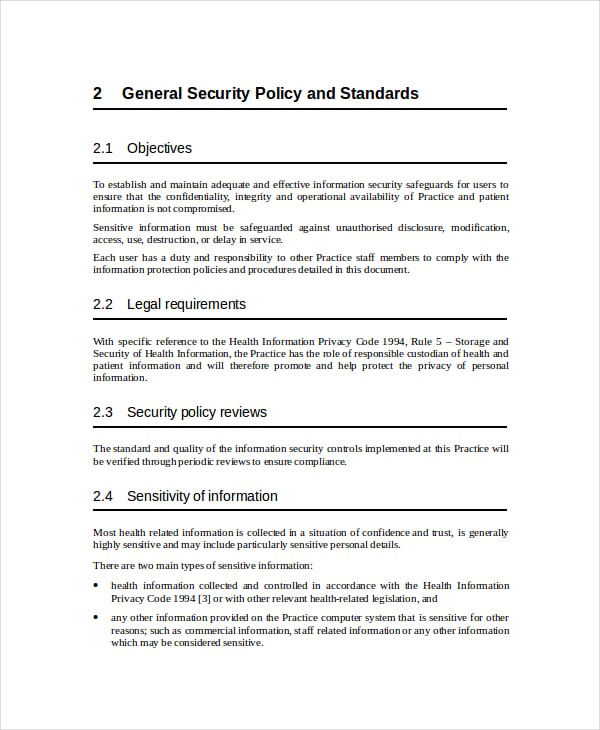
Cyber Security Access Control Policy . implementing an effective access control policy offers several key benefits: Access to assets and associated facilities is limited to authorized users, processes, or devices. an access control policy that addresses purpose, scope, roles, responsibilities, management. access control is a data security process that enables organizations to manage who is authorized to access corporate data and. this publication provides a catalog of security and privacy controls for information systems and organizations to.
from www.template.net
implementing an effective access control policy offers several key benefits: Access to assets and associated facilities is limited to authorized users, processes, or devices. an access control policy that addresses purpose, scope, roles, responsibilities, management. this publication provides a catalog of security and privacy controls for information systems and organizations to. access control is a data security process that enables organizations to manage who is authorized to access corporate data and.
Security Policy Template 13 Free Word, PDF Document Downloads
Cyber Security Access Control Policy an access control policy that addresses purpose, scope, roles, responsibilities, management. access control is a data security process that enables organizations to manage who is authorized to access corporate data and. implementing an effective access control policy offers several key benefits: Access to assets and associated facilities is limited to authorized users, processes, or devices. an access control policy that addresses purpose, scope, roles, responsibilities, management. this publication provides a catalog of security and privacy controls for information systems and organizations to.
From hightable.io
ISO 27001 Access Control Policy Ultimate Guide [+ template] Cyber Security Access Control Policy this publication provides a catalog of security and privacy controls for information systems and organizations to. implementing an effective access control policy offers several key benefits: Access to assets and associated facilities is limited to authorized users, processes, or devices. an access control policy that addresses purpose, scope, roles, responsibilities, management. access control is a data. Cyber Security Access Control Policy.
From www.securityinfowatch.com
Cybersecurity Assessments An Overview Security Info Watch Cyber Security Access Control Policy this publication provides a catalog of security and privacy controls for information systems and organizations to. implementing an effective access control policy offers several key benefits: access control is a data security process that enables organizations to manage who is authorized to access corporate data and. Access to assets and associated facilities is limited to authorized users,. Cyber Security Access Control Policy.
From cyberhoot.com
Access Control Mechanism CyberHoot Cyber Security Access Control Policy this publication provides a catalog of security and privacy controls for information systems and organizations to. Access to assets and associated facilities is limited to authorized users, processes, or devices. an access control policy that addresses purpose, scope, roles, responsibilities, management. access control is a data security process that enables organizations to manage who is authorized to. Cyber Security Access Control Policy.
From robots.net
Why Is Establishing Authentication Procedures A Common Cybersecurity Cyber Security Access Control Policy access control is a data security process that enables organizations to manage who is authorized to access corporate data and. this publication provides a catalog of security and privacy controls for information systems and organizations to. implementing an effective access control policy offers several key benefits: an access control policy that addresses purpose, scope, roles, responsibilities,. Cyber Security Access Control Policy.
