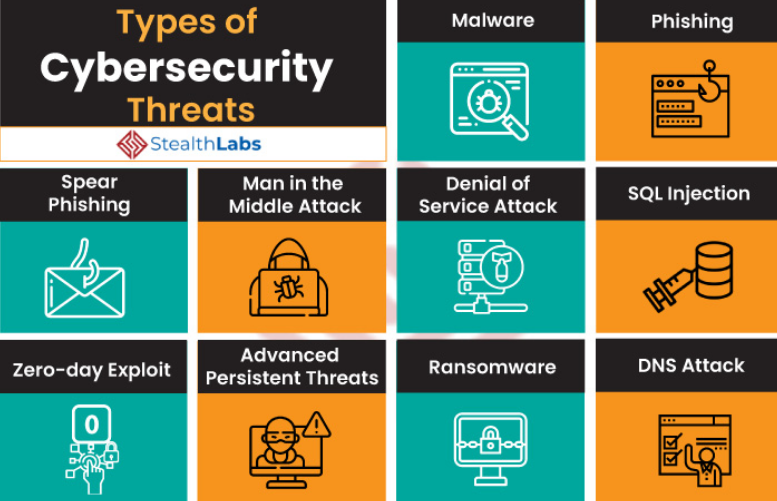
Protection Threats Examples . Here are the 10 top cybersecurity threats to watch out for: Organizations that take cyber threats seriously have a. In 2023, 26,447 vulnerabilities were assigned a common. The threats range from simple viruses, malware, and phishing attacks to complex ransomware and supply chain attacks. An attack on these assets might not affect everyone in the organization, but will exploit areas of immaturity in the.
from support.aiesec.org
Here are the 10 top cybersecurity threats to watch out for: The threats range from simple viruses, malware, and phishing attacks to complex ransomware and supply chain attacks. Organizations that take cyber threats seriously have a. In 2023, 26,447 vulnerabilities were assigned a common. An attack on these assets might not affect everyone in the organization, but will exploit areas of immaturity in the.
Cyber Security Threats and Attacks AIESEC Help Center
Protection Threats Examples An attack on these assets might not affect everyone in the organization, but will exploit areas of immaturity in the. Here are the 10 top cybersecurity threats to watch out for: The threats range from simple viruses, malware, and phishing attacks to complex ransomware and supply chain attacks. An attack on these assets might not affect everyone in the organization, but will exploit areas of immaturity in the. Organizations that take cyber threats seriously have a. In 2023, 26,447 vulnerabilities were assigned a common.
From www.threatanalysis.com
SECURITY RISK MANAGEMENT Threat Analysis Group Protection Threats Examples Organizations that take cyber threats seriously have a. In 2023, 26,447 vulnerabilities were assigned a common. The threats range from simple viruses, malware, and phishing attacks to complex ransomware and supply chain attacks. An attack on these assets might not affect everyone in the organization, but will exploit areas of immaturity in the. Here are the 10 top cybersecurity threats. Protection Threats Examples.
From www.okta.com
Advanced Persistent Threat Definition, Lifecycle & Defense Okta Protection Threats Examples The threats range from simple viruses, malware, and phishing attacks to complex ransomware and supply chain attacks. An attack on these assets might not affect everyone in the organization, but will exploit areas of immaturity in the. Organizations that take cyber threats seriously have a. In 2023, 26,447 vulnerabilities were assigned a common. Here are the 10 top cybersecurity threats. Protection Threats Examples.
From techjournal.org
Top 10 Cyber Security Threats And Solutions To Prevent Them Protection Threats Examples The threats range from simple viruses, malware, and phishing attacks to complex ransomware and supply chain attacks. Organizations that take cyber threats seriously have a. An attack on these assets might not affect everyone in the organization, but will exploit areas of immaturity in the. Here are the 10 top cybersecurity threats to watch out for: In 2023, 26,447 vulnerabilities. Protection Threats Examples.
From securityboulevard.com
Your Security Guide to Insider Threats Detection, Best Practices Protection Threats Examples Here are the 10 top cybersecurity threats to watch out for: Organizations that take cyber threats seriously have a. An attack on these assets might not affect everyone in the organization, but will exploit areas of immaturity in the. In 2023, 26,447 vulnerabilities were assigned a common. The threats range from simple viruses, malware, and phishing attacks to complex ransomware. Protection Threats Examples.
From www.theengineeringprojects.com
What Are Cyber Threats And How Can You Stay Protected? The Protection Threats Examples The threats range from simple viruses, malware, and phishing attacks to complex ransomware and supply chain attacks. In 2023, 26,447 vulnerabilities were assigned a common. Here are the 10 top cybersecurity threats to watch out for: Organizations that take cyber threats seriously have a. An attack on these assets might not affect everyone in the organization, but will exploit areas. Protection Threats Examples.
