Kubernetes Dashboard Sso . Today we saw how to use azure ad authentication capabilities to leverage single sign on for kubernetes dashboards and kubectl use. Here are two ways to bypass the authentication, but use for caution. Once your ingress controller is deployed, the next step is to deploy the dashboard. This is otherwise known as basic auth. For engineers interacting with the api, kubernetes has three main authentication methods. In this series of posts we cover how to setup a comprehensive group based single sign on system for kubernetes including the kubectl cli,. The kubernetes dashboard is a powerful and simple way to work with your cluster without. There’s a page listing more authentication methods but the three below are the more common ones for user authentication.
from checkmk.com
Here are two ways to bypass the authentication, but use for caution. This is otherwise known as basic auth. The kubernetes dashboard is a powerful and simple way to work with your cluster without. In this series of posts we cover how to setup a comprehensive group based single sign on system for kubernetes including the kubectl cli,. Today we saw how to use azure ad authentication capabilities to leverage single sign on for kubernetes dashboards and kubectl use. For engineers interacting with the api, kubernetes has three main authentication methods. There’s a page listing more authentication methods but the three below are the more common ones for user authentication. Once your ingress controller is deployed, the next step is to deploy the dashboard.
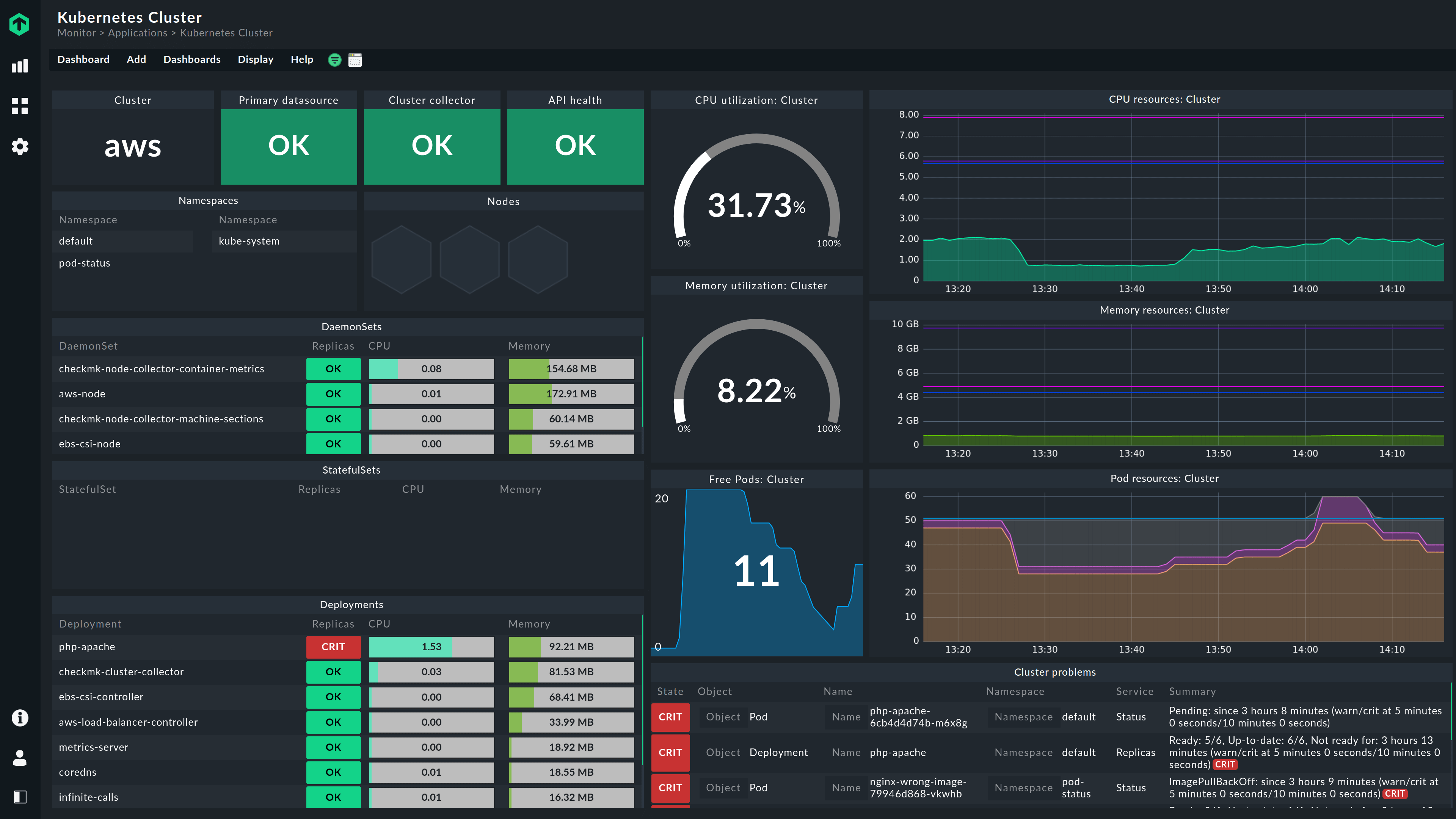
Checkmk 2.1 hybrid IT infrastructure monitoring at its best Checkmk
Kubernetes Dashboard Sso For engineers interacting with the api, kubernetes has three main authentication methods. Today we saw how to use azure ad authentication capabilities to leverage single sign on for kubernetes dashboards and kubectl use. The kubernetes dashboard is a powerful and simple way to work with your cluster without. This is otherwise known as basic auth. Here are two ways to bypass the authentication, but use for caution. Once your ingress controller is deployed, the next step is to deploy the dashboard. There’s a page listing more authentication methods but the three below are the more common ones for user authentication. For engineers interacting with the api, kubernetes has three main authentication methods. In this series of posts we cover how to setup a comprehensive group based single sign on system for kubernetes including the kubectl cli,.
From techiezhub.medium.com
