Splunk Log4J Example . Running this application should allow the user to type in a line in the console, which should then be logged via log4j, and. For example, if we want. Place the log4j2.xml and logback.xml. The following example shows how to configure log4j 2. This example assumes that you have splunk enterprise running locally (with an ip. The splunk logging library for java contains example configuration files. Using the data collected, we developed 13 new detections and 9 playbooks to. Log4j 2 appender for logging to splunk hec endpoint and for config examples for tcp and udp logging. Splunk threat research team simulated the log4j vulnerabilities in the splunk attack range.
from research.splunk.com
Splunk threat research team simulated the log4j vulnerabilities in the splunk attack range. The following example shows how to configure log4j 2. Using the data collected, we developed 13 new detections and 9 playbooks to. Log4j 2 appender for logging to splunk hec endpoint and for config examples for tcp and udp logging. This example assumes that you have splunk enterprise running locally (with an ip. Place the log4j2.xml and logback.xml. For example, if we want. Running this application should allow the user to type in a line in the console, which should then be logged via log4j, and. The splunk logging library for java contains example configuration files.
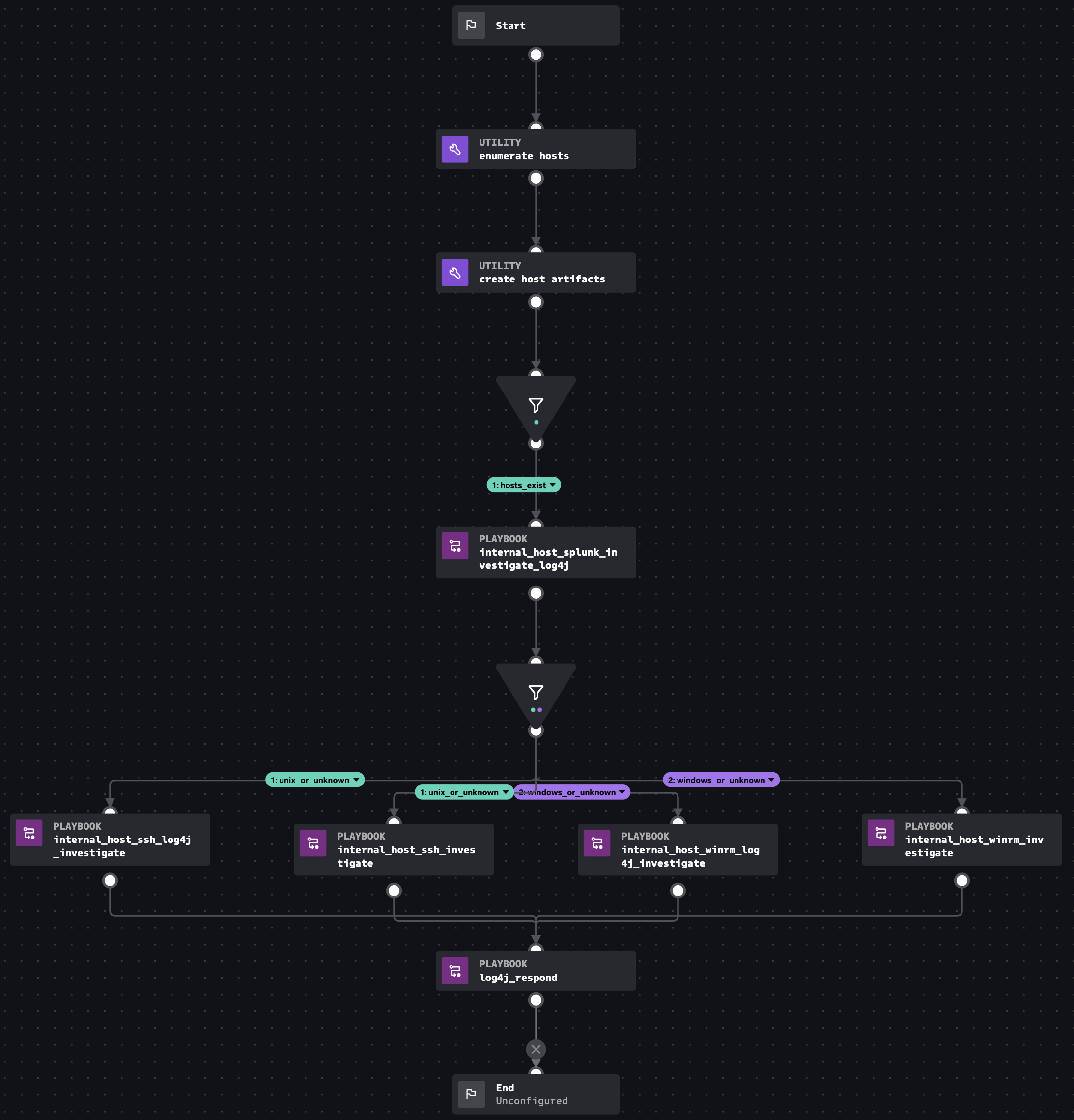
Log4j Investigate Splunk Security Content
Splunk Log4J Example The following example shows how to configure log4j 2. Using the data collected, we developed 13 new detections and 9 playbooks to. Log4j 2 appender for logging to splunk hec endpoint and for config examples for tcp and udp logging. The following example shows how to configure log4j 2. This example assumes that you have splunk enterprise running locally (with an ip. The splunk logging library for java contains example configuration files. For example, if we want. Splunk threat research team simulated the log4j vulnerabilities in the splunk attack range. Running this application should allow the user to type in a line in the console, which should then be logged via log4j, and. Place the log4j2.xml and logback.xml.
From www.splunk.com
Log4Shell Detecting Log4j 2 RCE Using Splunk Splunk Splunk Log4J Example Running this application should allow the user to type in a line in the console, which should then be logged via log4j, and. For example, if we want. Splunk threat research team simulated the log4j vulnerabilities in the splunk attack range. Place the log4j2.xml and logback.xml. Using the data collected, we developed 13 new detections and 9 playbooks to. The. Splunk Log4J Example.