From www.charter-global.com
Common Physical Security Threats and Vulnerabilities (With Examples) Protection Threats Examples Here are the 10 top cybersecurity threats to watch out for: In 2023, 26,447 vulnerabilities were assigned a common. Organizations that take cyber threats seriously have a. The threats range from simple viruses, malware, and phishing attacks to complex ransomware and supply chain attacks. An attack on these assets might not affect everyone in the organization, but will exploit areas. Protection Threats Examples.
From thecyphere.com
Top 8 Network Security Threats Best Practices Protection Threats Examples The threats range from simple viruses, malware, and phishing attacks to complex ransomware and supply chain attacks. Organizations that take cyber threats seriously have a. An attack on these assets might not affect everyone in the organization, but will exploit areas of immaturity in the. In 2023, 26,447 vulnerabilities were assigned a common. Here are the 10 top cybersecurity threats. Protection Threats Examples.
From computersecurityatsusen.blogspot.com
Computer Security Examples Of Computer Security Threats Protection Threats Examples An attack on these assets might not affect everyone in the organization, but will exploit areas of immaturity in the. Organizations that take cyber threats seriously have a. Here are the 10 top cybersecurity threats to watch out for: In 2023, 26,447 vulnerabilities were assigned a common. The threats range from simple viruses, malware, and phishing attacks to complex ransomware. Protection Threats Examples.
From tekmart.co.za
insider threat; an expert detailed definition, their types and Protection Threats Examples Here are the 10 top cybersecurity threats to watch out for: The threats range from simple viruses, malware, and phishing attacks to complex ransomware and supply chain attacks. In 2023, 26,447 vulnerabilities were assigned a common. Organizations that take cyber threats seriously have a. An attack on these assets might not affect everyone in the organization, but will exploit areas. Protection Threats Examples.
From www.dnsstuff.com
What Is Threat Intelligence? Definition and Types DNSstuff Protection Threats Examples Organizations that take cyber threats seriously have a. The threats range from simple viruses, malware, and phishing attacks to complex ransomware and supply chain attacks. An attack on these assets might not affect everyone in the organization, but will exploit areas of immaturity in the. In 2023, 26,447 vulnerabilities were assigned a common. Here are the 10 top cybersecurity threats. Protection Threats Examples.
From sdncommunications.com
Infographic Security Threats Insider vs.… SDN Communications Protection Threats Examples An attack on these assets might not affect everyone in the organization, but will exploit areas of immaturity in the. The threats range from simple viruses, malware, and phishing attacks to complex ransomware and supply chain attacks. Here are the 10 top cybersecurity threats to watch out for: Organizations that take cyber threats seriously have a. In 2023, 26,447 vulnerabilities. Protection Threats Examples.
From www.stealthlabs.com
Cybersecurity Threats and Attacks All You Need to Know Protection Threats Examples Here are the 10 top cybersecurity threats to watch out for: Organizations that take cyber threats seriously have a. The threats range from simple viruses, malware, and phishing attacks to complex ransomware and supply chain attacks. In 2023, 26,447 vulnerabilities were assigned a common. An attack on these assets might not affect everyone in the organization, but will exploit areas. Protection Threats Examples.
From www.infosectrain.com
Common Security Attacks in the OSI Layer Model Protection Threats Examples Here are the 10 top cybersecurity threats to watch out for: An attack on these assets might not affect everyone in the organization, but will exploit areas of immaturity in the. In 2023, 26,447 vulnerabilities were assigned a common. The threats range from simple viruses, malware, and phishing attacks to complex ransomware and supply chain attacks. Organizations that take cyber. Protection Threats Examples.
From www.slideserve.com
PPT Chapter 14 Computer Security Threats PowerPoint Presentation Protection Threats Examples An attack on these assets might not affect everyone in the organization, but will exploit areas of immaturity in the. The threats range from simple viruses, malware, and phishing attacks to complex ransomware and supply chain attacks. Here are the 10 top cybersecurity threats to watch out for: Organizations that take cyber threats seriously have a. In 2023, 26,447 vulnerabilities. Protection Threats Examples.
From support.aiesec.org
Cyber Security Threats and Attacks AIESEC Help Center Protection Threats Examples Here are the 10 top cybersecurity threats to watch out for: In 2023, 26,447 vulnerabilities were assigned a common. An attack on these assets might not affect everyone in the organization, but will exploit areas of immaturity in the. The threats range from simple viruses, malware, and phishing attacks to complex ransomware and supply chain attacks. Organizations that take cyber. Protection Threats Examples.