To install and deploy an ingress in a cluster by Rohit Kubernetes Dashboard Sso For engineers interacting with the api, kubernetes has three main authentication methods. Today we saw how to use azure ad authentication capabilities to leverage single sign on for kubernetes dashboards and kubectl use. This is otherwise known as basic auth. Once your ingress controller is deployed, the next step is to deploy the dashboard. Here are two ways to bypass. Kubernetes Dashboard Sso.
From www.youtube.com
Dashboard Easiest way to deploy and access in 3 simple Kubernetes Dashboard Sso This is otherwise known as basic auth. Today we saw how to use azure ad authentication capabilities to leverage single sign on for kubernetes dashboards and kubectl use. Here are two ways to bypass the authentication, but use for caution. There’s a page listing more authentication methods but the three below are the more common ones for user authentication. Once. Kubernetes Dashboard Sso.
From www.elastic.co
dashboard Elastic Security Solution [8.15] Elastic Kubernetes Dashboard Sso Today we saw how to use azure ad authentication capabilities to leverage single sign on for kubernetes dashboards and kubectl use. Once your ingress controller is deployed, the next step is to deploy the dashboard. There’s a page listing more authentication methods but the three below are the more common ones for user authentication. This is otherwise known as basic. Kubernetes Dashboard Sso.
From www.youtube.com
Setting Up Dashboard YouTube Kubernetes Dashboard Sso Today we saw how to use azure ad authentication capabilities to leverage single sign on for kubernetes dashboards and kubectl use. There’s a page listing more authentication methods but the three below are the more common ones for user authentication. Here are two ways to bypass the authentication, but use for caution. The kubernetes dashboard is a powerful and simple. Kubernetes Dashboard Sso.
From komodor.com
Dashboard Quick Guide and 4 Great Alternatives Kubernetes Dashboard Sso In this series of posts we cover how to setup a comprehensive group based single sign on system for kubernetes including the kubectl cli,. Today we saw how to use azure ad authentication capabilities to leverage single sign on for kubernetes dashboards and kubectl use. Once your ingress controller is deployed, the next step is to deploy the dashboard. This. Kubernetes Dashboard Sso.
From devtron.ai
Manage with Dashboard by Devtron Kubernetes Dashboard Sso Today we saw how to use azure ad authentication capabilities to leverage single sign on for kubernetes dashboards and kubectl use. For engineers interacting with the api, kubernetes has three main authentication methods. The kubernetes dashboard is a powerful and simple way to work with your cluster without. Once your ingress controller is deployed, the next step is to deploy. Kubernetes Dashboard Sso.
