Access Control List Best Practices . There is a common number or name that assigns multiple statements to the. Access control powered by acls helps manage resource access, improve security and prevent network abuse. The network administrator should apply a standard acl closest to the destination. What are access control list best practices? What are the best practices when setting up an access control list? However, the wrong acl configuration can. There are some recommended best practices when creating and applying access control lists (acl). Access control lists are essential elements of an effective network security strategy. Network admins use access control lists (acls) to define permissions associated with network traffic and control security and. What are the types of access controls implemented in access control lists? The standard acl statement is comprised of a source ip address and wildcard mask. Implementing best practices can help keep your access controls current, effective, and. An access control list (acl) is a set of rules that determine whether a user or a system is allowed or denied access to a particular digital resource, such as files,.
from www.slideserve.com
What are the types of access controls implemented in access control lists? Access control lists are essential elements of an effective network security strategy. The network administrator should apply a standard acl closest to the destination. What are access control list best practices? What are the best practices when setting up an access control list? An access control list (acl) is a set of rules that determine whether a user or a system is allowed or denied access to a particular digital resource, such as files,. Access control powered by acls helps manage resource access, improve security and prevent network abuse. Network admins use access control lists (acls) to define permissions associated with network traffic and control security and. However, the wrong acl configuration can. There are some recommended best practices when creating and applying access control lists (acl).
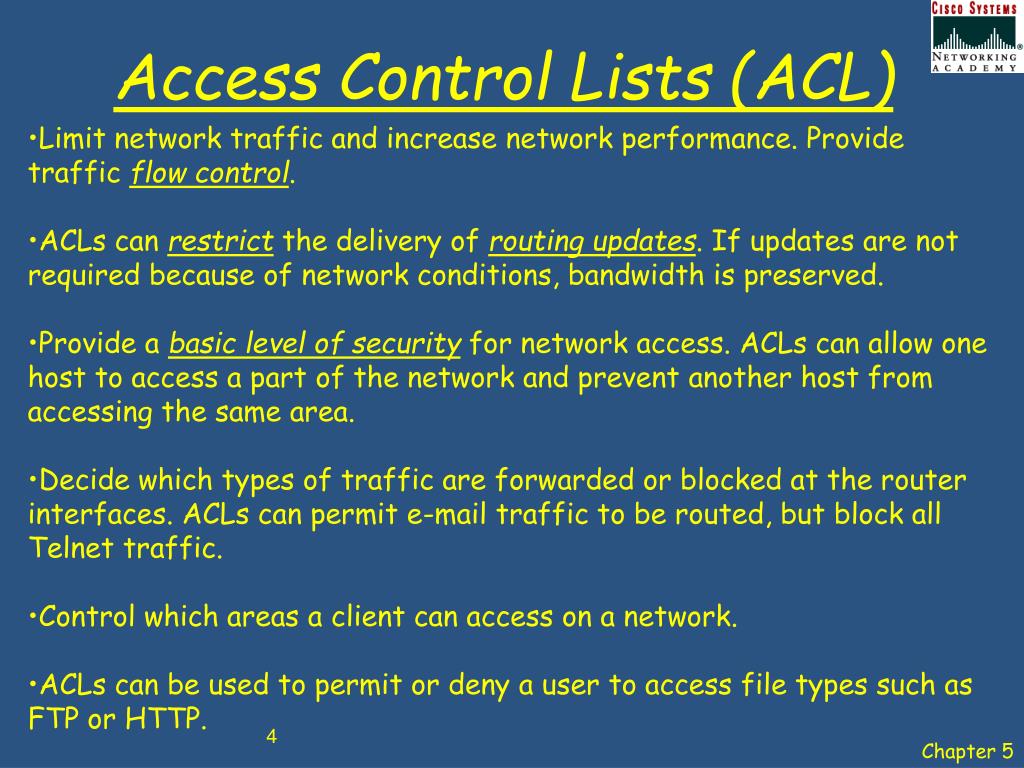
PPT Chap 5 Access Control Lists Learning Objectives PowerPoint
Access Control List Best Practices Access control lists are essential elements of an effective network security strategy. Implementing best practices can help keep your access controls current, effective, and. Network admins use access control lists (acls) to define permissions associated with network traffic and control security and. The network administrator should apply a standard acl closest to the destination. The standard acl statement is comprised of a source ip address and wildcard mask. What are the types of access controls implemented in access control lists? What are the best practices when setting up an access control list? There are some recommended best practices when creating and applying access control lists (acl). What are access control list best practices? However, the wrong acl configuration can. Access control lists are essential elements of an effective network security strategy. Access control powered by acls helps manage resource access, improve security and prevent network abuse. There is a common number or name that assigns multiple statements to the. An access control list (acl) is a set of rules that determine whether a user or a system is allowed or denied access to a particular digital resource, such as files,.
