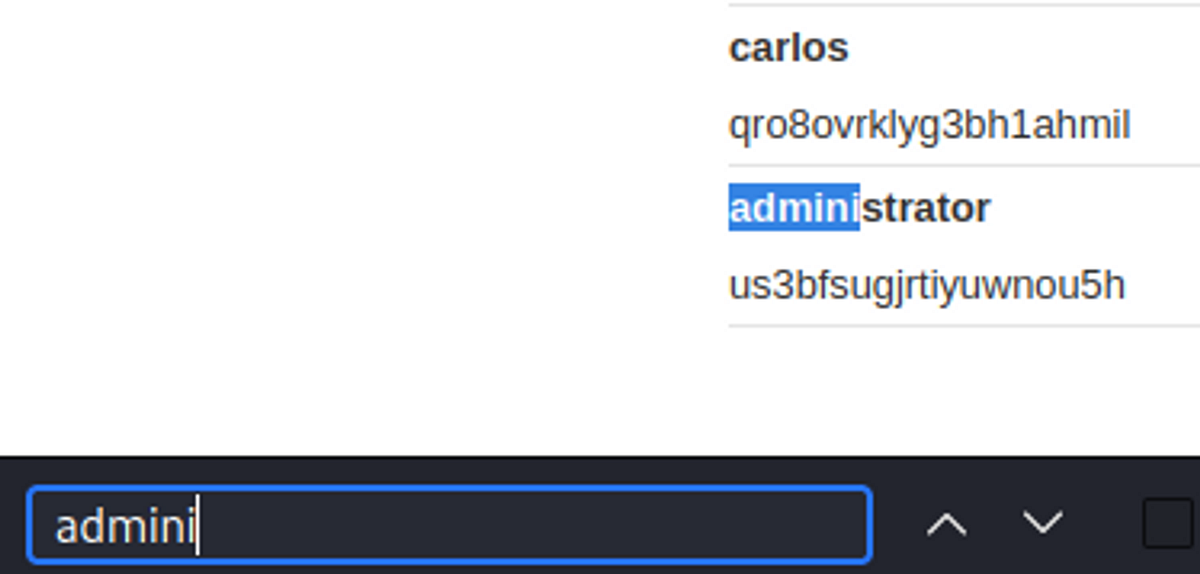
Sql Injection Get Password For User . if a user’s input is being passed unvalidated and unsanitized as part of an sql query, the user can manipulate the query itself and force it to return different. After we confirm that the site is vulnerable to sql injection, the next step is to type the appropriate payload (input) in the. The sql query is crafted in such a way that both. this sql injection cheat sheet contains examples of useful syntax that you can use to perform a variety of tasks that often arise. we get a successful login even though these are not valid credentials — it’s because we’ve found a successful sql injection payload that tricks. what is the impact of a successful sql injection attack? A successful sql injection attack can result in unauthorized access to sensitive data, such as:. select * from users where name= '' or '1'='1' and password= '' or '1'='1'. Evaluates to select * from.
from medium.com
A successful sql injection attack can result in unauthorized access to sensitive data, such as:. this sql injection cheat sheet contains examples of useful syntax that you can use to perform a variety of tasks that often arise. select * from users where name= '' or '1'='1' and password= '' or '1'='1'. After we confirm that the site is vulnerable to sql injection, the next step is to type the appropriate payload (input) in the. Evaluates to select * from. if a user’s input is being passed unvalidated and unsanitized as part of an sql query, the user can manipulate the query itself and force it to return different. what is the impact of a successful sql injection attack? The sql query is crafted in such a way that both. we get a successful login even though these are not valid credentials — it’s because we’ve found a successful sql injection payload that tricks.
Dumping Passwords From Databases — Unionbased SQL Injection Scripting
Sql Injection Get Password For User we get a successful login even though these are not valid credentials — it’s because we’ve found a successful sql injection payload that tricks. what is the impact of a successful sql injection attack? if a user’s input is being passed unvalidated and unsanitized as part of an sql query, the user can manipulate the query itself and force it to return different. A successful sql injection attack can result in unauthorized access to sensitive data, such as:. After we confirm that the site is vulnerable to sql injection, the next step is to type the appropriate payload (input) in the. this sql injection cheat sheet contains examples of useful syntax that you can use to perform a variety of tasks that often arise. The sql query is crafted in such a way that both. select * from users where name= '' or '1'='1' and password= '' or '1'='1'. we get a successful login even though these are not valid credentials — it’s because we’ve found a successful sql injection payload that tricks. Evaluates to select * from.
