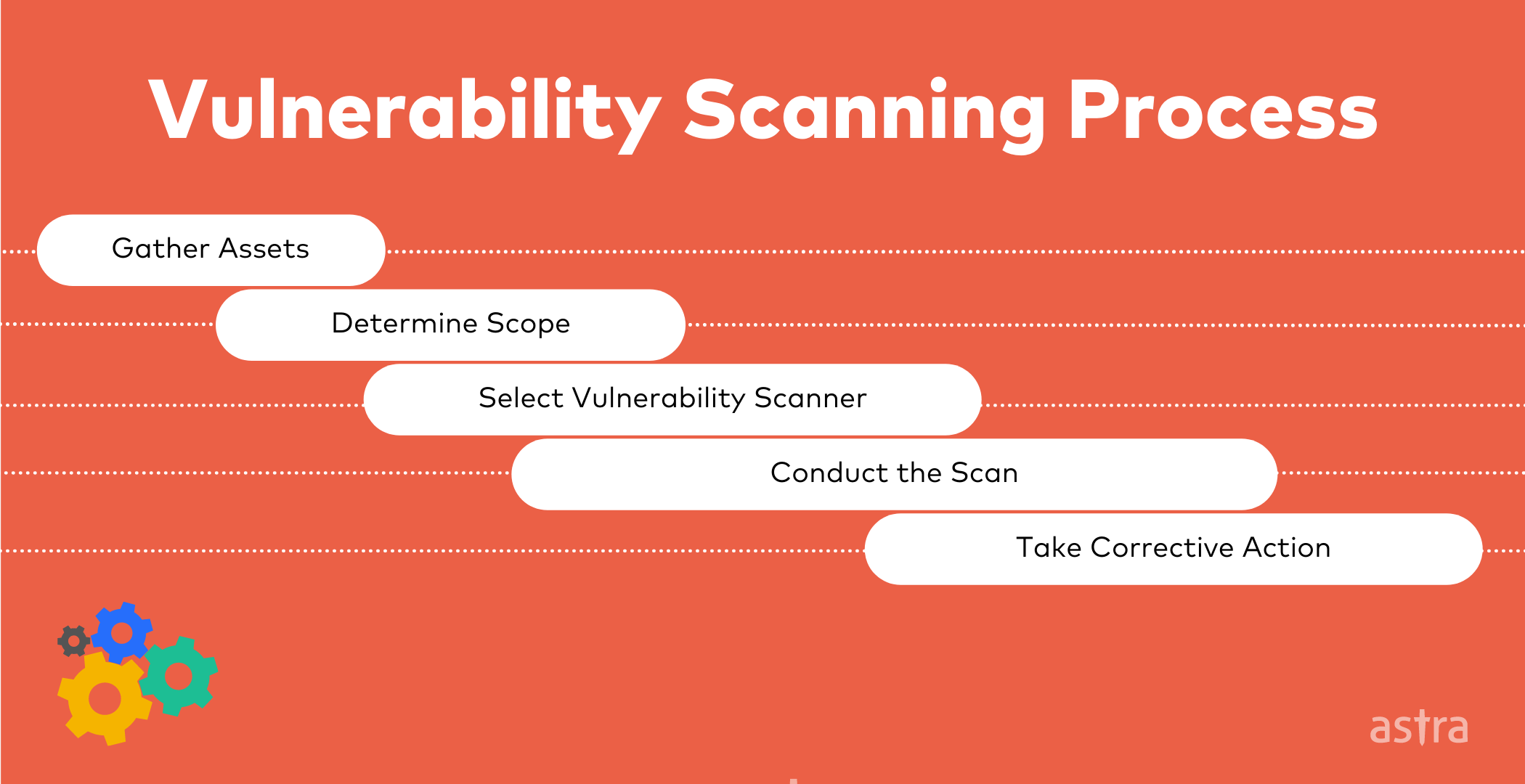
How To Perform External Vulnerability Scan . By performing external vulnerability scanning, organizations can proactively identify and address security weaknesses in their external network perimeter, reducing. Best for comprehensive website and. Discover the best tools and techniques for scanning your systems. Pci dss requires two independent methods of pci scanning: The vulnerability scanner identifies and creates an inventory of all systems connected to a. Best overall vulnerability scanner and enterprise vulscan option. An external vulnerability scan is performed outside of your network (e.g., at your network. Vulnerability scanning is the process of detecting and evaluating security flaws in it systems, networks, and software. Running an external vulnerability scan (or perimeter scan) is critical for ensuring that the perimeter of your network doesn’t have any glaring.
