Relay Attack Machine . In this article, we’re going to talk about how smb relay attacks work and how they can impact your business. The classic sam dump smb to smb relay using responder and ntlm relay. In a nutshell, smb relaying relies on having a valid encrypted challenge, once you have captured the hash (with a man in the middle. in this post, we will look into the details on how to simulate this kind of attack within core impact to uncover hidden attack paths that nefarious actors. If the account being relayed has local administrative privileges on the box, you can utilize their privileges to dump sam hashes or to get a system. All smb sessions use the ntml protocol for encryption and authentication purposes (i.e. during an smb relay attack, attackers capture a valid authentication session and then relay it, gaining access. smb relay attack overview. An smb relay attack is where an attacker captures a users ntlm hash and then relays it to access another machine on the network that has smb signing disabled.
from www.extrahop.com
In this article, we’re going to talk about how smb relay attacks work and how they can impact your business. in this post, we will look into the details on how to simulate this kind of attack within core impact to uncover hidden attack paths that nefarious actors. In a nutshell, smb relaying relies on having a valid encrypted challenge, once you have captured the hash (with a man in the middle. smb relay attack overview. If the account being relayed has local administrative privileges on the box, you can utilize their privileges to dump sam hashes or to get a system. The classic sam dump smb to smb relay using responder and ntlm relay. during an smb relay attack, attackers capture a valid authentication session and then relay it, gaining access. All smb sessions use the ntml protocol for encryption and authentication purposes (i.e. An smb relay attack is where an attacker captures a users ntlm hash and then relays it to access another machine on the network that has smb signing disabled.
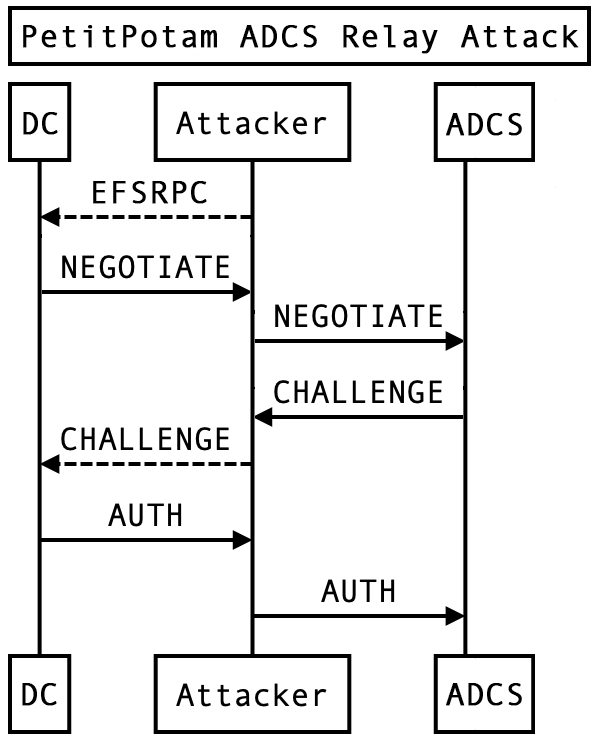
PetitPotam Expanding NTLM Relay Attacks
Relay Attack Machine smb relay attack overview. in this post, we will look into the details on how to simulate this kind of attack within core impact to uncover hidden attack paths that nefarious actors. An smb relay attack is where an attacker captures a users ntlm hash and then relays it to access another machine on the network that has smb signing disabled. smb relay attack overview. All smb sessions use the ntml protocol for encryption and authentication purposes (i.e. In a nutshell, smb relaying relies on having a valid encrypted challenge, once you have captured the hash (with a man in the middle. The classic sam dump smb to smb relay using responder and ntlm relay. If the account being relayed has local administrative privileges on the box, you can utilize their privileges to dump sam hashes or to get a system. during an smb relay attack, attackers capture a valid authentication session and then relay it, gaining access. In this article, we’re going to talk about how smb relay attacks work and how they can impact your business.
From www.intechopen.com
Implementation of a Countermeasure to Relay Attacks for Contactless HF Relay Attack Machine during an smb relay attack, attackers capture a valid authentication session and then relay it, gaining access. In this article, we’re going to talk about how smb relay attacks work and how they can impact your business. smb relay attack overview. An smb relay attack is where an attacker captures a users ntlm hash and then relays it. Relay Attack Machine.
