Keycloak Auth_Time . It can overwrite and customize almost every aspect of a product or module. Keycloak is an open source identity and access management (iam) tool. Being based on keycloak authentication server, you can obtain attributes from identities and runtime environment during. Everything will be done using api calls, so keycloak's ui is not exposed to the public directly. In keycloak (kc), one can explicitly set the access token lifespan (atl) at the realm and client levels. It implements almost all standard iam protocols, including oauth 2.0, openid, and saml. One of red hat sso's strongest features is that we can access keycloak directly in many ways, whether through a simple html login form, or an api call. Learn how to go beyond the simple login api and enable the full force of keycloak's authentication and authorization features using the keycloak rest api. In the following scenario, we will generate a jwt token and then validate it. It's a solid product with a good community. Those options are not available for the id token lifespan, but kc will make it.
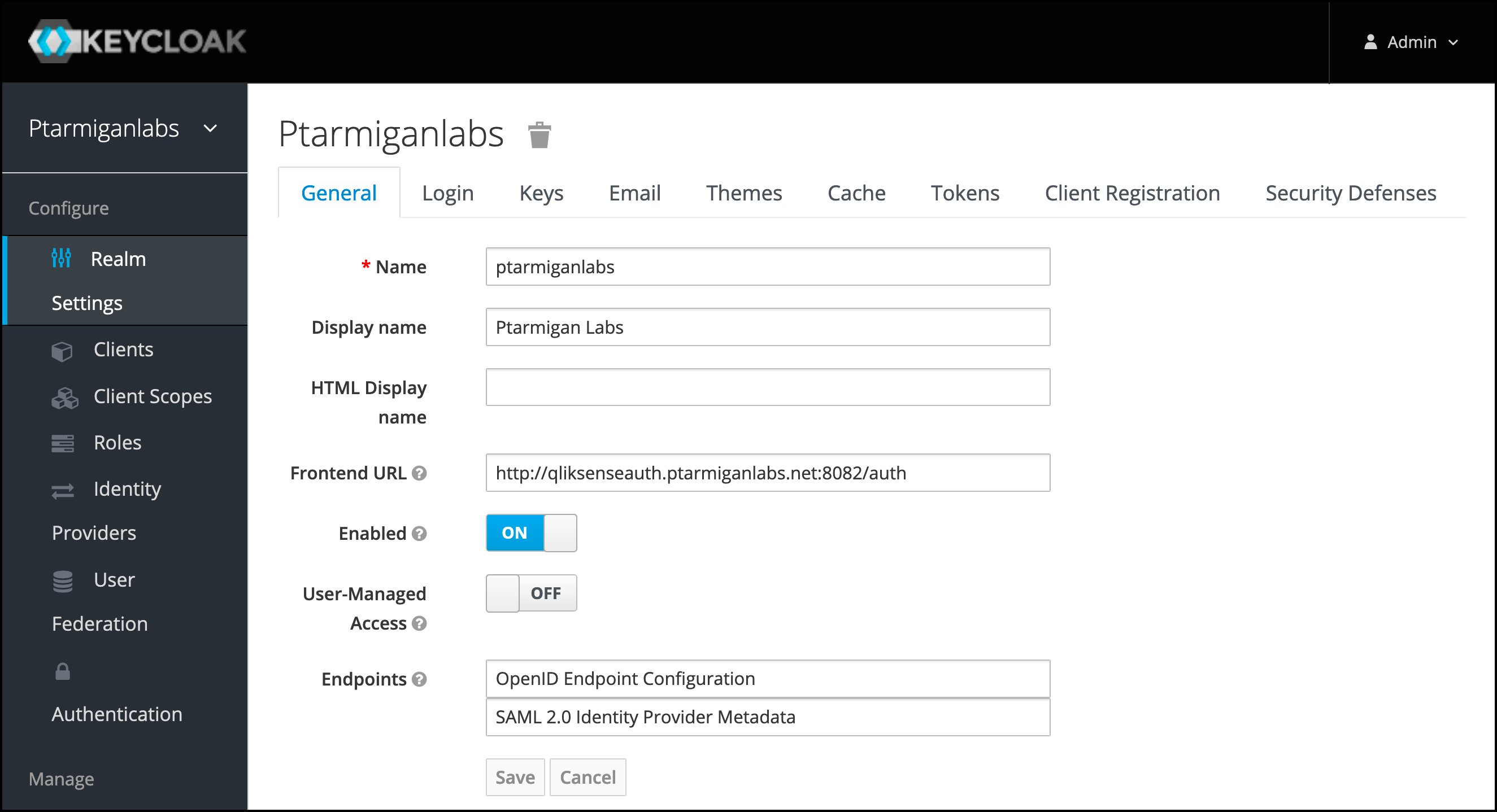
from butler-auth.ptarmiganlabs.com
It's a solid product with a good community. One of red hat sso's strongest features is that we can access keycloak directly in many ways, whether through a simple html login form, or an api call. Keycloak is an open source identity and access management (iam) tool. Learn how to go beyond the simple login api and enable the full force of keycloak's authentication and authorization features using the keycloak rest api. It can overwrite and customize almost every aspect of a product or module. Being based on keycloak authentication server, you can obtain attributes from identities and runtime environment during. Everything will be done using api calls, so keycloak's ui is not exposed to the public directly. Those options are not available for the id token lifespan, but kc will make it. In keycloak (kc), one can explicitly set the access token lifespan (atl) at the realm and client levels. In the following scenario, we will generate a jwt token and then validate it.
Keycloak Butler Auth
Keycloak Auth_Time Being based on keycloak authentication server, you can obtain attributes from identities and runtime environment during. In keycloak (kc), one can explicitly set the access token lifespan (atl) at the realm and client levels. Keycloak is an open source identity and access management (iam) tool. It's a solid product with a good community. One of red hat sso's strongest features is that we can access keycloak directly in