Current Hardware- And Software-Based Cybersecurity Tools Tactics And Procedures . Ttps in cybersecurity describe how cybercriminals plan and execute attacks. The term tactics, techniques and procedures (ttp) describes the behavior of a threat actor and a structured framework for executing a cyberattack. Remove unwanted, unneeded or unexpected hardware and software from the network. Below we define the three. The widespread adoption of artificial. More than just a protective shield, these. Cybersecurity threats are becoming increasingly complex, sophisticated, malicious, well organized and well funded. Each component, named tactics, techniques, and procedures, offers insight into different. The actors can range from. At its core, it refers to physical devices explicitly crafted to defend computer systems against vulnerabilities and threats. Starting from a known baseline reduces the attack. Ttp analysis can help security teams detect and mitigate attacks by understanding the way threat actors operate.
from studyonline.ecu.edu.au
Below we define the three. Remove unwanted, unneeded or unexpected hardware and software from the network. Ttp analysis can help security teams detect and mitigate attacks by understanding the way threat actors operate. The term tactics, techniques and procedures (ttp) describes the behavior of a threat actor and a structured framework for executing a cyberattack. More than just a protective shield, these. The widespread adoption of artificial. Starting from a known baseline reduces the attack. Ttps in cybersecurity describe how cybercriminals plan and execute attacks. Each component, named tactics, techniques, and procedures, offers insight into different. The actors can range from.
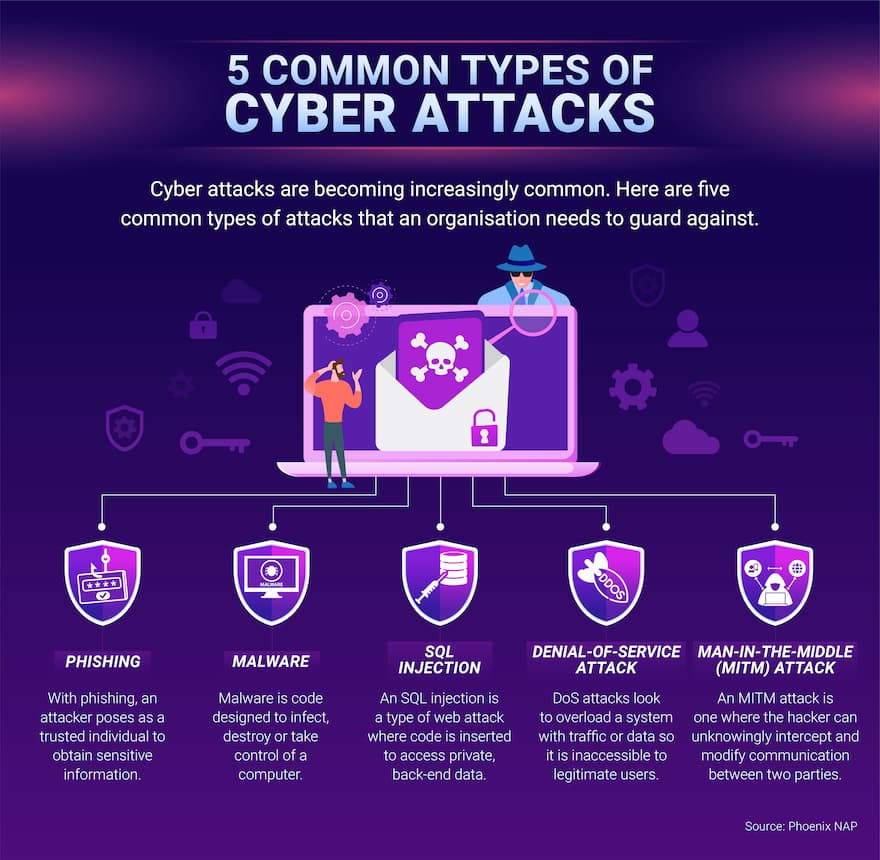
Cyber Attacks Tips for Protecting Your Organisation ECU Online
Current Hardware- And Software-Based Cybersecurity Tools Tactics And Procedures The term tactics, techniques and procedures (ttp) describes the behavior of a threat actor and a structured framework for executing a cyberattack. Ttp analysis can help security teams detect and mitigate attacks by understanding the way threat actors operate. The actors can range from. More than just a protective shield, these. The widespread adoption of artificial. Below we define the three. At its core, it refers to physical devices explicitly crafted to defend computer systems against vulnerabilities and threats. Each component, named tactics, techniques, and procedures, offers insight into different. Remove unwanted, unneeded or unexpected hardware and software from the network. The term tactics, techniques and procedures (ttp) describes the behavior of a threat actor and a structured framework for executing a cyberattack. Starting from a known baseline reduces the attack. Cybersecurity threats are becoming increasingly complex, sophisticated, malicious, well organized and well funded. Ttps in cybersecurity describe how cybercriminals plan and execute attacks.
