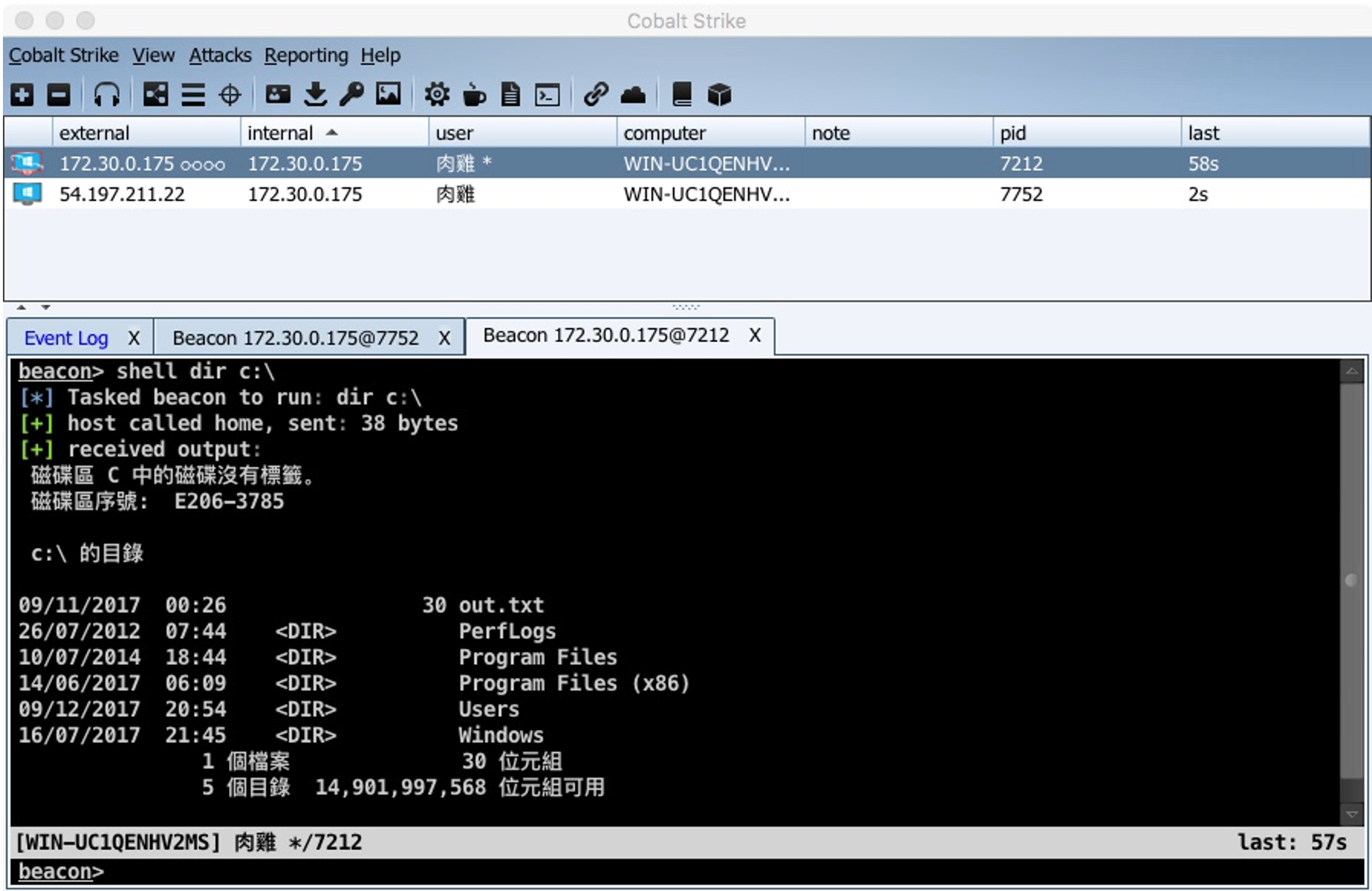
Cobalt Strike Used By Apt . One of the first cybercriminal gangs to use it extensively. While cobalt strike has long been used by apt groups. New data from sophos that cataloged attacker behavior, tools, techniques, and procedures (ttps) witnessed by its threat hunters and. Apt groups also used cobalt strike in the. In the wastedlocker ransomware attack, an advanced persistent threat (apt) group used cobalt strike to move laterally within a network. Other than that, the group relied solely on lolbins and mostly fileless methods for local execution and lateral movement. Normally used by organizations for penetration testing, cobalt strike is exploited by cybercriminals to launch attacks, says proofpoint. Cobalt strike, a threat emulation tool used by red teams, has emerged as a favored weapon for malicious criminal actors and. In 2018, the apt29 hacking group was found to use cobalt strike in their attacks on the u.s. The group used cobalt strike to.
