Onion Encryption Layers . Implementation of onion routing allows each layer to be decrypted at each relay, revealing the next relay It's a digital delicacy where. Directory server periodically uploads the list of nodes that are available for relaying data. Messages are encapsulated in layers of encryption, comparable to the layers of an onion. Inside the tor network are.onion sites, or ‘hidden services’. Onion routing is a technique that encrypts data in multiple layers to protect online anonymity and privacy. Client selects three nodes from this list. Tor facilitates anonymized browsing by allowing traffic to pass onto or through the network through nodes that only know the immediately preceding and following node in a relay.
from slideplayer.com
Inside the tor network are.onion sites, or ‘hidden services’. Messages are encapsulated in layers of encryption, comparable to the layers of an onion. Directory server periodically uploads the list of nodes that are available for relaying data. Tor facilitates anonymized browsing by allowing traffic to pass onto or through the network through nodes that only know the immediately preceding and following node in a relay. Implementation of onion routing allows each layer to be decrypted at each relay, revealing the next relay It's a digital delicacy where. Onion routing is a technique that encrypts data in multiple layers to protect online anonymity and privacy. Client selects three nodes from this list.
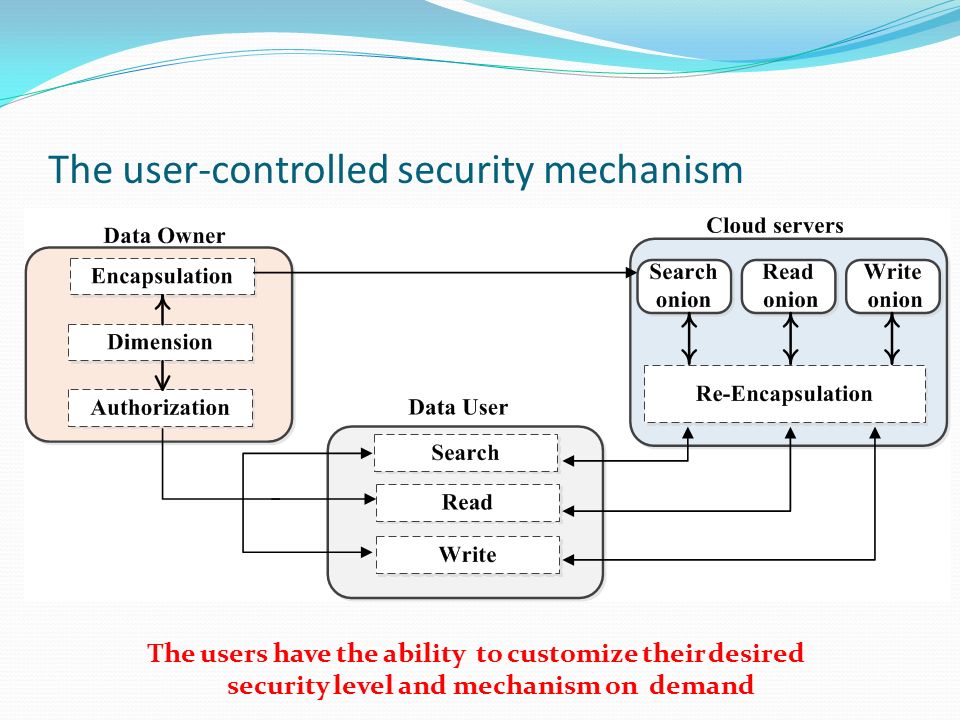
HPCC 2015, August , New York, USA Wei Chang c Joint work with Qin Liu a
Onion Encryption Layers Directory server periodically uploads the list of nodes that are available for relaying data. It's a digital delicacy where. Onion routing is a technique that encrypts data in multiple layers to protect online anonymity and privacy. Implementation of onion routing allows each layer to be decrypted at each relay, revealing the next relay Client selects three nodes from this list. Messages are encapsulated in layers of encryption, comparable to the layers of an onion. Directory server periodically uploads the list of nodes that are available for relaying data. Inside the tor network are.onion sites, or ‘hidden services’. Tor facilitates anonymized browsing by allowing traffic to pass onto or through the network through nodes that only know the immediately preceding and following node in a relay.