from www.getastra.com
The vulnerability scanner identifies and creates an inventory of all systems connected to a. By performing external vulnerability scanning, organizations can proactively identify and address security weaknesses in their external network perimeter, reducing. An external vulnerability scan is performed outside of your network (e.g., at your network. Discover the best tools and techniques for scanning your systems. Best overall vulnerability scanner and enterprise vulscan option. Running an external vulnerability scan (or perimeter scan) is critical for ensuring that the perimeter of your network doesn’t have any glaring. Vulnerability scanning is the process of detecting and evaluating security flaws in it systems, networks, and software. Best for comprehensive website and. Pci dss requires two independent methods of pci scanning:
Vulnerability Scanning Process and Types Astra Security Blog
How To Perform External Vulnerability Scan Pci dss requires two independent methods of pci scanning: Pci dss requires two independent methods of pci scanning: By performing external vulnerability scanning, organizations can proactively identify and address security weaknesses in their external network perimeter, reducing. Best overall vulnerability scanner and enterprise vulscan option. Discover the best tools and techniques for scanning your systems. Best for comprehensive website and. The vulnerability scanner identifies and creates an inventory of all systems connected to a. An external vulnerability scan is performed outside of your network (e.g., at your network. Running an external vulnerability scan (or perimeter scan) is critical for ensuring that the perimeter of your network doesn’t have any glaring. Vulnerability scanning is the process of detecting and evaluating security flaws in it systems, networks, and software.
From www.comparitech.com
How to Perform an External Vulnerability Scan (& Detect Vulnerabilties) How To Perform External Vulnerability Scan Best overall vulnerability scanner and enterprise vulscan option. By performing external vulnerability scanning, organizations can proactively identify and address security weaknesses in their external network perimeter, reducing. Running an external vulnerability scan (or perimeter scan) is critical for ensuring that the perimeter of your network doesn’t have any glaring. Vulnerability scanning is the process of detecting and evaluating security flaws. How To Perform External Vulnerability Scan.
From www.locknetmanagedit.com
Vulnerability Scanning What It Is and Why You Need It How To Perform External Vulnerability Scan The vulnerability scanner identifies and creates an inventory of all systems connected to a. Best for comprehensive website and. Vulnerability scanning is the process of detecting and evaluating security flaws in it systems, networks, and software. Running an external vulnerability scan (or perimeter scan) is critical for ensuring that the perimeter of your network doesn’t have any glaring. Discover the. How To Perform External Vulnerability Scan.
From loezhhvpb.blob.core.windows.net
Ip Camera Vulnerability Scanner at Helene Thompson blog How To Perform External Vulnerability Scan By performing external vulnerability scanning, organizations can proactively identify and address security weaknesses in their external network perimeter, reducing. The vulnerability scanner identifies and creates an inventory of all systems connected to a. Best for comprehensive website and. Best overall vulnerability scanner and enterprise vulscan option. Vulnerability scanning is the process of detecting and evaluating security flaws in it systems,. How To Perform External Vulnerability Scan.