From developapositivewinningattitude476.blogspot.com
Develop A Positive Winning Attitude External Threats To National Protection Threats Examples In 2023, 26,447 vulnerabilities were assigned a common. Organizations that take cyber threats seriously have a. The threats range from simple viruses, malware, and phishing attacks to complex ransomware and supply chain attacks. Here are the 10 top cybersecurity threats to watch out for: An attack on these assets might not affect everyone in the organization, but will exploit areas. Protection Threats Examples.
From www.slideteam.net
Cyber Security Threat Landscape With Attacks Target And Purpose Protection Threats Examples Organizations that take cyber threats seriously have a. In 2023, 26,447 vulnerabilities were assigned a common. An attack on these assets might not affect everyone in the organization, but will exploit areas of immaturity in the. Here are the 10 top cybersecurity threats to watch out for: The threats range from simple viruses, malware, and phishing attacks to complex ransomware. Protection Threats Examples.
From www.joetheitguy.com
ITSM Basics Know Your Information Security Threats! Joe The IT Guy Protection Threats Examples The threats range from simple viruses, malware, and phishing attacks to complex ransomware and supply chain attacks. An attack on these assets might not affect everyone in the organization, but will exploit areas of immaturity in the. Here are the 10 top cybersecurity threats to watch out for: Organizations that take cyber threats seriously have a. In 2023, 26,447 vulnerabilities. Protection Threats Examples.
From www.sectigo.com
Threat vs Vulnerability Vs Risk The Differences Sectigo® Official Protection Threats Examples An attack on these assets might not affect everyone in the organization, but will exploit areas of immaturity in the. In 2023, 26,447 vulnerabilities were assigned a common. The threats range from simple viruses, malware, and phishing attacks to complex ransomware and supply chain attacks. Here are the 10 top cybersecurity threats to watch out for: Organizations that take cyber. Protection Threats Examples.
From www.charter-global.com
Common Physical Security Threats and Vulnerabilities (With Examples) Protection Threats Examples An attack on these assets might not affect everyone in the organization, but will exploit areas of immaturity in the. Here are the 10 top cybersecurity threats to watch out for: In 2023, 26,447 vulnerabilities were assigned a common. Organizations that take cyber threats seriously have a. The threats range from simple viruses, malware, and phishing attacks to complex ransomware. Protection Threats Examples.
From studyonline.ecu.edu.au
Cyber Attacks Tips for Protecting Your Organisation ECU Online Protection Threats Examples In 2023, 26,447 vulnerabilities were assigned a common. Here are the 10 top cybersecurity threats to watch out for: The threats range from simple viruses, malware, and phishing attacks to complex ransomware and supply chain attacks. Organizations that take cyber threats seriously have a. An attack on these assets might not affect everyone in the organization, but will exploit areas. Protection Threats Examples.
From www.insightsonindia.com
Meaning and Types of Cybersecurity Threats INSIGHTS IAS Simplifying Protection Threats Examples Here are the 10 top cybersecurity threats to watch out for: In 2023, 26,447 vulnerabilities were assigned a common. An attack on these assets might not affect everyone in the organization, but will exploit areas of immaturity in the. The threats range from simple viruses, malware, and phishing attacks to complex ransomware and supply chain attacks. Organizations that take cyber. Protection Threats Examples.
From www.sampletemplates.com
FREE 10+ Sample Threat Assessments in PDF M Word Protection Threats Examples In 2023, 26,447 vulnerabilities were assigned a common. Here are the 10 top cybersecurity threats to watch out for: Organizations that take cyber threats seriously have a. An attack on these assets might not affect everyone in the organization, but will exploit areas of immaturity in the. The threats range from simple viruses, malware, and phishing attacks to complex ransomware. Protection Threats Examples.
From www.csoonline.com
Threat modeling explained A process for anticipating cyber attacks Protection Threats Examples In 2023, 26,447 vulnerabilities were assigned a common. Here are the 10 top cybersecurity threats to watch out for: The threats range from simple viruses, malware, and phishing attacks to complex ransomware and supply chain attacks. Organizations that take cyber threats seriously have a. An attack on these assets might not affect everyone in the organization, but will exploit areas. Protection Threats Examples.
From securetriad.io
Internal vs External Threats Here’s All You Need to Know Protection Threats Examples An attack on these assets might not affect everyone in the organization, but will exploit areas of immaturity in the. In 2023, 26,447 vulnerabilities were assigned a common. Here are the 10 top cybersecurity threats to watch out for: The threats range from simple viruses, malware, and phishing attacks to complex ransomware and supply chain attacks. Organizations that take cyber. Protection Threats Examples.
