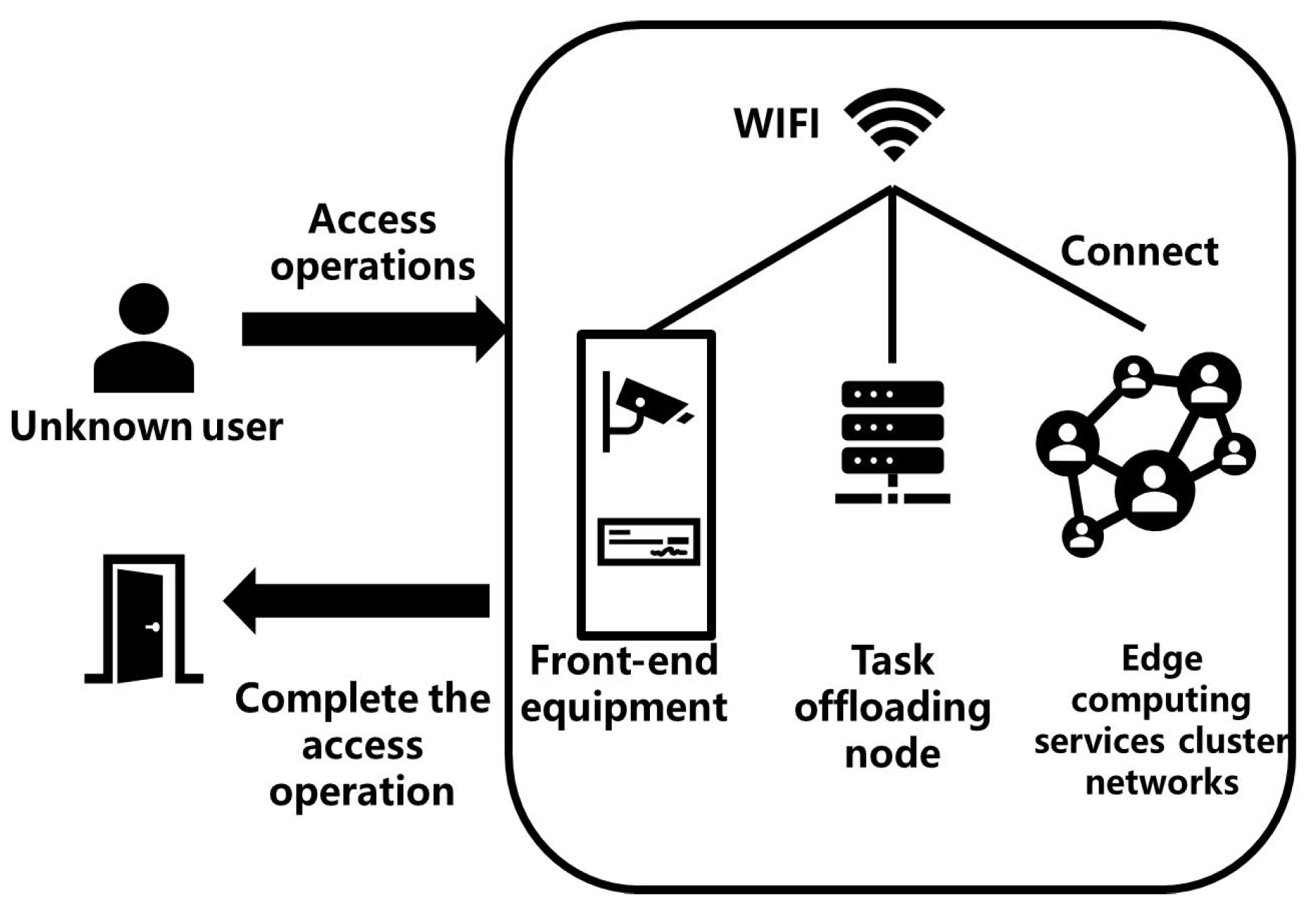
Adaptive Access Control System . Ibm verify uses machine learning and ai to analyze key parameters—user, device, activity,. To reduce the risks of users abusing their privileges, we need to empower access control with proactive measures that adapt. Effective access control must balance trust and risk. Dynamic security allows security managers to select the best control for achieving required security levels lively. Access control is an essential mechanism in collaborative environments, which guarantees the security of shared resources. Adaptive access control means your physical access control system can be adapted easily, both functionally and operationally.
