Keycloak Authentication Backend . By integrating keycloak into your application, you can ensure that only authorized users have access to your backend services, preventing unauthorized access and potential security. I'm trying to implement authentication throughout my backend services of a microservice oriented application using keycloak and spring boot with. Oidc (build on top of oauth 2.0) is. The goal was to establish a solid. Keycloak offers a wide range of authentication and authorization capabilities, making it an ideal choice for implementing backend service authorization. Oidc and oauth 2.0 can be used with keycloak for authentication and authorization respectively. Learn how to go beyond the simple login api and enable the full force of keycloak's authentication and authorization features using the keycloak rest api. This spring security tutorial will explore how to use keycloak and spring security oauth2 module to implement authentication and authorization in a spring boot application. We explored how keycloak, as a powerful identity server, can be configured to manage authentication and authorization through oauth2 and openid connect.
from www.thomasvitale.com
This spring security tutorial will explore how to use keycloak and spring security oauth2 module to implement authentication and authorization in a spring boot application. Learn how to go beyond the simple login api and enable the full force of keycloak's authentication and authorization features using the keycloak rest api. The goal was to establish a solid. Oidc (build on top of oauth 2.0) is. Oidc and oauth 2.0 can be used with keycloak for authentication and authorization respectively. By integrating keycloak into your application, you can ensure that only authorized users have access to your backend services, preventing unauthorized access and potential security. We explored how keycloak, as a powerful identity server, can be configured to manage authentication and authorization through oauth2 and openid connect. Keycloak offers a wide range of authentication and authorization capabilities, making it an ideal choice for implementing backend service authorization. I'm trying to implement authentication throughout my backend services of a microservice oriented application using keycloak and spring boot with.
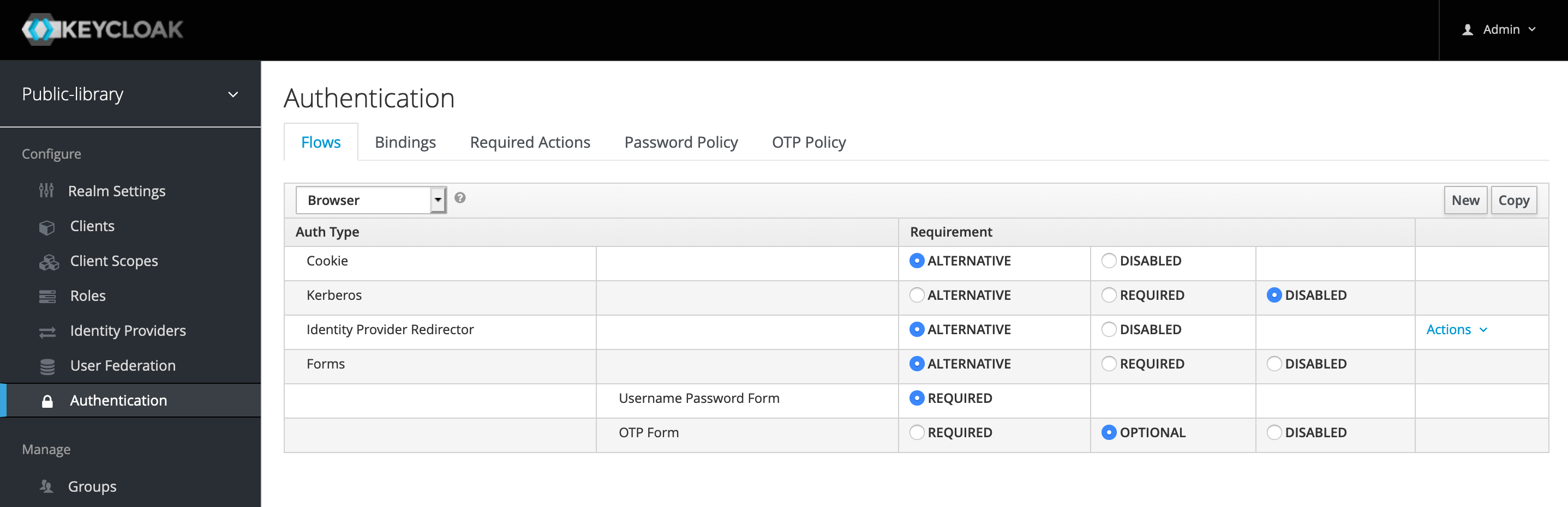
Keycloak Authentication Flows, SSO Protocols and Client Configuration
Keycloak Authentication Backend This spring security tutorial will explore how to use keycloak and spring security oauth2 module to implement authentication and authorization in a spring boot application. The goal was to establish a solid. I'm trying to implement authentication throughout my backend services of a microservice oriented application using keycloak and spring boot with. This spring security tutorial will explore how to use keycloak and spring security oauth2 module to implement authentication and authorization in a spring boot application. We explored how keycloak, as a powerful identity server, can be configured to manage authentication and authorization through oauth2 and openid connect. Learn how to go beyond the simple login api and enable the full force of keycloak's authentication and authorization features using the keycloak rest api. Oidc (build on top of oauth 2.0) is. Keycloak offers a wide range of authentication and authorization capabilities, making it an ideal choice for implementing backend service authorization. Oidc and oauth 2.0 can be used with keycloak for authentication and authorization respectively. By integrating keycloak into your application, you can ensure that only authorized users have access to your backend services, preventing unauthorized access and potential security.
From stackoverflow.com
