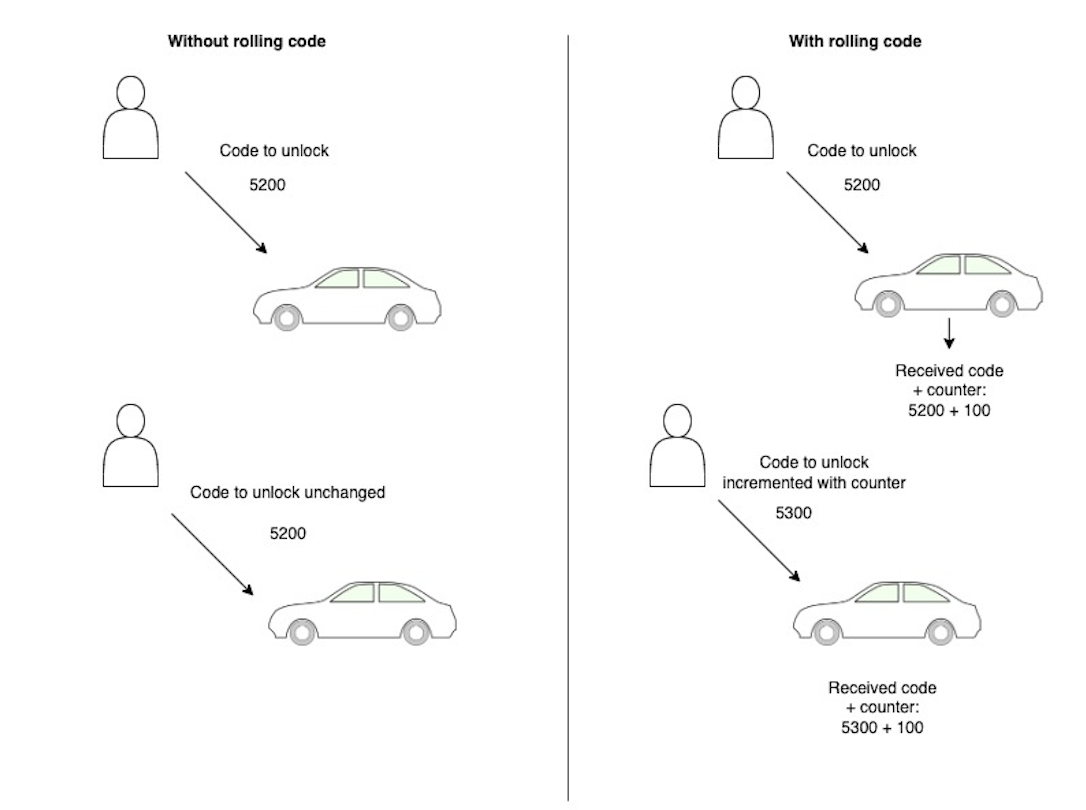
Rolling Code Attack . Thus, a remote control that uses the rolling code feature generates a new code every time we press a button. Most car manufacturers nowadays practice a keyless entry system called rolling codes. In a nutshell, by using a careful. The basic idea is to make it difficult for an attacker to intercept and replicate any code exchanged between the transmitter and receiver. This was put into place to counter replay attacks, in which the attacker captures. When a rolling code receiver gets a message with a keyfob serial number that seems to match one of the authorized keyfobs in its internal.
from istrosec.com
Thus, a remote control that uses the rolling code feature generates a new code every time we press a button. Most car manufacturers nowadays practice a keyless entry system called rolling codes. This was put into place to counter replay attacks, in which the attacker captures. When a rolling code receiver gets a message with a keyfob serial number that seems to match one of the authorized keyfobs in its internal. In a nutshell, by using a careful. The basic idea is to make it difficult for an attacker to intercept and replicate any code exchanged between the transmitter and receiver.
CVE202227254 technical description
Rolling Code Attack Thus, a remote control that uses the rolling code feature generates a new code every time we press a button. The basic idea is to make it difficult for an attacker to intercept and replicate any code exchanged between the transmitter and receiver. Most car manufacturers nowadays practice a keyless entry system called rolling codes. In a nutshell, by using a careful. Thus, a remote control that uses the rolling code feature generates a new code every time we press a button. This was put into place to counter replay attacks, in which the attacker captures. When a rolling code receiver gets a message with a keyfob serial number that seems to match one of the authorized keyfobs in its internal.
From www.youtube.com
Estudio del Rolling Code ¿ Que necesitamos para empezar ? YouTube Rolling Code Attack This was put into place to counter replay attacks, in which the attacker captures. In a nutshell, by using a careful. The basic idea is to make it difficult for an attacker to intercept and replicate any code exchanged between the transmitter and receiver. When a rolling code receiver gets a message with a keyfob serial number that seems to. Rolling Code Attack.