From slideplayer.com
Anonymous Communication ppt download Onion Encryption Layers Client selects three nodes from this list. Inside the tor network are.onion sites, or ‘hidden services’. Implementation of onion routing allows each layer to be decrypted at each relay, revealing the next relay Messages are encapsulated in layers of encryption, comparable to the layers of an onion. Tor facilitates anonymized browsing by allowing traffic to pass onto or through the. Onion Encryption Layers.
From www.collidu.com
Onion Diagram 6 Stages PowerPoint and Google Slides Template PPT Slides Onion Encryption Layers Tor facilitates anonymized browsing by allowing traffic to pass onto or through the network through nodes that only know the immediately preceding and following node in a relay. Implementation of onion routing allows each layer to be decrypted at each relay, revealing the next relay Client selects three nodes from this list. It's a digital delicacy where. Messages are encapsulated. Onion Encryption Layers.
From www.researchgate.net
“Onion layer” model suggesting emotions occurring at multiple nested Onion Encryption Layers Inside the tor network are.onion sites, or ‘hidden services’. Directory server periodically uploads the list of nodes that are available for relaying data. Client selects three nodes from this list. It's a digital delicacy where. Onion routing is a technique that encrypts data in multiple layers to protect online anonymity and privacy. Messages are encapsulated in layers of encryption, comparable. Onion Encryption Layers.
From www.researchgate.net
Encryption options in the different OSI layers over optical networks Onion Encryption Layers Messages are encapsulated in layers of encryption, comparable to the layers of an onion. Onion routing is a technique that encrypts data in multiple layers to protect online anonymity and privacy. Inside the tor network are.onion sites, or ‘hidden services’. It's a digital delicacy where. Directory server periodically uploads the list of nodes that are available for relaying data. Tor. Onion Encryption Layers.
From www.technadu.com
OnionCrypter Uses Three Individual Layers of Encryption TechNadu Onion Encryption Layers Implementation of onion routing allows each layer to be decrypted at each relay, revealing the next relay Onion routing is a technique that encrypts data in multiple layers to protect online anonymity and privacy. Tor facilitates anonymized browsing by allowing traffic to pass onto or through the network through nodes that only know the immediately preceding and following node in. Onion Encryption Layers.
From www.pandasecurity.com
The Secrets of the Deep Panda Security Onion Encryption Layers Client selects three nodes from this list. Inside the tor network are.onion sites, or ‘hidden services’. Implementation of onion routing allows each layer to be decrypted at each relay, revealing the next relay Tor facilitates anonymized browsing by allowing traffic to pass onto or through the network through nodes that only know the immediately preceding and following node in a. Onion Encryption Layers.
From www.massmux.com
How TOR really works for protecting identity Bitcoin Freedom Onion Encryption Layers It's a digital delicacy where. Messages are encapsulated in layers of encryption, comparable to the layers of an onion. Onion routing is a technique that encrypts data in multiple layers to protect online anonymity and privacy. Tor facilitates anonymized browsing by allowing traffic to pass onto or through the network through nodes that only know the immediately preceding and following. Onion Encryption Layers.
From www.researchgate.net
1 Layers of an Onion SOURCE Groeschl & Doherty (2000, p.14 Onion Encryption Layers Inside the tor network are.onion sites, or ‘hidden services’. Directory server periodically uploads the list of nodes that are available for relaying data. Messages are encapsulated in layers of encryption, comparable to the layers of an onion. Onion routing is a technique that encrypts data in multiple layers to protect online anonymity and privacy. Tor facilitates anonymized browsing by allowing. Onion Encryption Layers.
