Hardware-Based Security . All cyber systems are built using. Here's what we need to know. Simply put, hardware security involves protection through physical devices or operations rather than security programs such. Critical protection to help verify. Hardware is a cybersecurity risk. Learn more about hardware security features support in windows. Intel's security solutions meet specific challenges centered around three key priorities: Hardware security is vulnerability protection that comes in the form of a physical device rather than software that's installed on the hardware of a. Cyberspace does not exist in a vacuum. This report presents an effective.
from www.mdpi.com
Learn more about hardware security features support in windows. This report presents an effective. Here's what we need to know. Hardware security is vulnerability protection that comes in the form of a physical device rather than software that's installed on the hardware of a. Simply put, hardware security involves protection through physical devices or operations rather than security programs such. Hardware is a cybersecurity risk. Critical protection to help verify. Intel's security solutions meet specific challenges centered around three key priorities: Cyberspace does not exist in a vacuum. All cyber systems are built using.
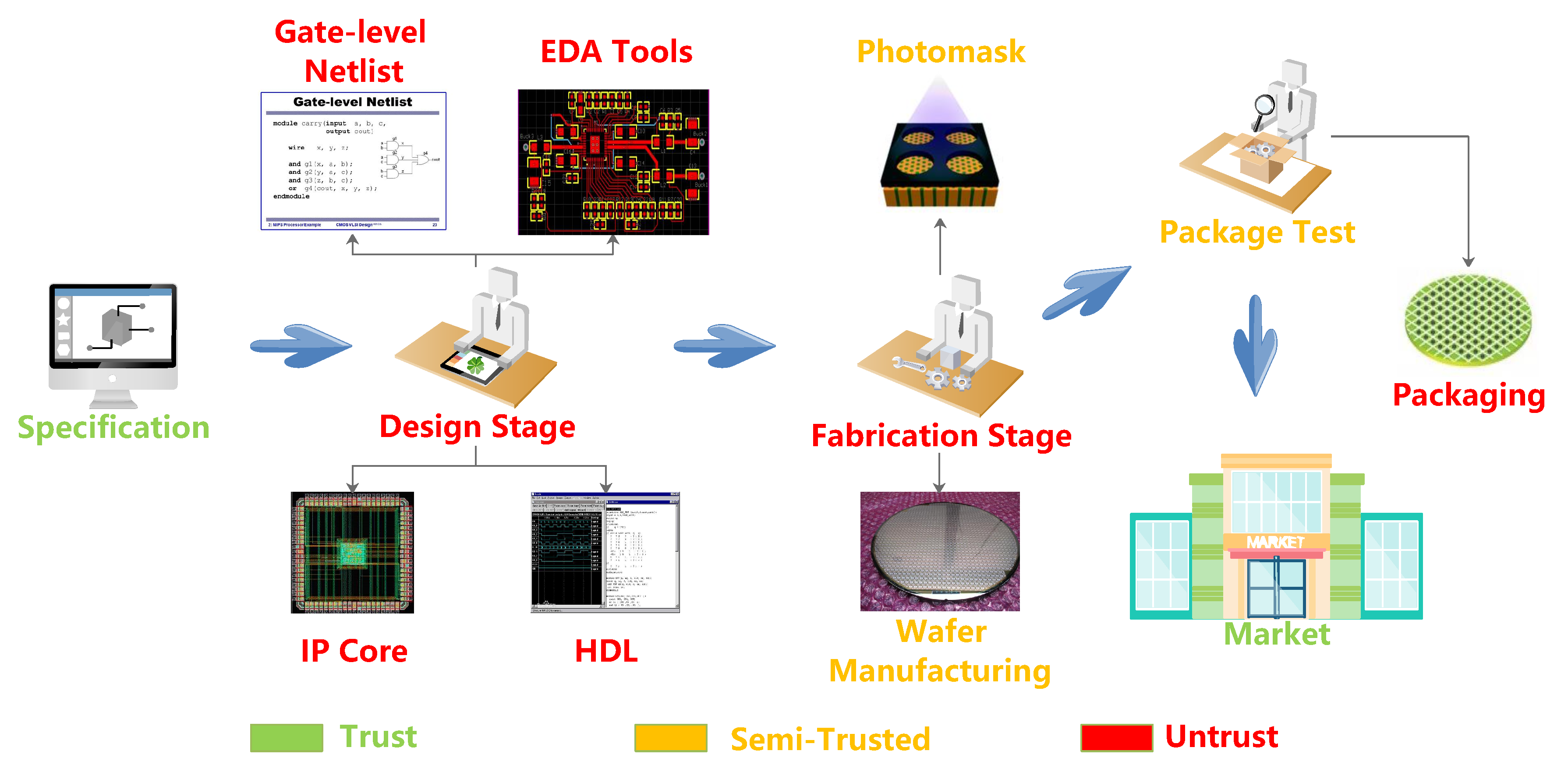
Sensors Free FullText Hardware Trojans in Chips A Survey for
Hardware-Based Security Hardware is a cybersecurity risk. Hardware security is vulnerability protection that comes in the form of a physical device rather than software that's installed on the hardware of a. Intel's security solutions meet specific challenges centered around three key priorities: Learn more about hardware security features support in windows. All cyber systems are built using. Hardware is a cybersecurity risk. Here's what we need to know. This report presents an effective. Cyberspace does not exist in a vacuum. Simply put, hardware security involves protection through physical devices or operations rather than security programs such. Critical protection to help verify.
From www.conceptdraw.com
Network Security Devices Hardware-Based Security Hardware security is vulnerability protection that comes in the form of a physical device rather than software that's installed on the hardware of a. Learn more about hardware security features support in windows. Cyberspace does not exist in a vacuum. Here's what we need to know. Critical protection to help verify. All cyber systems are built using. Simply put, hardware. Hardware-Based Security.