From www.vrogue.co
The Best Techniques And Tools To Perform A Cybersecur vrogue.co Current Hardware- And Software-Based Cybersecurity Tools Tactics And Procedures More than just a protective shield, these. The term tactics, techniques and procedures (ttp) describes the behavior of a threat actor and a structured framework for executing a cyberattack. Ttp analysis can help security teams detect and mitigate attacks by understanding the way threat actors operate. The widespread adoption of artificial. Below we define the three. Ttps in cybersecurity describe. Current Hardware- And Software-Based Cybersecurity Tools Tactics And Procedures.
From www.balbix.com
Tactics, Techniques and Procedures in Cyber Security Balbix Current Hardware- And Software-Based Cybersecurity Tools Tactics And Procedures Ttps in cybersecurity describe how cybercriminals plan and execute attacks. Starting from a known baseline reduces the attack. The term tactics, techniques and procedures (ttp) describes the behavior of a threat actor and a structured framework for executing a cyberattack. Each component, named tactics, techniques, and procedures, offers insight into different. Remove unwanted, unneeded or unexpected hardware and software from. Current Hardware- And Software-Based Cybersecurity Tools Tactics And Procedures.
From spectralops.io
7 Building Blocks of an Effective Cyber Security Strategy Spectral Current Hardware- And Software-Based Cybersecurity Tools Tactics And Procedures Starting from a known baseline reduces the attack. Cybersecurity threats are becoming increasingly complex, sophisticated, malicious, well organized and well funded. Each component, named tactics, techniques, and procedures, offers insight into different. The widespread adoption of artificial. Ttp analysis can help security teams detect and mitigate attacks by understanding the way threat actors operate. More than just a protective shield,. Current Hardware- And Software-Based Cybersecurity Tools Tactics And Procedures.
From www.comparitech.com
NIST Cybersecurity Framework Guide 2024 Core, Implementation & Profile Current Hardware- And Software-Based Cybersecurity Tools Tactics And Procedures The actors can range from. The widespread adoption of artificial. Each component, named tactics, techniques, and procedures, offers insight into different. Starting from a known baseline reduces the attack. Remove unwanted, unneeded or unexpected hardware and software from the network. Ttps in cybersecurity describe how cybercriminals plan and execute attacks. Below we define the three. At its core, it refers. Current Hardware- And Software-Based Cybersecurity Tools Tactics And Procedures.
From www.slideteam.net
Top 10 Cybersecurity Dashboard Templates With Samples and Examples Current Hardware- And Software-Based Cybersecurity Tools Tactics And Procedures Below we define the three. The term tactics, techniques and procedures (ttp) describes the behavior of a threat actor and a structured framework for executing a cyberattack. At its core, it refers to physical devices explicitly crafted to defend computer systems against vulnerabilities and threats. Each component, named tactics, techniques, and procedures, offers insight into different. Starting from a known. Current Hardware- And Software-Based Cybersecurity Tools Tactics And Procedures.
From support.aiesec.org
Cyber Security Threats and Attacks AIESEC Help Center Current Hardware- And Software-Based Cybersecurity Tools Tactics And Procedures Below we define the three. Each component, named tactics, techniques, and procedures, offers insight into different. Ttp analysis can help security teams detect and mitigate attacks by understanding the way threat actors operate. At its core, it refers to physical devices explicitly crafted to defend computer systems against vulnerabilities and threats. The term tactics, techniques and procedures (ttp) describes the. Current Hardware- And Software-Based Cybersecurity Tools Tactics And Procedures.