From morioh.com
SQL Tutorial for Beginners SQL Injection Sql Injection Get Password For User what is the impact of a successful sql injection attack? if a user’s input is being passed unvalidated and unsanitized as part of an sql query, the user can manipulate the query itself and force it to return different. select * from users where name= '' or '1'='1' and password= '' or '1'='1'. we get a. Sql Injection Get Password For User.
From escape.tech
SQL Injection in GraphQL ⎜Escape Blog Sql Injection Get Password For User select * from users where name= '' or '1'='1' and password= '' or '1'='1'. we get a successful login even though these are not valid credentials — it’s because we’ve found a successful sql injection payload that tricks. A successful sql injection attack can result in unauthorized access to sensitive data, such as:. After we confirm that the. Sql Injection Get Password For User.
From thereviewstories.com
Sql Injection Sql Injection Get Password For User what is the impact of a successful sql injection attack? select * from users where name= '' or '1'='1' and password= '' or '1'='1'. this sql injection cheat sheet contains examples of useful syntax that you can use to perform a variety of tasks that often arise. we get a successful login even though these are. Sql Injection Get Password For User.
From indiancybersecuritysolutions.com
What is SQL Injection Indian Cyber Security Solutions Sql Injection Get Password For User After we confirm that the site is vulnerable to sql injection, the next step is to type the appropriate payload (input) in the. if a user’s input is being passed unvalidated and unsanitized as part of an sql query, the user can manipulate the query itself and force it to return different. what is the impact of a. Sql Injection Get Password For User.
From www.hackercoolmagazine.com
SQL Injection for beginners Hackercool Magazine Sql Injection Get Password For User we get a successful login even though these are not valid credentials — it’s because we’ve found a successful sql injection payload that tricks. this sql injection cheat sheet contains examples of useful syntax that you can use to perform a variety of tasks that often arise. what is the impact of a successful sql injection attack?. Sql Injection Get Password For User.
From medium.com
Dumping Passwords From Databases — Unionbased SQL Injection Scripting Sql Injection Get Password For User Evaluates to select * from. A successful sql injection attack can result in unauthorized access to sensitive data, such as:. this sql injection cheat sheet contains examples of useful syntax that you can use to perform a variety of tasks that often arise. we get a successful login even though these are not valid credentials — it’s because. Sql Injection Get Password For User.
From kratikal.com
SQL Injection in ERP Applications Kratikal Blogs Sql Injection Get Password For User Evaluates to select * from. this sql injection cheat sheet contains examples of useful syntax that you can use to perform a variety of tasks that often arise. what is the impact of a successful sql injection attack? After we confirm that the site is vulnerable to sql injection, the next step is to type the appropriate payload. Sql Injection Get Password For User.
From slideplayer.com
SQL INJECTION ATTACKS. ppt download Sql Injection Get Password For User we get a successful login even though these are not valid credentials — it’s because we’ve found a successful sql injection payload that tricks. what is the impact of a successful sql injection attack? select * from users where name= '' or '1'='1' and password= '' or '1'='1'. The sql query is crafted in such a way. Sql Injection Get Password For User.
From whatismyipaddress.com
SQL Injection What It Is and How Does It Work Sql Injection Get Password For User if a user’s input is being passed unvalidated and unsanitized as part of an sql query, the user can manipulate the query itself and force it to return different. The sql query is crafted in such a way that both. this sql injection cheat sheet contains examples of useful syntax that you can use to perform a variety. Sql Injection Get Password For User.
From www.youtube.com
Get all usernames and password sql injection union attack retrieving Sql Injection Get Password For User The sql query is crafted in such a way that both. After we confirm that the site is vulnerable to sql injection, the next step is to type the appropriate payload (input) in the. this sql injection cheat sheet contains examples of useful syntax that you can use to perform a variety of tasks that often arise. we. Sql Injection Get Password For User.
From wikihow.com
How to Prevent SQL Injection in PHP (with Pictures) wikiHow Sql Injection Get Password For User this sql injection cheat sheet contains examples of useful syntax that you can use to perform a variety of tasks that often arise. if a user’s input is being passed unvalidated and unsanitized as part of an sql query, the user can manipulate the query itself and force it to return different. A successful sql injection attack can. Sql Injection Get Password For User.
From www.getastra.com
Server Security Beginner's Guide Sql Injection Get Password For User The sql query is crafted in such a way that both. Evaluates to select * from. After we confirm that the site is vulnerable to sql injection, the next step is to type the appropriate payload (input) in the. this sql injection cheat sheet contains examples of useful syntax that you can use to perform a variety of tasks. Sql Injection Get Password For User.