oauth 2.0 Keycloak for backend service Stack Overflow Keycloak Authentication Backend This spring security tutorial will explore how to use keycloak and spring security oauth2 module to implement authentication and authorization in a spring boot application. Keycloak offers a wide range of authentication and authorization capabilities, making it an ideal choice for implementing backend service authorization. I'm trying to implement authentication throughout my backend services of a microservice oriented application using. Keycloak Authentication Backend.
From www.thomasvitale.com
Keycloak Authentication Flows, SSO Protocols and Client Configuration Keycloak Authentication Backend Oidc (build on top of oauth 2.0) is. This spring security tutorial will explore how to use keycloak and spring security oauth2 module to implement authentication and authorization in a spring boot application. I'm trying to implement authentication throughout my backend services of a microservice oriented application using keycloak and spring boot with. The goal was to establish a solid.. Keycloak Authentication Backend.
From blog.getambassador.io
StepbyStep Centralized Authentication for with Keycloak Keycloak Authentication Backend Keycloak offers a wide range of authentication and authorization capabilities, making it an ideal choice for implementing backend service authorization. Learn how to go beyond the simple login api and enable the full force of keycloak's authentication and authorization features using the keycloak rest api. This spring security tutorial will explore how to use keycloak and spring security oauth2 module. Keycloak Authentication Backend.
From stackoverflow.com
authentication Keycloak Authorization between services and the Keycloak Authentication Backend We explored how keycloak, as a powerful identity server, can be configured to manage authentication and authorization through oauth2 and openid connect. This spring security tutorial will explore how to use keycloak and spring security oauth2 module to implement authentication and authorization in a spring boot application. I'm trying to implement authentication throughout my backend services of a microservice oriented. Keycloak Authentication Backend.
From docs.dominodatalab.com
Keycloak Upstream IDP Trust Keycloak Authentication Backend Oidc (build on top of oauth 2.0) is. I'm trying to implement authentication throughout my backend services of a microservice oriented application using keycloak and spring boot with. Oidc and oauth 2.0 can be used with keycloak for authentication and authorization respectively. The goal was to establish a solid. By integrating keycloak into your application, you can ensure that only. Keycloak Authentication Backend.
From janus-idp.io
Enabling Keycloak Authentication in Backstage Janus Keycloak Authentication Backend I'm trying to implement authentication throughout my backend services of a microservice oriented application using keycloak and spring boot with. Oidc and oauth 2.0 can be used with keycloak for authentication and authorization respectively. We explored how keycloak, as a powerful identity server, can be configured to manage authentication and authorization through oauth2 and openid connect. By integrating keycloak into. Keycloak Authentication Backend.
From laptrinhx.com
Docker Authentication with Keycloak LaptrinhX Keycloak Authentication Backend The goal was to establish a solid. I'm trying to implement authentication throughout my backend services of a microservice oriented application using keycloak and spring boot with. Keycloak offers a wide range of authentication and authorization capabilities, making it an ideal choice for implementing backend service authorization. By integrating keycloak into your application, you can ensure that only authorized users. Keycloak Authentication Backend.