From www.enterprisenetworkingplanet.com
What Is Network Vulnerability Scanning? Complete Guide How To Perform External Vulnerability Scan Running an external vulnerability scan (or perimeter scan) is critical for ensuring that the perimeter of your network doesn’t have any glaring. Vulnerability scanning is the process of detecting and evaluating security flaws in it systems, networks, and software. Best overall vulnerability scanner and enterprise vulscan option. By performing external vulnerability scanning, organizations can proactively identify and address security weaknesses. How To Perform External Vulnerability Scan.
From www.corvid.co.uk
CORVID Vulnerability Scanning Services Security Scanning How To Perform External Vulnerability Scan Best for comprehensive website and. The vulnerability scanner identifies and creates an inventory of all systems connected to a. Running an external vulnerability scan (or perimeter scan) is critical for ensuring that the perimeter of your network doesn’t have any glaring. Vulnerability scanning is the process of detecting and evaluating security flaws in it systems, networks, and software. Discover the. How To Perform External Vulnerability Scan.
From www.techtarget.com
Types of vulnerability scanning and when to use each TechTarget How To Perform External Vulnerability Scan Discover the best tools and techniques for scanning your systems. Pci dss requires two independent methods of pci scanning: Vulnerability scanning is the process of detecting and evaluating security flaws in it systems, networks, and software. An external vulnerability scan is performed outside of your network (e.g., at your network. Running an external vulnerability scan (or perimeter scan) is critical. How To Perform External Vulnerability Scan.
From blog.securitymetrics.com
Vulnerability Scanners 101 What, Why, and How to Comply How To Perform External Vulnerability Scan Best overall vulnerability scanner and enterprise vulscan option. The vulnerability scanner identifies and creates an inventory of all systems connected to a. Best for comprehensive website and. Vulnerability scanning is the process of detecting and evaluating security flaws in it systems, networks, and software. Discover the best tools and techniques for scanning your systems. An external vulnerability scan is performed. How To Perform External Vulnerability Scan.
From www.youtube.com
3 External Vulnerability Scans YouTube How To Perform External Vulnerability Scan An external vulnerability scan is performed outside of your network (e.g., at your network. Best for comprehensive website and. Vulnerability scanning is the process of detecting and evaluating security flaws in it systems, networks, and software. Running an external vulnerability scan (or perimeter scan) is critical for ensuring that the perimeter of your network doesn’t have any glaring. By performing. How To Perform External Vulnerability Scan.
From www.linkedin.com
Newsflash How to Perform a Vulnerability Scan in 10 Steps How To Perform External Vulnerability Scan By performing external vulnerability scanning, organizations can proactively identify and address security weaknesses in their external network perimeter, reducing. Running an external vulnerability scan (or perimeter scan) is critical for ensuring that the perimeter of your network doesn’t have any glaring. Discover the best tools and techniques for scanning your systems. Best overall vulnerability scanner and enterprise vulscan option. The. How To Perform External Vulnerability Scan.
From www.linkedin.com
How do external vulnerability scans provide the external temperature of How To Perform External Vulnerability Scan Discover the best tools and techniques for scanning your systems. By performing external vulnerability scanning, organizations can proactively identify and address security weaknesses in their external network perimeter, reducing. Best for comprehensive website and. An external vulnerability scan is performed outside of your network (e.g., at your network. Best overall vulnerability scanner and enterprise vulscan option. Pci dss requires two. How To Perform External Vulnerability Scan.
From www.g2.com
Vulnerability Scanners Types, Benefits, And Top 5 Scanners How To Perform External Vulnerability Scan The vulnerability scanner identifies and creates an inventory of all systems connected to a. Vulnerability scanning is the process of detecting and evaluating security flaws in it systems, networks, and software. Discover the best tools and techniques for scanning your systems. Pci dss requires two independent methods of pci scanning: By performing external vulnerability scanning, organizations can proactively identify and. How To Perform External Vulnerability Scan.
