Form Based Authentication For Rest Api . — today, we’re going to cover everything you need to know about working with the most common rest api authentication methods. in this article, we’ll cover one very powerful yet simple way to secure a rest api using json web tokens (jwt), reviewing some best practices and. rest api authentication is a process used to authenticate users and applications when making api requests. In this article, we’ll discuss the different. — in this article, we will explore the fundamentals of securing restful apis with a focus on authentication and authorization, using java,. api authentication is a primary way in which apis are secured, and it enables teams to protect sensitive data, build trust with.
from support.kemptechnologies.com
In this article, we’ll discuss the different. api authentication is a primary way in which apis are secured, and it enables teams to protect sensitive data, build trust with. — today, we’re going to cover everything you need to know about working with the most common rest api authentication methods. in this article, we’ll cover one very powerful yet simple way to secure a rest api using json web tokens (jwt), reviewing some best practices and. rest api authentication is a process used to authenticate users and applications when making api requests. — in this article, we will explore the fundamentals of securing restful apis with a focus on authentication and authorization, using java,.
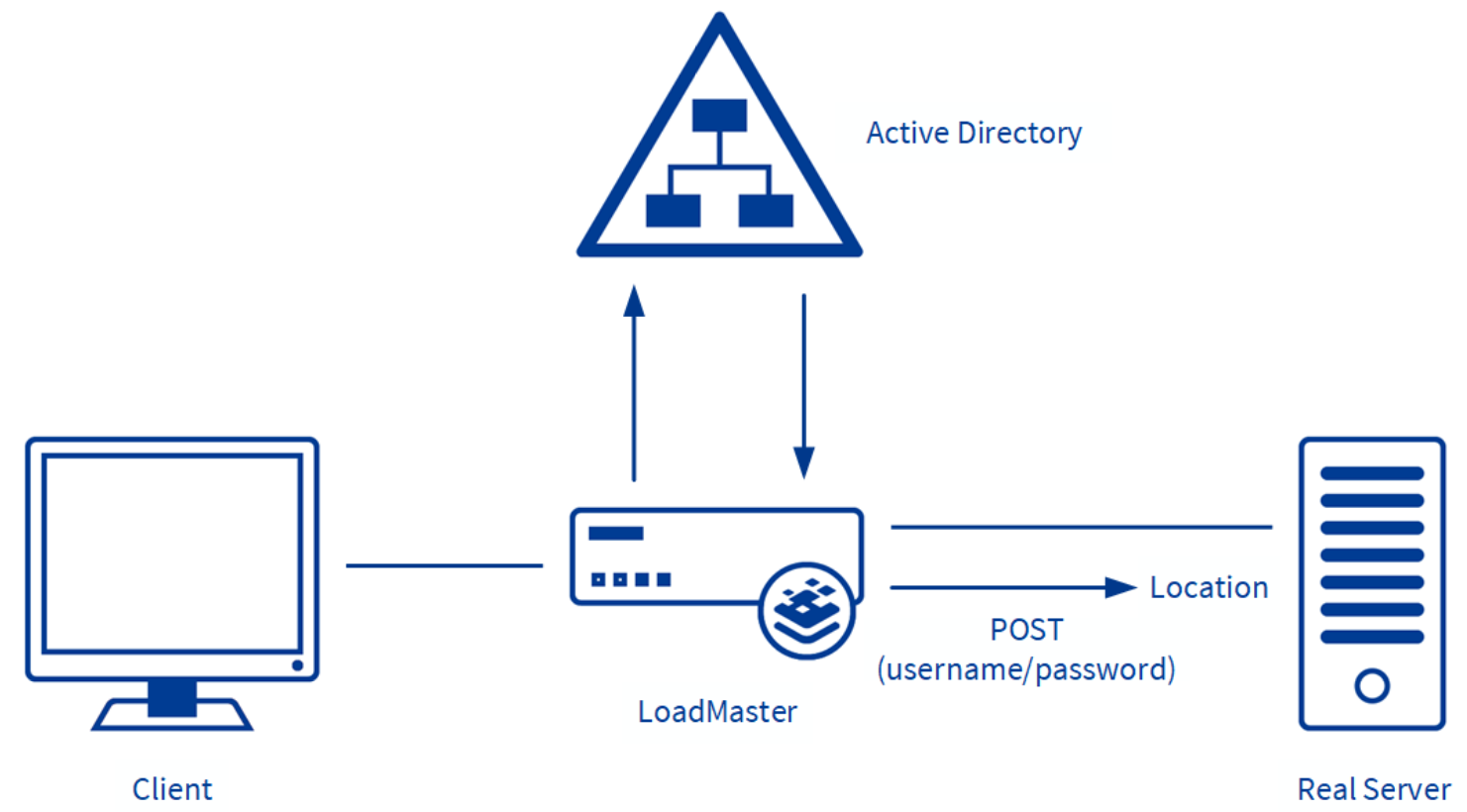
Form based to Form based Authentication Kemp Support
Form Based Authentication For Rest Api — today, we’re going to cover everything you need to know about working with the most common rest api authentication methods. — in this article, we will explore the fundamentals of securing restful apis with a focus on authentication and authorization, using java,. — today, we’re going to cover everything you need to know about working with the most common rest api authentication methods. In this article, we’ll discuss the different. in this article, we’ll cover one very powerful yet simple way to secure a rest api using json web tokens (jwt), reviewing some best practices and. rest api authentication is a process used to authenticate users and applications when making api requests. api authentication is a primary way in which apis are secured, and it enables teams to protect sensitive data, build trust with.
From dotnettutorials.net
Form Based Authentication in JSP Dot Net Tutorials Form Based Authentication For Rest Api In this article, we’ll discuss the different. rest api authentication is a process used to authenticate users and applications when making api requests. — today, we’re going to cover everything you need to know about working with the most common rest api authentication methods. api authentication is a primary way in which apis are secured, and it. Form Based Authentication For Rest Api.