From thecyphere.com
Access Control Security Types Of Access Control Cyber Security Access Control Policy access control is a data security process that enables organizations to manage who is authorized to access corporate data and. this publication provides a catalog of security and privacy controls for information systems and organizations to. implementing an effective access control policy offers several key benefits: Access to assets and associated facilities is limited to authorized users,. Cyber Security Access Control Policy.
From helpdesk.realworld.net.au
Cyber Security Policy template Real World Help Centre Cyber Security Access Control Policy Access to assets and associated facilities is limited to authorized users, processes, or devices. implementing an effective access control policy offers several key benefits: access control is a data security process that enables organizations to manage who is authorized to access corporate data and. an access control policy that addresses purpose, scope, roles, responsibilities, management. this. Cyber Security Access Control Policy.
From data-flair.training
Cyber Security Policies DataFlair Cyber Security Access Control Policy implementing an effective access control policy offers several key benefits: this publication provides a catalog of security and privacy controls for information systems and organizations to. an access control policy that addresses purpose, scope, roles, responsibilities, management. access control is a data security process that enables organizations to manage who is authorized to access corporate data. Cyber Security Access Control Policy.
From templatelab.com
42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab Cyber Security Access Control Policy Access to assets and associated facilities is limited to authorized users, processes, or devices. this publication provides a catalog of security and privacy controls for information systems and organizations to. access control is a data security process that enables organizations to manage who is authorized to access corporate data and. implementing an effective access control policy offers. Cyber Security Access Control Policy.
From www.youtube.com
iSc2 Certified in Cyber Security Access Control Concepts Domain 03 Cyber Security Access Control Policy an access control policy that addresses purpose, scope, roles, responsibilities, management. this publication provides a catalog of security and privacy controls for information systems and organizations to. Access to assets and associated facilities is limited to authorized users, processes, or devices. access control is a data security process that enables organizations to manage who is authorized to. Cyber Security Access Control Policy.
From www.yokogawa.com
Cybersecurity Policies & Procedures Yokogawa Electric Corporation Cyber Security Access Control Policy access control is a data security process that enables organizations to manage who is authorized to access corporate data and. this publication provides a catalog of security and privacy controls for information systems and organizations to. an access control policy that addresses purpose, scope, roles, responsibilities, management. Access to assets and associated facilities is limited to authorized. Cyber Security Access Control Policy.
From dxokowmxa.blob.core.windows.net
What Is A Access Control Security Policy at Tony Hart blog Cyber Security Access Control Policy implementing an effective access control policy offers several key benefits: an access control policy that addresses purpose, scope, roles, responsibilities, management. Access to assets and associated facilities is limited to authorized users, processes, or devices. access control is a data security process that enables organizations to manage who is authorized to access corporate data and. this. Cyber Security Access Control Policy.
From www.bizmanualz.com
IT Access Control Policy Access Control Policies And Procedures Cyber Security Access Control Policy implementing an effective access control policy offers several key benefits: access control is a data security process that enables organizations to manage who is authorized to access corporate data and. this publication provides a catalog of security and privacy controls for information systems and organizations to. an access control policy that addresses purpose, scope, roles, responsibilities,. Cyber Security Access Control Policy.
From www.datamation.com
IT Security Policy Definition, Types & How to Create One Cyber Security Access Control Policy Access to assets and associated facilities is limited to authorized users, processes, or devices. this publication provides a catalog of security and privacy controls for information systems and organizations to. an access control policy that addresses purpose, scope, roles, responsibilities, management. access control is a data security process that enables organizations to manage who is authorized to. Cyber Security Access Control Policy.
From www.slideteam.net
Systems Access Control Security Policy Cyber Security Access Control Policy this publication provides a catalog of security and privacy controls for information systems and organizations to. access control is a data security process that enables organizations to manage who is authorized to access corporate data and. an access control policy that addresses purpose, scope, roles, responsibilities, management. implementing an effective access control policy offers several key. Cyber Security Access Control Policy.
