What Is X-Sender . If the message is spoofed, you’ll see. Now, to find the real sender of your email, you must find the earliest trusted gateway — last when reading the headers from top. Let's start by finding bill's mail server. For a very simple example, ars. Email headers are read chronologically from the bottom up and can be broken down into three main categories: I want to address this because it’s often why people go digging into headers in the first place. The owner of a domain can set a txt record in its dns that states what servers are allowed to send mail on behalf of that domain. A field like this will contain the actual sending email address of the attacker. 1) message information 2) x.
from github.com
If the message is spoofed, you’ll see. I want to address this because it’s often why people go digging into headers in the first place. The owner of a domain can set a txt record in its dns that states what servers are allowed to send mail on behalf of that domain. For a very simple example, ars. Email headers are read chronologically from the bottom up and can be broken down into three main categories: Let's start by finding bill's mail server. A field like this will contain the actual sending email address of the attacker. 1) message information 2) x. Now, to find the real sender of your email, you must find the earliest trusted gateway — last when reading the headers from top.
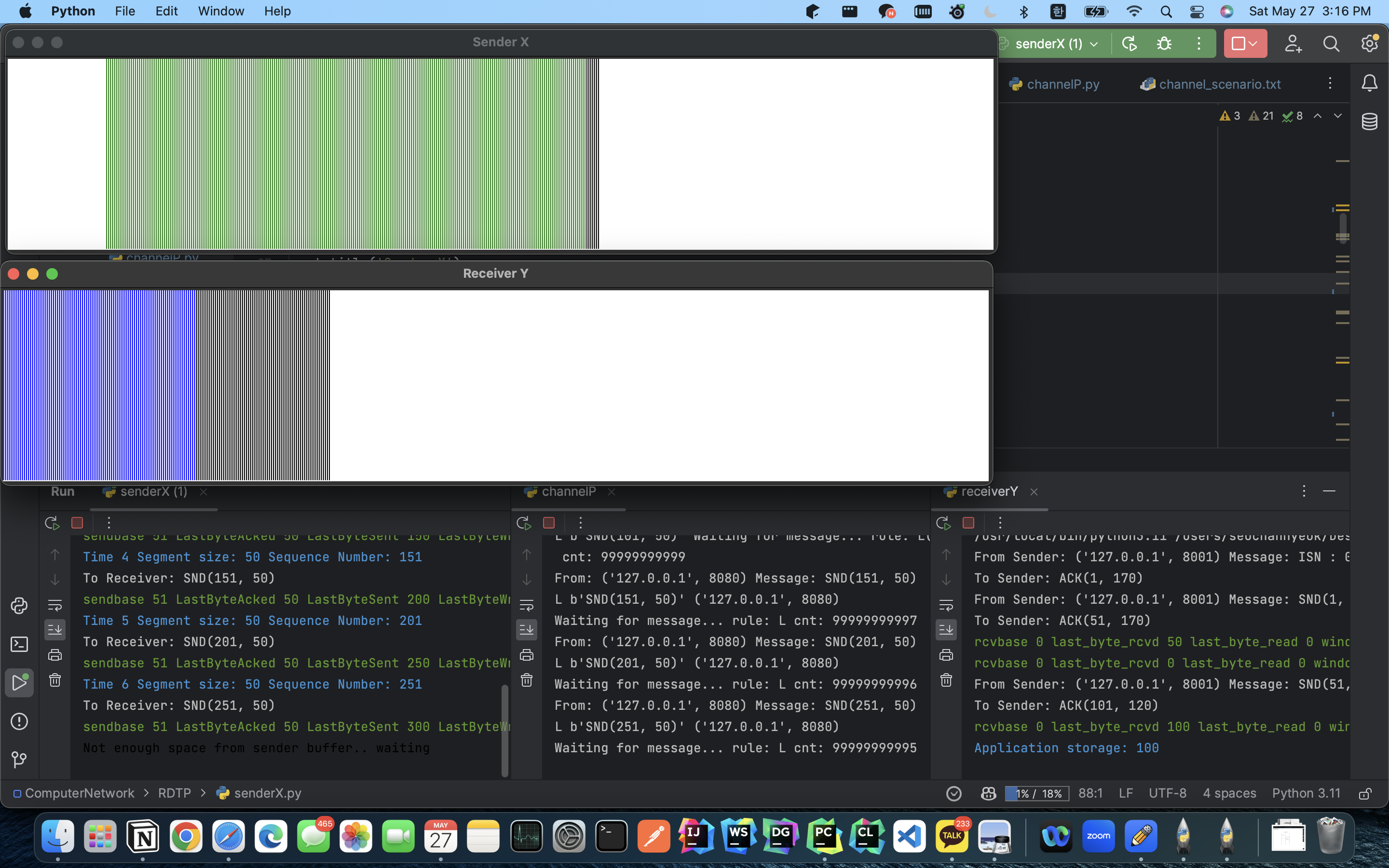
GitHub mushroom1324/RDTP
What Is X-Sender If the message is spoofed, you’ll see. The owner of a domain can set a txt record in its dns that states what servers are allowed to send mail on behalf of that domain. Now, to find the real sender of your email, you must find the earliest trusted gateway — last when reading the headers from top. Email headers are read chronologically from the bottom up and can be broken down into three main categories: 1) message information 2) x. I want to address this because it’s often why people go digging into headers in the first place. For a very simple example, ars. Let's start by finding bill's mail server. If the message is spoofed, you’ll see. A field like this will contain the actual sending email address of the attacker.