From www.youtube.com
SQL Injection (GET/Search) YouTube Sql Injection Get Password For User this sql injection cheat sheet contains examples of useful syntax that you can use to perform a variety of tasks that often arise. A successful sql injection attack can result in unauthorized access to sensitive data, such as:. After we confirm that the site is vulnerable to sql injection, the next step is to type the appropriate payload (input). Sql Injection Get Password For User.
From www.slideserve.com
PPT SQL Injection PowerPoint Presentation, free download ID6662917 Sql Injection Get Password For User what is the impact of a successful sql injection attack? select * from users where name= '' or '1'='1' and password= '' or '1'='1'. this sql injection cheat sheet contains examples of useful syntax that you can use to perform a variety of tasks that often arise. After we confirm that the site is vulnerable to sql. Sql Injection Get Password For User.
From medium.com
Introduction to SQL Injections. SQL injection is an attack technique Sql Injection Get Password For User The sql query is crafted in such a way that both. After we confirm that the site is vulnerable to sql injection, the next step is to type the appropriate payload (input) in the. select * from users where name= '' or '1'='1' and password= '' or '1'='1'. A successful sql injection attack can result in unauthorized access to. Sql Injection Get Password For User.
From topdev.vn
SQL Injection là gì? Cách giảm thiểu và phòng ngừa SQL Injection Sql Injection Get Password For User After we confirm that the site is vulnerable to sql injection, the next step is to type the appropriate payload (input) in the. The sql query is crafted in such a way that both. Evaluates to select * from. what is the impact of a successful sql injection attack? A successful sql injection attack can result in unauthorized access. Sql Injection Get Password For User.
From www.opentechinfo.com
Sql injection Tutorials Beginners Guide website hacking Sql Injection Get Password For User The sql query is crafted in such a way that both. select * from users where name= '' or '1'='1' and password= '' or '1'='1'. Evaluates to select * from. what is the impact of a successful sql injection attack? A successful sql injection attack can result in unauthorized access to sensitive data, such as:. this sql. Sql Injection Get Password For User.
From www.youtube.com
Sqlmap (Sql injection) Get the root password YouTube Sql Injection Get Password For User if a user’s input is being passed unvalidated and unsanitized as part of an sql query, the user can manipulate the query itself and force it to return different. A successful sql injection attack can result in unauthorized access to sensitive data, such as:. After we confirm that the site is vulnerable to sql injection, the next step is. Sql Injection Get Password For User.
From programming.vip
6.SQL injection and bypass Sql Injection Get Password For User we get a successful login even though these are not valid credentials — it’s because we’ve found a successful sql injection payload that tricks. select * from users where name= '' or '1'='1' and password= '' or '1'='1'. what is the impact of a successful sql injection attack? After we confirm that the site is vulnerable to. Sql Injection Get Password For User.
From www.youtube.com
SQL Injection on server with sqlmap YouTube Sql Injection Get Password For User Evaluates to select * from. The sql query is crafted in such a way that both. A successful sql injection attack can result in unauthorized access to sensitive data, such as:. if a user’s input is being passed unvalidated and unsanitized as part of an sql query, the user can manipulate the query itself and force it to return. Sql Injection Get Password For User.
From computersecuritypgp.blogspot.com
Computer Security and PGP What is an SQL Injection Attack Sql Injection Get Password For User this sql injection cheat sheet contains examples of useful syntax that you can use to perform a variety of tasks that often arise. Evaluates to select * from. After we confirm that the site is vulnerable to sql injection, the next step is to type the appropriate payload (input) in the. The sql query is crafted in such a. Sql Injection Get Password For User.
From slideplayer.com
Lecture 27 Security I April 4, 2018 Open news web sites. ppt download Sql Injection Get Password For User we get a successful login even though these are not valid credentials — it’s because we’ve found a successful sql injection payload that tricks. After we confirm that the site is vulnerable to sql injection, the next step is to type the appropriate payload (input) in the. what is the impact of a successful sql injection attack? . Sql Injection Get Password For User.
From thehackerish.com
SQL injection examples for practice thehackerish Sql Injection Get Password For User The sql query is crafted in such a way that both. Evaluates to select * from. A successful sql injection attack can result in unauthorized access to sensitive data, such as:. we get a successful login even though these are not valid credentials — it’s because we’ve found a successful sql injection payload that tricks. select * from. Sql Injection Get Password For User.
From ithemes.com
SQL Injection A Guide for WordPress Users Sql Injection Get Password For User we get a successful login even though these are not valid credentials — it’s because we’ve found a successful sql injection payload that tricks. After we confirm that the site is vulnerable to sql injection, the next step is to type the appropriate payload (input) in the. Evaluates to select * from. what is the impact of a. Sql Injection Get Password For User.
