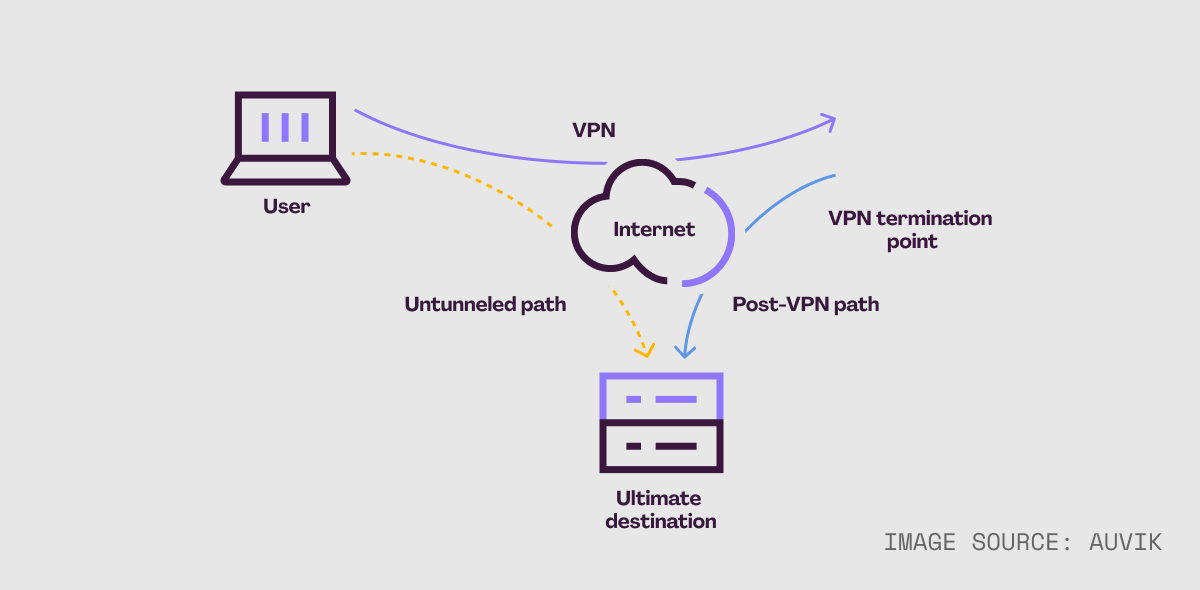
Tunnel Vpn Point . Let’s take a closer look at the most popular vpn tunnel types and when you should use. The vpn tunnel encrypts the user’s internet traffic and. There are several vpn tunnel types, each with its own strength. The vpn tunnel creates a private pathway,. A vpn tunnel is a secure, encrypted connection between a user’s device and the internet through a virtual private network. A vpn tunnel is a secure, encrypted connection between a network device and a vpn server that safeguards data transfer over the internet. It encrypts data at the source, sends it through a virtual tunnel, and decrypts it at the. It operates by using a tcp. A tls vpn solution can penetrate firewalls, since most firewalls open tcp port 443. Vpn tunneling securely extends a private network across the internet.
from www.auvik.com
It encrypts data at the source, sends it through a virtual tunnel, and decrypts it at the. Let’s take a closer look at the most popular vpn tunnel types and when you should use. There are several vpn tunnel types, each with its own strength. A tls vpn solution can penetrate firewalls, since most firewalls open tcp port 443. It operates by using a tcp. The vpn tunnel encrypts the user’s internet traffic and. A vpn tunnel is a secure, encrypted connection between a network device and a vpn server that safeguards data transfer over the internet. Vpn tunneling securely extends a private network across the internet. The vpn tunnel creates a private pathway,. A vpn tunnel is a secure, encrypted connection between a user’s device and the internet through a virtual private network.