From www.springcloud.io
Unified authentication authorization platform keycloak Introduction Keycloak Authentication Backend We explored how keycloak, as a powerful identity server, can be configured to manage authentication and authorization through oauth2 and openid connect. This spring security tutorial will explore how to use keycloak and spring security oauth2 module to implement authentication and authorization in a spring boot application. I'm trying to implement authentication throughout my backend services of a microservice oriented. Keycloak Authentication Backend.
From stackoverflow.com
authentication keycloak, why does backend channels need a redirect Keycloak Authentication Backend This spring security tutorial will explore how to use keycloak and spring security oauth2 module to implement authentication and authorization in a spring boot application. I'm trying to implement authentication throughout my backend services of a microservice oriented application using keycloak and spring boot with. The goal was to establish a solid. Keycloak offers a wide range of authentication and. Keycloak Authentication Backend.
From medium.com
authn based authentication in Keycloak by Rishabh Singh Medium Keycloak Authentication Backend Learn how to go beyond the simple login api and enable the full force of keycloak's authentication and authorization features using the keycloak rest api. This spring security tutorial will explore how to use keycloak and spring security oauth2 module to implement authentication and authorization in a spring boot application. By integrating keycloak into your application, you can ensure that. Keycloak Authentication Backend.
From www.thomasvitale.com
Keycloak Basic Configuration for Authentication and Authorization Keycloak Authentication Backend By integrating keycloak into your application, you can ensure that only authorized users have access to your backend services, preventing unauthorized access and potential security. Oidc and oauth 2.0 can be used with keycloak for authentication and authorization respectively. This spring security tutorial will explore how to use keycloak and spring security oauth2 module to implement authentication and authorization in. Keycloak Authentication Backend.
From www.thomasvitale.com
Keycloak Authentication Flows, SSO Protocols and Client Configuration Keycloak Authentication Backend By integrating keycloak into your application, you can ensure that only authorized users have access to your backend services, preventing unauthorized access and potential security. Oidc (build on top of oauth 2.0) is. Learn how to go beyond the simple login api and enable the full force of keycloak's authentication and authorization features using the keycloak rest api. This spring. Keycloak Authentication Backend.
From docs.wundergraph.com
Keycloak OpenID Connect Authentication Example WunderGraph Docs Keycloak Authentication Backend This spring security tutorial will explore how to use keycloak and spring security oauth2 module to implement authentication and authorization in a spring boot application. Learn how to go beyond the simple login api and enable the full force of keycloak's authentication and authorization features using the keycloak rest api. We explored how keycloak, as a powerful identity server, can. Keycloak Authentication Backend.
From witekio.com
Authentication Management Focus On Keycloak Witekio Keycloak Authentication Backend I'm trying to implement authentication throughout my backend services of a microservice oriented application using keycloak and spring boot with. This spring security tutorial will explore how to use keycloak and spring security oauth2 module to implement authentication and authorization in a spring boot application. By integrating keycloak into your application, you can ensure that only authorized users have access. Keycloak Authentication Backend.
From baptistout.net
Passwordless authentication with Authn, Keycloak and Istio Keycloak Authentication Backend I'm trying to implement authentication throughout my backend services of a microservice oriented application using keycloak and spring boot with. Learn how to go beyond the simple login api and enable the full force of keycloak's authentication and authorization features using the keycloak rest api. By integrating keycloak into your application, you can ensure that only authorized users have access. Keycloak Authentication Backend.
From www.tremolosecurity.com
Authentication Comparing Solutions Keycloak Authentication Backend By integrating keycloak into your application, you can ensure that only authorized users have access to your backend services, preventing unauthorized access and potential security. The goal was to establish a solid. We explored how keycloak, as a powerful identity server, can be configured to manage authentication and authorization through oauth2 and openid connect. Learn how to go beyond the. Keycloak Authentication Backend.