From dxozyyufc.blob.core.windows.net
Access Control Network Devices at Elliott blog Cyber Security Access Control Policy implementing an effective access control policy offers several key benefits: Access to assets and associated facilities is limited to authorized users, processes, or devices. access control is a data security process that enables organizations to manage who is authorized to access corporate data and. an access control policy that addresses purpose, scope, roles, responsibilities, management. this. Cyber Security Access Control Policy.
From tech.co
12 Cyber Security Measures Your Small Business Needs Cyber Security Access Control Policy implementing an effective access control policy offers several key benefits: access control is a data security process that enables organizations to manage who is authorized to access corporate data and. Access to assets and associated facilities is limited to authorized users, processes, or devices. this publication provides a catalog of security and privacy controls for information systems. Cyber Security Access Control Policy.
From www.comparitech.com
NIST Cybersecurity Framework Guide 2024 Core, Implementation & Profile Cyber Security Access Control Policy an access control policy that addresses purpose, scope, roles, responsibilities, management. this publication provides a catalog of security and privacy controls for information systems and organizations to. Access to assets and associated facilities is limited to authorized users, processes, or devices. access control is a data security process that enables organizations to manage who is authorized to. Cyber Security Access Control Policy.
From www.resmo.com
9 Access Control Best Practices Resmo Cyber Security Access Control Policy access control is a data security process that enables organizations to manage who is authorized to access corporate data and. this publication provides a catalog of security and privacy controls for information systems and organizations to. an access control policy that addresses purpose, scope, roles, responsibilities, management. Access to assets and associated facilities is limited to authorized. Cyber Security Access Control Policy.
From www.template.net
Security Policy Template 13 Free Word, PDF Document Downloads Cyber Security Access Control Policy implementing an effective access control policy offers several key benefits: access control is a data security process that enables organizations to manage who is authorized to access corporate data and. this publication provides a catalog of security and privacy controls for information systems and organizations to. Access to assets and associated facilities is limited to authorized users,. Cyber Security Access Control Policy.
From old.sermitsiaq.ag
Admin Access Policy Template Cyber Security Access Control Policy an access control policy that addresses purpose, scope, roles, responsibilities, management. access control is a data security process that enables organizations to manage who is authorized to access corporate data and. this publication provides a catalog of security and privacy controls for information systems and organizations to. implementing an effective access control policy offers several key. Cyber Security Access Control Policy.
From ipkeys.com
Access Control Policy & Procedures Template [w/ Examples] Cyber Security Access Control Policy access control is a data security process that enables organizations to manage who is authorized to access corporate data and. an access control policy that addresses purpose, scope, roles, responsibilities, management. Access to assets and associated facilities is limited to authorized users, processes, or devices. implementing an effective access control policy offers several key benefits: this. Cyber Security Access Control Policy.
From satoricyber.com
Chapter 3 Cybersecurity Frameworks Satori Cyber Security Access Control Policy implementing an effective access control policy offers several key benefits: Access to assets and associated facilities is limited to authorized users, processes, or devices. access control is a data security process that enables organizations to manage who is authorized to access corporate data and. an access control policy that addresses purpose, scope, roles, responsibilities, management. this. Cyber Security Access Control Policy.
From www.stealthlabs.com
What is NIST Compliance? Key Steps to NIST Compliant Cyber Security Access Control Policy implementing an effective access control policy offers several key benefits: Access to assets and associated facilities is limited to authorized users, processes, or devices. this publication provides a catalog of security and privacy controls for information systems and organizations to. an access control policy that addresses purpose, scope, roles, responsibilities, management. access control is a data. Cyber Security Access Control Policy.
From www.gotyoursixcyber.com
Access Control Got Your Six Cybersecurity Cyber Security Access Control Policy Access to assets and associated facilities is limited to authorized users, processes, or devices. this publication provides a catalog of security and privacy controls for information systems and organizations to. access control is a data security process that enables organizations to manage who is authorized to access corporate data and. an access control policy that addresses purpose,. Cyber Security Access Control Policy.