From kycfeel.github.io
스스로 클러스터 구축하기 Kubernetes Dashboard Sso Once your ingress controller is deployed, the next step is to deploy the dashboard. In this series of posts we cover how to setup a comprehensive group based single sign on system for kubernetes including the kubectl cli,. The kubernetes dashboard is a powerful and simple way to work with your cluster without. Today we saw how to use azure. Kubernetes Dashboard Sso.
From thenewstack.io
Single SignOn for Dashboard Experience The New Stack Kubernetes Dashboard Sso Today we saw how to use azure ad authentication capabilities to leverage single sign on for kubernetes dashboards and kubectl use. Here are two ways to bypass the authentication, but use for caution. This is otherwise known as basic auth. The kubernetes dashboard is a powerful and simple way to work with your cluster without. There’s a page listing more. Kubernetes Dashboard Sso.
From www.mathworks.com
Monitor MATLAB Online Server Using Dashboard MATLAB & Simulink Kubernetes Dashboard Sso The kubernetes dashboard is a powerful and simple way to work with your cluster without. Today we saw how to use azure ad authentication capabilities to leverage single sign on for kubernetes dashboards and kubectl use. This is otherwise known as basic auth. In this series of posts we cover how to setup a comprehensive group based single sign on. Kubernetes Dashboard Sso.
From upcloud.com
How to deploy Dashboard quickly and easily UpCloud Kubernetes Dashboard Sso Today we saw how to use azure ad authentication capabilities to leverage single sign on for kubernetes dashboards and kubectl use. Here are two ways to bypass the authentication, but use for caution. The kubernetes dashboard is a powerful and simple way to work with your cluster without. This is otherwise known as basic auth. There’s a page listing more. Kubernetes Dashboard Sso.
From www.youtube.com
Dashboard Setup Deploy Applications using UI YouTube Kubernetes Dashboard Sso This is otherwise known as basic auth. Once your ingress controller is deployed, the next step is to deploy the dashboard. There’s a page listing more authentication methods but the three below are the more common ones for user authentication. Today we saw how to use azure ad authentication capabilities to leverage single sign on for kubernetes dashboards and kubectl. Kubernetes Dashboard Sso.
From lyz-code.github.io
Dashboard The Blue Book Kubernetes Dashboard Sso There’s a page listing more authentication methods but the three below are the more common ones for user authentication. In this series of posts we cover how to setup a comprehensive group based single sign on system for kubernetes including the kubectl cli,. The kubernetes dashboard is a powerful and simple way to work with your cluster without. This is. Kubernetes Dashboard Sso.
From daily-dev-tips.com
101 dashboard Kubernetes Dashboard Sso In this series of posts we cover how to setup a comprehensive group based single sign on system for kubernetes including the kubectl cli,. Here are two ways to bypass the authentication, but use for caution. This is otherwise known as basic auth. Once your ingress controller is deployed, the next step is to deploy the dashboard. For engineers interacting. Kubernetes Dashboard Sso.
From ikarus.sg
My Dashboard and How To Deploy Yours Kubernetes Dashboard Sso Here are two ways to bypass the authentication, but use for caution. The kubernetes dashboard is a powerful and simple way to work with your cluster without. This is otherwise known as basic auth. Today we saw how to use azure ad authentication capabilities to leverage single sign on for kubernetes dashboards and kubectl use. There’s a page listing more. Kubernetes Dashboard Sso.
From 0-14-0.docs.pomerium.com
Dashboard Pomerium Kubernetes Dashboard Sso There’s a page listing more authentication methods but the three below are the more common ones for user authentication. Once your ingress controller is deployed, the next step is to deploy the dashboard. In this series of posts we cover how to setup a comprehensive group based single sign on system for kubernetes including the kubectl cli,. Today we saw. Kubernetes Dashboard Sso.