From www.stratosphereips.org
Getting Started With Splunk Basic Searching & Data Viz — Stratosphere IPS Splunk Log4J Example This example assumes that you have splunk enterprise running locally (with an ip. For example, if we want. Place the log4j2.xml and logback.xml. The splunk logging library for java contains example configuration files. Using the data collected, we developed 13 new detections and 9 playbooks to. Running this application should allow the user to type in a line in the. Splunk Log4J Example.
From www.splunk.com
Log4Shell Detecting Log4j 2 RCE Using Splunk Splunk Splunk Log4J Example For example, if we want. Place the log4j2.xml and logback.xml. The following example shows how to configure log4j 2. Log4j 2 appender for logging to splunk hec endpoint and for config examples for tcp and udp logging. This example assumes that you have splunk enterprise running locally (with an ip. The splunk logging library for java contains example configuration files.. Splunk Log4J Example.
From www.function1.com
Event Sampling Splunk 6.4 Feature Function1 Splunk Log4J Example The following example shows how to configure log4j 2. The splunk logging library for java contains example configuration files. Using the data collected, we developed 13 new detections and 9 playbooks to. This example assumes that you have splunk enterprise running locally (with an ip. Running this application should allow the user to type in a line in the console,. Splunk Log4J Example.
From www.atatus.com
15 Best Log Monitoring Tools and Event Logging Software in 2024 Splunk Log4J Example Using the data collected, we developed 13 new detections and 9 playbooks to. Place the log4j2.xml and logback.xml. The splunk logging library for java contains example configuration files. Running this application should allow the user to type in a line in the console, which should then be logged via log4j, and. For example, if we want. Log4j 2 appender for. Splunk Log4J Example.
From kinneygroup.com
What Happened With Log4j in Splunk? Kinney Group Splunk Log4J Example Running this application should allow the user to type in a line in the console, which should then be logged via log4j, and. The splunk logging library for java contains example configuration files. For example, if we want. The following example shows how to configure log4j 2. Log4j 2 appender for logging to splunk hec endpoint and for config examples. Splunk Log4J Example.