from www.mandiant.com
The group used cobalt strike to. New data from sophos that cataloged attacker behavior, tools, techniques, and procedures (ttps) witnessed by its threat hunters and. While cobalt strike has long been used by apt groups. One of the first cybercriminal gangs to use it extensively. In 2018, the apt29 hacking group was found to use cobalt strike in their attacks on the u.s. In the wastedlocker ransomware attack, an advanced persistent threat (apt) group used cobalt strike to move laterally within a network. Apt groups also used cobalt strike in the. Other than that, the group relied solely on lolbins and mostly fileless methods for local execution and lateral movement. Normally used by organizations for penetration testing, cobalt strike is exploited by cybercriminals to launch attacks, says proofpoint. Cobalt strike, a threat emulation tool used by red teams, has emerged as a favored weapon for malicious criminal actors and.
Cobalt Strike Defining Cobalt Strike Components & BEACON
Cobalt Strike Used By Apt The group used cobalt strike to. In 2018, the apt29 hacking group was found to use cobalt strike in their attacks on the u.s. In the wastedlocker ransomware attack, an advanced persistent threat (apt) group used cobalt strike to move laterally within a network. Other than that, the group relied solely on lolbins and mostly fileless methods for local execution and lateral movement. The group used cobalt strike to. Apt groups also used cobalt strike in the. Normally used by organizations for penetration testing, cobalt strike is exploited by cybercriminals to launch attacks, says proofpoint. While cobalt strike has long been used by apt groups. New data from sophos that cataloged attacker behavior, tools, techniques, and procedures (ttps) witnessed by its threat hunters and. Cobalt strike, a threat emulation tool used by red teams, has emerged as a favored weapon for malicious criminal actors and. One of the first cybercriminal gangs to use it extensively.
From thehackernews.com
New "Earth Longzhi" APT Targets Ukraine and Asian Countries with Custom Cobalt Strike Used By Apt One of the first cybercriminal gangs to use it extensively. In the wastedlocker ransomware attack, an advanced persistent threat (apt) group used cobalt strike to move laterally within a network. Normally used by organizations for penetration testing, cobalt strike is exploited by cybercriminals to launch attacks, says proofpoint. The group used cobalt strike to. In 2018, the apt29 hacking group. Cobalt Strike Used By Apt.
From www.malwarebytes.com
Cobalt Strike, a testing tool abused by criminals Cobalt Strike Used By Apt Normally used by organizations for penetration testing, cobalt strike is exploited by cybercriminals to launch attacks, says proofpoint. New data from sophos that cataloged attacker behavior, tools, techniques, and procedures (ttps) witnessed by its threat hunters and. Cobalt strike, a threat emulation tool used by red teams, has emerged as a favored weapon for malicious criminal actors and. Apt groups. Cobalt Strike Used By Apt.
From www.proofpoint.com
Cobalt Strike 国家を後ろ盾とする APT からサイバー犯罪者までが愛用する攻撃ツール Proofpoint JP Cobalt Strike Used By Apt Cobalt strike, a threat emulation tool used by red teams, has emerged as a favored weapon for malicious criminal actors and. Normally used by organizations for penetration testing, cobalt strike is exploited by cybercriminals to launch attacks, says proofpoint. Other than that, the group relied solely on lolbins and mostly fileless methods for local execution and lateral movement. In the. Cobalt Strike Used By Apt.