From checkmk.com
Checkmk 2.1 hybrid IT infrastructure monitoring at its best Checkmk Kubernetes Dashboard Sso The kubernetes dashboard is a powerful and simple way to work with your cluster without. In this series of posts we cover how to setup a comprehensive group based single sign on system for kubernetes including the kubectl cli,. Once your ingress controller is deployed, the next step is to deploy the dashboard. For engineers interacting with the api, kubernetes. Kubernetes Dashboard Sso.
From ikarus.sg
My Dashboard and How To Deploy Yours Kubernetes Dashboard Sso The kubernetes dashboard is a powerful and simple way to work with your cluster without. Once your ingress controller is deployed, the next step is to deploy the dashboard. Here are two ways to bypass the authentication, but use for caution. This is otherwise known as basic auth. Today we saw how to use azure ad authentication capabilities to leverage. Kubernetes Dashboard Sso.
From devtron.ai
Manage with Dashboard by Devtron Kubernetes Dashboard Sso Once your ingress controller is deployed, the next step is to deploy the dashboard. Today we saw how to use azure ad authentication capabilities to leverage single sign on for kubernetes dashboards and kubectl use. There’s a page listing more authentication methods but the three below are the more common ones for user authentication. The kubernetes dashboard is a powerful. Kubernetes Dashboard Sso.
From sysdig.com
Unravel the hidden mysteries of your cluster with the new Kubernetes Dashboard Sso Here are two ways to bypass the authentication, but use for caution. For engineers interacting with the api, kubernetes has three main authentication methods. In this series of posts we cover how to setup a comprehensive group based single sign on system for kubernetes including the kubectl cli,. Today we saw how to use azure ad authentication capabilities to leverage. Kubernetes Dashboard Sso.
From devtron.ai
Securing Dashboard Devtron implementation? Kubernetes Dashboard Sso For engineers interacting with the api, kubernetes has three main authentication methods. There’s a page listing more authentication methods but the three below are the more common ones for user authentication. This is otherwise known as basic auth. In this series of posts we cover how to setup a comprehensive group based single sign on system for kubernetes including the. Kubernetes Dashboard Sso.
From www.marksei.com
How to install and access Kuberntes Dashboard Marksei Kubernetes Dashboard Sso There’s a page listing more authentication methods but the three below are the more common ones for user authentication. For engineers interacting with the api, kubernetes has three main authentication methods. Today we saw how to use azure ad authentication capabilities to leverage single sign on for kubernetes dashboards and kubectl use. The kubernetes dashboard is a powerful and simple. Kubernetes Dashboard Sso.
From aws.plainenglish.io
Management Dashboard Setup in AWS EKS, ELB & Route 53 AWS Kubernetes Dashboard Sso For engineers interacting with the api, kubernetes has three main authentication methods. Today we saw how to use azure ad authentication capabilities to leverage single sign on for kubernetes dashboards and kubectl use. Here are two ways to bypass the authentication, but use for caution. Once your ingress controller is deployed, the next step is to deploy the dashboard. In. Kubernetes Dashboard Sso.
From github.com
GitHub A set of modern Grafana Kubernetes Dashboard Sso Today we saw how to use azure ad authentication capabilities to leverage single sign on for kubernetes dashboards and kubectl use. In this series of posts we cover how to setup a comprehensive group based single sign on system for kubernetes including the kubectl cli,. Here are two ways to bypass the authentication, but use for caution. The kubernetes dashboard. Kubernetes Dashboard Sso.
From www.dynatrace.com
Get deep observability with the new cloud application view Kubernetes Dashboard Sso This is otherwise known as basic auth. For engineers interacting with the api, kubernetes has three main authentication methods. There’s a page listing more authentication methods but the three below are the more common ones for user authentication. Today we saw how to use azure ad authentication capabilities to leverage single sign on for kubernetes dashboards and kubectl use. Once. Kubernetes Dashboard Sso.
From k21academy.com
What is Monitoring A Comprehensive Guide Kubernetes Dashboard Sso Today we saw how to use azure ad authentication capabilities to leverage single sign on for kubernetes dashboards and kubectl use. In this series of posts we cover how to setup a comprehensive group based single sign on system for kubernetes including the kubectl cli,. The kubernetes dashboard is a powerful and simple way to work with your cluster without.. Kubernetes Dashboard Sso.