From www.slideshare.net
Access Control Principles and Practice Access Control List Best Practices However, the wrong acl configuration can. An access control list (acl) is a set of rules that determine whether a user or a system is allowed or denied access to a particular digital resource, such as files,. There is a common number or name that assigns multiple statements to the. The standard acl statement is comprised of a source ip. Access Control List Best Practices.
From www.twingate.com
Access Control Lists (ACLs) How They Work & Best Practices Twingate Access Control List Best Practices What are the best practices when setting up an access control list? An access control list (acl) is a set of rules that determine whether a user or a system is allowed or denied access to a particular digital resource, such as files,. What are the types of access controls implemented in access control lists? Implementing best practices can help. Access Control List Best Practices.
From the-packet.blogspot.com
...The Packet... Best Practice Access List Branch Office Router (Firewall) Access Control List Best Practices Access control powered by acls helps manage resource access, improve security and prevent network abuse. Implementing best practices can help keep your access controls current, effective, and. What are the types of access controls implemented in access control lists? What are the best practices when setting up an access control list? What are access control list best practices? The network. Access Control List Best Practices.
From iesmartsystems.com
Access Control Best Practices 14 Tips For 2022 Access Control List Best Practices An access control list (acl) is a set of rules that determine whether a user or a system is allowed or denied access to a particular digital resource, such as files,. Access control lists are essential elements of an effective network security strategy. What are access control list best practices? The standard acl statement is comprised of a source ip. Access Control List Best Practices.
From jaycemeowcunningham.blogspot.com
What Function Describe the Uses of an Access Control List Access Control List Best Practices The standard acl statement is comprised of a source ip address and wildcard mask. Access control powered by acls helps manage resource access, improve security and prevent network abuse. There are some recommended best practices when creating and applying access control lists (acl). An access control list (acl) is a set of rules that determine whether a user or a. Access Control List Best Practices.
From frontegg.com
Role Based Access Control Best Practices You Must Know Frontegg Access Control List Best Practices Implementing best practices can help keep your access controls current, effective, and. Access control lists are essential elements of an effective network security strategy. There are some recommended best practices when creating and applying access control lists (acl). An access control list (acl) is a set of rules that determine whether a user or a system is allowed or denied. Access Control List Best Practices.
From www.slideserve.com
PPT Chap 5 Access Control Lists Learning Objectives PowerPoint Access Control List Best Practices There is a common number or name that assigns multiple statements to the. However, the wrong acl configuration can. The standard acl statement is comprised of a source ip address and wildcard mask. What are the types of access controls implemented in access control lists? Access control lists are essential elements of an effective network security strategy. Access control powered. Access Control List Best Practices.
From www.youtube.com
What Are Access Lists? Access Control Lists (ACLs) Part 1 of 8 Access Control List Best Practices Access control lists are essential elements of an effective network security strategy. However, the wrong acl configuration can. There is a common number or name that assigns multiple statements to the. The network administrator should apply a standard acl closest to the destination. There are some recommended best practices when creating and applying access control lists (acl). What are access. Access Control List Best Practices.
From www.slideshare.net
Access Control Principles and Practice Access Control List Best Practices The network administrator should apply a standard acl closest to the destination. What are the best practices when setting up an access control list? Access control lists are essential elements of an effective network security strategy. There are some recommended best practices when creating and applying access control lists (acl). However, the wrong acl configuration can. What are the types. Access Control List Best Practices.
From www.webservertalk.com
How to Make an Access Control List (ACL) Access Control List Best Practices However, the wrong acl configuration can. What are the best practices when setting up an access control list? An access control list (acl) is a set of rules that determine whether a user or a system is allowed or denied access to a particular digital resource, such as files,. Access control lists are essential elements of an effective network security. Access Control List Best Practices.
From www.freecodecamp.org
What is An ACL? Access Control Lists Explained Access Control List Best Practices What are the types of access controls implemented in access control lists? There are some recommended best practices when creating and applying access control lists (acl). Access control powered by acls helps manage resource access, improve security and prevent network abuse. The network administrator should apply a standard acl closest to the destination. The standard acl statement is comprised of. Access Control List Best Practices.
