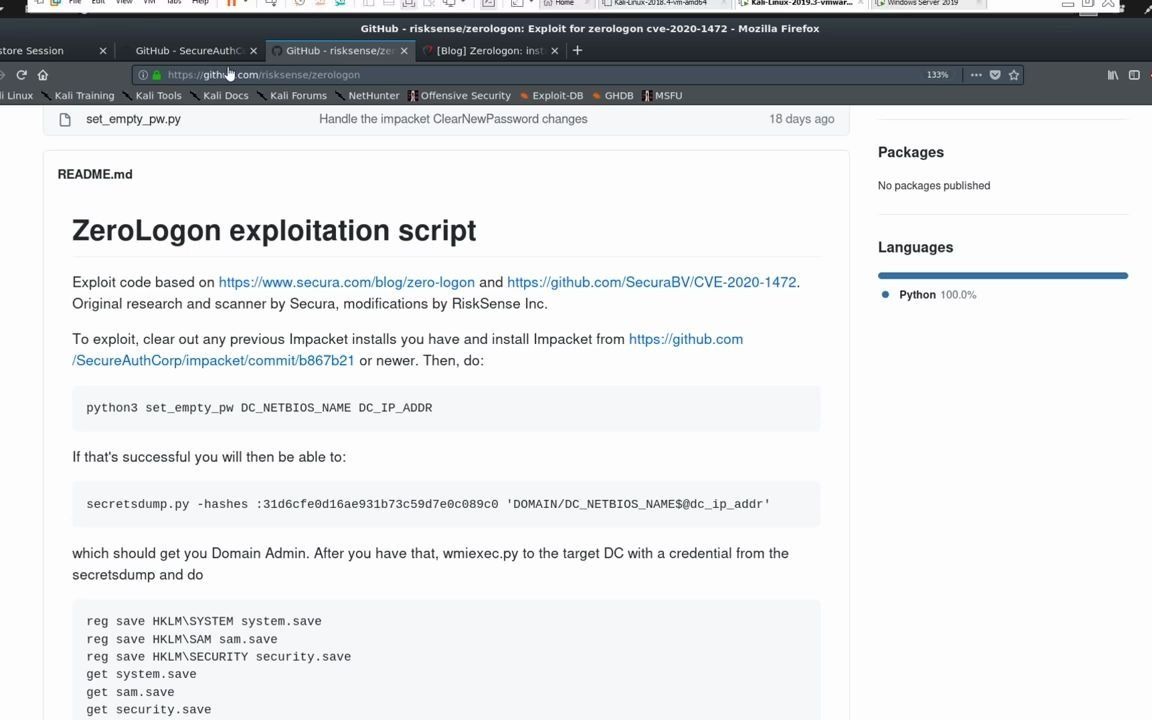
Exploiting Zerologon . — zerologon is a powerful vulnerability for attackers to leverage, but in a normal attack scenario it will require an initial entry vector inside an organization to facilitate exploitation against domain controllers. — dive into our technical walkthrough of zerologon, an elevation of privilege vulnerability exploited by. — the walkthrough below will show you how to exploit the zerologon vulnerability to gain domain admin during.
from www.bilibili.com
— dive into our technical walkthrough of zerologon, an elevation of privilege vulnerability exploited by. — the walkthrough below will show you how to exploit the zerologon vulnerability to gain domain admin during. — zerologon is a powerful vulnerability for attackers to leverage, but in a normal attack scenario it will require an initial entry vector inside an organization to facilitate exploitation against domain controllers.
ZeroLogon Exploit Abusing CVE20201472 (Way Too Easy!)_哔哩哔哩_bilibili
Exploiting Zerologon — the walkthrough below will show you how to exploit the zerologon vulnerability to gain domain admin during. — zerologon is a powerful vulnerability for attackers to leverage, but in a normal attack scenario it will require an initial entry vector inside an organization to facilitate exploitation against domain controllers. — dive into our technical walkthrough of zerologon, an elevation of privilege vulnerability exploited by. — the walkthrough below will show you how to exploit the zerologon vulnerability to gain domain admin during.