many ways, whether through a simple html login form, or an api call. Everything will be done using api calls, so keycloak's ui is not exposed to the public directly. In the following scenario, we will generate a jwt token and then validate it. It can overwrite and customize almost every aspect of a product or module. It implements almost all standard iam protocols, including oauth 2.0, openid, and saml. Learn how to go beyond the simple login api and enable the full force of keycloak's authentication and authorization features using the keycloak rest api. Those options are not available for the id token lifespan, but kc will make it. Being based on keycloak authentication server, you can obtain attributes from identities and runtime environment during.
From neon.tech
Auth setup with Neon, Keycloak and Koyeb Neon Keycloak Auth_Time It's a solid product with a good community. It implements almost all standard iam protocols, including oauth 2.0, openid, and saml. In keycloak (kc), one can explicitly set the access token lifespan (atl) at the realm and client levels. Everything will be done using api calls, so keycloak's ui is not exposed to the public directly. It can overwrite and. Keycloak Auth_Time.
From github.com
GitHub shinyay/springkeycloakauthzserver Embedded Keycloak Server Keycloak Auth_Time Being based on keycloak authentication server, you can obtain attributes from identities and runtime environment during. Everything will be done using api calls, so keycloak's ui is not exposed to the public directly. Those options are not available for the id token lifespan, but kc will make it. Learn how to go beyond the simple login api and enable the. Keycloak Auth_Time.
From medium.com
Authentication in Angular using Keycloak by Damilare A. Adedoyin Medium Keycloak Auth_Time Those options are not available for the id token lifespan, but kc will make it. In the following scenario, we will generate a jwt token and then validate it. It can overwrite and customize almost every aspect of a product or module. Keycloak is an open source identity and access management (iam) tool. It's a solid product with a good. Keycloak Auth_Time.
From swazzy.com
User Synchronization in APS from Keycloak Swazzy Keycloak Auth_Time Those options are not available for the id token lifespan, but kc will make it. One of red hat sso's strongest features is that we can access keycloak directly in many ways, whether through a simple html login form, or an api call. It's a solid product with a good community. Being based on keycloak authentication server, you can obtain. Keycloak Auth_Time.