VPN Split Tunneling What It Is & Pros and Cons Auvik
Tunnel Vpn Point The vpn tunnel encrypts the user’s internet traffic and. Let’s take a closer look at the most popular vpn tunnel types and when you should use. A tls vpn solution can penetrate firewalls, since most firewalls open tcp port 443. There are several vpn tunnel types, each with its own strength. Vpn tunneling securely extends a private network across the internet. It operates by using a tcp. It encrypts data at the source, sends it through a virtual tunnel, and decrypts it at the. The vpn tunnel creates a private pathway,. A vpn tunnel is a secure, encrypted connection between a network device and a vpn server that safeguards data transfer over the internet. A vpn tunnel is a secure, encrypted connection between a user’s device and the internet through a virtual private network. The vpn tunnel encrypts the user’s internet traffic and.
From napkforpc.com
RDM Tunnel VPN Unlimited Net for PC / Mac / Windows 11,10,8,7 Free Tunnel Vpn Point It operates by using a tcp. There are several vpn tunnel types, each with its own strength. It encrypts data at the source, sends it through a virtual tunnel, and decrypts it at the. A vpn tunnel is a secure, encrypted connection between a network device and a vpn server that safeguards data transfer over the internet. Vpn tunneling securely. Tunnel Vpn Point.
From www.youtube.com
VPN Tunneling and VPN Tunneling Protocols Explained YouTube Tunnel Vpn Point There are several vpn tunnel types, each with its own strength. A vpn tunnel is a secure, encrypted connection between a user’s device and the internet through a virtual private network. Let’s take a closer look at the most popular vpn tunnel types and when you should use. The vpn tunnel creates a private pathway,. It operates by using a. Tunnel Vpn Point.
From www.youtube.com
Configuring a PointtoPoint GRE VPN Tunnel, Packet Tracer v 7.2 YouTube Tunnel Vpn Point A vpn tunnel is a secure, encrypted connection between a user’s device and the internet through a virtual private network. Let’s take a closer look at the most popular vpn tunnel types and when you should use. A tls vpn solution can penetrate firewalls, since most firewalls open tcp port 443. There are several vpn tunnel types, each with its. Tunnel Vpn Point.
From update-tutorials.blogspot.com
update tutorials Tutorial Mikrotik VPN Point to Point Tunnel Tunnel Vpn Point It encrypts data at the source, sends it through a virtual tunnel, and decrypts it at the. A tls vpn solution can penetrate firewalls, since most firewalls open tcp port 443. It operates by using a tcp. The vpn tunnel encrypts the user’s internet traffic and. A vpn tunnel is a secure, encrypted connection between a network device and a. Tunnel Vpn Point.
From kreyda.blogspot.com
kreyda Creating Check Point VPNtunnel for Remote Access users. Tunnel Vpn Point The vpn tunnel creates a private pathway,. A tls vpn solution can penetrate firewalls, since most firewalls open tcp port 443. Vpn tunneling securely extends a private network across the internet. It operates by using a tcp. The vpn tunnel encrypts the user’s internet traffic and. There are several vpn tunnel types, each with its own strength. A vpn tunnel. Tunnel Vpn Point.
From ccnapoint.com
How to configure a Basic VPN with Packet Tracer(GRE Tunneling)? CCNA Tunnel Vpn Point It encrypts data at the source, sends it through a virtual tunnel, and decrypts it at the. The vpn tunnel creates a private pathway,. Vpn tunneling securely extends a private network across the internet. It operates by using a tcp. The vpn tunnel encrypts the user’s internet traffic and. Let’s take a closer look at the most popular vpn tunnel. Tunnel Vpn Point.
From info-firewalls.s4x18.com
Vpn Tunnels Explained What Are They And How Can Firewalls Tunnel Vpn Point A vpn tunnel is a secure, encrypted connection between a user’s device and the internet through a virtual private network. The vpn tunnel encrypts the user’s internet traffic and. The vpn tunnel creates a private pathway,. Vpn tunneling securely extends a private network across the internet. It operates by using a tcp. There are several vpn tunnel types, each with. Tunnel Vpn Point.
From itexamanswers.net
3.4.2.6 Lab Configuring a PointtoPoint GRE VPN Tunnel Answers Tunnel Vpn Point The vpn tunnel encrypts the user’s internet traffic and. A tls vpn solution can penetrate firewalls, since most firewalls open tcp port 443. It operates by using a tcp. It encrypts data at the source, sends it through a virtual tunnel, and decrypts it at the. Vpn tunneling securely extends a private network across the internet. Let’s take a closer. Tunnel Vpn Point.