From wideskills.com
Authentication and Authorization in tutorial by Form Based Authentication For Rest Api In this article, we’ll discuss the different. in this article, we’ll cover one very powerful yet simple way to secure a rest api using json web tokens (jwt), reviewing some best practices and. — in this article, we will explore the fundamentals of securing restful apis with a focus on authentication and authorization, using java,. rest api. Form Based Authentication For Rest Api.
From blog.restcase.com
4 Most Used REST API Authentication Methods Form Based Authentication For Rest Api — today, we’re going to cover everything you need to know about working with the most common rest api authentication methods. In this article, we’ll discuss the different. in this article, we’ll cover one very powerful yet simple way to secure a rest api using json web tokens (jwt), reviewing some best practices and. rest api authentication. Form Based Authentication For Rest Api.
From www.ksathra.com
2. Fundamental essentials for (RESTful) API design and configurations Form Based Authentication For Rest Api in this article, we’ll cover one very powerful yet simple way to secure a rest api using json web tokens (jwt), reviewing some best practices and. rest api authentication is a process used to authenticate users and applications when making api requests. api authentication is a primary way in which apis are secured, and it enables teams. Form Based Authentication For Rest Api.
From www.cubedrive.com
REST APIs Form Based Authentication For Rest Api api authentication is a primary way in which apis are secured, and it enables teams to protect sensitive data, build trust with. — today, we’re going to cover everything you need to know about working with the most common rest api authentication methods. rest api authentication is a process used to authenticate users and applications when making. Form Based Authentication For Rest Api.
From lo-victoria.com
Introduction to REST API Authentication Methods Form Based Authentication For Rest Api In this article, we’ll discuss the different. rest api authentication is a process used to authenticate users and applications when making api requests. api authentication is a primary way in which apis are secured, and it enables teams to protect sensitive data, build trust with. — today, we’re going to cover everything you need to know about. Form Based Authentication For Rest Api.