from www.mdpi.com
To reduce the risks of users abusing their privileges, we need to empower access control with proactive measures that adapt. Effective access control must balance trust and risk. Access control is an essential mechanism in collaborative environments, which guarantees the security of shared resources. Adaptive access control means your physical access control system can be adapted easily, both functionally and operationally. Dynamic security allows security managers to select the best control for achieving required security levels lively. Ibm verify uses machine learning and ai to analyze key parameters—user, device, activity,.
Electronics Free FullText LACE LowCost Access Control Based on
Adaptive Access Control System To reduce the risks of users abusing their privileges, we need to empower access control with proactive measures that adapt. To reduce the risks of users abusing their privileges, we need to empower access control with proactive measures that adapt. Adaptive access control means your physical access control system can be adapted easily, both functionally and operationally. Dynamic security allows security managers to select the best control for achieving required security levels lively. Effective access control must balance trust and risk. Access control is an essential mechanism in collaborative environments, which guarantees the security of shared resources. Ibm verify uses machine learning and ai to analyze key parameters—user, device, activity,.
From www.aratek.co
Biometric Access Control System—A Complete Guide Adaptive Access Control System Effective access control must balance trust and risk. Access control is an essential mechanism in collaborative environments, which guarantees the security of shared resources. Ibm verify uses machine learning and ai to analyze key parameters—user, device, activity,. Adaptive access control means your physical access control system can be adapted easily, both functionally and operationally. Dynamic security allows security managers to. Adaptive Access Control System.
From protechsecurity.com
Commercial Access Control Systems Letting People in With Access Adaptive Access Control System To reduce the risks of users abusing their privileges, we need to empower access control with proactive measures that adapt. Access control is an essential mechanism in collaborative environments, which guarantees the security of shared resources. Ibm verify uses machine learning and ai to analyze key parameters—user, device, activity,. Effective access control must balance trust and risk. Adaptive access control. Adaptive Access Control System.
From worldlinks.com.pk
Access Control Systems In Islamabad Adaptive Access Control System To reduce the risks of users abusing their privileges, we need to empower access control with proactive measures that adapt. Ibm verify uses machine learning and ai to analyze key parameters—user, device, activity,. Effective access control must balance trust and risk. Adaptive access control means your physical access control system can be adapted easily, both functionally and operationally. Access control. Adaptive Access Control System.
From mavink.com
Access Control System Flow Chart Adaptive Access Control System Effective access control must balance trust and risk. Dynamic security allows security managers to select the best control for achieving required security levels lively. To reduce the risks of users abusing their privileges, we need to empower access control with proactive measures that adapt. Access control is an essential mechanism in collaborative environments, which guarantees the security of shared resources.. Adaptive Access Control System.
From devblogs.microsoft.com
Adaptive Access Control Azure Government Adaptive Access Control System To reduce the risks of users abusing their privileges, we need to empower access control with proactive measures that adapt. Access control is an essential mechanism in collaborative environments, which guarantees the security of shared resources. Ibm verify uses machine learning and ai to analyze key parameters—user, device, activity,. Dynamic security allows security managers to select the best control for. Adaptive Access Control System.
From www.touchstar-atc.com
Access Control Systems, Turnstiles & Biometric Devices TouchStar Adaptive Access Control System To reduce the risks of users abusing their privileges, we need to empower access control with proactive measures that adapt. Ibm verify uses machine learning and ai to analyze key parameters—user, device, activity,. Dynamic security allows security managers to select the best control for achieving required security levels lively. Effective access control must balance trust and risk. Adaptive access control. Adaptive Access Control System.