From community.nasscom.in
RBAC for frontend and backend using Keycloak The Official Keycloak Authentication Backend I'm trying to implement authentication throughout my backend services of a microservice oriented application using keycloak and spring boot with. Oidc and oauth 2.0 can be used with keycloak for authentication and authorization respectively. This spring security tutorial will explore how to use keycloak and spring security oauth2 module to implement authentication and authorization in a spring boot application. By. Keycloak Authentication Backend.
From walkingtree.tech
Keycloak and MultiFactor Authentication (MFA) Strengthening Security Keycloak Authentication Backend We explored how keycloak, as a powerful identity server, can be configured to manage authentication and authorization through oauth2 and openid connect. This spring security tutorial will explore how to use keycloak and spring security oauth2 module to implement authentication and authorization in a spring boot application. Keycloak offers a wide range of authentication and authorization capabilities, making it an. Keycloak Authentication Backend.
From scalac.io
User Authentication with Keycloak Part 1 React frontend Keycloak Authentication Backend I'm trying to implement authentication throughout my backend services of a microservice oriented application using keycloak and spring boot with. We explored how keycloak, as a powerful identity server, can be configured to manage authentication and authorization through oauth2 and openid connect. The goal was to establish a solid. Keycloak offers a wide range of authentication and authorization capabilities, making. Keycloak Authentication Backend.
From stackoverflow.com
rest Keycloak Oauth2 Authentication Flow Stack Overflow Keycloak Authentication Backend This spring security tutorial will explore how to use keycloak and spring security oauth2 module to implement authentication and authorization in a spring boot application. Learn how to go beyond the simple login api and enable the full force of keycloak's authentication and authorization features using the keycloak rest api. The goal was to establish a solid. Keycloak offers a. Keycloak Authentication Backend.
From community.ibm.com
Extending Keycloak's authentication capabilities by integrating with Keycloak Authentication Backend By integrating keycloak into your application, you can ensure that only authorized users have access to your backend services, preventing unauthorized access and potential security. I'm trying to implement authentication throughout my backend services of a microservice oriented application using keycloak and spring boot with. Keycloak offers a wide range of authentication and authorization capabilities, making it an ideal choice. Keycloak Authentication Backend.
From walkingtree.tech
Keycloak Identity Access Management Solutions WalkingTree Technologies Keycloak Authentication Backend The goal was to establish a solid. Keycloak offers a wide range of authentication and authorization capabilities, making it an ideal choice for implementing backend service authorization. I'm trying to implement authentication throughout my backend services of a microservice oriented application using keycloak and spring boot with. Learn how to go beyond the simple login api and enable the full. Keycloak Authentication Backend.
From andrevianna-1662831931436.hashnode.dev
Understanding the Powerful Keycloak Tool Keycloak Authentication Backend We explored how keycloak, as a powerful identity server, can be configured to manage authentication and authorization through oauth2 and openid connect. Learn how to go beyond the simple login api and enable the full force of keycloak's authentication and authorization features using the keycloak rest api. I'm trying to implement authentication throughout my backend services of a microservice oriented. Keycloak Authentication Backend.
From www.thomasvitale.com
Keycloak Basic Configuration for Authentication and Authorization Keycloak Authentication Backend By integrating keycloak into your application, you can ensure that only authorized users have access to your backend services, preventing unauthorized access and potential security. We explored how keycloak, as a powerful identity server, can be configured to manage authentication and authorization through oauth2 and openid connect. Keycloak offers a wide range of authentication and authorization capabilities, making it an. Keycloak Authentication Backend.
From apisix.apache.org
Accessing APISIXDashboard from Everywhere with Keycloak Authentication Keycloak Authentication Backend The goal was to establish a solid. This spring security tutorial will explore how to use keycloak and spring security oauth2 module to implement authentication and authorization in a spring boot application. I'm trying to implement authentication throughout my backend services of a microservice oriented application using keycloak and spring boot with. Oidc and oauth 2.0 can be used with. Keycloak Authentication Backend.
From younite.us
Configuring SSO and OAuth with Keycloak Keycloak Authentication Backend By integrating keycloak into your application, you can ensure that only authorized users have access to your backend services, preventing unauthorized access and potential security. I'm trying to implement authentication throughout my backend services of a microservice oriented application using keycloak and spring boot with. This spring security tutorial will explore how to use keycloak and spring security oauth2 module. Keycloak Authentication Backend.