From www.thomasvitale.com
Keycloak Authentication Flows, SSO Protocols and Client Configuration Keycloak Auth_Time Being based on keycloak authentication server, you can obtain attributes from identities and runtime environment during. In the following scenario, we will generate a jwt token and then validate it. In keycloak (kc), one can explicitly set the access token lifespan (atl) at the realm and client levels. It can overwrite and customize almost every aspect of a product or. Keycloak Auth_Time.
From butler-auth.ptarmiganlabs.com
Keycloak Butler Auth Keycloak Auth_Time Everything will be done using api calls, so keycloak's ui is not exposed to the public directly. One of red hat sso's strongest features is that we can access keycloak directly in many ways, whether through a simple html login form, or an api call. It implements almost all standard iam protocols, including oauth 2.0, openid, and saml. It's a. Keycloak Auth_Time.
From devopsi.pl
Keycloak an introduction to easy user management Keycloak Auth_Time Everything will be done using api calls, so keycloak's ui is not exposed to the public directly. Being based on keycloak authentication server, you can obtain attributes from identities and runtime environment during. It's a solid product with a good community. Keycloak is an open source identity and access management (iam) tool. Those options are not available for the id. Keycloak Auth_Time.
From deephaven.io
Configure Keycloak for authentication Deephaven Keycloak Auth_Time It's a solid product with a good community. One of red hat sso's strongest features is that we can access keycloak directly in many ways, whether through a simple html login form, or an api call. Keycloak is an open source identity and access management (iam) tool. It implements almost all standard iam protocols, including oauth 2.0, openid, and saml.. Keycloak Auth_Time.
From neon.tech
Auth setup with Neon, Keycloak and Koyeb Neon Keycloak Auth_Time Learn how to go beyond the simple login api and enable the full force of keycloak's authentication and authorization features using the keycloak rest api. In the following scenario, we will generate a jwt token and then validate it. Keycloak is an open source identity and access management (iam) tool. Being based on keycloak authentication server, you can obtain attributes. Keycloak Auth_Time.
From witekio.com
Authentication Management Focus On Keycloak Witekio Keycloak Auth_Time Everything will be done using api calls, so keycloak's ui is not exposed to the public directly. In keycloak (kc), one can explicitly set the access token lifespan (atl) at the realm and client levels. Being based on keycloak authentication server, you can obtain attributes from identities and runtime environment during. In the following scenario, we will generate a jwt. Keycloak Auth_Time.
From blog.lazybit.ch
Harbor Keycloak Auth Keycloak Auth_Time In the following scenario, we will generate a jwt token and then validate it. One of red hat sso's strongest features is that we can access keycloak directly in many ways, whether through a simple html login form, or an api call. Everything will be done using api calls, so keycloak's ui is not exposed to the public directly. Keycloak. Keycloak Auth_Time.
From uptrace.dev
Keycloak Auth Keycloak Auth_Time Those options are not available for the id token lifespan, but kc will make it. It can overwrite and customize almost every aspect of a product or module. Everything will be done using api calls, so keycloak's ui is not exposed to the public directly. In keycloak (kc), one can explicitly set the access token lifespan (atl) at the realm. Keycloak Auth_Time.
From awesomeopensource.com
Vue Go Keycloak Auth Keycloak Auth_Time Those options are not available for the id token lifespan, but kc will make it. Being based on keycloak authentication server, you can obtain attributes from identities and runtime environment during. It can overwrite and customize almost every aspect of a product or module. It implements almost all standard iam protocols, including oauth 2.0, openid, and saml. In the following. Keycloak Auth_Time.
From www.thomasvitale.com
Keycloak Basic Configuration for Authentication and Authorization Keycloak Auth_Time It's a solid product with a good community. In the following scenario, we will generate a jwt token and then validate it. Everything will be done using api calls, so keycloak's ui is not exposed to the public directly. It can overwrite and customize almost every aspect of a product or module. Learn how to go beyond the simple login. Keycloak Auth_Time.
From www.soundsessential.com
Setting Up A Keycloak Server For Authenticating To FileMaker Part 7 Keycloak Auth_Time In the following scenario, we will generate a jwt token and then validate it. Those options are not available for the id token lifespan, but kc will make it. Learn how to go beyond the simple login api and enable the full force of keycloak's authentication and authorization features using the keycloak rest api. It can overwrite and customize almost. Keycloak Auth_Time.