From medium.com
REST — Basic and Form based authentication by Phani Kumar Medium Form Based Authentication For Rest Api in this article, we’ll cover one very powerful yet simple way to secure a rest api using json web tokens (jwt), reviewing some best practices and. — in this article, we will explore the fundamentals of securing restful apis with a focus on authentication and authorization, using java,. rest api authentication is a process used to authenticate. Form Based Authentication For Rest Api.
From medium.com
REST — Basic and Form based authentication Phani Kumar Medium Form Based Authentication For Rest Api api authentication is a primary way in which apis are secured, and it enables teams to protect sensitive data, build trust with. — in this article, we will explore the fundamentals of securing restful apis with a focus on authentication and authorization, using java,. in this article, we’ll cover one very powerful yet simple way to secure. Form Based Authentication For Rest Api.
From dzone.com
API Authentication Methods An Overview DZone Form Based Authentication For Rest Api — today, we’re going to cover everything you need to know about working with the most common rest api authentication methods. in this article, we’ll cover one very powerful yet simple way to secure a rest api using json web tokens (jwt), reviewing some best practices and. In this article, we’ll discuss the different. api authentication is. Form Based Authentication For Rest Api.
From rapidapi.com
React API Authorization Implement Authentication & Authorization in Form Based Authentication For Rest Api rest api authentication is a process used to authenticate users and applications when making api requests. — today, we’re going to cover everything you need to know about working with the most common rest api authentication methods. In this article, we’ll discuss the different. — in this article, we will explore the fundamentals of securing restful apis. Form Based Authentication For Rest Api.
From exovfnasl.blob.core.windows.net
Forms Authentication Userdata at Justin Gibson blog Form Based Authentication For Rest Api in this article, we’ll cover one very powerful yet simple way to secure a rest api using json web tokens (jwt), reviewing some best practices and. — today, we’re going to cover everything you need to know about working with the most common rest api authentication methods. rest api authentication is a process used to authenticate users. Form Based Authentication For Rest Api.
From www.bezkoder.com
Spring Boot + React JWT Authentication with Spring Security BezKoder Form Based Authentication For Rest Api — in this article, we will explore the fundamentals of securing restful apis with a focus on authentication and authorization, using java,. rest api authentication is a process used to authenticate users and applications when making api requests. In this article, we’ll discuss the different. — today, we’re going to cover everything you need to know about. Form Based Authentication For Rest Api.
From www.youtube.com
API Authentication via API Keys AWS API Gateway YouTube Form Based Authentication For Rest Api — in this article, we will explore the fundamentals of securing restful apis with a focus on authentication and authorization, using java,. in this article, we’ll cover one very powerful yet simple way to secure a rest api using json web tokens (jwt), reviewing some best practices and. rest api authentication is a process used to authenticate. Form Based Authentication For Rest Api.
From www.middlewareinventory.com
Sample Java Application with FormBased Authentication Step by Step Form Based Authentication For Rest Api In this article, we’ll discuss the different. — in this article, we will explore the fundamentals of securing restful apis with a focus on authentication and authorization, using java,. — today, we’re going to cover everything you need to know about working with the most common rest api authentication methods. in this article, we’ll cover one very. Form Based Authentication For Rest Api.
From mlsdev.com
A Beginner's Tutorial for Understanding RESTful API [MLSDev] Form Based Authentication For Rest Api rest api authentication is a process used to authenticate users and applications when making api requests. in this article, we’ll cover one very powerful yet simple way to secure a rest api using json web tokens (jwt), reviewing some best practices and. api authentication is a primary way in which apis are secured, and it enables teams. Form Based Authentication For Rest Api.