From consultdts.com
Nist 800171 Vulnerability scanning, game changer cyber security How To Perform External Vulnerability Scan The vulnerability scanner identifies and creates an inventory of all systems connected to a. Best overall vulnerability scanner and enterprise vulscan option. Pci dss requires two independent methods of pci scanning: By performing external vulnerability scanning, organizations can proactively identify and address security weaknesses in their external network perimeter, reducing. Vulnerability scanning is the process of detecting and evaluating security. How To Perform External Vulnerability Scan.
From www.getastra.com
Vulnerability Scanning Process and Types Astra Security Blog How To Perform External Vulnerability Scan An external vulnerability scan is performed outside of your network (e.g., at your network. Running an external vulnerability scan (or perimeter scan) is critical for ensuring that the perimeter of your network doesn’t have any glaring. Best for comprehensive website and. Pci dss requires two independent methods of pci scanning: Discover the best tools and techniques for scanning your systems.. How To Perform External Vulnerability Scan.
From alertcyber.com
Vulnerability Scanner Vulnerability Management Alert IT How To Perform External Vulnerability Scan By performing external vulnerability scanning, organizations can proactively identify and address security weaknesses in their external network perimeter, reducing. An external vulnerability scan is performed outside of your network (e.g., at your network. Discover the best tools and techniques for scanning your systems. The vulnerability scanner identifies and creates an inventory of all systems connected to a. Best for comprehensive. How To Perform External Vulnerability Scan.
From cybersecurity.att.com
External Vulnerability Scanning AT&T Cybersecurity How To Perform External Vulnerability Scan Best overall vulnerability scanner and enterprise vulscan option. Discover the best tools and techniques for scanning your systems. The vulnerability scanner identifies and creates an inventory of all systems connected to a. Best for comprehensive website and. Pci dss requires two independent methods of pci scanning: Running an external vulnerability scan (or perimeter scan) is critical for ensuring that the. How To Perform External Vulnerability Scan.
From www.clone-systems.com
Vulnerability Assessment Clone Systems, Inc. How To Perform External Vulnerability Scan Best for comprehensive website and. Running an external vulnerability scan (or perimeter scan) is critical for ensuring that the perimeter of your network doesn’t have any glaring. Discover the best tools and techniques for scanning your systems. By performing external vulnerability scanning, organizations can proactively identify and address security weaknesses in their external network perimeter, reducing. The vulnerability scanner identifies. How To Perform External Vulnerability Scan.
From sprinto.com
11 Best Vulnerability Scanning Tools You Must Know in 2024 Sprinto How To Perform External Vulnerability Scan Best overall vulnerability scanner and enterprise vulscan option. Pci dss requires two independent methods of pci scanning: Vulnerability scanning is the process of detecting and evaluating security flaws in it systems, networks, and software. The vulnerability scanner identifies and creates an inventory of all systems connected to a. Running an external vulnerability scan (or perimeter scan) is critical for ensuring. How To Perform External Vulnerability Scan.
From hackcontrol.org
The ultimate guide to vulnerability scanning best practices How To Perform External Vulnerability Scan Discover the best tools and techniques for scanning your systems. The vulnerability scanner identifies and creates an inventory of all systems connected to a. An external vulnerability scan is performed outside of your network (e.g., at your network. Best overall vulnerability scanner and enterprise vulscan option. Best for comprehensive website and. By performing external vulnerability scanning, organizations can proactively identify. How To Perform External Vulnerability Scan.
From www.intruder.io
Vulnerability Scanning Frequency Best Practices Intruder How To Perform External Vulnerability Scan Best overall vulnerability scanner and enterprise vulscan option. Discover the best tools and techniques for scanning your systems. Best for comprehensive website and. By performing external vulnerability scanning, organizations can proactively identify and address security weaknesses in their external network perimeter, reducing. Vulnerability scanning is the process of detecting and evaluating security flaws in it systems, networks, and software. Running. How To Perform External Vulnerability Scan.