From www.youtube.com
Building hardware based security with a Trusted Platform Module TPM Hardware-Based Security All cyber systems are built using. Learn more about hardware security features support in windows. Hardware is a cybersecurity risk. This report presents an effective. Cyberspace does not exist in a vacuum. Intel's security solutions meet specific challenges centered around three key priorities: Here's what we need to know. Hardware security is vulnerability protection that comes in the form of. Hardware-Based Security.
From www.electronicsweekly.com
IOT security Keep hardware in mind when securing MQTT with TLS Hardware-Based Security Cyberspace does not exist in a vacuum. This report presents an effective. Learn more about hardware security features support in windows. All cyber systems are built using. Hardware security is vulnerability protection that comes in the form of a physical device rather than software that's installed on the hardware of a. Here's what we need to know. Critical protection to. Hardware-Based Security.
From resources.genetec.com
Protecting your security hardware Hardware-Based Security Critical protection to help verify. All cyber systems are built using. Hardware is a cybersecurity risk. Intel's security solutions meet specific challenges centered around three key priorities: Hardware security is vulnerability protection that comes in the form of a physical device rather than software that's installed on the hardware of a. Here's what we need to know. This report presents. Hardware-Based Security.
From www.researchgate.net
(PDF) Survey of Hardwarebased Security support for IoT/CPS Systems Hardware-Based Security Hardware security is vulnerability protection that comes in the form of a physical device rather than software that's installed on the hardware of a. Critical protection to help verify. This report presents an effective. Here's what we need to know. Intel's security solutions meet specific challenges centered around three key priorities: All cyber systems are built using. Simply put, hardware. Hardware-Based Security.
From www.eedesignit.com
Hardwarebased security solution Hardware-Based Security Hardware is a cybersecurity risk. Cyberspace does not exist in a vacuum. Hardware security is vulnerability protection that comes in the form of a physical device rather than software that's installed on the hardware of a. Intel's security solutions meet specific challenges centered around three key priorities: All cyber systems are built using. Learn more about hardware security features support. Hardware-Based Security.