From www.cobaltstrike.com
Cobalt Strike Flexibility Cobalt Strike Features Cobalt Strike Used By Apt Apt groups also used cobalt strike in the. In the wastedlocker ransomware attack, an advanced persistent threat (apt) group used cobalt strike to move laterally within a network. Cobalt strike, a threat emulation tool used by red teams, has emerged as a favored weapon for malicious criminal actors and. One of the first cybercriminal gangs to use it extensively. Normally. Cobalt Strike Used By Apt.
From www.proofpoint.com
Cobalt Strike herramienta favorita desde APT a crimeware Proofpoint ES Cobalt Strike Used By Apt In the wastedlocker ransomware attack, an advanced persistent threat (apt) group used cobalt strike to move laterally within a network. Cobalt strike, a threat emulation tool used by red teams, has emerged as a favored weapon for malicious criminal actors and. In 2018, the apt29 hacking group was found to use cobalt strike in their attacks on the u.s. One. Cobalt Strike Used By Apt.
From github.com
GitHub AhmetHan/cobalt_strike_hunting Hunting Cobalt Strike Beacons Cobalt Strike Used By Apt Apt groups also used cobalt strike in the. In 2018, the apt29 hacking group was found to use cobalt strike in their attacks on the u.s. One of the first cybercriminal gangs to use it extensively. While cobalt strike has long been used by apt groups. New data from sophos that cataloged attacker behavior, tools, techniques, and procedures (ttps) witnessed. Cobalt Strike Used By Apt.
From elistix.com
Cobalt Strike 4.9 Launched What’s New! Cobalt Strike Used By Apt One of the first cybercriminal gangs to use it extensively. Normally used by organizations for penetration testing, cobalt strike is exploited by cybercriminals to launch attacks, says proofpoint. In the wastedlocker ransomware attack, an advanced persistent threat (apt) group used cobalt strike to move laterally within a network. The group used cobalt strike to. Apt groups also used cobalt strike. Cobalt Strike Used By Apt.
From www.mandiant.com
Cobalt Strike Defining Cobalt Strike Components & BEACON Cobalt Strike Used By Apt While cobalt strike has long been used by apt groups. In 2018, the apt29 hacking group was found to use cobalt strike in their attacks on the u.s. One of the first cybercriminal gangs to use it extensively. In the wastedlocker ransomware attack, an advanced persistent threat (apt) group used cobalt strike to move laterally within a network. The group. Cobalt Strike Used By Apt.
From blog.aabyss.cn
Cobalt Strike 4.5来啦 渊龙Sec安全团队博客为国之安全而奋斗,为信息安全而发声! Cobalt Strike Used By Apt Other than that, the group relied solely on lolbins and mostly fileless methods for local execution and lateral movement. In 2018, the apt29 hacking group was found to use cobalt strike in their attacks on the u.s. New data from sophos that cataloged attacker behavior, tools, techniques, and procedures (ttps) witnessed by its threat hunters and. Normally used by organizations. Cobalt Strike Used By Apt.
From www.gdatasoftware.com
Cobalt Strike Looking for Beacons Cobalt Strike Used By Apt New data from sophos that cataloged attacker behavior, tools, techniques, and procedures (ttps) witnessed by its threat hunters and. One of the first cybercriminal gangs to use it extensively. Cobalt strike, a threat emulation tool used by red teams, has emerged as a favored weapon for malicious criminal actors and. In 2018, the apt29 hacking group was found to use. Cobalt Strike Used By Apt.