From ampletrails.com
Biometric Access Control System Biometric Attendance System Adaptive Access Control System To reduce the risks of users abusing their privileges, we need to empower access control with proactive measures that adapt. Access control is an essential mechanism in collaborative environments, which guarantees the security of shared resources. Ibm verify uses machine learning and ai to analyze key parameters—user, device, activity,. Dynamic security allows security managers to select the best control for. Adaptive Access Control System.
From www.nedapsecurity.com
Why adaptive access control is essential for a secure future Nedap Adaptive Access Control System Access control is an essential mechanism in collaborative environments, which guarantees the security of shared resources. Ibm verify uses machine learning and ai to analyze key parameters—user, device, activity,. Dynamic security allows security managers to select the best control for achieving required security levels lively. To reduce the risks of users abusing their privileges, we need to empower access control. Adaptive Access Control System.
From sssengineeringbd.com
Access Control System with all type of Hardware and Software Solution Adaptive Access Control System Adaptive access control means your physical access control system can be adapted easily, both functionally and operationally. To reduce the risks of users abusing their privileges, we need to empower access control with proactive measures that adapt. Access control is an essential mechanism in collaborative environments, which guarantees the security of shared resources. Effective access control must balance trust and. Adaptive Access Control System.
From www.youtube.com
Adaptive control YouTube Adaptive Access Control System Adaptive access control means your physical access control system can be adapted easily, both functionally and operationally. Effective access control must balance trust and risk. Ibm verify uses machine learning and ai to analyze key parameters—user, device, activity,. Dynamic security allows security managers to select the best control for achieving required security levels lively. To reduce the risks of users. Adaptive Access Control System.
From getsafeandsound.com
Access Control Systems The Complete Guide for 2023 Adaptive Access Control System Ibm verify uses machine learning and ai to analyze key parameters—user, device, activity,. To reduce the risks of users abusing their privileges, we need to empower access control with proactive measures that adapt. Dynamic security allows security managers to select the best control for achieving required security levels lively. Access control is an essential mechanism in collaborative environments, which guarantees. Adaptive Access Control System.
From www.iboss.com
Adaptive Access Policies Provide Conditional Access to Resources iboss Adaptive Access Control System Ibm verify uses machine learning and ai to analyze key parameters—user, device, activity,. Access control is an essential mechanism in collaborative environments, which guarantees the security of shared resources. Dynamic security allows security managers to select the best control for achieving required security levels lively. Effective access control must balance trust and risk. Adaptive access control means your physical access. Adaptive Access Control System.
From eureka.patsnap.com
Barcodeadaptive access control system based on Wiegand protocol and Adaptive Access Control System Access control is an essential mechanism in collaborative environments, which guarantees the security of shared resources. Dynamic security allows security managers to select the best control for achieving required security levels lively. Adaptive access control means your physical access control system can be adapted easily, both functionally and operationally. To reduce the risks of users abusing their privileges, we need. Adaptive Access Control System.
From bitwards.fi
The different flavours of Mobile Access Adaptive Access Control System To reduce the risks of users abusing their privileges, we need to empower access control with proactive measures that adapt. Effective access control must balance trust and risk. Ibm verify uses machine learning and ai to analyze key parameters—user, device, activity,. Dynamic security allows security managers to select the best control for achieving required security levels lively. Adaptive access control. Adaptive Access Control System.
From tektronixtechnology.blogspot.com
HID Access Control Systems Adaptive Access Control System Adaptive access control means your physical access control system can be adapted easily, both functionally and operationally. To reduce the risks of users abusing their privileges, we need to empower access control with proactive measures that adapt. Ibm verify uses machine learning and ai to analyze key parameters—user, device, activity,. Effective access control must balance trust and risk. Access control. Adaptive Access Control System.
From www.researchgate.net
The Proposed Adaptive Riskbased Access Control Model. Download Adaptive Access Control System Effective access control must balance trust and risk. Dynamic security allows security managers to select the best control for achieving required security levels lively. To reduce the risks of users abusing their privileges, we need to empower access control with proactive measures that adapt. Access control is an essential mechanism in collaborative environments, which guarantees the security of shared resources.. Adaptive Access Control System.