From wethegeek.com
What Is A VPN Tunnel & How Does It Work Tunnel Vpn Point A tls vpn solution can penetrate firewalls, since most firewalls open tcp port 443. It operates by using a tcp. A vpn tunnel is a secure, encrypted connection between a network device and a vpn server that safeguards data transfer over the internet. The vpn tunnel encrypts the user’s internet traffic and. Let’s take a closer look at the most. Tunnel Vpn Point.
From www.artofit.org
What is a vpn tunnel Artofit Tunnel Vpn Point The vpn tunnel creates a private pathway,. A vpn tunnel is a secure, encrypted connection between a network device and a vpn server that safeguards data transfer over the internet. There are several vpn tunnel types, each with its own strength. It operates by using a tcp. A tls vpn solution can penetrate firewalls, since most firewalls open tcp port. Tunnel Vpn Point.
From www.wiresandwi.fi
Check Point SitetoSite VPN Tunnel (DomainBased) — WIRES AND WI.FI Tunnel Vpn Point The vpn tunnel encrypts the user’s internet traffic and. A tls vpn solution can penetrate firewalls, since most firewalls open tcp port 443. A vpn tunnel is a secure, encrypted connection between a user’s device and the internet through a virtual private network. It operates by using a tcp. Vpn tunneling securely extends a private network across the internet. The. Tunnel Vpn Point.
From thunder.catapultsports.com
VPN Split Tunneling Overview Catapult Thunder Support Tunnel Vpn Point The vpn tunnel encrypts the user’s internet traffic and. It operates by using a tcp. A tls vpn solution can penetrate firewalls, since most firewalls open tcp port 443. It encrypts data at the source, sends it through a virtual tunnel, and decrypts it at the. There are several vpn tunnel types, each with its own strength. Vpn tunneling securely. Tunnel Vpn Point.
From www.vrogue.co
How To Setup Vpn Tunnel Between Mikrotik And Cisco Ro vrogue.co Tunnel Vpn Point The vpn tunnel encrypts the user’s internet traffic and. It encrypts data at the source, sends it through a virtual tunnel, and decrypts it at the. A vpn tunnel is a secure, encrypted connection between a user’s device and the internet through a virtual private network. Vpn tunneling securely extends a private network across the internet. It operates by using. Tunnel Vpn Point.
From bulkyvpn.com
What is a VPN tunnel and how does it work? Tunnel Vpn Point The vpn tunnel creates a private pathway,. A tls vpn solution can penetrate firewalls, since most firewalls open tcp port 443. Vpn tunneling securely extends a private network across the internet. It operates by using a tcp. The vpn tunnel encrypts the user’s internet traffic and. Let’s take a closer look at the most popular vpn tunnel types and when. Tunnel Vpn Point.
From slideplayer.com
Virtual Private Network zswu ppt download Tunnel Vpn Point A vpn tunnel is a secure, encrypted connection between a user’s device and the internet through a virtual private network. There are several vpn tunnel types, each with its own strength. The vpn tunnel creates a private pathway,. A vpn tunnel is a secure, encrypted connection between a network device and a vpn server that safeguards data transfer over the. Tunnel Vpn Point.
From coursehohpa.weebly.com
Check point vpn tunnel latency coursehohpa Tunnel Vpn Point It operates by using a tcp. A tls vpn solution can penetrate firewalls, since most firewalls open tcp port 443. It encrypts data at the source, sends it through a virtual tunnel, and decrypts it at the. There are several vpn tunnel types, each with its own strength. A vpn tunnel is a secure, encrypted connection between a user’s device. Tunnel Vpn Point.
From openvpn.net
Site To Site VPN Routing Explained In Detail OpenVPN Tunnel Vpn Point It operates by using a tcp. A tls vpn solution can penetrate firewalls, since most firewalls open tcp port 443. It encrypts data at the source, sends it through a virtual tunnel, and decrypts it at the. The vpn tunnel creates a private pathway,. The vpn tunnel encrypts the user’s internet traffic and. There are several vpn tunnel types, each. Tunnel Vpn Point.