From underdefense.com
How to Detect CobaltStrike Command & Control Communication UnderDefense Cobalt Strike Used By Apt Normally used by organizations for penetration testing, cobalt strike is exploited by cybercriminals to launch attacks, says proofpoint. One of the first cybercriminal gangs to use it extensively. Other than that, the group relied solely on lolbins and mostly fileless methods for local execution and lateral movement. Cobalt strike, a threat emulation tool used by red teams, has emerged as. Cobalt Strike Used By Apt.
From www.sidechannel.blog
Cobalt Strike Infrastructure Analysis SideChannel Tempest Cobalt Strike Used By Apt New data from sophos that cataloged attacker behavior, tools, techniques, and procedures (ttps) witnessed by its threat hunters and. In the wastedlocker ransomware attack, an advanced persistent threat (apt) group used cobalt strike to move laterally within a network. Normally used by organizations for penetration testing, cobalt strike is exploited by cybercriminals to launch attacks, says proofpoint. One of the. Cobalt Strike Used By Apt.
From www.sidechannel.blog
Cobalt Strike Infrastructure Analysis SideChannel Tempest Cobalt Strike Used By Apt Normally used by organizations for penetration testing, cobalt strike is exploited by cybercriminals to launch attacks, says proofpoint. Other than that, the group relied solely on lolbins and mostly fileless methods for local execution and lateral movement. The group used cobalt strike to. In the wastedlocker ransomware attack, an advanced persistent threat (apt) group used cobalt strike to move laterally. Cobalt Strike Used By Apt.
From www.mandiant.com
Cobalt Strike Defining Cobalt Strike Components & BEACON Cobalt Strike Used By Apt Apt groups also used cobalt strike in the. In 2018, the apt29 hacking group was found to use cobalt strike in their attacks on the u.s. The group used cobalt strike to. While cobalt strike has long been used by apt groups. Other than that, the group relied solely on lolbins and mostly fileless methods for local execution and lateral. Cobalt Strike Used By Apt.
From www.malwarebytes.com
Multistage APT attack drops Cobalt Strike using Malleable C2 feature Cobalt Strike Used By Apt The group used cobalt strike to. Cobalt strike, a threat emulation tool used by red teams, has emerged as a favored weapon for malicious criminal actors and. Apt groups also used cobalt strike in the. In the wastedlocker ransomware attack, an advanced persistent threat (apt) group used cobalt strike to move laterally within a network. Normally used by organizations for. Cobalt Strike Used By Apt.
From www.sentinelone.com
What is Cobalt Strike? A Comprehensive Guide 101 Cobalt Strike Used By Apt The group used cobalt strike to. One of the first cybercriminal gangs to use it extensively. In the wastedlocker ransomware attack, an advanced persistent threat (apt) group used cobalt strike to move laterally within a network. While cobalt strike has long been used by apt groups. Cobalt strike, a threat emulation tool used by red teams, has emerged as a. Cobalt Strike Used By Apt.
From fr.gridinsoft.com
Explication de Cobalt Strike Gridinsoft 2024 Cobalt Strike Used By Apt Cobalt strike, a threat emulation tool used by red teams, has emerged as a favored weapon for malicious criminal actors and. Other than that, the group relied solely on lolbins and mostly fileless methods for local execution and lateral movement. While cobalt strike has long been used by apt groups. In the wastedlocker ransomware attack, an advanced persistent threat (apt). Cobalt Strike Used By Apt.
From live.paloaltonetworks.com
Cobalt Strike Attack Detection & Defense Technology Overview Palo Cobalt Strike Used By Apt One of the first cybercriminal gangs to use it extensively. Apt groups also used cobalt strike in the. In 2018, the apt29 hacking group was found to use cobalt strike in their attacks on the u.s. Cobalt strike, a threat emulation tool used by red teams, has emerged as a favored weapon for malicious criminal actors and. Other than that,. Cobalt Strike Used By Apt.
From www.mandiant.com
Cobalt Strike Defining Cobalt Strike Components & BEACON Cobalt Strike Used By Apt In 2018, the apt29 hacking group was found to use cobalt strike in their attacks on the u.s. Normally used by organizations for penetration testing, cobalt strike is exploited by cybercriminals to launch attacks, says proofpoint. Other than that, the group relied solely on lolbins and mostly fileless methods for local execution and lateral movement. New data from sophos that. Cobalt Strike Used By Apt.