From www.techtarget.com
Secure data in the cloud with encryption and access controls TechTarget Access Control List Best Practices However, the wrong acl configuration can. Access control powered by acls helps manage resource access, improve security and prevent network abuse. The network administrator should apply a standard acl closest to the destination. Network admins use access control lists (acls) to define permissions associated with network traffic and control security and. Access control lists are essential elements of an effective. Access Control List Best Practices.
From artofservice.com.au
Access Control List Toolkit Access Control List Best Practices The network administrator should apply a standard acl closest to the destination. What are access control list best practices? The standard acl statement is comprised of a source ip address and wildcard mask. Network admins use access control lists (acls) to define permissions associated with network traffic and control security and. However, the wrong acl configuration can. What are the. Access Control List Best Practices.
From www.slideserve.com
PPT Computer Security Network + Link Layer Security + Network Access Control List Best Practices There is a common number or name that assigns multiple statements to the. Access control powered by acls helps manage resource access, improve security and prevent network abuse. Access control lists are essential elements of an effective network security strategy. What are the types of access controls implemented in access control lists? The network administrator should apply a standard acl. Access Control List Best Practices.
From www.networkeducator.com
What Is Access Control List (ACL) & How It Works Network Educator Access Control List Best Practices What are the types of access controls implemented in access control lists? Network admins use access control lists (acls) to define permissions associated with network traffic and control security and. There are some recommended best practices when creating and applying access control lists (acl). The network administrator should apply a standard acl closest to the destination. What are access control. Access Control List Best Practices.
From www.secureidentityhub.com
RoleBased Access Control Best Practices and Guidelines Access Control List Best Practices There are some recommended best practices when creating and applying access control lists (acl). What are the best practices when setting up an access control list? Implementing best practices can help keep your access controls current, effective, and. What are the types of access controls implemented in access control lists? What are access control list best practices? However, the wrong. Access Control List Best Practices.
From www.devopsschool.com
Aws Auditing Environments Security Best Practices Access Control List Best Practices The network administrator should apply a standard acl closest to the destination. Access control powered by acls helps manage resource access, improve security and prevent network abuse. Access control lists are essential elements of an effective network security strategy. What are the types of access controls implemented in access control lists? The standard acl statement is comprised of a source. Access Control List Best Practices.
From pharmakondergi.com
An Access Control List ACL Download Scientific Diagram Access Control List Best Practices However, the wrong acl configuration can. What are the types of access controls implemented in access control lists? Network admins use access control lists (acls) to define permissions associated with network traffic and control security and. What are the best practices when setting up an access control list? Access control powered by acls helps manage resource access, improve security and. Access Control List Best Practices.
From www.slideshare.net
Access Control List & its Types Access Control List Best Practices The network administrator should apply a standard acl closest to the destination. Implementing best practices can help keep your access controls current, effective, and. There are some recommended best practices when creating and applying access control lists (acl). What are access control list best practices? There is a common number or name that assigns multiple statements to the. The standard. Access Control List Best Practices.
From www.scribd.com
HC110110027 Access Control Lists PDF Access Control Networking Access Control List Best Practices What are the types of access controls implemented in access control lists? There are some recommended best practices when creating and applying access control lists (acl). Access control powered by acls helps manage resource access, improve security and prevent network abuse. Access control lists are essential elements of an effective network security strategy. What are the best practices when setting. Access Control List Best Practices.
From www.varonis.com
What is RoleBased Access Control (RBAC)? Access Control List Best Practices What are access control list best practices? The standard acl statement is comprised of a source ip address and wildcard mask. Access control powered by acls helps manage resource access, improve security and prevent network abuse. The network administrator should apply a standard acl closest to the destination. What are the types of access controls implemented in access control lists?. Access Control List Best Practices.
From www.wallarm.com
What is ACL? Examples and Types of Access Control List Access Control List Best Practices Implementing best practices can help keep your access controls current, effective, and. Access control powered by acls helps manage resource access, improve security and prevent network abuse. Access control lists are essential elements of an effective network security strategy. The network administrator should apply a standard acl closest to the destination. However, the wrong acl configuration can. There are some. Access Control List Best Practices.
From www.g2.com
What Is an Access Control List (ACL)? Types and Examples Access Control List Best Practices Access control lists are essential elements of an effective network security strategy. There are some recommended best practices when creating and applying access control lists (acl). Access control powered by acls helps manage resource access, improve security and prevent network abuse. Network admins use access control lists (acls) to define permissions associated with network traffic and control security and. What. Access Control List Best Practices.