From research.splunk.com
Log4j Investigate Splunk Security Content Splunk Log4J Example The following example shows how to configure log4j 2. Splunk threat research team simulated the log4j vulnerabilities in the splunk attack range. The splunk logging library for java contains example configuration files. This example assumes that you have splunk enterprise running locally (with an ip. Using the data collected, we developed 13 new detections and 9 playbooks to. Running this. Splunk Log4J Example.
From blog.rnhintegrations.com
Configure Appender to Splunk in Mule Application log4j configuration Splunk Log4J Example Running this application should allow the user to type in a line in the console, which should then be logged via log4j, and. This example assumes that you have splunk enterprise running locally (with an ip. Log4j 2 appender for logging to splunk hec endpoint and for config examples for tcp and udp logging. Splunk threat research team simulated the. Splunk Log4J Example.
From www.splunk.com
Log4Shell Detecting Log4j Vulnerability (CVE202144228) Continued Splunk Splunk Log4J Example The following example shows how to configure log4j 2. Place the log4j2.xml and logback.xml. For example, if we want. Using the data collected, we developed 13 new detections and 9 playbooks to. This example assumes that you have splunk enterprise running locally (with an ip. Log4j 2 appender for logging to splunk hec endpoint and for config examples for tcp. Splunk Log4J Example.
From blog.rnhintegrations.com
Configure Appender to Splunk in Mule Application log4j configuration Splunk Log4J Example The splunk logging library for java contains example configuration files. Running this application should allow the user to type in a line in the console, which should then be logged via log4j, and. The following example shows how to configure log4j 2. This example assumes that you have splunk enterprise running locally (with an ip. Using the data collected, we. Splunk Log4J Example.
From www.codeproject.com
Integrating OpenShift and Splunk for Logging CodeProject Splunk Log4J Example Running this application should allow the user to type in a line in the console, which should then be logged via log4j, and. Using the data collected, we developed 13 new detections and 9 playbooks to. Log4j 2 appender for logging to splunk hec endpoint and for config examples for tcp and udp logging. Splunk threat research team simulated the. Splunk Log4J Example.
From betterstack.com
How to Get Started with Log4j for Logging in Java Better Stack Community Splunk Log4J Example Running this application should allow the user to type in a line in the console, which should then be logged via log4j, and. Using the data collected, we developed 13 new detections and 9 playbooks to. This example assumes that you have splunk enterprise running locally (with an ip. The following example shows how to configure log4j 2. The splunk. Splunk Log4J Example.
From www.splunk.com
Log4Shell Detecting Log4j 2 RCE Using Splunk Splunk Splunk Log4J Example Log4j 2 appender for logging to splunk hec endpoint and for config examples for tcp and udp logging. Running this application should allow the user to type in a line in the console, which should then be logged via log4j, and. Place the log4j2.xml and logback.xml. Using the data collected, we developed 13 new detections and 9 playbooks to. The. Splunk Log4J Example.
From examples.javacodegeeks.com
Splunk Basic Search Example Java Code Geeks Splunk Log4J Example Place the log4j2.xml and logback.xml. The splunk logging library for java contains example configuration files. The following example shows how to configure log4j 2. Splunk threat research team simulated the log4j vulnerabilities in the splunk attack range. Log4j 2 appender for logging to splunk hec endpoint and for config examples for tcp and udp logging. This example assumes that you. Splunk Log4J Example.
From blog.csdn.net
Spring 日志配置log4j.properties步骤:_如何创建log4j.properties配置文件CSDN博客 Splunk Log4J Example The following example shows how to configure log4j 2. This example assumes that you have splunk enterprise running locally (with an ip. Place the log4j2.xml and logback.xml. Using the data collected, we developed 13 new detections and 9 playbooks to. Splunk threat research team simulated the log4j vulnerabilities in the splunk attack range. The splunk logging library for java contains. Splunk Log4J Example.
From help.mulesoft.com
Create a Test Splunk Server For Custom Log4j Testings MuleSoft Help Center Splunk Log4J Example Splunk threat research team simulated the log4j vulnerabilities in the splunk attack range. Place the log4j2.xml and logback.xml. This example assumes that you have splunk enterprise running locally (with an ip. The following example shows how to configure log4j 2. The splunk logging library for java contains example configuration files. Using the data collected, we developed 13 new detections and. Splunk Log4J Example.