From vastnational.weebly.com
Cobalt strike beacon persistence vastnational Cobalt Strike Used By Apt While cobalt strike has long been used by apt groups. Apt groups also used cobalt strike in the. In the wastedlocker ransomware attack, an advanced persistent threat (apt) group used cobalt strike to move laterally within a network. The group used cobalt strike to. Normally used by organizations for penetration testing, cobalt strike is exploited by cybercriminals to launch attacks,. Cobalt Strike Used By Apt.
From likosergo.weebly.com
How to detect cobalt strike beacon likosergo Cobalt Strike Used By Apt In 2018, the apt29 hacking group was found to use cobalt strike in their attacks on the u.s. Normally used by organizations for penetration testing, cobalt strike is exploited by cybercriminals to launch attacks, says proofpoint. Apt groups also used cobalt strike in the. One of the first cybercriminal gangs to use it extensively. New data from sophos that cataloged. Cobalt Strike Used By Apt.
From www.sekoia.io
How to hunt and detect Cobalt Strike ? SEKOIA.IO Cobalt Strike Used By Apt The group used cobalt strike to. One of the first cybercriminal gangs to use it extensively. In 2018, the apt29 hacking group was found to use cobalt strike in their attacks on the u.s. Apt groups also used cobalt strike in the. New data from sophos that cataloged attacker behavior, tools, techniques, and procedures (ttps) witnessed by its threat hunters. Cobalt Strike Used By Apt.
From lasopacap575.weebly.com
How to install cobalt strike lasopacap Cobalt Strike Used By Apt New data from sophos that cataloged attacker behavior, tools, techniques, and procedures (ttps) witnessed by its threat hunters and. While cobalt strike has long been used by apt groups. Apt groups also used cobalt strike in the. In the wastedlocker ransomware attack, an advanced persistent threat (apt) group used cobalt strike to move laterally within a network. One of the. Cobalt Strike Used By Apt.
From www.proofpoint.com
Cobalt Strike l'outil apprécié des APT et cybercriminels Proofpoint FR Cobalt Strike Used By Apt The group used cobalt strike to. In 2018, the apt29 hacking group was found to use cobalt strike in their attacks on the u.s. While cobalt strike has long been used by apt groups. In the wastedlocker ransomware attack, an advanced persistent threat (apt) group used cobalt strike to move laterally within a network. Other than that, the group relied. Cobalt Strike Used By Apt.
From thedfirreport.com
Cobalt Strike, a Defender's Guide Cobalt Strike Used By Apt One of the first cybercriminal gangs to use it extensively. The group used cobalt strike to. New data from sophos that cataloged attacker behavior, tools, techniques, and procedures (ttps) witnessed by its threat hunters and. Apt groups also used cobalt strike in the. Normally used by organizations for penetration testing, cobalt strike is exploited by cybercriminals to launch attacks, says. Cobalt Strike Used By Apt.
From any.run
Cobalt Strike Malware Analysis, Overview by ANY.RUN Cobalt Strike Used By Apt Apt groups also used cobalt strike in the. While cobalt strike has long been used by apt groups. One of the first cybercriminal gangs to use it extensively. In 2018, the apt29 hacking group was found to use cobalt strike in their attacks on the u.s. Normally used by organizations for penetration testing, cobalt strike is exploited by cybercriminals to. Cobalt Strike Used By Apt.
From www.e-spincorp.com
Cobalt Strike product overview ESPIN Group Cobalt Strike Used By Apt In the wastedlocker ransomware attack, an advanced persistent threat (apt) group used cobalt strike to move laterally within a network. In 2018, the apt29 hacking group was found to use cobalt strike in their attacks on the u.s. Other than that, the group relied solely on lolbins and mostly fileless methods for local execution and lateral movement. One of the. Cobalt Strike Used By Apt.