From auto-grab.com
Keyless go repeater Starter Kit Relay attack device for 3 onoff Relay Attack Machine during an smb relay attack, attackers capture a valid authentication session and then relay it, gaining access. If the account being relayed has local administrative privileges on the box, you can utilize their privileges to dump sam hashes or to get a system. smb relay attack overview. All smb sessions use the ntml protocol for encryption and authentication. Relay Attack Machine.
From www.youtube.com
Relay attack device RANGE TEST YouTube Relay Attack Machine In this article, we’re going to talk about how smb relay attacks work and how they can impact your business. The classic sam dump smb to smb relay using responder and ntlm relay. In a nutshell, smb relaying relies on having a valid encrypted challenge, once you have captured the hash (with a man in the middle. during an. Relay Attack Machine.
From www.slideserve.com
PPT Keep Your Enemies Close Distance Bounding Against Smartcard Relay Attack Machine in this post, we will look into the details on how to simulate this kind of attack within core impact to uncover hidden attack paths that nefarious actors. smb relay attack overview. An smb relay attack is where an attacker captures a users ntlm hash and then relays it to access another machine on the network that has. Relay Attack Machine.
From www.comparitech.com
What is a Relay Attack (with examples) and How Do They Work? Relay Attack Machine in this post, we will look into the details on how to simulate this kind of attack within core impact to uncover hidden attack paths that nefarious actors. In this article, we’re going to talk about how smb relay attacks work and how they can impact your business. All smb sessions use the ntml protocol for encryption and authentication. Relay Attack Machine.
From file.scirp.org
Vehicle Relay Attack Avoidance Methods Using RF Signal Strength Relay Attack Machine The classic sam dump smb to smb relay using responder and ntlm relay. In a nutshell, smb relaying relies on having a valid encrypted challenge, once you have captured the hash (with a man in the middle. In this article, we’re going to talk about how smb relay attacks work and how they can impact your business. smb relay. Relay Attack Machine.
From www.researchgate.net
A PIN and Chip based relay attack Download Scientific Diagram Relay Attack Machine during an smb relay attack, attackers capture a valid authentication session and then relay it, gaining access. In this article, we’re going to talk about how smb relay attacks work and how they can impact your business. If the account being relayed has local administrative privileges on the box, you can utilize their privileges to dump sam hashes or. Relay Attack Machine.
From www.extrahop.com
PetitPotam Expanding NTLM Relay Attacks Relay Attack Machine in this post, we will look into the details on how to simulate this kind of attack within core impact to uncover hidden attack paths that nefarious actors. In a nutshell, smb relaying relies on having a valid encrypted challenge, once you have captured the hash (with a man in the middle. An smb relay attack is where an. Relay Attack Machine.
From howcarspecs.blogspot.com
Relay Attack Device How Car Specs Relay Attack Machine In this article, we’re going to talk about how smb relay attacks work and how they can impact your business. An smb relay attack is where an attacker captures a users ntlm hash and then relays it to access another machine on the network that has smb signing disabled. in this post, we will look into the details on. Relay Attack Machine.
From auto-grab.com
Keyless go repeater Starter Kit Relay attack device for 3 onoff Relay Attack Machine In a nutshell, smb relaying relies on having a valid encrypted challenge, once you have captured the hash (with a man in the middle. in this post, we will look into the details on how to simulate this kind of attack within core impact to uncover hidden attack paths that nefarious actors. smb relay attack overview. An smb. Relay Attack Machine.
From www.slideserve.com
PPT ZeroInteraction Authentication and Relay Attacks PowerPoint Relay Attack Machine In a nutshell, smb relaying relies on having a valid encrypted challenge, once you have captured the hash (with a man in the middle. The classic sam dump smb to smb relay using responder and ntlm relay. In this article, we’re going to talk about how smb relay attacks work and how they can impact your business. smb relay. Relay Attack Machine.
From www.hackingloops.com
SMB Relay Attack Relay Attack Machine If the account being relayed has local administrative privileges on the box, you can utilize their privileges to dump sam hashes or to get a system. in this post, we will look into the details on how to simulate this kind of attack within core impact to uncover hidden attack paths that nefarious actors. smb relay attack overview.. Relay Attack Machine.
From www.researchgate.net
Illustration of a typical malware based relay attack Download Relay Attack Machine in this post, we will look into the details on how to simulate this kind of attack within core impact to uncover hidden attack paths that nefarious actors. In this article, we’re going to talk about how smb relay attacks work and how they can impact your business. If the account being relayed has local administrative privileges on the. Relay Attack Machine.