From blog.lazybit.ch
Harbor Keycloak Auth Keycloak Auth_Time Those options are not available for the id token lifespan, but kc will make it. In the following scenario, we will generate a jwt token and then validate it. Learn how to go beyond the simple login api and enable the full force of keycloak's authentication and authorization features using the keycloak rest api. It implements almost all standard iam. Keycloak Auth_Time.
From docs.hedgedoc.org
SAML Keycloak HedgeDoc Keycloak Auth_Time Keycloak is an open source identity and access management (iam) tool. Those options are not available for the id token lifespan, but kc will make it. In keycloak (kc), one can explicitly set the access token lifespan (atl) at the realm and client levels. It implements almost all standard iam protocols, including oauth 2.0, openid, and saml. It can overwrite. Keycloak Auth_Time.
From github.com
GitHub micedre/keycloakauthdecorator Add keycloak user attribute Keycloak Auth_Time One of red hat sso's strongest features is that we can access keycloak directly in many ways, whether through a simple html login form, or an api call. Keycloak is an open source identity and access management (iam) tool. It implements almost all standard iam protocols, including oauth 2.0, openid, and saml. Being based on keycloak authentication server, you can. Keycloak Auth_Time.
From younite.us
Configuring SSO and OAuth with Keycloak Keycloak Auth_Time One of red hat sso's strongest features is that we can access keycloak directly in many ways, whether through a simple html login form, or an api call. Everything will be done using api calls, so keycloak's ui is not exposed to the public directly. In the following scenario, we will generate a jwt token and then validate it. It. Keycloak Auth_Time.
From uptrace.dev
Keycloak Auth Keycloak Auth_Time In keycloak (kc), one can explicitly set the access token lifespan (atl) at the realm and client levels. It's a solid product with a good community. In the following scenario, we will generate a jwt token and then validate it. Learn how to go beyond the simple login api and enable the full force of keycloak's authentication and authorization features. Keycloak Auth_Time.
From neon.tech
Auth setup with Neon, Keycloak and Koyeb Neon Keycloak Auth_Time It implements almost all standard iam protocols, including oauth 2.0, openid, and saml. Being based on keycloak authentication server, you can obtain attributes from identities and runtime environment during. It can overwrite and customize almost every aspect of a product or module. Everything will be done using api calls, so keycloak's ui is not exposed to the public directly. One. Keycloak Auth_Time.
From www.thomasvitale.com
Keycloak Authentication Flows, SSO Protocols and Client Configuration Keycloak Auth_Time It's a solid product with a good community. Being based on keycloak authentication server, you can obtain attributes from identities and runtime environment during. It implements almost all standard iam protocols, including oauth 2.0, openid, and saml. One of red hat sso's strongest features is that we can access keycloak directly in many ways, whether through a simple html login. Keycloak Auth_Time.
From docs.openfaas.com
Keycloak OpenFaaS Keycloak Auth_Time In keycloak (kc), one can explicitly set the access token lifespan (atl) at the realm and client levels. Keycloak is an open source identity and access management (iam) tool. It implements almost all standard iam protocols, including oauth 2.0, openid, and saml. In the following scenario, we will generate a jwt token and then validate it. Learn how to go. Keycloak Auth_Time.
From awesomeopensource.com
Laravel Keycloak Guard Keycloak Auth_Time In keycloak (kc), one can explicitly set the access token lifespan (atl) at the realm and client levels. It can overwrite and customize almost every aspect of a product or module. It implements almost all standard iam protocols, including oauth 2.0, openid, and saml. Those options are not available for the id token lifespan, but kc will make it. Keycloak. Keycloak Auth_Time.
From wilddiary.com
OAuth2 Authentication in Keycloak for Public Clients Keycloak Auth_Time Learn how to go beyond the simple login api and enable the full force of keycloak's authentication and authorization features using the keycloak rest api. It implements almost all standard iam protocols, including oauth 2.0, openid, and saml. Those options are not available for the id token lifespan, but kc will make it. It's a solid product with a good. Keycloak Auth_Time.