From www.infobeans.com
Forms Based Authentication with External ADDS InfoBeans Form Based Authentication For Rest Api — today, we’re going to cover everything you need to know about working with the most common rest api authentication methods. api authentication is a primary way in which apis are secured, and it enables teams to protect sensitive data, build trust with. rest api authentication is a process used to authenticate users and applications when making. Form Based Authentication For Rest Api.
From www.bezkoder.com
Spring Boot 2 JWT Authentication with Spring Security BezKoder Form Based Authentication For Rest Api In this article, we’ll discuss the different. api authentication is a primary way in which apis are secured, and it enables teams to protect sensitive data, build trust with. — in this article, we will explore the fundamentals of securing restful apis with a focus on authentication and authorization, using java,. — today, we’re going to cover. Form Based Authentication For Rest Api.
From securityboulevard.com
Common REST API Authentication Methods Explained Security Boulevard Form Based Authentication For Rest Api — in this article, we will explore the fundamentals of securing restful apis with a focus on authentication and authorization, using java,. api authentication is a primary way in which apis are secured, and it enables teams to protect sensitive data, build trust with. in this article, we’ll cover one very powerful yet simple way to secure. Form Based Authentication For Rest Api.
From itecnotes.com
Rest Authentication setup advice for web app and its backend API Form Based Authentication For Rest Api api authentication is a primary way in which apis are secured, and it enables teams to protect sensitive data, build trust with. — in this article, we will explore the fundamentals of securing restful apis with a focus on authentication and authorization, using java,. In this article, we’ll discuss the different. in this article, we’ll cover one. Form Based Authentication For Rest Api.
From schematicpaliza06.z22.web.core.windows.net
Restful Api Diagram Form Based Authentication For Rest Api — today, we’re going to cover everything you need to know about working with the most common rest api authentication methods. api authentication is a primary way in which apis are secured, and it enables teams to protect sensitive data, build trust with. In this article, we’ll discuss the different. rest api authentication is a process used. Form Based Authentication For Rest Api.
From apifriends.com
API Keys versus OAuth How to secure your APIs? Form Based Authentication For Rest Api In this article, we’ll discuss the different. api authentication is a primary way in which apis are secured, and it enables teams to protect sensitive data, build trust with. rest api authentication is a process used to authenticate users and applications when making api requests. in this article, we’ll cover one very powerful yet simple way to. Form Based Authentication For Rest Api.
From www.youtube.com
Overview of the REST API basics YouTube Form Based Authentication For Rest Api — today, we’re going to cover everything you need to know about working with the most common rest api authentication methods. In this article, we’ll discuss the different. — in this article, we will explore the fundamentals of securing restful apis with a focus on authentication and authorization, using java,. in this article, we’ll cover one very. Form Based Authentication For Rest Api.
From printableformsfree.com
How To Use Basic Authentication In Rest Api Postman Printable Forms Form Based Authentication For Rest Api rest api authentication is a process used to authenticate users and applications when making api requests. — today, we’re going to cover everything you need to know about working with the most common rest api authentication methods. api authentication is a primary way in which apis are secured, and it enables teams to protect sensitive data, build. Form Based Authentication For Rest Api.
From sidtechtalks.in
What is API and REST APIs? In easy language SidTechTalks Form Based Authentication For Rest Api — in this article, we will explore the fundamentals of securing restful apis with a focus on authentication and authorization, using java,. rest api authentication is a process used to authenticate users and applications when making api requests. api authentication is a primary way in which apis are secured, and it enables teams to protect sensitive data,. Form Based Authentication For Rest Api.
From www.mindomo.com
API REST Mind Map Form Based Authentication For Rest Api — in this article, we will explore the fundamentals of securing restful apis with a focus on authentication and authorization, using java,. rest api authentication is a process used to authenticate users and applications when making api requests. api authentication is a primary way in which apis are secured, and it enables teams to protect sensitive data,. Form Based Authentication For Rest Api.