From hackernoon.com
Signal Amplification Relay Attack (SARA) HackerNoon Relay Attack Machine smb relay attack overview. All smb sessions use the ntml protocol for encryption and authentication purposes (i.e. An smb relay attack is where an attacker captures a users ntlm hash and then relays it to access another machine on the network that has smb signing disabled. during an smb relay attack, attackers capture a valid authentication session and. Relay Attack Machine.
From www.hhcaetech.com
Advanced Automotive Relay Machine Relay Making Machine Relay Attack Machine in this post, we will look into the details on how to simulate this kind of attack within core impact to uncover hidden attack paths that nefarious actors. The classic sam dump smb to smb relay using responder and ntlm relay. during an smb relay attack, attackers capture a valid authentication session and then relay it, gaining access.. Relay Attack Machine.
From www.bernardsmith.eu
Relay Attacks Bernard Smith Relay Attack Machine An smb relay attack is where an attacker captures a users ntlm hash and then relays it to access another machine on the network that has smb signing disabled. in this post, we will look into the details on how to simulate this kind of attack within core impact to uncover hidden attack paths that nefarious actors. All smb. Relay Attack Machine.
From arstechnica.com
New Bluetooth hack can unlock your Tesla—and all kinds of other devices Relay Attack Machine during an smb relay attack, attackers capture a valid authentication session and then relay it, gaining access. All smb sessions use the ntml protocol for encryption and authentication purposes (i.e. The classic sam dump smb to smb relay using responder and ntlm relay. An smb relay attack is where an attacker captures a users ntlm hash and then relays. Relay Attack Machine.
From www.slideserve.com
PPT ZeroInteraction Authentication and Relay Attacks PowerPoint Relay Attack Machine In a nutshell, smb relaying relies on having a valid encrypted challenge, once you have captured the hash (with a man in the middle. In this article, we’re going to talk about how smb relay attacks work and how they can impact your business. smb relay attack overview. The classic sam dump smb to smb relay using responder and. Relay Attack Machine.
From www.youtube.com
What is a Keyless Relay Attack? How to protect against Car Theft YouTube Relay Attack Machine If the account being relayed has local administrative privileges on the box, you can utilize their privileges to dump sam hashes or to get a system. smb relay attack overview. In a nutshell, smb relaying relies on having a valid encrypted challenge, once you have captured the hash (with a man in the middle. in this post, we. Relay Attack Machine.
From howcarspecs.blogspot.com
Relay Attack Device How Car Specs Relay Attack Machine In this article, we’re going to talk about how smb relay attacks work and how they can impact your business. during an smb relay attack, attackers capture a valid authentication session and then relay it, gaining access. The classic sam dump smb to smb relay using responder and ntlm relay. smb relay attack overview. An smb relay attack. Relay Attack Machine.
From www.extrahop.com
PetitPotam Expanding NTLM Relay Attacks Relay Attack Machine An smb relay attack is where an attacker captures a users ntlm hash and then relays it to access another machine on the network that has smb signing disabled. In a nutshell, smb relaying relies on having a valid encrypted challenge, once you have captured the hash (with a man in the middle. during an smb relay attack, attackers. Relay Attack Machine.
From unlockcarsgrabber.com
Keyless Go Repeater FBS4 Relay Attack UnlockCars Grabber Relay Attack Machine In a nutshell, smb relaying relies on having a valid encrypted challenge, once you have captured the hash (with a man in the middle. smb relay attack overview. An smb relay attack is where an attacker captures a users ntlm hash and then relays it to access another machine on the network that has smb signing disabled. If the. Relay Attack Machine.
From auto-grab.com
Keyless go repeater Starter Kit Relay attack device for 3 onoff Relay Attack Machine in this post, we will look into the details on how to simulate this kind of attack within core impact to uncover hidden attack paths that nefarious actors. An smb relay attack is where an attacker captures a users ntlm hash and then relays it to access another machine on the network that has smb signing disabled. The classic. Relay Attack Machine.
From socradar.io
NTLM Relay Attack Leads to Windows Domain Takeover SOCRadar® Cyber Relay Attack Machine If the account being relayed has local administrative privileges on the box, you can utilize their privileges to dump sam hashes or to get a system. The classic sam dump smb to smb relay using responder and ntlm relay. In a nutshell, smb relaying relies on having a valid encrypted challenge, once you have captured the hash (with a man. Relay Attack Machine.