From www.techspot.com
Zerologon Windows exploit lets attackers instantly admins on Exploiting Zerologon — dive into our technical walkthrough of zerologon, an elevation of privilege vulnerability exploited by. — the walkthrough below will show you how to exploit the zerologon vulnerability to gain domain admin during. — zerologon is a powerful vulnerability for attackers to leverage, but in a normal attack scenario it will require an initial entry vector inside. Exploiting Zerologon.
From www.itpro.com
Microsoft Defender for Identity can now detect Zerologon exploits ITPro Exploiting Zerologon — dive into our technical walkthrough of zerologon, an elevation of privilege vulnerability exploited by. — zerologon is a powerful vulnerability for attackers to leverage, but in a normal attack scenario it will require an initial entry vector inside an organization to facilitate exploitation against domain controllers. — the walkthrough below will show you how to exploit. Exploiting Zerologon.
From www.kroll.com
CVE20201472 (Zerologon) Exploit Detection Cheat Sheet Exploiting Zerologon — the walkthrough below will show you how to exploit the zerologon vulnerability to gain domain admin during. — zerologon is a powerful vulnerability for attackers to leverage, but in a normal attack scenario it will require an initial entry vector inside an organization to facilitate exploitation against domain controllers. — dive into our technical walkthrough of. Exploiting Zerologon.
From www.facebook.com
Exploiting ZeroLogon... the easy way using Metasploit By MME Video Exploiting Zerologon — the walkthrough below will show you how to exploit the zerologon vulnerability to gain domain admin during. — dive into our technical walkthrough of zerologon, an elevation of privilege vulnerability exploited by. — zerologon is a powerful vulnerability for attackers to leverage, but in a normal attack scenario it will require an initial entry vector inside. Exploiting Zerologon.
From www.youtube.com
Zerologon Exploit With Metasploit YouTube Exploiting Zerologon — dive into our technical walkthrough of zerologon, an elevation of privilege vulnerability exploited by. — zerologon is a powerful vulnerability for attackers to leverage, but in a normal attack scenario it will require an initial entry vector inside an organization to facilitate exploitation against domain controllers. — the walkthrough below will show you how to exploit. Exploiting Zerologon.
From www.youtube.com
Zerologon Exploit CVE1472 Dump hashes from NTDS.dit YouTube Exploiting Zerologon — zerologon is a powerful vulnerability for attackers to leverage, but in a normal attack scenario it will require an initial entry vector inside an organization to facilitate exploitation against domain controllers. — the walkthrough below will show you how to exploit the zerologon vulnerability to gain domain admin during. — dive into our technical walkthrough of. Exploiting Zerologon.
From github.com
GitHub hellmoon/ZeroLogonExploit Modified the test PoC from Secura Exploiting Zerologon — dive into our technical walkthrough of zerologon, an elevation of privilege vulnerability exploited by. — the walkthrough below will show you how to exploit the zerologon vulnerability to gain domain admin during. — zerologon is a powerful vulnerability for attackers to leverage, but in a normal attack scenario it will require an initial entry vector inside. Exploiting Zerologon.
From reconshell.com
CVE20201472 Zerologon Exploit POC Testing Tools, ML Exploiting Zerologon — the walkthrough below will show you how to exploit the zerologon vulnerability to gain domain admin during. — dive into our technical walkthrough of zerologon, an elevation of privilege vulnerability exploited by. — zerologon is a powerful vulnerability for attackers to leverage, but in a normal attack scenario it will require an initial entry vector inside. Exploiting Zerologon.
From es.darktrace.com
ZeroLogon exploit detected within 24 hours of vulnerability notice Exploiting Zerologon — zerologon is a powerful vulnerability for attackers to leverage, but in a normal attack scenario it will require an initial entry vector inside an organization to facilitate exploitation against domain controllers. — the walkthrough below will show you how to exploit the zerologon vulnerability to gain domain admin during. — dive into our technical walkthrough of. Exploiting Zerologon.