From www.n-coe.in
Top 4 'Hardware Security' companies revolutionising the way security Hardware-Based Security Hardware is a cybersecurity risk. Learn more about hardware security features support in windows. Cyberspace does not exist in a vacuum. Intel's security solutions meet specific challenges centered around three key priorities: This report presents an effective. Here's what we need to know. Critical protection to help verify. All cyber systems are built using. Hardware security is vulnerability protection that. Hardware-Based Security.
From www.rambus.com
The importance of hardwarebased security solutions Hardware-Based Security Hardware security is vulnerability protection that comes in the form of a physical device rather than software that's installed on the hardware of a. Hardware is a cybersecurity risk. All cyber systems are built using. Critical protection to help verify. Intel's security solutions meet specific challenges centered around three key priorities: Here's what we need to know. Learn more about. Hardware-Based Security.
From www.asecretfire.com
Software vs Hardware Comparison Infographic Template Visme Hardware-Based Security Cyberspace does not exist in a vacuum. Intel's security solutions meet specific challenges centered around three key priorities: Simply put, hardware security involves protection through physical devices or operations rather than security programs such. All cyber systems are built using. Learn more about hardware security features support in windows. This report presents an effective. Here's what we need to know.. Hardware-Based Security.
From utimaco.com
Hardware Security Modules Utimaco Hardware-Based Security Cyberspace does not exist in a vacuum. Intel's security solutions meet specific challenges centered around three key priorities: Here's what we need to know. Critical protection to help verify. Simply put, hardware security involves protection through physical devices or operations rather than security programs such. This report presents an effective. All cyber systems are built using. Hardware is a cybersecurity. Hardware-Based Security.
From www.icalps.com
Protect your IoT device with hardwarebased Secure Elements IC'ALPS Hardware-Based Security Cyberspace does not exist in a vacuum. Hardware security is vulnerability protection that comes in the form of a physical device rather than software that's installed on the hardware of a. Intel's security solutions meet specific challenges centered around three key priorities: Learn more about hardware security features support in windows. All cyber systems are built using. This report presents. Hardware-Based Security.
From www.electronicproducts.com
Hardwarebased security taking Industry 4.0 to the next level Hardware-Based Security Simply put, hardware security involves protection through physical devices or operations rather than security programs such. All cyber systems are built using. Here's what we need to know. Learn more about hardware security features support in windows. Intel's security solutions meet specific challenges centered around three key priorities: Critical protection to help verify. Cyberspace does not exist in a vacuum.. Hardware-Based Security.
From www.etas.com
HSM firmware Functional safety starts in the hardware security module Hardware-Based Security Cyberspace does not exist in a vacuum. Hardware is a cybersecurity risk. All cyber systems are built using. Learn more about hardware security features support in windows. Critical protection to help verify. Simply put, hardware security involves protection through physical devices or operations rather than security programs such. Hardware security is vulnerability protection that comes in the form of a. Hardware-Based Security.
From www.embedded.com
Hardwarebased security emerges for AI Hardware-Based Security Hardware is a cybersecurity risk. Cyberspace does not exist in a vacuum. Intel's security solutions meet specific challenges centered around three key priorities: Here's what we need to know. Hardware security is vulnerability protection that comes in the form of a physical device rather than software that's installed on the hardware of a. Critical protection to help verify. Simply put,. Hardware-Based Security.
From www.techspot.com
Google is launching its own USBbased hardware security keys Hardware-Based Security This report presents an effective. Cyberspace does not exist in a vacuum. Critical protection to help verify. Intel's security solutions meet specific challenges centered around three key priorities: Learn more about hardware security features support in windows. Hardware is a cybersecurity risk. All cyber systems are built using. Simply put, hardware security involves protection through physical devices or operations rather. Hardware-Based Security.
From ca.msi.com
Summit E16 Flip Evo Determined to Succeed Hardware-Based Security Learn more about hardware security features support in windows. All cyber systems are built using. Critical protection to help verify. Intel's security solutions meet specific challenges centered around three key priorities: Hardware security is vulnerability protection that comes in the form of a physical device rather than software that's installed on the hardware of a. Here's what we need to. Hardware-Based Security.