From lasopaviewer688.weebly.com
Azure point to site vpn force tunneling lasopaviewer Tunnel Vpn Point It operates by using a tcp. It encrypts data at the source, sends it through a virtual tunnel, and decrypts it at the. The vpn tunnel encrypts the user’s internet traffic and. Vpn tunneling securely extends a private network across the internet. A vpn tunnel is a secure, encrypted connection between a network device and a vpn server that safeguards. Tunnel Vpn Point.
From clearvpn.com
What Is a VPN Tunnel And How It Works ClearVPN Tunnel Vpn Point A vpn tunnel is a secure, encrypted connection between a network device and a vpn server that safeguards data transfer over the internet. A tls vpn solution can penetrate firewalls, since most firewalls open tcp port 443. There are several vpn tunnel types, each with its own strength. Vpn tunneling securely extends a private network across the internet. Let’s take. Tunnel Vpn Point.
From techgenix.com
An Introductory Guide to the PointtoPoint Tunneling Protocol (PPTP) Tunnel Vpn Point A vpn tunnel is a secure, encrypted connection between a network device and a vpn server that safeguards data transfer over the internet. A vpn tunnel is a secure, encrypted connection between a user’s device and the internet through a virtual private network. Let’s take a closer look at the most popular vpn tunnel types and when you should use.. Tunnel Vpn Point.
From documentation.meraki.com
SSID Tunneling and Layer 3 Roaming VPN Concentration Configuration Tunnel Vpn Point Let’s take a closer look at the most popular vpn tunnel types and when you should use. A tls vpn solution can penetrate firewalls, since most firewalls open tcp port 443. A vpn tunnel is a secure, encrypted connection between a network device and a vpn server that safeguards data transfer over the internet. It operates by using a tcp.. Tunnel Vpn Point.
From play.google.com
TM Tunnel Fast, Secure VPN Apps on Google Play Tunnel Vpn Point The vpn tunnel creates a private pathway,. A vpn tunnel is a secure, encrypted connection between a network device and a vpn server that safeguards data transfer over the internet. A tls vpn solution can penetrate firewalls, since most firewalls open tcp port 443. It encrypts data at the source, sends it through a virtual tunnel, and decrypts it at. Tunnel Vpn Point.
From coursehohpa.weebly.com
Check point vpn tunnel latency coursehohpa Tunnel Vpn Point There are several vpn tunnel types, each with its own strength. Vpn tunneling securely extends a private network across the internet. The vpn tunnel creates a private pathway,. A vpn tunnel is a secure, encrypted connection between a user’s device and the internet through a virtual private network. It operates by using a tcp. A tls vpn solution can penetrate. Tunnel Vpn Point.
From www.wiresandwi.fi
Check Point SitetoSite VPN Tunnel (DomainBased) — WIRES AND WI.FI Tunnel Vpn Point It operates by using a tcp. A tls vpn solution can penetrate firewalls, since most firewalls open tcp port 443. The vpn tunnel encrypts the user’s internet traffic and. A vpn tunnel is a secure, encrypted connection between a user’s device and the internet through a virtual private network. There are several vpn tunnel types, each with its own strength.. Tunnel Vpn Point.
From buananetpbun.github.io
VPN Tunnel All Traffic Script Generator For Mikrotik Routeros Tunnel Vpn Point Let’s take a closer look at the most popular vpn tunnel types and when you should use. It encrypts data at the source, sends it through a virtual tunnel, and decrypts it at the. A tls vpn solution can penetrate firewalls, since most firewalls open tcp port 443. Vpn tunneling securely extends a private network across the internet. It operates. Tunnel Vpn Point.
From diengcyber.com
Apa itu PointtoPoint Tunneling Protocol PT DIENG CYBER INDONESIA Tunnel Vpn Point The vpn tunnel encrypts the user’s internet traffic and. Vpn tunneling securely extends a private network across the internet. There are several vpn tunnel types, each with its own strength. It operates by using a tcp. A vpn tunnel is a secure, encrypted connection between a user’s device and the internet through a virtual private network. Let’s take a closer. Tunnel Vpn Point.