From medium.com
Let’s Learn SQL Injection and Bypass Login by sachith sujeewa Medium Sql Injection Get Password For User select * from users where name= '' or '1'='1' and password= '' or '1'='1'. we get a successful login even though these are not valid credentials — it’s because we’ve found a successful sql injection payload that tricks. if a user’s input is being passed unvalidated and unsanitized as part of an sql query, the user can. Sql Injection Get Password For User.
From techterms.com
SQL Injection Definition Sql Injection Get Password For User A successful sql injection attack can result in unauthorized access to sensitive data, such as:. this sql injection cheat sheet contains examples of useful syntax that you can use to perform a variety of tasks that often arise. if a user’s input is being passed unvalidated and unsanitized as part of an sql query, the user can manipulate. Sql Injection Get Password For User.
From www.researchgate.net
SQL normal and SQL injection attack data flow. All subsequent strings Sql Injection Get Password For User Evaluates to select * from. After we confirm that the site is vulnerable to sql injection, the next step is to type the appropriate payload (input) in the. The sql query is crafted in such a way that both. what is the impact of a successful sql injection attack? select * from users where name= '' or '1'='1'. Sql Injection Get Password For User.
From www.slideshare.net
SQL INJECTION EXAMPLE username Sql Injection Get Password For User Evaluates to select * from. The sql query is crafted in such a way that both. After we confirm that the site is vulnerable to sql injection, the next step is to type the appropriate payload (input) in the. A successful sql injection attack can result in unauthorized access to sensitive data, such as:. this sql injection cheat sheet. Sql Injection Get Password For User.
From linuxhint.com
Blind SQL Injection Techniques Tutorial Sql Injection Get Password For User this sql injection cheat sheet contains examples of useful syntax that you can use to perform a variety of tasks that often arise. A successful sql injection attack can result in unauthorized access to sensitive data, such as:. Evaluates to select * from. After we confirm that the site is vulnerable to sql injection, the next step is to. Sql Injection Get Password For User.
From www.slideserve.com
PPT SQL Injection PowerPoint Presentation, free download ID3956697 Sql Injection Get Password For User A successful sql injection attack can result in unauthorized access to sensitive data, such as:. we get a successful login even though these are not valid credentials — it’s because we’ve found a successful sql injection payload that tricks. if a user’s input is being passed unvalidated and unsanitized as part of an sql query, the user can. Sql Injection Get Password For User.
From systemweakness.com
SQL Injection Attacks. What is a SQL Injection attack? by ADITYA Sql Injection Get Password For User what is the impact of a successful sql injection attack? this sql injection cheat sheet contains examples of useful syntax that you can use to perform a variety of tasks that often arise. The sql query is crafted in such a way that both. select * from users where name= '' or '1'='1' and password= '' or. Sql Injection Get Password For User.
From www.milesweb.com
SQL Injection SQL Queries, Working, Types, Tips to Prevent the Attack Sql Injection Get Password For User what is the impact of a successful sql injection attack? After we confirm that the site is vulnerable to sql injection, the next step is to type the appropriate payload (input) in the. The sql query is crafted in such a way that both. Evaluates to select * from. if a user’s input is being passed unvalidated and. Sql Injection Get Password For User.
From www.globaldots.com
How to Prevent SQL Injection Attacks? Best Practices GlobalDots Sql Injection Get Password For User we get a successful login even though these are not valid credentials — it’s because we’ve found a successful sql injection payload that tricks. Evaluates to select * from. what is the impact of a successful sql injection attack? A successful sql injection attack can result in unauthorized access to sensitive data, such as:. select * from. Sql Injection Get Password For User.
From techofide.com
SQL Injection Attack (SQLi) SQL Injection Prevention Sql Injection Get Password For User Evaluates to select * from. we get a successful login even though these are not valid credentials — it’s because we’ve found a successful sql injection payload that tricks. what is the impact of a successful sql injection attack? A successful sql injection attack can result in unauthorized access to sensitive data, such as:. this sql injection. Sql Injection Get Password For User.
From www.youtube.com
Ethical Hacking Compromising account passwords using SQL Injection Sql Injection Get Password For User After we confirm that the site is vulnerable to sql injection, the next step is to type the appropriate payload (input) in the. this sql injection cheat sheet contains examples of useful syntax that you can use to perform a variety of tasks that often arise. A successful sql injection attack can result in unauthorized access to sensitive data,. Sql Injection Get Password For User.