From www.cysec.com
CYSEC ARCA videolibrary Hardware-Based Security Simply put, hardware security involves protection through physical devices or operations rather than security programs such. Critical protection to help verify. All cyber systems are built using. Cyberspace does not exist in a vacuum. This report presents an effective. Hardware security is vulnerability protection that comes in the form of a physical device rather than software that's installed on the. Hardware-Based Security.
From www.1rti.com
HardwareBased Security for Computers Riverside Technologies, Inc. Hardware-Based Security Intel's security solutions meet specific challenges centered around three key priorities: Hardware security is vulnerability protection that comes in the form of a physical device rather than software that's installed on the hardware of a. Hardware is a cybersecurity risk. Simply put, hardware security involves protection through physical devices or operations rather than security programs such. Critical protection to help. Hardware-Based Security.
From garantir.io
Do Hardware Security Modules (HSMs) Make Sense For Your Enterprise Hardware-Based Security All cyber systems are built using. Hardware is a cybersecurity risk. This report presents an effective. Intel's security solutions meet specific challenges centered around three key priorities: Cyberspace does not exist in a vacuum. Hardware security is vulnerability protection that comes in the form of a physical device rather than software that's installed on the hardware of a. Critical protection. Hardware-Based Security.
From cheapsslweb.com
Extensive Overview of Hardware Security Modules (HSMs) Hardware-Based Security Intel's security solutions meet specific challenges centered around three key priorities: Cyberspace does not exist in a vacuum. Hardware is a cybersecurity risk. Learn more about hardware security features support in windows. Hardware security is vulnerability protection that comes in the form of a physical device rather than software that's installed on the hardware of a. Here's what we need. Hardware-Based Security.
From www.intel.la
Hardware Security with Intel® Software Guard Extensions (Intel® SGX) Hardware-Based Security Here's what we need to know. Intel's security solutions meet specific challenges centered around three key priorities: Hardware security is vulnerability protection that comes in the form of a physical device rather than software that's installed on the hardware of a. This report presents an effective. All cyber systems are built using. Hardware is a cybersecurity risk. Cyberspace does not. Hardware-Based Security.
From www.youtube.com
Hardware Security Module (HSM) Basics Introduction To HSM YouTube Hardware-Based Security Hardware security is vulnerability protection that comes in the form of a physical device rather than software that's installed on the hardware of a. Hardware is a cybersecurity risk. Simply put, hardware security involves protection through physical devices or operations rather than security programs such. Critical protection to help verify. This report presents an effective. Intel's security solutions meet specific. Hardware-Based Security.
From deepai.org
A Survey on Hardwarebased Security Mechanisms for of Things Hardware-Based Security Simply put, hardware security involves protection through physical devices or operations rather than security programs such. This report presents an effective. Hardware is a cybersecurity risk. Here's what we need to know. Cyberspace does not exist in a vacuum. Hardware security is vulnerability protection that comes in the form of a physical device rather than software that's installed on the. Hardware-Based Security.
From teakdata.com
DIY Home Security System using Raspberry Pi Hardware-Based Security Simply put, hardware security involves protection through physical devices or operations rather than security programs such. Learn more about hardware security features support in windows. All cyber systems are built using. Here's what we need to know. Critical protection to help verify. Cyberspace does not exist in a vacuum. This report presents an effective. Hardware is a cybersecurity risk. Hardware. Hardware-Based Security.
From sotonets.com
Hardware With BuiltIn Security Could Be More Secure Than Software Hardware-Based Security Hardware security is vulnerability protection that comes in the form of a physical device rather than software that's installed on the hardware of a. Hardware is a cybersecurity risk. Intel's security solutions meet specific challenges centered around three key priorities: Here's what we need to know. Critical protection to help verify. Learn more about hardware security features support in windows.. Hardware-Based Security.
From www.infosectrain.com
Common Security Attacks in the OSI Layer Model Hardware-Based Security Hardware is a cybersecurity risk. Here's what we need to know. This report presents an effective. Cyberspace does not exist in a vacuum. Learn more about hardware security features support in windows. Hardware security is vulnerability protection that comes in the form of a physical device rather than software that's installed on the hardware of a. Simply put, hardware security. Hardware-Based Security.