From sekurak.pl
Exploit na podatność Zerologon dostępny jest w najnowszym Mimikatz Exploiting Zerologon — zerologon is a powerful vulnerability for attackers to leverage, but in a normal attack scenario it will require an initial entry vector inside an organization to facilitate exploitation against domain controllers. — the walkthrough below will show you how to exploit the zerologon vulnerability to gain domain admin during. — dive into our technical walkthrough of. Exploiting Zerologon.
From www.youtube.com
Zerologon exploit by using metasploit YouTube Exploiting Zerologon — zerologon is a powerful vulnerability for attackers to leverage, but in a normal attack scenario it will require an initial entry vector inside an organization to facilitate exploitation against domain controllers. — the walkthrough below will show you how to exploit the zerologon vulnerability to gain domain admin during. — dive into our technical walkthrough of. Exploiting Zerologon.
From www.youtube.com
ZeroLogon Exploit PoC CVE20201472 on WS16 DC (Exploiting From Exploiting Zerologon — dive into our technical walkthrough of zerologon, an elevation of privilege vulnerability exploited by. — zerologon is a powerful vulnerability for attackers to leverage, but in a normal attack scenario it will require an initial entry vector inside an organization to facilitate exploitation against domain controllers. — the walkthrough below will show you how to exploit. Exploiting Zerologon.
From www.techspot.com
Zerologon Windows exploit lets attackers instantly admins on Exploiting Zerologon — dive into our technical walkthrough of zerologon, an elevation of privilege vulnerability exploited by. — zerologon is a powerful vulnerability for attackers to leverage, but in a normal attack scenario it will require an initial entry vector inside an organization to facilitate exploitation against domain controllers. — the walkthrough below will show you how to exploit. Exploiting Zerologon.
From www.netwrix.com
Zerologon Exploit Attack Exploiting Zerologon — dive into our technical walkthrough of zerologon, an elevation of privilege vulnerability exploited by. — the walkthrough below will show you how to exploit the zerologon vulnerability to gain domain admin during. — zerologon is a powerful vulnerability for attackers to leverage, but in a normal attack scenario it will require an initial entry vector inside. Exploiting Zerologon.
From www.eyerys.com
How 'Zerologon', One Of The Most Severe Windows Bugs Ever Reported Exploiting Zerologon — the walkthrough below will show you how to exploit the zerologon vulnerability to gain domain admin during. — zerologon is a powerful vulnerability for attackers to leverage, but in a normal attack scenario it will require an initial entry vector inside an organization to facilitate exploitation against domain controllers. — dive into our technical walkthrough of. Exploiting Zerologon.
From github.com
GitHub hellmoon/ZeroLogonExploit Modified the test PoC from Secura Exploiting Zerologon — zerologon is a powerful vulnerability for attackers to leverage, but in a normal attack scenario it will require an initial entry vector inside an organization to facilitate exploitation against domain controllers. — dive into our technical walkthrough of zerologon, an elevation of privilege vulnerability exploited by. — the walkthrough below will show you how to exploit. Exploiting Zerologon.
From reconshell.com
CVE20201472 Zerologon Exploit POC Testing Tools, ML Exploiting Zerologon — the walkthrough below will show you how to exploit the zerologon vulnerability to gain domain admin during. — zerologon is a powerful vulnerability for attackers to leverage, but in a normal attack scenario it will require an initial entry vector inside an organization to facilitate exploitation against domain controllers. — dive into our technical walkthrough of. Exploiting Zerologon.