From io.bikegremlin.com
TOR network and Onion routing explained BikeGremlin I/O Onion Encryption Layers It's a digital delicacy where. Client selects three nodes from this list. Tor facilitates anonymized browsing by allowing traffic to pass onto or through the network through nodes that only know the immediately preceding and following node in a relay. Directory server periodically uploads the list of nodes that are available for relaying data. Onion routing is a technique that. Onion Encryption Layers.
From slideplayer.com
HPCC 2015, August , New York, USA Wei Chang c Joint work with Qin Liu a Onion Encryption Layers Inside the tor network are.onion sites, or ‘hidden services’. It's a digital delicacy where. Tor facilitates anonymized browsing by allowing traffic to pass onto or through the network through nodes that only know the immediately preceding and following node in a relay. Implementation of onion routing allows each layer to be decrypted at each relay, revealing the next relay Onion. Onion Encryption Layers.
From slidetodoc.com
Enhancing the Bootstrapping Network in Cloudbased Onion Routing Onion Encryption Layers Onion routing is a technique that encrypts data in multiple layers to protect online anonymity and privacy. Client selects three nodes from this list. Directory server periodically uploads the list of nodes that are available for relaying data. Tor facilitates anonymized browsing by allowing traffic to pass onto or through the network through nodes that only know the immediately preceding. Onion Encryption Layers.
From www.researchgate.net
DBMS outer layer encryption and decryption Download Scientific Diagram Onion Encryption Layers Messages are encapsulated in layers of encryption, comparable to the layers of an onion. Directory server periodically uploads the list of nodes that are available for relaying data. Inside the tor network are.onion sites, or ‘hidden services’. Tor facilitates anonymized browsing by allowing traffic to pass onto or through the network through nodes that only know the immediately preceding and. Onion Encryption Layers.
From community.torproject.org
Tor Project How do Onion Services work? Onion Encryption Layers Messages are encapsulated in layers of encryption, comparable to the layers of an onion. Onion routing is a technique that encrypts data in multiple layers to protect online anonymity and privacy. Client selects three nodes from this list. Implementation of onion routing allows each layer to be decrypted at each relay, revealing the next relay Inside the tor network are.onion. Onion Encryption Layers.
From www.researchgate.net
General description of the TOR protocol (left). Encryption layers Onion Encryption Layers Inside the tor network are.onion sites, or ‘hidden services’. It's a digital delicacy where. Client selects three nodes from this list. Directory server periodically uploads the list of nodes that are available for relaying data. Implementation of onion routing allows each layer to be decrypted at each relay, revealing the next relay Messages are encapsulated in layers of encryption, comparable. Onion Encryption Layers.
From www.geeksforgeeks.org
Onion Routing Onion Encryption Layers Inside the tor network are.onion sites, or ‘hidden services’. It's a digital delicacy where. Implementation of onion routing allows each layer to be decrypted at each relay, revealing the next relay Directory server periodically uploads the list of nodes that are available for relaying data. Tor facilitates anonymized browsing by allowing traffic to pass onto or through the network through. Onion Encryption Layers.
From www.infodiagram.com
Onion Layers Diagrams (PPT Template) Onion Encryption Layers Messages are encapsulated in layers of encryption, comparable to the layers of an onion. Directory server periodically uploads the list of nodes that are available for relaying data. Implementation of onion routing allows each layer to be decrypted at each relay, revealing the next relay Tor facilitates anonymized browsing by allowing traffic to pass onto or through the network through. Onion Encryption Layers.
From medium.com
An intro to the Onion Routing (TOR) by Sapphire void security Medium Onion Encryption Layers It's a digital delicacy where. Messages are encapsulated in layers of encryption, comparable to the layers of an onion. Inside the tor network are.onion sites, or ‘hidden services’. Implementation of onion routing allows each layer to be decrypted at each relay, revealing the next relay Tor facilitates anonymized browsing by allowing traffic to pass onto or through the network through. Onion Encryption Layers.