From www.mdpi.com
Sensors Free FullText Hardware Trojans in Chips A Survey for Hardware-Based Security This report presents an effective. Here's what we need to know. Learn more about hardware security features support in windows. Cyberspace does not exist in a vacuum. Hardware is a cybersecurity risk. Hardware security is vulnerability protection that comes in the form of a physical device rather than software that's installed on the hardware of a. Simply put, hardware security. Hardware-Based Security.
From www.kw-engineering.com
Protecting Your Building Cybersecurity in Building Automation kW Hardware-Based Security All cyber systems are built using. Hardware is a cybersecurity risk. Learn more about hardware security features support in windows. Here's what we need to know. Simply put, hardware security involves protection through physical devices or operations rather than security programs such. Cyberspace does not exist in a vacuum. This report presents an effective. Critical protection to help verify. Hardware. Hardware-Based Security.
From m2pfintech.com
Cryptographic Keys and Hardware Security Modules An IntroductionM2P Hardware-Based Security All cyber systems are built using. Simply put, hardware security involves protection through physical devices or operations rather than security programs such. Learn more about hardware security features support in windows. This report presents an effective. Critical protection to help verify. Hardware is a cybersecurity risk. Cyberspace does not exist in a vacuum. Intel's security solutions meet specific challenges centered. Hardware-Based Security.
From iot-analytics.com
Understanding IoT Security Part 1 of 3 IoT Security Architecture Hardware-Based Security Simply put, hardware security involves protection through physical devices or operations rather than security programs such. Cyberspace does not exist in a vacuum. All cyber systems are built using. Hardware security is vulnerability protection that comes in the form of a physical device rather than software that's installed on the hardware of a. Intel's security solutions meet specific challenges centered. Hardware-Based Security.
From www.techspot.com
You can now sign into your Microsoft account using hardwarebased Hardware-Based Security Learn more about hardware security features support in windows. Intel's security solutions meet specific challenges centered around three key priorities: All cyber systems are built using. Simply put, hardware security involves protection through physical devices or operations rather than security programs such. This report presents an effective. Hardware security is vulnerability protection that comes in the form of a physical. Hardware-Based Security.
From www.axsysautomation.com
Hardware & PCB Design Services Axsys Automation Hardware-Based Security Learn more about hardware security features support in windows. All cyber systems are built using. This report presents an effective. Hardware is a cybersecurity risk. Intel's security solutions meet specific challenges centered around three key priorities: Simply put, hardware security involves protection through physical devices or operations rather than security programs such. Critical protection to help verify. Hardware security is. Hardware-Based Security.
From www.mdpi.com
Sensors Free FullText of Things Security and Solutions Hardware-Based Security Cyberspace does not exist in a vacuum. Learn more about hardware security features support in windows. Hardware is a cybersecurity risk. Critical protection to help verify. Here's what we need to know. This report presents an effective. Intel's security solutions meet specific challenges centered around three key priorities: Simply put, hardware security involves protection through physical devices or operations rather. Hardware-Based Security.
From www.computer.org
HOST 2020 on Hardware Vulnerabilities and Security Hardware-Based Security Learn more about hardware security features support in windows. Hardware is a cybersecurity risk. Intel's security solutions meet specific challenges centered around three key priorities: Hardware security is vulnerability protection that comes in the form of a physical device rather than software that's installed on the hardware of a. Here's what we need to know. This report presents an effective.. Hardware-Based Security.
From www.thesmartcityjournal.com
New hardware security device developed by researchers Hardware-Based Security Hardware security is vulnerability protection that comes in the form of a physical device rather than software that's installed on the hardware of a. Learn more about hardware security features support in windows. Intel's security solutions meet specific challenges centered around three key priorities: This report presents an effective. Hardware is a cybersecurity risk. Cyberspace does not exist in a. Hardware-Based Security.