From www.percona.com
Percona Monitoring and Management 2.37 The Improved Inventory View Kubernetes Dashboard Sso Today we saw how to use azure ad authentication capabilities to leverage single sign on for kubernetes dashboards and kubectl use. Once your ingress controller is deployed, the next step is to deploy the dashboard. In this series of posts we cover how to setup a comprehensive group based single sign on system for kubernetes including the kubectl cli,. The. Kubernetes Dashboard Sso.
From www.dynatrace.com
Monitoring Tour Kubernetes Dashboard Sso There’s a page listing more authentication methods but the three below are the more common ones for user authentication. Today we saw how to use azure ad authentication capabilities to leverage single sign on for kubernetes dashboards and kubectl use. This is otherwise known as basic auth. Once your ingress controller is deployed, the next step is to deploy the. Kubernetes Dashboard Sso.
From docs.sciencelogic.com
SL1 Dashboards PowerPack Release Notes v102 Kubernetes Dashboard Sso This is otherwise known as basic auth. The kubernetes dashboard is a powerful and simple way to work with your cluster without. Once your ingress controller is deployed, the next step is to deploy the dashboard. In this series of posts we cover how to setup a comprehensive group based single sign on system for kubernetes including the kubectl cli,.. Kubernetes Dashboard Sso.
From blog.opsramp.com
Close the Visibility Gap for Modern Cloud Native Services with OpsRamp Kubernetes Dashboard Sso For engineers interacting with the api, kubernetes has three main authentication methods. Once your ingress controller is deployed, the next step is to deploy the dashboard. Here are two ways to bypass the authentication, but use for caution. Today we saw how to use azure ad authentication capabilities to leverage single sign on for kubernetes dashboards and kubectl use. In. Kubernetes Dashboard Sso.
From devtron.ai
Which Dashboard to choose Devtron vs Octant Kubernetes Dashboard Sso In this series of posts we cover how to setup a comprehensive group based single sign on system for kubernetes including the kubectl cli,. Once your ingress controller is deployed, the next step is to deploy the dashboard. There’s a page listing more authentication methods but the three below are the more common ones for user authentication. Today we saw. Kubernetes Dashboard Sso.
From www.geeksforgeeks.org
Dashboard Setup Kubernetes Dashboard Sso Here are two ways to bypass the authentication, but use for caution. Today we saw how to use azure ad authentication capabilities to leverage single sign on for kubernetes dashboards and kubectl use. This is otherwise known as basic auth. The kubernetes dashboard is a powerful and simple way to work with your cluster without. For engineers interacting with the. Kubernetes Dashboard Sso.
From grafana.com
5 key benefits of monitoring Kubernetes Dashboard Sso Once your ingress controller is deployed, the next step is to deploy the dashboard. Today we saw how to use azure ad authentication capabilities to leverage single sign on for kubernetes dashboards and kubectl use. In this series of posts we cover how to setup a comprehensive group based single sign on system for kubernetes including the kubectl cli,. For. Kubernetes Dashboard Sso.
From komodor.com
Dashboard Quick Guide and 4 Great Alternatives Kubernetes Dashboard Sso Here are two ways to bypass the authentication, but use for caution. Once your ingress controller is deployed, the next step is to deploy the dashboard. There’s a page listing more authentication methods but the three below are the more common ones for user authentication. For engineers interacting with the api, kubernetes has three main authentication methods. Today we saw. Kubernetes Dashboard Sso.
From ikarus.sg
My Dashboard and How To Deploy Yours Kubernetes Dashboard Sso In this series of posts we cover how to setup a comprehensive group based single sign on system for kubernetes including the kubectl cli,. Here are two ways to bypass the authentication, but use for caution. Once your ingress controller is deployed, the next step is to deploy the dashboard. This is otherwise known as basic auth. Today we saw. Kubernetes Dashboard Sso.
From www.aquasec.com
Dashboard Ultimate Quick Start Guide Kubernetes Dashboard Sso Here are two ways to bypass the authentication, but use for caution. Today we saw how to use azure ad authentication capabilities to leverage single sign on for kubernetes dashboards and kubectl use. There’s a page listing more authentication methods but the three below are the more common ones for user authentication. This is otherwise known as basic auth. In. Kubernetes Dashboard Sso.