From www.comparitech.com
What is VPN Tunneling? A complete guide to VPN Tunneling Tunnel Vpn Point It operates by using a tcp. Let’s take a closer look at the most popular vpn tunnel types and when you should use. A tls vpn solution can penetrate firewalls, since most firewalls open tcp port 443. The vpn tunnel encrypts the user’s internet traffic and. It encrypts data at the source, sends it through a virtual tunnel, and decrypts. Tunnel Vpn Point.
From www.draytek.com.tw
Make specific host use VPN tunnel as the default gateway DrayTek Tunnel Vpn Point Let’s take a closer look at the most popular vpn tunnel types and when you should use. The vpn tunnel encrypts the user’s internet traffic and. A tls vpn solution can penetrate firewalls, since most firewalls open tcp port 443. A vpn tunnel is a secure, encrypted connection between a network device and a vpn server that safeguards data transfer. Tunnel Vpn Point.
From www.linksys.com
Linksys Official Support Setting up a VPN Tunnel on two (2) routers Tunnel Vpn Point A vpn tunnel is a secure, encrypted connection between a network device and a vpn server that safeguards data transfer over the internet. There are several vpn tunnel types, each with its own strength. Let’s take a closer look at the most popular vpn tunnel types and when you should use. Vpn tunneling securely extends a private network across the. Tunnel Vpn Point.
From www.auvik.com
VPN Split Tunneling What It Is & Pros and Cons Auvik Tunnel Vpn Point There are several vpn tunnel types, each with its own strength. Vpn tunneling securely extends a private network across the internet. A tls vpn solution can penetrate firewalls, since most firewalls open tcp port 443. A vpn tunnel is a secure, encrypted connection between a user’s device and the internet through a virtual private network. A vpn tunnel is a. Tunnel Vpn Point.
From grayhohpa.weebly.com
Reset check point vpn tunnel command line grayhohpa Tunnel Vpn Point There are several vpn tunnel types, each with its own strength. A tls vpn solution can penetrate firewalls, since most firewalls open tcp port 443. The vpn tunnel creates a private pathway,. The vpn tunnel encrypts the user’s internet traffic and. It operates by using a tcp. It encrypts data at the source, sends it through a virtual tunnel, and. Tunnel Vpn Point.
From zonacel.net
Cómo configurar una red VPN en tu dispositivo móvil Tunnel Vpn Point There are several vpn tunnel types, each with its own strength. The vpn tunnel creates a private pathway,. Vpn tunneling securely extends a private network across the internet. It encrypts data at the source, sends it through a virtual tunnel, and decrypts it at the. It operates by using a tcp. A tls vpn solution can penetrate firewalls, since most. Tunnel Vpn Point.
From ccnadesdecero.es
Explicación del PPTP (Point to Point Tunneling Protocol) » Redes Tunnel Vpn Point A vpn tunnel is a secure, encrypted connection between a user’s device and the internet through a virtual private network. The vpn tunnel encrypts the user’s internet traffic and. It operates by using a tcp. It encrypts data at the source, sends it through a virtual tunnel, and decrypts it at the. The vpn tunnel creates a private pathway,. Vpn. Tunnel Vpn Point.
From www.scribd.com
Configuring a PointToPoint GRE VPN Tunnel Virtual Private Network Tunnel Vpn Point The vpn tunnel creates a private pathway,. A tls vpn solution can penetrate firewalls, since most firewalls open tcp port 443. There are several vpn tunnel types, each with its own strength. Let’s take a closer look at the most popular vpn tunnel types and when you should use. It operates by using a tcp. A vpn tunnel is a. Tunnel Vpn Point.
From help.ui.com
Intro to Networking Virtual Private Networks & Tunneling Ubiquiti Tunnel Vpn Point A tls vpn solution can penetrate firewalls, since most firewalls open tcp port 443. A vpn tunnel is a secure, encrypted connection between a network device and a vpn server that safeguards data transfer over the internet. It operates by using a tcp. A vpn tunnel is a secure, encrypted connection between a user’s device and the internet through a. Tunnel Vpn Point.