From www.youtube.com
Cobalt Strike Malware Analysis Summary Testing Tool Cobalt Strike Used By Apt Normally used by organizations for penetration testing, cobalt strike is exploited by cybercriminals to launch attacks, says proofpoint. New data from sophos that cataloged attacker behavior, tools, techniques, and procedures (ttps) witnessed by its threat hunters and. In 2018, the apt29 hacking group was found to use cobalt strike in their attacks on the u.s. The group used cobalt strike. Cobalt Strike Used By Apt.
From www.cioaxis.com
Google Strengents Cobalt Strike to Make it Harder for Attackers CIO AXIS Cobalt Strike Used By Apt Cobalt strike, a threat emulation tool used by red teams, has emerged as a favored weapon for malicious criminal actors and. The group used cobalt strike to. Apt groups also used cobalt strike in the. Other than that, the group relied solely on lolbins and mostly fileless methods for local execution and lateral movement. New data from sophos that cataloged. Cobalt Strike Used By Apt.
From threatmon.io
13 Organizations Targeted by ChineseLinked APT41 and a New Wave of Cobalt Strike Used By Apt While cobalt strike has long been used by apt groups. Other than that, the group relied solely on lolbins and mostly fileless methods for local execution and lateral movement. Cobalt strike, a threat emulation tool used by red teams, has emerged as a favored weapon for malicious criminal actors and. Apt groups also used cobalt strike in the. In 2018,. Cobalt Strike Used By Apt.
From howtofix.guide
Cobalt Strike Analysis — Is Cobalt Strike Malware? Cobalt Strike Used By Apt Cobalt strike, a threat emulation tool used by red teams, has emerged as a favored weapon for malicious criminal actors and. Apt groups also used cobalt strike in the. Other than that, the group relied solely on lolbins and mostly fileless methods for local execution and lateral movement. While cobalt strike has long been used by apt groups. The group. Cobalt Strike Used By Apt.
From sourceforge.net
Cobalt Strike Reviews and Pricing 2024 Cobalt Strike Used By Apt Cobalt strike, a threat emulation tool used by red teams, has emerged as a favored weapon for malicious criminal actors and. Normally used by organizations for penetration testing, cobalt strike is exploited by cybercriminals to launch attacks, says proofpoint. Other than that, the group relied solely on lolbins and mostly fileless methods for local execution and lateral movement. While cobalt. Cobalt Strike Used By Apt.
From www.youtube.com
Detecting Cobalt Strike Attacks using the NetWitness Platform YouTube Cobalt Strike Used By Apt In 2018, the apt29 hacking group was found to use cobalt strike in their attacks on the u.s. Other than that, the group relied solely on lolbins and mostly fileless methods for local execution and lateral movement. Apt groups also used cobalt strike in the. Cobalt strike, a threat emulation tool used by red teams, has emerged as a favored. Cobalt Strike Used By Apt.
From blogs.quickheal.com
Cobalt Strike 2021 Analysis of Malicious PowerShell Attack Framework Cobalt Strike Used By Apt In the wastedlocker ransomware attack, an advanced persistent threat (apt) group used cobalt strike to move laterally within a network. While cobalt strike has long been used by apt groups. In 2018, the apt29 hacking group was found to use cobalt strike in their attacks on the u.s. Other than that, the group relied solely on lolbins and mostly fileless. Cobalt Strike Used By Apt.
From community.sophos.com
Detecting Cobalt Strike Announcements Sophos NDR Sophos Community Cobalt Strike Used By Apt New data from sophos that cataloged attacker behavior, tools, techniques, and procedures (ttps) witnessed by its threat hunters and. While cobalt strike has long been used by apt groups. Normally used by organizations for penetration testing, cobalt strike is exploited by cybercriminals to launch attacks, says proofpoint. In 2018, the apt29 hacking group was found to use cobalt strike in. Cobalt Strike Used By Apt.