From www.youtube.com
Onion Architecture Example in CORE MVC MSSQL EF Core Onion Encryption Layers Tor facilitates anonymized browsing by allowing traffic to pass onto or through the network through nodes that only know the immediately preceding and following node in a relay. It's a digital delicacy where. Directory server periodically uploads the list of nodes that are available for relaying data. Inside the tor network are.onion sites, or ‘hidden services’. Messages are encapsulated in. Onion Encryption Layers.
From slideplayer.com
HPCC 2015, August , New York, USA Wei Chang c Joint work with Qin Liu a Onion Encryption Layers Onion routing is a technique that encrypts data in multiple layers to protect online anonymity and privacy. It's a digital delicacy where. Tor facilitates anonymized browsing by allowing traffic to pass onto or through the network through nodes that only know the immediately preceding and following node in a relay. Implementation of onion routing allows each layer to be decrypted. Onion Encryption Layers.
From www.oaktreecounselor.com
Autism Behaviors are like an onion... lots of layers... Oaktree Onion Encryption Layers It's a digital delicacy where. Inside the tor network are.onion sites, or ‘hidden services’. Messages are encapsulated in layers of encryption, comparable to the layers of an onion. Implementation of onion routing allows each layer to be decrypted at each relay, revealing the next relay Client selects three nodes from this list. Directory server periodically uploads the list of nodes. Onion Encryption Layers.
From slideplayer.com
HPCC 2015, August , New York, USA Wei Chang c Joint work with Qin Liu a Onion Encryption Layers Implementation of onion routing allows each layer to be decrypted at each relay, revealing the next relay Directory server periodically uploads the list of nodes that are available for relaying data. Messages are encapsulated in layers of encryption, comparable to the layers of an onion. Inside the tor network are.onion sites, or ‘hidden services’. Tor facilitates anonymized browsing by allowing. Onion Encryption Layers.
From inevitablescience.wixsite.com
Onion and its layers Onion Encryption Layers Implementation of onion routing allows each layer to be decrypted at each relay, revealing the next relay It's a digital delicacy where. Messages are encapsulated in layers of encryption, comparable to the layers of an onion. Directory server periodically uploads the list of nodes that are available for relaying data. Onion routing is a technique that encrypts data in multiple. Onion Encryption Layers.
From onion-encryption.gitbook.io
ONION ENCRYPTION Onion Encryption Whitepaper Onion Encryption Layers Directory server periodically uploads the list of nodes that are available for relaying data. Tor facilitates anonymized browsing by allowing traffic to pass onto or through the network through nodes that only know the immediately preceding and following node in a relay. Implementation of onion routing allows each layer to be decrypted at each relay, revealing the next relay Inside. Onion Encryption Layers.
From slideplayer.com
HPCC 2015, August , New York, USA Wei Chang c Joint work with Qin Liu a Onion Encryption Layers Tor facilitates anonymized browsing by allowing traffic to pass onto or through the network through nodes that only know the immediately preceding and following node in a relay. Onion routing is a technique that encrypts data in multiple layers to protect online anonymity and privacy. Messages are encapsulated in layers of encryption, comparable to the layers of an onion. Directory. Onion Encryption Layers.
From www.infodiagram.com
Onion diagram for three layers core Onion Encryption Layers Implementation of onion routing allows each layer to be decrypted at each relay, revealing the next relay Messages are encapsulated in layers of encryption, comparable to the layers of an onion. It's a digital delicacy where. Tor facilitates anonymized browsing by allowing traffic to pass onto or through the network through nodes that only know the immediately preceding and following. Onion Encryption Layers.
From www.researchgate.net
An example of onion encryption layers in CryptDB [12]. Download Onion Encryption Layers Directory server periodically uploads the list of nodes that are available for relaying data. Inside the tor network are.onion sites, or ‘hidden services’. Tor facilitates anonymized browsing by allowing traffic to pass onto or through the network through nodes that only know the immediately preceding and following node in a relay. Messages are encapsulated in layers of encryption, comparable to. Onion Encryption Layers.