From www.youtube.com
Rolling codes Hacking on RF Locks YouTube Rolling Code Attack When a rolling code receiver gets a message with a keyfob serial number that seems to match one of the authorized keyfobs in its internal. In a nutshell, by using a careful. Thus, a remote control that uses the rolling code feature generates a new code every time we press a button. The basic idea is to make it difficult. Rolling Code Attack.
From hackernoon.com
Signal Amplification Relay Attack (SARA) HackerNoon Rolling Code Attack Thus, a remote control that uses the rolling code feature generates a new code every time we press a button. When a rolling code receiver gets a message with a keyfob serial number that seems to match one of the authorized keyfobs in its internal. In a nutshell, by using a careful. This was put into place to counter replay. Rolling Code Attack.
From hackaday.com
Hacking Rolling Code Keyfobs Hackaday Rolling Code Attack The basic idea is to make it difficult for an attacker to intercept and replicate any code exchanged between the transmitter and receiver. Most car manufacturers nowadays practice a keyless entry system called rolling codes. In a nutshell, by using a careful. When a rolling code receiver gets a message with a keyfob serial number that seems to match one. Rolling Code Attack.
From www.youtube.com
I Hacked My OWN car using Replay Attack HackRF & Universal Radio Rolling Code Attack Thus, a remote control that uses the rolling code feature generates a new code every time we press a button. In a nutshell, by using a careful. This was put into place to counter replay attacks, in which the attacker captures. Most car manufacturers nowadays practice a keyless entry system called rolling codes. The basic idea is to make it. Rolling Code Attack.
From www.riyas.org
Learn on the fly A simple RF remote with code hopping or rolling code Rolling Code Attack This was put into place to counter replay attacks, in which the attacker captures. Thus, a remote control that uses the rolling code feature generates a new code every time we press a button. In a nutshell, by using a careful. When a rolling code receiver gets a message with a keyfob serial number that seems to match one of. Rolling Code Attack.
From www.andrewmohawk.com
Bypassing Rolling Code Systems AndrewNohawk Rolling Code Attack When a rolling code receiver gets a message with a keyfob serial number that seems to match one of the authorized keyfobs in its internal. In a nutshell, by using a careful. The basic idea is to make it difficult for an attacker to intercept and replicate any code exchanged between the transmitter and receiver. Most car manufacturers nowadays practice. Rolling Code Attack.
From www.semanticscholar.org
Figure 1 from Vehicle Relay Attack Avoidance Methods Using RF Signal Rolling Code Attack Most car manufacturers nowadays practice a keyless entry system called rolling codes. This was put into place to counter replay attacks, in which the attacker captures. The basic idea is to make it difficult for an attacker to intercept and replicate any code exchanged between the transmitter and receiver. In a nutshell, by using a careful. Thus, a remote control. Rolling Code Attack.
From pandwarf.com
New rolling code Click & Transmit mode in Android app PandwaRF Rolling Code Attack In a nutshell, by using a careful. The basic idea is to make it difficult for an attacker to intercept and replicate any code exchanged between the transmitter and receiver. This was put into place to counter replay attacks, in which the attacker captures. When a rolling code receiver gets a message with a keyfob serial number that seems to. Rolling Code Attack.
From www.youtube.com
Program fixed code and rolling code simple CAME TOP with NoNo Rolling Code Attack Thus, a remote control that uses the rolling code feature generates a new code every time we press a button. This was put into place to counter replay attacks, in which the attacker captures. The basic idea is to make it difficult for an attacker to intercept and replicate any code exchanged between the transmitter and receiver. Most car manufacturers. Rolling Code Attack.
From noticiasseguridad.com
Cómo hackear un auto con vulnerabilidades de Remote Keyless Entry (RKE) Rolling Code Attack This was put into place to counter replay attacks, in which the attacker captures. When a rolling code receiver gets a message with a keyfob serial number that seems to match one of the authorized keyfobs in its internal. In a nutshell, by using a careful. Thus, a remote control that uses the rolling code feature generates a new code. Rolling Code Attack.
From harryli0088.github.io
How Rolling Code Works Rolling Code Attack In a nutshell, by using a careful. The basic idea is to make it difficult for an attacker to intercept and replicate any code exchanged between the transmitter and receiver. When a rolling code receiver gets a message with a keyfob serial number that seems to match one of the authorized keyfobs in its internal. Most car manufacturers nowadays practice. Rolling Code Attack.