From grcassist.com
External Network Vulnerability Scan GRC Assist How To Perform External Vulnerability Scan An external vulnerability scan is performed outside of your network (e.g., at your network. Vulnerability scanning is the process of detecting and evaluating security flaws in it systems, networks, and software. Best for comprehensive website and. Best overall vulnerability scanner and enterprise vulscan option. Pci dss requires two independent methods of pci scanning: Discover the best tools and techniques for. How To Perform External Vulnerability Scan.
From thecyphere.com
Types Of Vulnerability Scanning Cloud & site Scanners How To Perform External Vulnerability Scan The vulnerability scanner identifies and creates an inventory of all systems connected to a. Vulnerability scanning is the process of detecting and evaluating security flaws in it systems, networks, and software. An external vulnerability scan is performed outside of your network (e.g., at your network. By performing external vulnerability scanning, organizations can proactively identify and address security weaknesses in their. How To Perform External Vulnerability Scan.
From www.intruder.io
External Vulnerability Scanner Intruder How To Perform External Vulnerability Scan Vulnerability scanning is the process of detecting and evaluating security flaws in it systems, networks, and software. Best for comprehensive website and. The vulnerability scanner identifies and creates an inventory of all systems connected to a. An external vulnerability scan is performed outside of your network (e.g., at your network. Pci dss requires two independent methods of pci scanning: Discover. How To Perform External Vulnerability Scan.
From www.researchgate.net
Vulnerability Scanner System Diagram Download Scientific Diagram How To Perform External Vulnerability Scan Pci dss requires two independent methods of pci scanning: Best overall vulnerability scanner and enterprise vulscan option. By performing external vulnerability scanning, organizations can proactively identify and address security weaknesses in their external network perimeter, reducing. Best for comprehensive website and. Vulnerability scanning is the process of detecting and evaluating security flaws in it systems, networks, and software. An external. How To Perform External Vulnerability Scan.
From docs.paloaltonetworks.com
Perform a Vulnerability Scan Using Qualys How To Perform External Vulnerability Scan Best for comprehensive website and. Discover the best tools and techniques for scanning your systems. An external vulnerability scan is performed outside of your network (e.g., at your network. The vulnerability scanner identifies and creates an inventory of all systems connected to a. Best overall vulnerability scanner and enterprise vulscan option. By performing external vulnerability scanning, organizations can proactively identify. How To Perform External Vulnerability Scan.
From blog.charlesit.com
What is External Vulnerability Scanning? How To Perform External Vulnerability Scan An external vulnerability scan is performed outside of your network (e.g., at your network. Discover the best tools and techniques for scanning your systems. Best for comprehensive website and. Vulnerability scanning is the process of detecting and evaluating security flaws in it systems, networks, and software. Best overall vulnerability scanner and enterprise vulscan option. The vulnerability scanner identifies and creates. How To Perform External Vulnerability Scan.
From www.intruder.io
How To Perform A Vulnerability Assessment StepbyStep How To Perform External Vulnerability Scan Pci dss requires two independent methods of pci scanning: An external vulnerability scan is performed outside of your network (e.g., at your network. Discover the best tools and techniques for scanning your systems. Vulnerability scanning is the process of detecting and evaluating security flaws in it systems, networks, and software. Best overall vulnerability scanner and enterprise vulscan option. The vulnerability. How To Perform External Vulnerability Scan.
From www.sapphire.net
Network Vulnerability Scanning Types & Tools Sapphire How To Perform External Vulnerability Scan An external vulnerability scan is performed outside of your network (e.g., at your network. Pci dss requires two independent methods of pci scanning: By performing external vulnerability scanning, organizations can proactively identify and address security weaknesses in their external network perimeter, reducing. The vulnerability scanner identifies and creates an inventory of all systems connected to a. Discover the best tools. How To Perform External Vulnerability Scan.