From slideplayer.com
1 Dissent Accountable Anonymous Group Communication Bryan Ford Joan Onion Encryption Layers Implementation of onion routing allows each layer to be decrypted at each relay, revealing the next relay Directory server periodically uploads the list of nodes that are available for relaying data. Onion routing is a technique that encrypts data in multiple layers to protect online anonymity and privacy. Tor facilitates anonymized browsing by allowing traffic to pass onto or through. Onion Encryption Layers.
From slideplayer.com
Dr. Genevieve Bartlett USC/ISI ppt download Onion Encryption Layers Messages are encapsulated in layers of encryption, comparable to the layers of an onion. Tor facilitates anonymized browsing by allowing traffic to pass onto or through the network through nodes that only know the immediately preceding and following node in a relay. Inside the tor network are.onion sites, or ‘hidden services’. Directory server periodically uploads the list of nodes that. Onion Encryption Layers.
From www.researchgate.net
2 The Research Onion Layers Download Scientific Diagram Onion Encryption Layers Onion routing is a technique that encrypts data in multiple layers to protect online anonymity and privacy. Client selects three nodes from this list. Tor facilitates anonymized browsing by allowing traffic to pass onto or through the network through nodes that only know the immediately preceding and following node in a relay. Implementation of onion routing allows each layer to. Onion Encryption Layers.
From slideplayer.com
Anonymity Modified from Christo Wilson, Levente Buttyan, Michael K Onion Encryption Layers Messages are encapsulated in layers of encryption, comparable to the layers of an onion. Directory server periodically uploads the list of nodes that are available for relaying data. Implementation of onion routing allows each layer to be decrypted at each relay, revealing the next relay Inside the tor network are.onion sites, or ‘hidden services’. Client selects three nodes from this. Onion Encryption Layers.
From slideplayer.com
1 Freeriders in P2P Pricing Incentives Don Towsley UMassAmherst Onion Encryption Layers Inside the tor network are.onion sites, or ‘hidden services’. Client selects three nodes from this list. Onion routing is a technique that encrypts data in multiple layers to protect online anonymity and privacy. Messages are encapsulated in layers of encryption, comparable to the layers of an onion. Implementation of onion routing allows each layer to be decrypted at each relay,. Onion Encryption Layers.
From www.researchgate.net
An example of onion encryption layers in CryptDB [12]. Download Onion Encryption Layers It's a digital delicacy where. Messages are encapsulated in layers of encryption, comparable to the layers of an onion. Implementation of onion routing allows each layer to be decrypted at each relay, revealing the next relay Directory server periodically uploads the list of nodes that are available for relaying data. Inside the tor network are.onion sites, or ‘hidden services’. Client. Onion Encryption Layers.
From www.researchgate.net
Onionencryption with cascades of mixes, as used by both push and pull Onion Encryption Layers Messages are encapsulated in layers of encryption, comparable to the layers of an onion. Implementation of onion routing allows each layer to be decrypted at each relay, revealing the next relay Inside the tor network are.onion sites, or ‘hidden services’. Directory server periodically uploads the list of nodes that are available for relaying data. It's a digital delicacy where. Tor. Onion Encryption Layers.
From au.norton.com
What is encryption? How it works + types of encryption Norton Onion Encryption Layers Inside the tor network are.onion sites, or ‘hidden services’. Onion routing is a technique that encrypts data in multiple layers to protect online anonymity and privacy. Implementation of onion routing allows each layer to be decrypted at each relay, revealing the next relay Tor facilitates anonymized browsing by allowing traffic to pass onto or through the network through nodes that. Onion Encryption Layers.
From www.slideserve.com
PPT Encryption PowerPoint Presentation, free download ID1144431 Onion Encryption Layers Tor facilitates anonymized browsing by allowing traffic to pass onto or through the network through nodes that only know the immediately preceding and following node in a relay. Inside the tor network are.onion sites, or ‘hidden services’. Messages are encapsulated in layers of encryption, comparable to the layers of an onion. Directory server periodically uploads the list of nodes that. Onion Encryption Layers.