From pandwarf.com
Gate opener receiver test device (rolling code) PandwaRF Rolling Code Attack The basic idea is to make it difficult for an attacker to intercept and replicate any code exchanged between the transmitter and receiver. In a nutshell, by using a careful. Thus, a remote control that uses the rolling code feature generates a new code every time we press a button. Most car manufacturers nowadays practice a keyless entry system called. Rolling Code Attack.
From eightify.app
How secure are rolling codes against replay and jamming attacks? Eightify Rolling Code Attack This was put into place to counter replay attacks, in which the attacker captures. Thus, a remote control that uses the rolling code feature generates a new code every time we press a button. Most car manufacturers nowadays practice a keyless entry system called rolling codes. The basic idea is to make it difficult for an attacker to intercept and. Rolling Code Attack.
From www.youtube.com
6. jam and replay rolling code rolljam codegrabbing YouTube Rolling Code Attack The basic idea is to make it difficult for an attacker to intercept and replicate any code exchanged between the transmitter and receiver. In a nutshell, by using a careful. When a rolling code receiver gets a message with a keyfob serial number that seems to match one of the authorized keyfobs in its internal. Thus, a remote control that. Rolling Code Attack.
From www.andrewmohawk.com
Bypassing Rolling Code Systems AndrewNohawk Rolling Code Attack This was put into place to counter replay attacks, in which the attacker captures. The basic idea is to make it difficult for an attacker to intercept and replicate any code exchanged between the transmitter and receiver. Most car manufacturers nowadays practice a keyless entry system called rolling codes. Thus, a remote control that uses the rolling code feature generates. Rolling Code Attack.
From www.tindie.com
Rolling Code Transmitter and Receiver from CraftyCrow on Tindie Rolling Code Attack When a rolling code receiver gets a message with a keyfob serial number that seems to match one of the authorized keyfobs in its internal. This was put into place to counter replay attacks, in which the attacker captures. Most car manufacturers nowadays practice a keyless entry system called rolling codes. In a nutshell, by using a careful. Thus, a. Rolling Code Attack.
From istrosec.com
CVE202227254 technical description Rolling Code Attack The basic idea is to make it difficult for an attacker to intercept and replicate any code exchanged between the transmitter and receiver. When a rolling code receiver gets a message with a keyfob serial number that seems to match one of the authorized keyfobs in its internal. In a nutshell, by using a careful. Thus, a remote control that. Rolling Code Attack.
From s34s0n.github.io
Jam and Replay Attacks on Vehicular Keyless Entry Systems Rolling Code Attack Most car manufacturers nowadays practice a keyless entry system called rolling codes. In a nutshell, by using a careful. The basic idea is to make it difficult for an attacker to intercept and replicate any code exchanged between the transmitter and receiver. This was put into place to counter replay attacks, in which the attacker captures. When a rolling code. Rolling Code Attack.
From eightify.app
How secure are rolling codes against replay and jamming attacks? Eightify Rolling Code Attack Most car manufacturers nowadays practice a keyless entry system called rolling codes. In a nutshell, by using a careful. The basic idea is to make it difficult for an attacker to intercept and replicate any code exchanged between the transmitter and receiver. This was put into place to counter replay attacks, in which the attacker captures. When a rolling code. Rolling Code Attack.
From www.riyas.org
Learn on the fly A simple RF remote with code hopping or rolling code Rolling Code Attack In a nutshell, by using a careful. The basic idea is to make it difficult for an attacker to intercept and replicate any code exchanged between the transmitter and receiver. When a rolling code receiver gets a message with a keyfob serial number that seems to match one of the authorized keyfobs in its internal. Thus, a remote control that. Rolling Code Attack.
From www.youtube.com
Rolling Codes Explained part 2. I hacked my own garage door Rolling Code Attack Thus, a remote control that uses the rolling code feature generates a new code every time we press a button. The basic idea is to make it difficult for an attacker to intercept and replicate any code exchanged between the transmitter and receiver. This was put into place to counter replay attacks, in which the attacker captures. Most car manufacturers. Rolling Code Attack.
From www.victoriana.com
vielversprechend Namentlich Schutz rolling code arduino Verbesserung Rolling Code Attack Thus, a remote control that uses the rolling code feature generates a new code every time we press a button. The basic idea is to make it difficult for an attacker to intercept and replicate any code exchanged between the transmitter and receiver. This was put into place to counter replay attacks, in which the attacker captures. When a rolling. Rolling Code Attack.
From forum.flipper.net
Rolling CODE with CAME SPACE problem Flipper Forum Rolling Code Attack Most car manufacturers nowadays practice a keyless entry system called rolling codes. In a nutshell, by using a careful. Thus, a remote control that uses the rolling code feature generates a new code every time we press a button. When a rolling code receiver gets a message with a keyfob serial number that seems to match one of the authorized. Rolling Code Attack.