From www.geeksforgeeks.org
10 Major Types of Enterprise CyberSecurity Tools Current Hardware- And Software-Based Cybersecurity Tools Tactics And Procedures At its core, it refers to physical devices explicitly crafted to defend computer systems against vulnerabilities and threats. Below we define the three. Remove unwanted, unneeded or unexpected hardware and software from the network. The widespread adoption of artificial. More than just a protective shield, these. Starting from a known baseline reduces the attack. Ttps in cybersecurity describe how cybercriminals. Current Hardware- And Software-Based Cybersecurity Tools Tactics And Procedures.
From www.slidegeeks.com
Cyber Security Tools And Techniques Ppt PowerPoint Presentation Styles Current Hardware- And Software-Based Cybersecurity Tools Tactics And Procedures Starting from a known baseline reduces the attack. The term tactics, techniques and procedures (ttp) describes the behavior of a threat actor and a structured framework for executing a cyberattack. Cybersecurity threats are becoming increasingly complex, sophisticated, malicious, well organized and well funded. Remove unwanted, unneeded or unexpected hardware and software from the network. Ttps in cybersecurity describe how cybercriminals. Current Hardware- And Software-Based Cybersecurity Tools Tactics And Procedures.
From data-flair.training
Top 29 Cyber Security Tools DataFlair Current Hardware- And Software-Based Cybersecurity Tools Tactics And Procedures The widespread adoption of artificial. The term tactics, techniques and procedures (ttp) describes the behavior of a threat actor and a structured framework for executing a cyberattack. Starting from a known baseline reduces the attack. Cybersecurity threats are becoming increasingly complex, sophisticated, malicious, well organized and well funded. Below we define the three. The actors can range from. At its. Current Hardware- And Software-Based Cybersecurity Tools Tactics And Procedures.
From sprinto.com
Top 16 Cyber Security tools You Must Know in 2024 Sprinto Current Hardware- And Software-Based Cybersecurity Tools Tactics And Procedures At its core, it refers to physical devices explicitly crafted to defend computer systems against vulnerabilities and threats. Below we define the three. The widespread adoption of artificial. Ttp analysis can help security teams detect and mitigate attacks by understanding the way threat actors operate. Cybersecurity threats are becoming increasingly complex, sophisticated, malicious, well organized and well funded. The actors. Current Hardware- And Software-Based Cybersecurity Tools Tactics And Procedures.
From assignmenthelp4me.com
A comprehensive study of Cyber Security and its types Current Hardware- And Software-Based Cybersecurity Tools Tactics And Procedures Below we define the three. Cybersecurity threats are becoming increasingly complex, sophisticated, malicious, well organized and well funded. Ttps in cybersecurity describe how cybercriminals plan and execute attacks. The term tactics, techniques and procedures (ttp) describes the behavior of a threat actor and a structured framework for executing a cyberattack. Each component, named tactics, techniques, and procedures, offers insight into. Current Hardware- And Software-Based Cybersecurity Tools Tactics And Procedures.
From www.insightsonindia.com
Meaning and Types of Cybersecurity Threats INSIGHTS IAS Simplifying Current Hardware- And Software-Based Cybersecurity Tools Tactics And Procedures Below we define the three. Each component, named tactics, techniques, and procedures, offers insight into different. More than just a protective shield, these. Starting from a known baseline reduces the attack. The widespread adoption of artificial. Ttps in cybersecurity describe how cybercriminals plan and execute attacks. The actors can range from. At its core, it refers to physical devices explicitly. Current Hardware- And Software-Based Cybersecurity Tools Tactics And Procedures.
From www.springboard.com
What Is Cybersecurity? A Complete Overview Guide Current Hardware- And Software-Based Cybersecurity Tools Tactics And Procedures The term tactics, techniques and procedures (ttp) describes the behavior of a threat actor and a structured framework for executing a cyberattack. Below we define the three. Starting from a known baseline reduces the attack. Ttp analysis can help security teams detect and mitigate attacks by understanding the way threat actors operate. At its core, it refers to physical devices. Current Hardware- And Software-Based Cybersecurity Tools Tactics And Procedures.