From reconasense.com
Proactive Security Starts with RiskAdaptive Access Control ReconaSense Adaptive Access Control System Access control is an essential mechanism in collaborative environments, which guarantees the security of shared resources. Effective access control must balance trust and risk. Adaptive access control means your physical access control system can be adapted easily, both functionally and operationally. To reduce the risks of users abusing their privileges, we need to empower access control with proactive measures that. Adaptive Access Control System.
From www.thebusinessresearchcompany.com
Access Control Market Size, Growth, Trends and Forecast 20242033 Adaptive Access Control System Effective access control must balance trust and risk. Dynamic security allows security managers to select the best control for achieving required security levels lively. Access control is an essential mechanism in collaborative environments, which guarantees the security of shared resources. Ibm verify uses machine learning and ai to analyze key parameters—user, device, activity,. Adaptive access control means your physical access. Adaptive Access Control System.
From allsecurityequipment.com
Linear Access Control Systems A Brand You Can Trust Adaptive Access Control System Ibm verify uses machine learning and ai to analyze key parameters—user, device, activity,. Adaptive access control means your physical access control system can be adapted easily, both functionally and operationally. Dynamic security allows security managers to select the best control for achieving required security levels lively. To reduce the risks of users abusing their privileges, we need to empower access. Adaptive Access Control System.
From www.businesstomark.com
The Benefits of a Custom Access Control System » Business to mark Adaptive Access Control System Access control is an essential mechanism in collaborative environments, which guarantees the security of shared resources. Adaptive access control means your physical access control system can be adapted easily, both functionally and operationally. Effective access control must balance trust and risk. Dynamic security allows security managers to select the best control for achieving required security levels lively. To reduce the. Adaptive Access Control System.
From fireaction.co.uk
Everything You Need to Know about Access Control Systems Fire Action Adaptive Access Control System Adaptive access control means your physical access control system can be adapted easily, both functionally and operationally. Access control is an essential mechanism in collaborative environments, which guarantees the security of shared resources. Dynamic security allows security managers to select the best control for achieving required security levels lively. To reduce the risks of users abusing their privileges, we need. Adaptive Access Control System.
From www.dayari.co.ke
Access Control System for Energy Infrastructure Dayari Kenya Adaptive Access Control System Ibm verify uses machine learning and ai to analyze key parameters—user, device, activity,. Effective access control must balance trust and risk. Adaptive access control means your physical access control system can be adapted easily, both functionally and operationally. Access control is an essential mechanism in collaborative environments, which guarantees the security of shared resources. To reduce the risks of users. Adaptive Access Control System.
From www.researchgate.net
The proposed adaptive riskbased access control model. Download Adaptive Access Control System To reduce the risks of users abusing their privileges, we need to empower access control with proactive measures that adapt. Ibm verify uses machine learning and ai to analyze key parameters—user, device, activity,. Adaptive access control means your physical access control system can be adapted easily, both functionally and operationally. Dynamic security allows security managers to select the best control. Adaptive Access Control System.
From cie-group.com
How to design an Access Control system Adaptive Access Control System Dynamic security allows security managers to select the best control for achieving required security levels lively. To reduce the risks of users abusing their privileges, we need to empower access control with proactive measures that adapt. Effective access control must balance trust and risk. Access control is an essential mechanism in collaborative environments, which guarantees the security of shared resources.. Adaptive Access Control System.
From www.researchgate.net
Proposed Adaptive Rolebased Access Control Mechanism Download Adaptive Access Control System To reduce the risks of users abusing their privileges, we need to empower access control with proactive measures that adapt. Access control is an essential mechanism in collaborative environments, which guarantees the security of shared resources. Adaptive access control means your physical access control system can be adapted easily, both functionally and operationally. Ibm verify uses machine learning and ai. Adaptive Access Control System.