From www.pentestpeople.com
External Vulnerability Scanning How To Perform External Vulnerability Scan Pci dss requires two independent methods of pci scanning: Best for comprehensive website and. Discover the best tools and techniques for scanning your systems. Best overall vulnerability scanner and enterprise vulscan option. An external vulnerability scan is performed outside of your network (e.g., at your network. Running an external vulnerability scan (or perimeter scan) is critical for ensuring that the. How To Perform External Vulnerability Scan.
From www.slideserve.com
PPT How Vulnerability Scanning Works PowerPoint Presentation, free How To Perform External Vulnerability Scan An external vulnerability scan is performed outside of your network (e.g., at your network. By performing external vulnerability scanning, organizations can proactively identify and address security weaknesses in their external network perimeter, reducing. Discover the best tools and techniques for scanning your systems. Best overall vulnerability scanner and enterprise vulscan option. Running an external vulnerability scan (or perimeter scan) is. How To Perform External Vulnerability Scan.
From purplesec.us
What Is A Network Vulnerability? PurpleSec How To Perform External Vulnerability Scan Vulnerability scanning is the process of detecting and evaluating security flaws in it systems, networks, and software. By performing external vulnerability scanning, organizations can proactively identify and address security weaknesses in their external network perimeter, reducing. Best for comprehensive website and. Best overall vulnerability scanner and enterprise vulscan option. An external vulnerability scan is performed outside of your network (e.g.,. How To Perform External Vulnerability Scan.
From www.datamation.com
How to Easily Run a Vulnerability Scan Using Nmap Datamation How To Perform External Vulnerability Scan Best overall vulnerability scanner and enterprise vulscan option. Pci dss requires two independent methods of pci scanning: Discover the best tools and techniques for scanning your systems. Best for comprehensive website and. An external vulnerability scan is performed outside of your network (e.g., at your network. Vulnerability scanning is the process of detecting and evaluating security flaws in it systems,. How To Perform External Vulnerability Scan.
From www.manageengine.com
Vulnerability Assessment Tools & Checklists ManageEngine How To Perform External Vulnerability Scan By performing external vulnerability scanning, organizations can proactively identify and address security weaknesses in their external network perimeter, reducing. Discover the best tools and techniques for scanning your systems. Pci dss requires two independent methods of pci scanning: Best for comprehensive website and. An external vulnerability scan is performed outside of your network (e.g., at your network. Best overall vulnerability. How To Perform External Vulnerability Scan.
From www.youtube.com
External vulnerability scanning service YouTube How To Perform External Vulnerability Scan An external vulnerability scan is performed outside of your network (e.g., at your network. Discover the best tools and techniques for scanning your systems. Running an external vulnerability scan (or perimeter scan) is critical for ensuring that the perimeter of your network doesn’t have any glaring. Best for comprehensive website and. By performing external vulnerability scanning, organizations can proactively identify. How To Perform External Vulnerability Scan.
From blog.charlesit.com
Why Is External Vulnerability Scanning Critical to IT Security Risk How To Perform External Vulnerability Scan Pci dss requires two independent methods of pci scanning: Running an external vulnerability scan (or perimeter scan) is critical for ensuring that the perimeter of your network doesn’t have any glaring. Best overall vulnerability scanner and enterprise vulscan option. Best for comprehensive website and. An external vulnerability scan is performed outside of your network (e.g., at your network. The vulnerability. How To Perform External Vulnerability Scan.
From www.comparitech.com
How to Perform an External Vulnerability Scan (& Detect Vulnerabilties) How To Perform External Vulnerability Scan An external vulnerability scan is performed outside of your network (e.g., at your network. Best for comprehensive website and. Discover the best tools and techniques for scanning your systems. Pci dss requires two independent methods of pci scanning: The vulnerability scanner identifies and creates an inventory of all systems connected to a. Best overall vulnerability scanner and enterprise vulscan option.. How To Perform External Vulnerability Scan.