From www.nist.gov
NIST Releases Version 1.1 of its Popular Cybersecurity Framework NIST Current Hardware- And Software-Based Cybersecurity Tools Tactics And Procedures Starting from a known baseline reduces the attack. Remove unwanted, unneeded or unexpected hardware and software from the network. At its core, it refers to physical devices explicitly crafted to defend computer systems against vulnerabilities and threats. Each component, named tactics, techniques, and procedures, offers insight into different. Ttp analysis can help security teams detect and mitigate attacks by understanding. Current Hardware- And Software-Based Cybersecurity Tools Tactics And Procedures.
From ape-europe.org
Cybersecurity Frameworks — Types, Strategies, Implementation and Current Hardware- And Software-Based Cybersecurity Tools Tactics And Procedures More than just a protective shield, these. Each component, named tactics, techniques, and procedures, offers insight into different. Starting from a known baseline reduces the attack. The term tactics, techniques and procedures (ttp) describes the behavior of a threat actor and a structured framework for executing a cyberattack. Cybersecurity threats are becoming increasingly complex, sophisticated, malicious, well organized and well. Current Hardware- And Software-Based Cybersecurity Tools Tactics And Procedures.
From studyonline.ecu.edu.au
Cyber Attacks Tips for Protecting Your Organisation ECU Online Current Hardware- And Software-Based Cybersecurity Tools Tactics And Procedures Each component, named tactics, techniques, and procedures, offers insight into different. Ttps in cybersecurity describe how cybercriminals plan and execute attacks. More than just a protective shield, these. Starting from a known baseline reduces the attack. Ttp analysis can help security teams detect and mitigate attacks by understanding the way threat actors operate. Below we define the three. The actors. Current Hardware- And Software-Based Cybersecurity Tools Tactics And Procedures.
From www.secjuice.com
Defining a Security Strategy WHY Current Hardware- And Software-Based Cybersecurity Tools Tactics And Procedures The term tactics, techniques and procedures (ttp) describes the behavior of a threat actor and a structured framework for executing a cyberattack. Cybersecurity threats are becoming increasingly complex, sophisticated, malicious, well organized and well funded. Ttp analysis can help security teams detect and mitigate attacks by understanding the way threat actors operate. Starting from a known baseline reduces the attack.. Current Hardware- And Software-Based Cybersecurity Tools Tactics And Procedures.
From blog.nettitude.com
How a Remote Cybersecurity Review Can Reduce CyberRisk Nettitude Current Hardware- And Software-Based Cybersecurity Tools Tactics And Procedures At its core, it refers to physical devices explicitly crafted to defend computer systems against vulnerabilities and threats. The actors can range from. Cybersecurity threats are becoming increasingly complex, sophisticated, malicious, well organized and well funded. The widespread adoption of artificial. Ttps in cybersecurity describe how cybercriminals plan and execute attacks. The term tactics, techniques and procedures (ttp) describes the. Current Hardware- And Software-Based Cybersecurity Tools Tactics And Procedures.
From sprinto.com
Top 16 Cyber Security tools You Must Know in 2024 Sprinto Current Hardware- And Software-Based Cybersecurity Tools Tactics And Procedures Starting from a known baseline reduces the attack. More than just a protective shield, these. Remove unwanted, unneeded or unexpected hardware and software from the network. At its core, it refers to physical devices explicitly crafted to defend computer systems against vulnerabilities and threats. Each component, named tactics, techniques, and procedures, offers insight into different. Ttp analysis can help security. Current Hardware- And Software-Based Cybersecurity Tools Tactics And Procedures.
From www.ukessays.ae
Methods for Cybersecurity Current Hardware- And Software-Based Cybersecurity Tools Tactics And Procedures Below we define the three. More than just a protective shield, these. Each component, named tactics, techniques, and procedures, offers insight into different. The actors can range from. The term tactics, techniques and procedures (ttp) describes the behavior of a threat actor and a structured framework for executing a cyberattack. Ttps in cybersecurity describe how cybercriminals plan and execute attacks.. Current Hardware- And Software-Based Cybersecurity Tools Tactics And Procedures.