From www.splunk.com
Log4Shell Detecting Log4j 2 RCE Using Splunk Splunk Splunk Log4J Example Using the data collected, we developed 13 new detections and 9 playbooks to. Log4j 2 appender for logging to splunk hec endpoint and for config examples for tcp and udp logging. This example assumes that you have splunk enterprise running locally (with an ip. Splunk threat research team simulated the log4j vulnerabilities in the splunk attack range. Running this application. Splunk Log4J Example.
From www.youtube.com
Splunk Fundamentals Ingest Logs and Get Them CIM Compliant Example 1 YouTube Splunk Log4J Example Using the data collected, we developed 13 new detections and 9 playbooks to. Place the log4j2.xml and logback.xml. Log4j 2 appender for logging to splunk hec endpoint and for config examples for tcp and udp logging. The splunk logging library for java contains example configuration files. Splunk threat research team simulated the log4j vulnerabilities in the splunk attack range. Running. Splunk Log4J Example.
From www.splunk.com
Log4Shell Detecting Log4j 2 RCE Using Splunk Splunk Splunk Log4J Example Using the data collected, we developed 13 new detections and 9 playbooks to. Log4j 2 appender for logging to splunk hec endpoint and for config examples for tcp and udp logging. Place the log4j2.xml and logback.xml. The splunk logging library for java contains example configuration files. This example assumes that you have splunk enterprise running locally (with an ip. Splunk. Splunk Log4J Example.
From jasonmurray.org
Detecting successful log4j compromises with Zeek and Splunk Splunk Log4J Example Place the log4j2.xml and logback.xml. Running this application should allow the user to type in a line in the console, which should then be logged via log4j, and. Log4j 2 appender for logging to splunk hec endpoint and for config examples for tcp and udp logging. For example, if we want. The splunk logging library for java contains example configuration. Splunk Log4J Example.
From www.splunk.com
Log4Shell Overview and Resources for Log4j Vulnerabilities Splunk Splunk Log4J Example The splunk logging library for java contains example configuration files. Running this application should allow the user to type in a line in the console, which should then be logged via log4j, and. Splunk threat research team simulated the log4j vulnerabilities in the splunk attack range. Using the data collected, we developed 13 new detections and 9 playbooks to. Log4j. Splunk Log4J Example.
From www.splunk.com
Using Splunk for SEO Log File Analysis Splunk Splunk Log4J Example The following example shows how to configure log4j 2. For example, if we want. The splunk logging library for java contains example configuration files. This example assumes that you have splunk enterprise running locally (with an ip. Log4j 2 appender for logging to splunk hec endpoint and for config examples for tcp and udp logging. Place the log4j2.xml and logback.xml.. Splunk Log4J Example.
From blog.rnhintegrations.com
Configure Appender to Splunk in Mule Application log4j configuration Splunk Log4J Example The following example shows how to configure log4j 2. For example, if we want. Using the data collected, we developed 13 new detections and 9 playbooks to. Splunk threat research team simulated the log4j vulnerabilities in the splunk attack range. Running this application should allow the user to type in a line in the console, which should then be logged. Splunk Log4J Example.
From www.linkedin.com
Splunk on LinkedIn Log4Shell Overview and Resources for Log4j Vulnerabilities Splunk Splunk Log4J Example The splunk logging library for java contains example configuration files. Running this application should allow the user to type in a line in the console, which should then be logged via log4j, and. Using the data collected, we developed 13 new detections and 9 playbooks to. Place the log4j2.xml and logback.xml. This example assumes that you have splunk enterprise running. Splunk Log4J Example.
From anchore.com
How to Find and Fix Log4j Open Source Anchore Splunk Log4J Example For example, if we want. Using the data collected, we developed 13 new detections and 9 playbooks to. Log4j 2 appender for logging to splunk hec endpoint and for config examples for tcp and udp logging. The following example shows how to configure log4j 2. Splunk threat research team simulated the log4j vulnerabilities in the splunk attack range. This example. Splunk Log4J Example.