From andrewmohawk.com
Bypassing Rolling Code Systems « AndrewNohawk Rolling Code Attack Most car manufacturers nowadays practice a keyless entry system called rolling codes. When a rolling code receiver gets a message with a keyfob serial number that seems to match one of the authorized keyfobs in its internal. Thus, a remote control that uses the rolling code feature generates a new code every time we press a button. In a nutshell,. Rolling Code Attack.
From www.youtube.com
What is Shrink Wrap Code Attack Detail Video in Hindi YouTube Rolling Code Attack Thus, a remote control that uses the rolling code feature generates a new code every time we press a button. This was put into place to counter replay attacks, in which the attacker captures. When a rolling code receiver gets a message with a keyfob serial number that seems to match one of the authorized keyfobs in its internal. The. Rolling Code Attack.
From www.youtube.com
Autos hacken mit Flipper Zero! 😱 Replay Attacks & Rolling Codes erklärt Rolling Code Attack This was put into place to counter replay attacks, in which the attacker captures. When a rolling code receiver gets a message with a keyfob serial number that seems to match one of the authorized keyfobs in its internal. Most car manufacturers nowadays practice a keyless entry system called rolling codes. In a nutshell, by using a careful. Thus, a. Rolling Code Attack.
From www.baeldung.com
How Does Rolling Code Work? Baeldung on Computer Science Rolling Code Attack When a rolling code receiver gets a message with a keyfob serial number that seems to match one of the authorized keyfobs in its internal. In a nutshell, by using a careful. Thus, a remote control that uses the rolling code feature generates a new code every time we press a button. Most car manufacturers nowadays practice a keyless entry. Rolling Code Attack.
From pandwarf.com
Kaiju Rolling code analyzer & generator PandwaRF Rolling Code Attack The basic idea is to make it difficult for an attacker to intercept and replicate any code exchanged between the transmitter and receiver. This was put into place to counter replay attacks, in which the attacker captures. Most car manufacturers nowadays practice a keyless entry system called rolling codes. In a nutshell, by using a careful. When a rolling code. Rolling Code Attack.
From www.bleepingcomputer.com
Hackers can unlock Honda cars remotely in RollingPWN attacks Rolling Code Attack Most car manufacturers nowadays practice a keyless entry system called rolling codes. In a nutshell, by using a careful. Thus, a remote control that uses the rolling code feature generates a new code every time we press a button. The basic idea is to make it difficult for an attacker to intercept and replicate any code exchanged between the transmitter. Rolling Code Attack.
From www.youtube.com
¿Cómo programar tu control Rolling Code copiador de Ferrecent? YouTube Rolling Code Attack Most car manufacturers nowadays practice a keyless entry system called rolling codes. Thus, a remote control that uses the rolling code feature generates a new code every time we press a button. The basic idea is to make it difficult for an attacker to intercept and replicate any code exchanged between the transmitter and receiver. In a nutshell, by using. Rolling Code Attack.
From pandwarf.com
New rolling code Click & Transmit mode in Android app PandwaRF Rolling Code Attack When a rolling code receiver gets a message with a keyfob serial number that seems to match one of the authorized keyfobs in its internal. In a nutshell, by using a careful. Thus, a remote control that uses the rolling code feature generates a new code every time we press a button. Most car manufacturers nowadays practice a keyless entry. Rolling Code Attack.
From www.dhgate.com
2018 Rolling Code Code Grabber Combination Packages Shadowless Code Rolling Code Attack When a rolling code receiver gets a message with a keyfob serial number that seems to match one of the authorized keyfobs in its internal. The basic idea is to make it difficult for an attacker to intercept and replicate any code exchanged between the transmitter and receiver. Thus, a remote control that uses the rolling code feature generates a. Rolling Code Attack.
From pandwarf.com
Kaiju Rolling code analyzer & generator PandwaRF Rolling Code Attack When a rolling code receiver gets a message with a keyfob serial number that seems to match one of the authorized keyfobs in its internal. Thus, a remote control that uses the rolling code feature generates a new code every time we press a button. This was put into place to counter replay attacks, in which the attacker captures. In. Rolling Code Attack.
From www.radware.com
7 Most Common Attack Types Application Firewall (WAF) Is Designed Rolling Code Attack This was put into place to counter replay attacks, in which the attacker captures. The basic idea is to make it difficult for an attacker to intercept and replicate any code exchanged between the transmitter and receiver. Most car manufacturers nowadays practice a keyless entry system called rolling codes. When a rolling code receiver gets a message with a keyfob. Rolling Code Attack.