From www.infosectrain.com
Common Security Attacks in the OSI Layer Model Current Hardware- And Software-Based Cybersecurity Tools Tactics And Procedures Below we define the three. The widespread adoption of artificial. More than just a protective shield, these. The actors can range from. Cybersecurity threats are becoming increasingly complex, sophisticated, malicious, well organized and well funded. Remove unwanted, unneeded or unexpected hardware and software from the network. Ttps in cybersecurity describe how cybercriminals plan and execute attacks. Starting from a known. Current Hardware- And Software-Based Cybersecurity Tools Tactics And Procedures.
From justpaste.it
Top 5 Most Powerful Cyber Security Software Tools in 2020 JustPaste.it Current Hardware- And Software-Based Cybersecurity Tools Tactics And Procedures More than just a protective shield, these. Cybersecurity threats are becoming increasingly complex, sophisticated, malicious, well organized and well funded. The widespread adoption of artificial. Starting from a known baseline reduces the attack. The term tactics, techniques and procedures (ttp) describes the behavior of a threat actor and a structured framework for executing a cyberattack. At its core, it refers. Current Hardware- And Software-Based Cybersecurity Tools Tactics And Procedures.
From www.dell.com
Strengthen Security of Your Data Center with the NIST Cybersecurity Current Hardware- And Software-Based Cybersecurity Tools Tactics And Procedures At its core, it refers to physical devices explicitly crafted to defend computer systems against vulnerabilities and threats. Each component, named tactics, techniques, and procedures, offers insight into different. Remove unwanted, unneeded or unexpected hardware and software from the network. The actors can range from. Ttp analysis can help security teams detect and mitigate attacks by understanding the way threat. Current Hardware- And Software-Based Cybersecurity Tools Tactics And Procedures.
From www.hayescollege.co.uk
Cyber security and risk assessment training Current Hardware- And Software-Based Cybersecurity Tools Tactics And Procedures Starting from a known baseline reduces the attack. Ttps in cybersecurity describe how cybercriminals plan and execute attacks. At its core, it refers to physical devices explicitly crafted to defend computer systems against vulnerabilities and threats. Below we define the three. The actors can range from. Ttp analysis can help security teams detect and mitigate attacks by understanding the way. Current Hardware- And Software-Based Cybersecurity Tools Tactics And Procedures.
From tech.co
13 Cyber Security Measures Your Small Business Must Take Current Hardware- And Software-Based Cybersecurity Tools Tactics And Procedures Starting from a known baseline reduces the attack. The widespread adoption of artificial. Below we define the three. More than just a protective shield, these. The actors can range from. Ttp analysis can help security teams detect and mitigate attacks by understanding the way threat actors operate. Ttps in cybersecurity describe how cybercriminals plan and execute attacks. The term tactics,. Current Hardware- And Software-Based Cybersecurity Tools Tactics And Procedures.
From cybriant.com
NIST Cybersecurity Framework Cybriant Current Hardware- And Software-Based Cybersecurity Tools Tactics And Procedures The actors can range from. Each component, named tactics, techniques, and procedures, offers insight into different. The widespread adoption of artificial. Below we define the three. At its core, it refers to physical devices explicitly crafted to defend computer systems against vulnerabilities and threats. Starting from a known baseline reduces the attack. Remove unwanted, unneeded or unexpected hardware and software. Current Hardware- And Software-Based Cybersecurity Tools Tactics And Procedures.
From www.edrawmax.com
Cyber Security Diagram EdrawMax Template Current Hardware- And Software-Based Cybersecurity Tools Tactics And Procedures Cybersecurity threats are becoming increasingly complex, sophisticated, malicious, well organized and well funded. The term tactics, techniques and procedures (ttp) describes the behavior of a threat actor and a structured framework for executing a cyberattack. Ttp analysis can help security teams detect and mitigate attacks by understanding the way threat actors operate. At its core, it refers to physical devices. Current Hardware- And Software-Based Cybersecurity Tools Tactics And Procedures.
From www.yokogawa.com
Cybersecurity Policies & Procedures Yokogawa Electric Corporation Current Hardware- And Software-Based Cybersecurity Tools Tactics And Procedures More than just a protective shield, these. Each component, named tactics, techniques, and procedures, offers insight into different. Ttp analysis can help security teams detect and mitigate attacks by understanding the way threat actors operate. Ttps in cybersecurity describe how cybercriminals plan and execute attacks. The widespread adoption of artificial. Remove unwanted, unneeded or unexpected hardware and software from the. Current Hardware- And Software-Based Cybersecurity Tools Tactics And Procedures.