From www.typingdna.com
Add twofactor authentication to your web app using Keycloak & Node.js Keycloak Authentication Backend I'm trying to implement authentication throughout my backend services of a microservice oriented application using keycloak and spring boot with. Oidc and oauth 2.0 can be used with keycloak for authentication and authorization respectively. By integrating keycloak into your application, you can ensure that only authorized users have access to your backend services, preventing unauthorized access and potential security. Oidc. Keycloak Authentication Backend.
From developers.redhat.com
Keycloak Core concepts of open source identity and access management Keycloak Authentication Backend By integrating keycloak into your application, you can ensure that only authorized users have access to your backend services, preventing unauthorized access and potential security. We explored how keycloak, as a powerful identity server, can be configured to manage authentication and authorization through oauth2 and openid connect. Oidc and oauth 2.0 can be used with keycloak for authentication and authorization. Keycloak Authentication Backend.
From developers.redhat.com
Authentication and authorization using the Keycloak REST API Red Hat Keycloak Authentication Backend Oidc and oauth 2.0 can be used with keycloak for authentication and authorization respectively. I'm trying to implement authentication throughout my backend services of a microservice oriented application using keycloak and spring boot with. This spring security tutorial will explore how to use keycloak and spring security oauth2 module to implement authentication and authorization in a spring boot application. Oidc. Keycloak Authentication Backend.
From sciencegateways.org
sciencegateways Tech Blog Using Keycloak to Provide Authentication Keycloak Authentication Backend Oidc and oauth 2.0 can be used with keycloak for authentication and authorization respectively. Oidc (build on top of oauth 2.0) is. We explored how keycloak, as a powerful identity server, can be configured to manage authentication and authorization through oauth2 and openid connect. Keycloak offers a wide range of authentication and authorization capabilities, making it an ideal choice for. Keycloak Authentication Backend.
From developers.redhat.com
How to implement single signout in Keycloak with Spring Boot Red Hat Keycloak Authentication Backend Oidc (build on top of oauth 2.0) is. Keycloak offers a wide range of authentication and authorization capabilities, making it an ideal choice for implementing backend service authorization. We explored how keycloak, as a powerful identity server, can be configured to manage authentication and authorization through oauth2 and openid connect. Oidc and oauth 2.0 can be used with keycloak for. Keycloak Authentication Backend.
From www.agile-solutions.ch
Keycloak agilesolution Keycloak Authentication Backend Keycloak offers a wide range of authentication and authorization capabilities, making it an ideal choice for implementing backend service authorization. The goal was to establish a solid. Oidc and oauth 2.0 can be used with keycloak for authentication and authorization respectively. I'm trying to implement authentication throughout my backend services of a microservice oriented application using keycloak and spring boot. Keycloak Authentication Backend.
From www.janua.fr
Client Initiated Backchannel Authentication and Keycloak JANUA Keycloak Authentication Backend Keycloak offers a wide range of authentication and authorization capabilities, making it an ideal choice for implementing backend service authorization. Oidc (build on top of oauth 2.0) is. We explored how keycloak, as a powerful identity server, can be configured to manage authentication and authorization through oauth2 and openid connect. Oidc and oauth 2.0 can be used with keycloak for. Keycloak Authentication Backend.
From www.vrogue.co
Step By Step Guide Using Keycloak vrogue.co Keycloak Authentication Backend We explored how keycloak, as a powerful identity server, can be configured to manage authentication and authorization through oauth2 and openid connect. I'm trying to implement authentication throughout my backend services of a microservice oriented application using keycloak and spring boot with. This spring security tutorial will explore how to use keycloak and spring security oauth2 module to implement authentication. Keycloak Authentication Backend.
From documentation.censhare.com
Configure Keycloak with SAML Keycloak Authentication Backend I'm trying to implement authentication throughout my backend services of a microservice oriented application using keycloak and spring boot with. The goal was to establish a solid. Learn how to go beyond the simple login api and enable the full force of keycloak's authentication and authorization features using the keycloak rest api. Oidc and oauth 2.0 can be used with. Keycloak Authentication Backend.