From www.mdpi.com
Electronics Free FullText LACE LowCost Access Control Based on Adaptive Access Control System Adaptive access control means your physical access control system can be adapted easily, both functionally and operationally. Dynamic security allows security managers to select the best control for achieving required security levels lively. To reduce the risks of users abusing their privileges, we need to empower access control with proactive measures that adapt. Ibm verify uses machine learning and ai. Adaptive Access Control System.
From kintronics.com
Access Control Installation Kintronics Adaptive Access Control System Ibm verify uses machine learning and ai to analyze key parameters—user, device, activity,. Adaptive access control means your physical access control system can be adapted easily, both functionally and operationally. To reduce the risks of users abusing their privileges, we need to empower access control with proactive measures that adapt. Access control is an essential mechanism in collaborative environments, which. Adaptive Access Control System.
From instrumentationtools.com
What is Adaptive Control? Direct & Indirect Systems Adaptive Access Control System Dynamic security allows security managers to select the best control for achieving required security levels lively. Effective access control must balance trust and risk. Adaptive access control means your physical access control system can be adapted easily, both functionally and operationally. Ibm verify uses machine learning and ai to analyze key parameters—user, device, activity,. Access control is an essential mechanism. Adaptive Access Control System.
From www.researchgate.net
(PDF) Adaptive Access Control Policies for IoT Deployments Adaptive Access Control System Ibm verify uses machine learning and ai to analyze key parameters—user, device, activity,. Effective access control must balance trust and risk. Access control is an essential mechanism in collaborative environments, which guarantees the security of shared resources. Dynamic security allows security managers to select the best control for achieving required security levels lively. To reduce the risks of users abusing. Adaptive Access Control System.
From adaptiverecognition.com
Solutions for Access Control Systems Operators Adaptive Recognition Adaptive Access Control System Adaptive access control means your physical access control system can be adapted easily, both functionally and operationally. Ibm verify uses machine learning and ai to analyze key parameters—user, device, activity,. To reduce the risks of users abusing their privileges, we need to empower access control with proactive measures that adapt. Effective access control must balance trust and risk. Dynamic security. Adaptive Access Control System.
From www.nedapsecurity.com
The Ultimate Guide to Physical Access Control Systems in 2023 Adaptive Access Control System Effective access control must balance trust and risk. To reduce the risks of users abusing their privileges, we need to empower access control with proactive measures that adapt. Access control is an essential mechanism in collaborative environments, which guarantees the security of shared resources. Ibm verify uses machine learning and ai to analyze key parameters—user, device, activity,. Adaptive access control. Adaptive Access Control System.
From www.3siraq.com
نظام الاكسس كنترول Access Control System Adaptive Access Control System Dynamic security allows security managers to select the best control for achieving required security levels lively. Adaptive access control means your physical access control system can be adapted easily, both functionally and operationally. Effective access control must balance trust and risk. To reduce the risks of users abusing their privileges, we need to empower access control with proactive measures that. Adaptive Access Control System.
From www.indiamart.com
Building Access Control Systems, Access Control Series, Access Control Adaptive Access Control System Access control is an essential mechanism in collaborative environments, which guarantees the security of shared resources. To reduce the risks of users abusing their privileges, we need to empower access control with proactive measures that adapt. Effective access control must balance trust and risk. Dynamic security allows security managers to select the best control for achieving required security levels lively.. Adaptive Access Control System.
From docs.verify.ibm.com
Adaptive access Adaptive Access Control System Adaptive access control means your physical access control system can be adapted easily, both functionally and operationally. Access control is an essential mechanism in collaborative environments, which guarantees the security of shared resources. Dynamic security allows security managers to select the best control for achieving required security levels lively. Effective access control must balance trust and risk. To reduce the. Adaptive Access Control System.
From www.360connect.com
Office Access Control Systems 360Connect Adaptive Access Control System Adaptive access control means your physical access control system can be adapted easily, both functionally and operationally. Access control is an essential mechanism in collaborative environments, which guarantees the security of shared resources. Ibm verify uses machine learning and ai to analyze key parameters—user, device, activity,. To reduce the risks of users abusing their privileges, we need to empower access. Adaptive Access Control System.