From www.gov.uk
[Withdrawn] 10 Steps Summary GOV.UK Current Hardware- And Software-Based Cybersecurity Tools Tactics And Procedures Remove unwanted, unneeded or unexpected hardware and software from the network. More than just a protective shield, these. The actors can range from. Cybersecurity threats are becoming increasingly complex, sophisticated, malicious, well organized and well funded. At its core, it refers to physical devices explicitly crafted to defend computer systems against vulnerabilities and threats. Ttp analysis can help security teams. Current Hardware- And Software-Based Cybersecurity Tools Tactics And Procedures.
From distantjob.com
8 Most Powerful Cybersecurity Tools in 2023 DistantJob Remote Current Hardware- And Software-Based Cybersecurity Tools Tactics And Procedures More than just a protective shield, these. The term tactics, techniques and procedures (ttp) describes the behavior of a threat actor and a structured framework for executing a cyberattack. Remove unwanted, unneeded or unexpected hardware and software from the network. Ttps in cybersecurity describe how cybercriminals plan and execute attacks. Ttp analysis can help security teams detect and mitigate attacks. Current Hardware- And Software-Based Cybersecurity Tools Tactics And Procedures.
From metaorangedigital.com
Incident Response Process in Cybersecurity Current Hardware- And Software-Based Cybersecurity Tools Tactics And Procedures Ttps in cybersecurity describe how cybercriminals plan and execute attacks. Below we define the three. The actors can range from. More than just a protective shield, these. Ttp analysis can help security teams detect and mitigate attacks by understanding the way threat actors operate. Remove unwanted, unneeded or unexpected hardware and software from the network. The widespread adoption of artificial.. Current Hardware- And Software-Based Cybersecurity Tools Tactics And Procedures.
From eduinput.com
Cyber Security Types, Threats, and Certifications Current Hardware- And Software-Based Cybersecurity Tools Tactics And Procedures Below we define the three. At its core, it refers to physical devices explicitly crafted to defend computer systems against vulnerabilities and threats. Ttp analysis can help security teams detect and mitigate attacks by understanding the way threat actors operate. Cybersecurity threats are becoming increasingly complex, sophisticated, malicious, well organized and well funded. Each component, named tactics, techniques, and procedures,. Current Hardware- And Software-Based Cybersecurity Tools Tactics And Procedures.
From www.networkworld.com
A framework to help make sense of cybersecurity tools Network World Current Hardware- And Software-Based Cybersecurity Tools Tactics And Procedures The actors can range from. The widespread adoption of artificial. Starting from a known baseline reduces the attack. At its core, it refers to physical devices explicitly crafted to defend computer systems against vulnerabilities and threats. The term tactics, techniques and procedures (ttp) describes the behavior of a threat actor and a structured framework for executing a cyberattack. More than. Current Hardware- And Software-Based Cybersecurity Tools Tactics And Procedures.
From www.temok.com
Top 43 Cyber Security Tools to Improve Your Network Security Current Hardware- And Software-Based Cybersecurity Tools Tactics And Procedures Each component, named tactics, techniques, and procedures, offers insight into different. The term tactics, techniques and procedures (ttp) describes the behavior of a threat actor and a structured framework for executing a cyberattack. Ttp analysis can help security teams detect and mitigate attacks by understanding the way threat actors operate. More than just a protective shield, these. At its core,. Current Hardware- And Software-Based Cybersecurity Tools Tactics And Procedures.
From akki-greatlearning.medium.com
Top 10 Best Cyber Security Tools and Softwares For 2020 by Technology Current Hardware- And Software-Based Cybersecurity Tools Tactics And Procedures The term tactics, techniques and procedures (ttp) describes the behavior of a threat actor and a structured framework for executing a cyberattack. Starting from a known baseline reduces the attack. Cybersecurity threats are becoming increasingly complex, sophisticated, malicious, well organized and well funded. Ttps in cybersecurity describe how cybercriminals plan and execute attacks. More than just a protective shield, these.. Current Hardware- And Software-Based Cybersecurity Tools Tactics And Procedures.