From www.callicoder.com
How to use Log4j 2 with Spring Boot CalliCoder Splunk Log4J Example Log4j 2 appender for logging to splunk hec endpoint and for config examples for tcp and udp logging. Splunk threat research team simulated the log4j vulnerabilities in the splunk attack range. For example, if we want. The following example shows how to configure log4j 2. Place the log4j2.xml and logback.xml. The splunk logging library for java contains example configuration files.. Splunk Log4J Example.
From www.youtube.com
Spring Boot APP With Splunk Integration Log4j Realtime logs analysis using Splunk EnggAdda Splunk Log4J Example Place the log4j2.xml and logback.xml. Log4j 2 appender for logging to splunk hec endpoint and for config examples for tcp and udp logging. Running this application should allow the user to type in a line in the console, which should then be logged via log4j, and. Splunk threat research team simulated the log4j vulnerabilities in the splunk attack range. The. Splunk Log4J Example.
From blog.rnhintegrations.com
Configure Appender to Splunk in Mule Application log4j configuration Splunk Log4J Example This example assumes that you have splunk enterprise running locally (with an ip. Place the log4j2.xml and logback.xml. Splunk threat research team simulated the log4j vulnerabilities in the splunk attack range. The splunk logging library for java contains example configuration files. Log4j 2 appender for logging to splunk hec endpoint and for config examples for tcp and udp logging. For. Splunk Log4J Example.
From documentation.n-able.com
Splunk logging Splunk Log4J Example Log4j 2 appender for logging to splunk hec endpoint and for config examples for tcp and udp logging. The following example shows how to configure log4j 2. Running this application should allow the user to type in a line in the console, which should then be logged via log4j, and. Place the log4j2.xml and logback.xml. Using the data collected, we. Splunk Log4J Example.
From kinneygroup.com
Splunk Collect Command Using It For Summary Indexing Kinney Group Splunk Log4J Example This example assumes that you have splunk enterprise running locally (with an ip. For example, if we want. Place the log4j2.xml and logback.xml. Log4j 2 appender for logging to splunk hec endpoint and for config examples for tcp and udp logging. The following example shows how to configure log4j 2. The splunk logging library for java contains example configuration files.. Splunk Log4J Example.
From examples.javacodegeeks.com
Splunk Stats Command Example Java Code Geeks Splunk Log4J Example Using the data collected, we developed 13 new detections and 9 playbooks to. For example, if we want. The following example shows how to configure log4j 2. Place the log4j2.xml and logback.xml. This example assumes that you have splunk enterprise running locally (with an ip. The splunk logging library for java contains example configuration files. Splunk threat research team simulated. Splunk Log4J Example.
From examples.javacodegeeks.com
Log4j Priority Example Java Code Geeks Splunk Log4J Example Splunk threat research team simulated the log4j vulnerabilities in the splunk attack range. This example assumes that you have splunk enterprise running locally (with an ip. Running this application should allow the user to type in a line in the console, which should then be logged via log4j, and. For example, if we want. Place the log4j2.xml and logback.xml. The. Splunk Log4J Example.
From intotheone.blogspot.com
Cyber Security Awareness Splunk Custom Search Command Searching for MISP IOC’s Splunk Log4J Example Splunk threat research team simulated the log4j vulnerabilities in the splunk attack range. This example assumes that you have splunk enterprise running locally (with an ip. The following example shows how to configure log4j 2. For example, if we want. Place the log4j2.xml and logback.xml. The splunk logging library for java contains example configuration files. Running this application should allow. Splunk Log4J Example.
From blog.rnhintegrations.com
Configure Appender to Splunk in Mule Application log4j configuration Splunk Log4J Example This example assumes that you have splunk enterprise running locally (with an ip. For example, if we want. Running this application should allow the user to type in a line in the console, which should then be logged via log4j, and. Using the data collected, we developed 13 new detections and 9 playbooks to. Log4j 2 appender for logging to. Splunk Log4J Example.
From blog.khairulazam.net
Hunting for Log4j RCE (CVE202144228) using Splunk & Excel Splunk Log4J Example Running this application should allow the user to type in a line in the console, which should then be logged via log4j, and. Splunk threat research team simulated the log4j vulnerabilities in the splunk attack range. Place the log4j2.xml and logback.xml. Log4j 2 appender for logging to splunk hec endpoint and for config examples for tcp and udp logging. The. Splunk Log4J Example.