From www.youtube.com
Keycloak tutorial 2factor auth with TOTP YouTube Keycloak Auth_Time Keycloak is an open source identity and access management (iam) tool. It's a solid product with a good community. One of red hat sso's strongest features is that we can access keycloak directly in many ways, whether through a simple html login form, or an api call. Being based on keycloak authentication server, you can obtain attributes from identities and. Keycloak Auth_Time.
From www.sobyte.net
Unified User Management for with KeyCloak SoByte Keycloak Auth_Time It implements almost all standard iam protocols, including oauth 2.0, openid, and saml. Being based on keycloak authentication server, you can obtain attributes from identities and runtime environment during. In keycloak (kc), one can explicitly set the access token lifespan (atl) at the realm and client levels. Learn how to go beyond the simple login api and enable the full. Keycloak Auth_Time.
From blog.tharinduhasthika.com
Authenticating Jitsi Meetings using Keycloak Keycloak Auth_Time One of red hat sso's strongest features is that we can access keycloak directly in many ways, whether through a simple html login form, or an api call. Learn how to go beyond the simple login api and enable the full force of keycloak's authentication and authorization features using the keycloak rest api. Those options are not available for the. Keycloak Auth_Time.
From clouddocs.f5.com
Step 7 Set up authentication and authorization Keycloak Auth_Time It implements almost all standard iam protocols, including oauth 2.0, openid, and saml. It's a solid product with a good community. Everything will be done using api calls, so keycloak's ui is not exposed to the public directly. It can overwrite and customize almost every aspect of a product or module. Being based on keycloak authentication server, you can obtain. Keycloak Auth_Time.
From developers.redhat.com
Keycloak Core concepts of open source identity and access management Keycloak Auth_Time It's a solid product with a good community. Learn how to go beyond the simple login api and enable the full force of keycloak's authentication and authorization features using the keycloak rest api. It implements almost all standard iam protocols, including oauth 2.0, openid, and saml. One of red hat sso's strongest features is that we can access keycloak directly. Keycloak Auth_Time.
From community.ibm.com
Extending Keycloak's authentication capabilities by integrating with Keycloak Auth_Time In the following scenario, we will generate a jwt token and then validate it. Learn how to go beyond the simple login api and enable the full force of keycloak's authentication and authorization features using the keycloak rest api. One of red hat sso's strongest features is that we can access keycloak directly in many ways, whether through a simple. Keycloak Auth_Time.
From uptrace.dev
Keycloak Auth Keycloak Auth_Time It's a solid product with a good community. Being based on keycloak authentication server, you can obtain attributes from identities and runtime environment during. Everything will be done using api calls, so keycloak's ui is not exposed to the public directly. Learn how to go beyond the simple login api and enable the full force of keycloak's authentication and authorization. Keycloak Auth_Time.
From walkingtree.tech
Keycloak Identity Access Management Solutions WalkingTree Technologies Keycloak Auth_Time Learn how to go beyond the simple login api and enable the full force of keycloak's authentication and authorization features using the keycloak rest api. Being based on keycloak authentication server, you can obtain attributes from identities and runtime environment during. One of red hat sso's strongest features is that we can access keycloak directly in many ways, whether through. Keycloak Auth_Time.
From omnivector-solutions.github.io
Getting Started with Keycloak armasec documentation Keycloak Auth_Time Those options are not available for the id token lifespan, but kc will make it. It implements almost all standard iam protocols, including oauth 2.0, openid, and saml. In keycloak (kc), one can explicitly set the access token lifespan (atl) at the realm and client levels. In the following scenario, we will generate a jwt token and then validate it.. Keycloak Auth_Time.
From www.olivercoding.com
at home Part 5 Keycloak for authentication Oliver Coding Keycloak Auth_Time Learn how to go beyond the simple login api and enable the full force of keycloak's authentication and authorization features using the keycloak rest api. Those options are not available for the id token lifespan, but kc will make it. It implements almost all standard iam protocols, including oauth 2.0, openid, and saml. Being based on keycloak authentication server, you. Keycloak Auth_Time.