provide your email address for order confirmation and your shipping address. You can enable a hardware totp token for an iam. Aws Hardware Key.
From aws.amazon.com
Introduction to semiconductor design workflows on AWS AWS for Industries Aws Hardware Key By using a hardware security key, you can make log in to and securing your aws account much easier. Designed to augment your security plan and protect your most sensitive assets, the free mfa security key adds an additional layer of security to protect you online. Choose your free security key from the available options. You can enable a hardware. Aws Hardware Key.
From medium.com
AWS SAA12 Amazon RDS Overview. Overview, storage auto scaling, read Aws Hardware Key Aws cloudhsm gives you full control of the algorithms and keys you. Provide your email address for order confirmation and your shipping address. Choose your free security key from the available options. Full control of your keys, algorithms, and application development. You can enable a hardware totp token for an iam user from the aws management console, the command line,. Aws Hardware Key.
From aws.amazon.com
AWS Outposts 42U rack Amazon Services Aws Hardware Key Choose your free security key from the available options. Designed to augment your security plan and protect your most sensitive assets, the free mfa security key adds an additional layer of security to protect you online. By using a hardware security key, you can make log in to and securing your aws account much easier. Full control of your keys,. Aws Hardware Key.
From profindsbazaar.com
What are {hardware} safety keys and the way do they work? ProFindsBazaar Aws Hardware Key Provide your email address for order confirmation and your shipping address. Full control of your keys, algorithms, and application development. Choose your free security key from the available options. In this article, i have demonstrated how to secure your aws sso log in. Designed to augment your security plan and protect your most sensitive assets, the free mfa security key. Aws Hardware Key.
From www.aboutamazon.com
How AWS data centers reuse retired hardware Aws Hardware Key By using a hardware security key, you can make log in to and securing your aws account much easier. In cloud security, one crucial component that often comes up in discussions is the hardware security module (hsm). Aws cloudhsm gives you full control of the algorithms and keys you. In this article, i have demonstrated how to secure your aws. Aws Hardware Key.
From www.awsjunkie.com
Test and Debug AWS CodeBuild Builds Locally using AWS CodeBuild agent Aws Hardware Key Provide your email address for order confirmation and your shipping address. Full control of your keys, algorithms, and application development. Aws cloudhsm gives you full control of the algorithms and keys you. In this article, i have demonstrated how to secure your aws sso log in. Choose your free security key from the available options. In cloud security, one crucial. Aws Hardware Key.
From josetran248rumor.blogspot.com
Jose Tran Rumor Aws Download Key Pair Aws Hardware Key Choose your free security key from the available options. You can enable a hardware totp token for an iam user from the aws management console, the command line, or the iam api. Aws cloudhsm gives you full control of the algorithms and keys you. In this article, i have demonstrated how to secure your aws sso log in. Full control. Aws Hardware Key.
From lifesciences-resources.awscloud.com
Expanded availability and streamlined ordering of the AWS Storage Aws Hardware Key Choose your free security key from the available options. Aws cloudhsm gives you full control of the algorithms and keys you. Designed to augment your security plan and protect your most sensitive assets, the free mfa security key adds an additional layer of security to protect you online. Provide your email address for order confirmation and your shipping address. You. Aws Hardware Key.
From zhenye-na.github.io
AWS Security and Encryption AWS Cert. Cheatsheet Aws Hardware Key Choose your free security key from the available options. By using a hardware security key, you can make log in to and securing your aws account much easier. Full control of your keys, algorithms, and application development. In this article, i have demonstrated how to secure your aws sso log in. In cloud security, one crucial component that often comes. Aws Hardware Key.
From paladincloud.io
How to rotate keys with AWS KMS Paladin Cloud Aws Hardware Key Provide your email address for order confirmation and your shipping address. In cloud security, one crucial component that often comes up in discussions is the hardware security module (hsm). Full control of your keys, algorithms, and application development. You can enable a hardware totp token for an iam user from the aws management console, the command line, or the iam. Aws Hardware Key.
From docs.aws.amazon.com
Navigating the AWS Toolkit for JetBrains AWS Toolkit for JetBrains Aws Hardware Key Full control of your keys, algorithms, and application development. Designed to augment your security plan and protect your most sensitive assets, the free mfa security key adds an additional layer of security to protect you online. Choose your free security key from the available options. You can enable a hardware totp token for an iam user from the aws management. Aws Hardware Key.