From hum4ng0d.github.io
CVE20201472 Zerologon Exploit POC hum4nG0D.github.io Exploiting Zerologon — zerologon is a powerful vulnerability for attackers to leverage, but in a normal attack scenario it will require an initial entry vector inside an organization to facilitate exploitation against domain controllers. — the walkthrough below will show you how to exploit the zerologon vulnerability to gain domain admin during. — dive into our technical walkthrough of. Exploiting Zerologon.
From www.bilibili.com
ZeroLogon Exploit Abusing CVE20201472 (Way Too Easy!)_哔哩哔哩_bilibili Exploiting Zerologon — the walkthrough below will show you how to exploit the zerologon vulnerability to gain domain admin during. — zerologon is a powerful vulnerability for attackers to leverage, but in a normal attack scenario it will require an initial entry vector inside an organization to facilitate exploitation against domain controllers. — dive into our technical walkthrough of. Exploiting Zerologon.
From www.youtube.com
Vuln chaining exploit Zerologon & take over the Domain Controller Exploiting Zerologon — the walkthrough below will show you how to exploit the zerologon vulnerability to gain domain admin during. — dive into our technical walkthrough of zerologon, an elevation of privilege vulnerability exploited by. — zerologon is a powerful vulnerability for attackers to leverage, but in a normal attack scenario it will require an initial entry vector inside. Exploiting Zerologon.
From hurricanelabs.com
Using Splunk Enterprise Security to Look for Zerologon Exploit Attempts Exploiting Zerologon — zerologon is a powerful vulnerability for attackers to leverage, but in a normal attack scenario it will require an initial entry vector inside an organization to facilitate exploitation against domain controllers. — the walkthrough below will show you how to exploit the zerologon vulnerability to gain domain admin during. — dive into our technical walkthrough of. Exploiting Zerologon.
From www.youtube.com
Cyber Sec Labs Shares, Office and Zero AD (ZeroLogon Exploit) YouTube Exploiting Zerologon — the walkthrough below will show you how to exploit the zerologon vulnerability to gain domain admin during. — zerologon is a powerful vulnerability for attackers to leverage, but in a normal attack scenario it will require an initial entry vector inside an organization to facilitate exploitation against domain controllers. — dive into our technical walkthrough of. Exploiting Zerologon.
From howtofix.guide
TrojanPowerShell/SharpZeroLogon (ZeroLogon Exploit) — Virus Removal Guide Exploiting Zerologon — zerologon is a powerful vulnerability for attackers to leverage, but in a normal attack scenario it will require an initial entry vector inside an organization to facilitate exploitation against domain controllers. — the walkthrough below will show you how to exploit the zerologon vulnerability to gain domain admin during. — dive into our technical walkthrough of. Exploiting Zerologon.
From www.kroll.com
CVE20201472 (Zerologon) Exploit Detection Cheat Sheet Exploiting Zerologon — dive into our technical walkthrough of zerologon, an elevation of privilege vulnerability exploited by. — zerologon is a powerful vulnerability for attackers to leverage, but in a normal attack scenario it will require an initial entry vector inside an organization to facilitate exploitation against domain controllers. — the walkthrough below will show you how to exploit. Exploiting Zerologon.
From darktrace.com
ZeroLogon exploit detected within 24 hours of vulnerability notice Exploiting Zerologon — zerologon is a powerful vulnerability for attackers to leverage, but in a normal attack scenario it will require an initial entry vector inside an organization to facilitate exploitation against domain controllers. — dive into our technical walkthrough of zerologon, an elevation of privilege vulnerability exploited by. — the walkthrough below will show you how to exploit. Exploiting Zerologon.
From www.youtube.com
ZeroLogon Exploit (CVE20201472) YouTube Exploiting Zerologon — dive into our technical walkthrough of zerologon, an elevation of privilege vulnerability exploited by. — the walkthrough below will show you how to exploit the zerologon vulnerability to gain domain admin during. — zerologon is a powerful vulnerability for attackers to leverage, but in a normal attack scenario it will require an initial entry vector inside. Exploiting Zerologon.