From ccnatutorials.in
Access Control Lists and their Implementation in Packet Tracer CCNA Access Control List Best Practices What are the types of access controls implemented in access control lists? Access control lists are essential elements of an effective network security strategy. The network administrator should apply a standard acl closest to the destination. The standard acl statement is comprised of a source ip address and wildcard mask. However, the wrong acl configuration can. Access control powered by. Access Control List Best Practices.
From pediaa.com
What is the Difference Between Access Control List and Access Control Access Control List Best Practices However, the wrong acl configuration can. Access control lists are essential elements of an effective network security strategy. What are access control list best practices? The network administrator should apply a standard acl closest to the destination. Access control powered by acls helps manage resource access, improve security and prevent network abuse. What are the best practices when setting up. Access Control List Best Practices.
From kintronics.com
Access Control Systems Good Practices Kintronics Access Control List Best Practices What are the types of access controls implemented in access control lists? Network admins use access control lists (acls) to define permissions associated with network traffic and control security and. Access control powered by acls helps manage resource access, improve security and prevent network abuse. What are the best practices when setting up an access control list? Access control lists. Access Control List Best Practices.
From www.slideserve.com
PPT Chap 5 Access Control Lists Learning Objectives PowerPoint Access Control List Best Practices Access control powered by acls helps manage resource access, improve security and prevent network abuse. Access control lists are essential elements of an effective network security strategy. However, the wrong acl configuration can. Network admins use access control lists (acls) to define permissions associated with network traffic and control security and. The standard acl statement is comprised of a source. Access Control List Best Practices.
From www.slideshare.net
Access Control Principles and Practice Access Control List Best Practices An access control list (acl) is a set of rules that determine whether a user or a system is allowed or denied access to a particular digital resource, such as files,. What are the types of access controls implemented in access control lists? Network admins use access control lists (acls) to define permissions associated with network traffic and control security. Access Control List Best Practices.
From content-1606--budibase.netlify.app
RoleBased Access Control Ultimate Guide Access Control List Best Practices What are the best practices when setting up an access control list? There is a common number or name that assigns multiple statements to the. However, the wrong acl configuration can. Network admins use access control lists (acls) to define permissions associated with network traffic and control security and. What are the types of access controls implemented in access control. Access Control List Best Practices.
From identitymanagementinstitute.org
Access Control Matrix and Capability List Identity Management Institute® Access Control List Best Practices Network admins use access control lists (acls) to define permissions associated with network traffic and control security and. There are some recommended best practices when creating and applying access control lists (acl). The standard acl statement is comprised of a source ip address and wildcard mask. There is a common number or name that assigns multiple statements to the. The. Access Control List Best Practices.
From www.ekransystem.com
User Access Review What Is It, Best Practices & Checklist Ekran System Access Control List Best Practices Network admins use access control lists (acls) to define permissions associated with network traffic and control security and. There are some recommended best practices when creating and applying access control lists (acl). What are the types of access controls implemented in access control lists? Access control lists are essential elements of an effective network security strategy. What are the best. Access Control List Best Practices.
From biznis-plus.com
What Is RoleBased Access Control? Here’s A Quick Guide For Every Access Control List Best Practices Access control lists are essential elements of an effective network security strategy. What are the best practices when setting up an access control list? There are some recommended best practices when creating and applying access control lists (acl). What are access control list best practices? The network administrator should apply a standard acl closest to the destination. Access control powered. Access Control List Best Practices.
From www.youtube.com
Types of access control lists explained Standard, Extended, Numbered Access Control List Best Practices Access control lists are essential elements of an effective network security strategy. The standard acl statement is comprised of a source ip address and wildcard mask. There are some recommended best practices when creating and applying access control lists (acl). What are the best practices when setting up an access control list? Access control powered by acls helps manage resource. Access Control List Best Practices.
From slideplayer.com
Access Control Lists. ppt download Access Control List Best Practices Network admins use access control lists (acls) to define permissions associated with network traffic and control security and. However, the wrong acl configuration can. Implementing best practices can help keep your access controls current, effective, and. What are the types of access controls implemented in access control lists? What are access control list best practices? An access control list (acl). Access Control List Best Practices.
From www.smartaccesssolutions.com
Top Access Control Setup Best Practices for Secure Environments Access Control List Best Practices What are the best practices when setting up an access control list? However, the wrong acl configuration can. The network administrator should apply a standard acl closest to the destination. What are access control list best practices? The standard acl statement is comprised of a source ip address and wildcard mask. Access control lists are essential elements of an effective. Access Control List Best Practices.