From exogculqz.blob.core.windows.net
Different Types Of Relay Attack at David Russo blog Relay Attack Machine smb relay attack overview. An smb relay attack is where an attacker captures a users ntlm hash and then relays it to access another machine on the network that has smb signing disabled. All smb sessions use the ntml protocol for encryption and authentication purposes (i.e. In a nutshell, smb relaying relies on having a valid encrypted challenge, once. Relay Attack Machine.
From www.semanticscholar.org
Figure 1 from Vehicle Relay Attack Avoidance Methods Using RF Signal Relay Attack Machine In this article, we’re going to talk about how smb relay attacks work and how they can impact your business. If the account being relayed has local administrative privileges on the box, you can utilize their privileges to dump sam hashes or to get a system. In a nutshell, smb relaying relies on having a valid encrypted challenge, once you. Relay Attack Machine.
From www.slideserve.com
PPT Relay Attacks on Passive Keyless Entry and Start Systems in Relay Attack Machine An smb relay attack is where an attacker captures a users ntlm hash and then relays it to access another machine on the network that has smb signing disabled. In this article, we’re going to talk about how smb relay attacks work and how they can impact your business. during an smb relay attack, attackers capture a valid authentication. Relay Attack Machine.
From smartkeylessprotector.com
Relay attack All you need to know Smart Keyless Protector Relay Attack Machine smb relay attack overview. The classic sam dump smb to smb relay using responder and ntlm relay. In this article, we’re going to talk about how smb relay attacks work and how they can impact your business. during an smb relay attack, attackers capture a valid authentication session and then relay it, gaining access. in this post,. Relay Attack Machine.
From www.autoevolution.com
Ford Patents Key Fob Relay Attack Prevention System, Will Make Stealing Relay Attack Machine An smb relay attack is where an attacker captures a users ntlm hash and then relays it to access another machine on the network that has smb signing disabled. during an smb relay attack, attackers capture a valid authentication session and then relay it, gaining access. In a nutshell, smb relaying relies on having a valid encrypted challenge, once. Relay Attack Machine.
From file.scirp.org
Vehicle Relay Attack Avoidance Methods Using RF Signal Strength Relay Attack Machine during an smb relay attack, attackers capture a valid authentication session and then relay it, gaining access. An smb relay attack is where an attacker captures a users ntlm hash and then relays it to access another machine on the network that has smb signing disabled. In a nutshell, smb relaying relies on having a valid encrypted challenge, once. Relay Attack Machine.
From blog.adafruit.com
The Relay Car Hack Reinvented with 22 Hardware and Up to 1000 Foot Relay Attack Machine smb relay attack overview. If the account being relayed has local administrative privileges on the box, you can utilize their privileges to dump sam hashes or to get a system. In a nutshell, smb relaying relies on having a valid encrypted challenge, once you have captured the hash (with a man in the middle. during an smb relay. Relay Attack Machine.
From www.intechopen.com
Implementation of a Countermeasure to Relay Attacks for Contactless HF Relay Attack Machine In this article, we’re going to talk about how smb relay attacks work and how they can impact your business. smb relay attack overview. during an smb relay attack, attackers capture a valid authentication session and then relay it, gaining access. In a nutshell, smb relaying relies on having a valid encrypted challenge, once you have captured the. Relay Attack Machine.
From www.researchgate.net
Adversaries relaying RF signal for long distance This paragraph Relay Attack Machine during an smb relay attack, attackers capture a valid authentication session and then relay it, gaining access. in this post, we will look into the details on how to simulate this kind of attack within core impact to uncover hidden attack paths that nefarious actors. If the account being relayed has local administrative privileges on the box, you. Relay Attack Machine.
From www.secureauth.com
What is old is new again The Relay Attack SecureAuth Relay Attack Machine during an smb relay attack, attackers capture a valid authentication session and then relay it, gaining access. In this article, we’re going to talk about how smb relay attacks work and how they can impact your business. smb relay attack overview. All smb sessions use the ntml protocol for encryption and authentication purposes (i.e. The classic sam dump. Relay Attack Machine.
From www.slideserve.com
PPT NTLM Relay Attacks PowerPoint Presentation, free download ID Relay Attack Machine In a nutshell, smb relaying relies on having a valid encrypted challenge, once you have captured the hash (with a man in the middle. in this post, we will look into the details on how to simulate this kind of attack within core impact to uncover hidden attack paths that nefarious actors. An smb relay attack is where an. Relay Attack Machine.