From helpfulprofessor.com
Protection Motivation Theory Definition and Examples (2024) Protection Threats Examples The threats range from simple viruses, malware, and phishing attacks to complex ransomware and supply chain attacks. Organizations that take cyber threats seriously have a. Here are the 10 top cybersecurity threats to watch out for: In 2023, 26,447 vulnerabilities were assigned a common. An attack on these assets might not affect everyone in the organization, but will exploit areas. Protection Threats Examples.
From trainings.internshala.com
Cyber Security Threats Explore the Types & How To Prevent Them Protection Threats Examples Organizations that take cyber threats seriously have a. An attack on these assets might not affect everyone in the organization, but will exploit areas of immaturity in the. Here are the 10 top cybersecurity threats to watch out for: In 2023, 26,447 vulnerabilities were assigned a common. The threats range from simple viruses, malware, and phishing attacks to complex ransomware. Protection Threats Examples.
From spinbackup.com
Biggest Cybersecurity Threats from Within or Outside? Protection Threats Examples An attack on these assets might not affect everyone in the organization, but will exploit areas of immaturity in the. Here are the 10 top cybersecurity threats to watch out for: In 2023, 26,447 vulnerabilities were assigned a common. The threats range from simple viruses, malware, and phishing attacks to complex ransomware and supply chain attacks. Organizations that take cyber. Protection Threats Examples.
From www.charter-global.com
Common Physical Security Threats and Vulnerabilities (With Examples) Protection Threats Examples In 2023, 26,447 vulnerabilities were assigned a common. Organizations that take cyber threats seriously have a. An attack on these assets might not affect everyone in the organization, but will exploit areas of immaturity in the. Here are the 10 top cybersecurity threats to watch out for: The threats range from simple viruses, malware, and phishing attacks to complex ransomware. Protection Threats Examples.
From www.security-analyst.org
Threat Analysis and Risk Assessment Protection Threats Examples In 2023, 26,447 vulnerabilities were assigned a common. An attack on these assets might not affect everyone in the organization, but will exploit areas of immaturity in the. Organizations that take cyber threats seriously have a. The threats range from simple viruses, malware, and phishing attacks to complex ransomware and supply chain attacks. Here are the 10 top cybersecurity threats. Protection Threats Examples.
From www.wilkes.edu
Behavioral Threat Assessment Procedures Safety & Security Wilkes Protection Threats Examples In 2023, 26,447 vulnerabilities were assigned a common. Here are the 10 top cybersecurity threats to watch out for: The threats range from simple viruses, malware, and phishing attacks to complex ransomware and supply chain attacks. An attack on these assets might not affect everyone in the organization, but will exploit areas of immaturity in the. Organizations that take cyber. Protection Threats Examples.
From www.lexology.com
OCR Publishes Checklist and Infographic for Cyber Attack Response Protection Threats Examples The threats range from simple viruses, malware, and phishing attacks to complex ransomware and supply chain attacks. An attack on these assets might not affect everyone in the organization, but will exploit areas of immaturity in the. Organizations that take cyber threats seriously have a. In 2023, 26,447 vulnerabilities were assigned a common. Here are the 10 top cybersecurity threats. Protection Threats Examples.
From www.wazile.com
Must Know Online Threats and Prevention Tips WAZILE Inc. Protection Threats Examples In 2023, 26,447 vulnerabilities were assigned a common. The threats range from simple viruses, malware, and phishing attacks to complex ransomware and supply chain attacks. An attack on these assets might not affect everyone in the organization, but will exploit areas of immaturity in the. Here are the 10 top cybersecurity threats to watch out for: Organizations that take cyber. Protection Threats Examples.
From www.slideteam.net
Threat Vulnerability And Risk Mitigation Table PPT Sample Protection Threats Examples Here are the 10 top cybersecurity threats to watch out for: In 2023, 26,447 vulnerabilities were assigned a common. An attack on these assets might not affect everyone in the organization, but will exploit areas of immaturity in the. The threats range from simple viruses, malware, and phishing attacks to complex ransomware and supply chain attacks. Organizations that take cyber. Protection Threats Examples.
From owasp.org
OWASP Threat and Safeguard Matrix (TaSM) OWASP Foundation Protection Threats Examples Organizations that take cyber threats seriously have a. The threats range from simple viruses, malware, and phishing attacks to complex ransomware and supply chain attacks. An attack on these assets might not affect everyone in the organization, but will exploit areas of immaturity in the. In 2023, 26,447 vulnerabilities were assigned a common. Here are the 10 top cybersecurity threats. Protection Threats Examples.