From www.filestash.app
How to create your AWS access Key ID and AWS Secret Access key Aws Hardware Key Designed to augment your security plan and protect your most sensitive assets, the free mfa security key adds an additional layer of security to protect you online. You can enable a hardware totp token for an iam user from the aws management console, the command line, or the iam api. In this article, i have demonstrated how to secure your. Aws Hardware Key.
From noodls.com
AWS CDK Structure Components Noodls Aws Hardware Key By using a hardware security key, you can make log in to and securing your aws account much easier. Provide your email address for order confirmation and your shipping address. In this article, i have demonstrated how to secure your aws sso log in. Choose your free security key from the available options. In cloud security, one crucial component that. Aws Hardware Key.
From digitalcloud.training
AWS KMS AWS Cheat Sheet Aws Hardware Key In this article, i have demonstrated how to secure your aws sso log in. You can enable a hardware totp token for an iam user from the aws management console, the command line, or the iam api. Provide your email address for order confirmation and your shipping address. Aws cloudhsm gives you full control of the algorithms and keys you.. Aws Hardware Key.
From hiwanglong.github.io
AWS Solutions Architect Associate2 Data Security Aws Hardware Key By using a hardware security key, you can make log in to and securing your aws account much easier. Choose your free security key from the available options. Aws cloudhsm gives you full control of the algorithms and keys you. In cloud security, one crucial component that often comes up in discussions is the hardware security module (hsm). Full control. Aws Hardware Key.
From aws.amazon.com
AWS Outposts Hardware Specs Aws Hardware Key Provide your email address for order confirmation and your shipping address. In cloud security, one crucial component that often comes up in discussions is the hardware security module (hsm). Choose your free security key from the available options. You can enable a hardware totp token for an iam user from the aws management console, the command line, or the iam. Aws Hardware Key.
From thichnaunuong.com
What Is Aws Access Key And Secret Key Your Essential Guide Aws Hardware Key Full control of your keys, algorithms, and application development. Provide your email address for order confirmation and your shipping address. You can enable a hardware totp token for an iam user from the aws management console, the command line, or the iam api. By using a hardware security key, you can make log in to and securing your aws account. Aws Hardware Key.
From www.amazon.com
Yubico 安全金鑰 NFC 黑色 雙因素驗證 (2FA) 安全金鑰,透過 USBA 或 NFC 連接 Aws Hardware Key Choose your free security key from the available options. In cloud security, one crucial component that often comes up in discussions is the hardware security module (hsm). You can enable a hardware totp token for an iam user from the aws management console, the command line, or the iam api. By using a hardware security key, you can make log. Aws Hardware Key.
From aws.amazon.com
New AWS Storage Gateway Hardware Appliance AWS News Blog Aws Hardware Key In cloud security, one crucial component that often comes up in discussions is the hardware security module (hsm). Designed to augment your security plan and protect your most sensitive assets, the free mfa security key adds an additional layer of security to protect you online. Full control of your keys, algorithms, and application development. Provide your email address for order. Aws Hardware Key.
From www.pinterest.com
Pin on Software Science Aws Hardware Key Full control of your keys, algorithms, and application development. Designed to augment your security plan and protect your most sensitive assets, the free mfa security key adds an additional layer of security to protect you online. In cloud security, one crucial component that often comes up in discussions is the hardware security module (hsm). Choose your free security key from. Aws Hardware Key.
From aws.amazon.com
CloudHSM best practices to maximize performance and avoid common Aws Hardware Key Full control of your keys, algorithms, and application development. You can enable a hardware totp token for an iam user from the aws management console, the command line, or the iam api. In cloud security, one crucial component that often comes up in discussions is the hardware security module (hsm). By using a hardware security key, you can make log. Aws Hardware Key.
From aws.amazon.com
Use Key Management Service (AWS KMS) to securely manage Ethereum Aws Hardware Key You can enable a hardware totp token for an iam user from the aws management console, the command line, or the iam api. Choose your free security key from the available options. By using a hardware security key, you can make log in to and securing your aws account much easier. Aws cloudhsm gives you full control of the algorithms. Aws Hardware Key.