From www.slideshare.net
Basic Authentication + Form based Auth. PPT Form Based Authentication For Rest Api api authentication is a primary way in which apis are secured, and it enables teams to protect sensitive data, build trust with. — today, we’re going to cover everything you need to know about working with the most common rest api authentication methods. rest api authentication is a process used to authenticate users and applications when making. Form Based Authentication For Rest Api.
From www.systemconf.com
What is REST and RESTful API? REST API and RESTful API with Examples Form Based Authentication For Rest Api rest api authentication is a process used to authenticate users and applications when making api requests. api authentication is a primary way in which apis are secured, and it enables teams to protect sensitive data, build trust with. — in this article, we will explore the fundamentals of securing restful apis with a focus on authentication and. Form Based Authentication For Rest Api.
From support.kemptechnologies.com
Form based to Form based Authentication Kemp Support Form Based Authentication For Rest Api in this article, we’ll cover one very powerful yet simple way to secure a rest api using json web tokens (jwt), reviewing some best practices and. api authentication is a primary way in which apis are secured, and it enables teams to protect sensitive data, build trust with. — in this article, we will explore the fundamentals. Form Based Authentication For Rest Api.
From www.javaguides.net
Difference Between Basic Authentication and Form Based Authentication Form Based Authentication For Rest Api — today, we’re going to cover everything you need to know about working with the most common rest api authentication methods. api authentication is a primary way in which apis are secured, and it enables teams to protect sensitive data, build trust with. In this article, we’ll discuss the different. rest api authentication is a process used. Form Based Authentication For Rest Api.
From www.altexsoft.com
REST API Best Practices, Concepts, Structure, and Benefits AltexSoft Form Based Authentication For Rest Api api authentication is a primary way in which apis are secured, and it enables teams to protect sensitive data, build trust with. in this article, we’ll cover one very powerful yet simple way to secure a rest api using json web tokens (jwt), reviewing some best practices and. — today, we’re going to cover everything you need. Form Based Authentication For Rest Api.
From printableformsfree.com
How To Use Basic Authentication In Rest Api Postman Printable Forms Form Based Authentication For Rest Api api authentication is a primary way in which apis are secured, and it enables teams to protect sensitive data, build trust with. — today, we’re going to cover everything you need to know about working with the most common rest api authentication methods. In this article, we’ll discuss the different. in this article, we’ll cover one very. Form Based Authentication For Rest Api.
From medium.com
Authorization and Authentication in API services by Ratros Y. Medium Form Based Authentication For Rest Api — in this article, we will explore the fundamentals of securing restful apis with a focus on authentication and authorization, using java,. — today, we’re going to cover everything you need to know about working with the most common rest api authentication methods. rest api authentication is a process used to authenticate users and applications when making. Form Based Authentication For Rest Api.
From github.com
GitHub ayyappan18/WCFRESTAPIWithFormsAuthentication A demo of a Form Based Authentication For Rest Api api authentication is a primary way in which apis are secured, and it enables teams to protect sensitive data, build trust with. In this article, we’ll discuss the different. — in this article, we will explore the fundamentals of securing restful apis with a focus on authentication and authorization, using java,. rest api authentication is a process. Form Based Authentication For Rest Api.
From www.devopsschool.com
What is Bearer token and How it works? Form Based Authentication For Rest Api in this article, we’ll cover one very powerful yet simple way to secure a rest api using json web tokens (jwt), reviewing some best practices and. — today, we’re going to cover everything you need to know about working with the most common rest api authentication methods. rest api authentication is a process used to authenticate users. Form Based Authentication For Rest Api.
From medium.com
REST — Basic and Form based authentication by Phani Kumar Medium Form Based Authentication For Rest Api in this article, we’ll cover one very powerful yet simple way to secure a rest api using json web tokens (jwt), reviewing some best practices and. rest api authentication is a process used to authenticate users and applications when making api requests. — today, we’re going to cover everything you need to know about working with the. Form Based Authentication For Rest Api.