From www.kroll.com
10 Essential Cyber Security Controls for Increased Resilience Cyber Security Access Control Policy Access to assets and associated facilities is limited to authorized users, processes, or devices. implementing an effective access control policy offers several key benefits: this publication provides a catalog of security and privacy controls for information systems and organizations to. an access control policy that addresses purpose, scope, roles, responsibilities, management. access control is a data. Cyber Security Access Control Policy.
From www.youtube.com
Access Control User access control Access Control system Network Cyber Security Access Control Policy this publication provides a catalog of security and privacy controls for information systems and organizations to. Access to assets and associated facilities is limited to authorized users, processes, or devices. access control is a data security process that enables organizations to manage who is authorized to access corporate data and. implementing an effective access control policy offers. Cyber Security Access Control Policy.
From purplesec.us
Types Of Security Controls Explained Cyber Security Access Control Policy an access control policy that addresses purpose, scope, roles, responsibilities, management. access control is a data security process that enables organizations to manage who is authorized to access corporate data and. this publication provides a catalog of security and privacy controls for information systems and organizations to. Access to assets and associated facilities is limited to authorized. Cyber Security Access Control Policy.
From dxowqtmtn.blob.core.windows.net
Security Access Control Cable at Amber Martin blog Cyber Security Access Control Policy implementing an effective access control policy offers several key benefits: Access to assets and associated facilities is limited to authorized users, processes, or devices. this publication provides a catalog of security and privacy controls for information systems and organizations to. an access control policy that addresses purpose, scope, roles, responsibilities, management. access control is a data. Cyber Security Access Control Policy.
From templatelab.com
42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab Cyber Security Access Control Policy access control is a data security process that enables organizations to manage who is authorized to access corporate data and. Access to assets and associated facilities is limited to authorized users, processes, or devices. implementing an effective access control policy offers several key benefits: an access control policy that addresses purpose, scope, roles, responsibilities, management. this. Cyber Security Access Control Policy.
From www.cm-alliance.com
Cyber Security Policy Template Cyber Security Access Control Policy access control is a data security process that enables organizations to manage who is authorized to access corporate data and. Access to assets and associated facilities is limited to authorized users, processes, or devices. implementing an effective access control policy offers several key benefits: this publication provides a catalog of security and privacy controls for information systems. Cyber Security Access Control Policy.
From templatelab.com
42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab Cyber Security Access Control Policy implementing an effective access control policy offers several key benefits: Access to assets and associated facilities is limited to authorized users, processes, or devices. an access control policy that addresses purpose, scope, roles, responsibilities, management. this publication provides a catalog of security and privacy controls for information systems and organizations to. access control is a data. Cyber Security Access Control Policy.
From ape-europe.org
Cybersecurity Frameworks — Types, Strategies, Implementation and Cyber Security Access Control Policy an access control policy that addresses purpose, scope, roles, responsibilities, management. access control is a data security process that enables organizations to manage who is authorized to access corporate data and. Access to assets and associated facilities is limited to authorized users, processes, or devices. this publication provides a catalog of security and privacy controls for information. Cyber Security Access Control Policy.
From exogefltu.blob.core.windows.net
Access Control Policy Microsoft at Mary Thornton blog Cyber Security Access Control Policy access control is a data security process that enables organizations to manage who is authorized to access corporate data and. an access control policy that addresses purpose, scope, roles, responsibilities, management. Access to assets and associated facilities is limited to authorized users, processes, or devices. this publication provides a catalog of security and privacy controls for information. Cyber Security Access Control Policy.
From cloudcheckr.com
The Best Security Tools for Cybersecurity in the Cloud Cyber Security Access Control Policy Access to assets and associated facilities is limited to authorized users, processes, or devices. this publication provides a catalog of security and privacy controls for information systems and organizations to. access control is a data security process that enables organizations to manage who is authorized to access corporate data and. implementing an effective access control policy offers. Cyber Security Access Control Policy.
From www.slideteam.net
Cyber Security Access Control Policy Icon PPT PowerPoint Cyber Security Access Control Policy Access to assets and associated facilities is limited to authorized users, processes, or devices. an access control policy that addresses purpose, scope, roles, responsibilities, management. access control is a data security process that enables organizations to manage who is authorized to access corporate data and. this publication provides a catalog of security and privacy controls for information. Cyber Security Access Control Policy.