From www.youtube.com
Zerologon exploit POC YouTube Exploiting Zerologon — dive into our technical walkthrough of zerologon, an elevation of privilege vulnerability exploited by. — zerologon is a powerful vulnerability for attackers to leverage, but in a normal attack scenario it will require an initial entry vector inside an organization to facilitate exploitation against domain controllers. — the walkthrough below will show you how to exploit. Exploiting Zerologon.
From www.youtube.com
Exploiting ZeroLogon (Part II Restore) YouTube Exploiting Zerologon — dive into our technical walkthrough of zerologon, an elevation of privilege vulnerability exploited by. — zerologon is a powerful vulnerability for attackers to leverage, but in a normal attack scenario it will require an initial entry vector inside an organization to facilitate exploitation against domain controllers. — the walkthrough below will show you how to exploit. Exploiting Zerologon.
From www.kroll.com
CVE20201472 (Zerologon) Exploit Detection Cheat Sheet Exploiting Zerologon — dive into our technical walkthrough of zerologon, an elevation of privilege vulnerability exploited by. — the walkthrough below will show you how to exploit the zerologon vulnerability to gain domain admin during. — zerologon is a powerful vulnerability for attackers to leverage, but in a normal attack scenario it will require an initial entry vector inside. Exploiting Zerologon.
From github.com
GitHub hellmoon/ZeroLogonExploit Modified the test PoC from Secura Exploiting Zerologon — the walkthrough below will show you how to exploit the zerologon vulnerability to gain domain admin during. — zerologon is a powerful vulnerability for attackers to leverage, but in a normal attack scenario it will require an initial entry vector inside an organization to facilitate exploitation against domain controllers. — dive into our technical walkthrough of. Exploiting Zerologon.
From www.kroll.com
CVE20201472 (Zerologon) Exploit Detection Cheat Sheet Exploiting Zerologon — zerologon is a powerful vulnerability for attackers to leverage, but in a normal attack scenario it will require an initial entry vector inside an organization to facilitate exploitation against domain controllers. — dive into our technical walkthrough of zerologon, an elevation of privilege vulnerability exploited by. — the walkthrough below will show you how to exploit. Exploiting Zerologon.
From www.kroll.com
CVE20201472 (Zerologon) Exploit Detection Cheat Sheet Exploiting Zerologon — zerologon is a powerful vulnerability for attackers to leverage, but in a normal attack scenario it will require an initial entry vector inside an organization to facilitate exploitation against domain controllers. — the walkthrough below will show you how to exploit the zerologon vulnerability to gain domain admin during. — dive into our technical walkthrough of. Exploiting Zerologon.
From firsthackersnews.com
"Zerologon" Exploit for Netlogon Remote Protocol First Hackers News Exploiting Zerologon — the walkthrough below will show you how to exploit the zerologon vulnerability to gain domain admin during. — dive into our technical walkthrough of zerologon, an elevation of privilege vulnerability exploited by. — zerologon is a powerful vulnerability for attackers to leverage, but in a normal attack scenario it will require an initial entry vector inside. Exploiting Zerologon.
From www.youtube.com
ZeroLogon Exploit (CVE20201472) Very Easy..! YouTube Exploiting Zerologon — dive into our technical walkthrough of zerologon, an elevation of privilege vulnerability exploited by. — zerologon is a powerful vulnerability for attackers to leverage, but in a normal attack scenario it will require an initial entry vector inside an organization to facilitate exploitation against domain controllers. — the walkthrough below will show you how to exploit. Exploiting Zerologon.
From blackpointcyber.com
Critical Windows “MSNRPC” Exploit ZeroLogon (CVE20201472 Exploiting Zerologon — the walkthrough below will show you how to exploit the zerologon vulnerability to gain domain admin during. — zerologon is a powerful vulnerability for attackers to leverage, but in a normal attack scenario it will require an initial entry vector inside an organization to facilitate exploitation against domain controllers. — dive into our technical walkthrough of. Exploiting Zerologon.