From noatechinfo.com
Effortlessly Send Bulk Emails, SMS and WhatsApp Messages with XSender What Is X-Sender Now, to find the real sender of your email, you must find the earliest trusted gateway — last when reading the headers from top. If the message is spoofed, you’ll see. I want to address this because it’s often why people go digging into headers in the first place. 1) message information 2) x. Email headers are read chronologically from. What Is X-Sender.
From circuitwiringreseau123.z22.web.core.windows.net
Fuel Sender Wiring Diagram What Is X-Sender Email headers are read chronologically from the bottom up and can be broken down into three main categories: The owner of a domain can set a txt record in its dns that states what servers are allowed to send mail on behalf of that domain. If the message is spoofed, you’ll see. A field like this will contain the actual. What Is X-Sender.
From www.youtube.com
X_SENDER INBOX SMTP SENDER 2019 BY XGHOST MA YouTube What Is X-Sender If the message is spoofed, you’ll see. Now, to find the real sender of your email, you must find the earliest trusted gateway — last when reading the headers from top. The owner of a domain can set a txt record in its dns that states what servers are allowed to send mail on behalf of that domain. Let's start. What Is X-Sender.
From www.dreamstime.com
Sender and Receiver Cycle Illustration Stock Illustration What Is X-Sender Email headers are read chronologically from the bottom up and can be broken down into three main categories: 1) message information 2) x. Now, to find the real sender of your email, you must find the earliest trusted gateway — last when reading the headers from top. I want to address this because it’s often why people go digging into. What Is X-Sender.
From apkpure.com
X Sender File Transfer & Share APK für Android herunterladen What Is X-Sender The owner of a domain can set a txt record in its dns that states what servers are allowed to send mail on behalf of that domain. Email headers are read chronologically from the bottom up and can be broken down into three main categories: Let's start by finding bill's mail server. Now, to find the real sender of your. What Is X-Sender.
From www.reddit.com
Sent This on Twitter/X. Sender claims “a frame from the second trailer What Is X-Sender 1) message information 2) x. Email headers are read chronologically from the bottom up and can be broken down into three main categories: If the message is spoofed, you’ll see. Now, to find the real sender of your email, you must find the earliest trusted gateway — last when reading the headers from top. A field like this will contain. What Is X-Sender.
From www.sound1.com
JTS SPT Wireless Audio System 1 x Sender, 2 x Mottakere What Is X-Sender 1) message information 2) x. The owner of a domain can set a txt record in its dns that states what servers are allowed to send mail on behalf of that domain. Let's start by finding bill's mail server. For a very simple example, ars. Now, to find the real sender of your email, you must find the earliest trusted. What Is X-Sender.
From github.com
GitHub mushroom1324/RDTP What Is X-Sender A field like this will contain the actual sending email address of the attacker. If the message is spoofed, you’ll see. I want to address this because it’s often why people go digging into headers in the first place. The owner of a domain can set a txt record in its dns that states what servers are allowed to send. What Is X-Sender.
From www.smtpshop.com
GX Sender Version 1 What Is X-Sender Now, to find the real sender of your email, you must find the earliest trusted gateway — last when reading the headers from top. 1) message information 2) x. The owner of a domain can set a txt record in its dns that states what servers are allowed to send mail on behalf of that domain. Email headers are read. What Is X-Sender.
From www.distractify.com
What Is an Infinity Pillow TikTok? Folks Need Answers What Is X-Sender 1) message information 2) x. The owner of a domain can set a txt record in its dns that states what servers are allowed to send mail on behalf of that domain. Now, to find the real sender of your email, you must find the earliest trusted gateway — last when reading the headers from top. A field like this. What Is X-Sender.
From giolfuetz.blob.core.windows.net
What Is The Best Way To Get Loot Bags In Pet Sim X at Connie Marez blog What Is X-Sender I want to address this because it’s often why people go digging into headers in the first place. Email headers are read chronologically from the bottom up and can be broken down into three main categories: If the message is spoofed, you’ll see. Now, to find the real sender of your email, you must find the earliest trusted gateway —. What Is X-Sender.
From giolfuetz.blob.core.windows.net
What Is The Best Way To Get Loot Bags In Pet Sim X at Connie Marez blog What Is X-Sender 1) message information 2) x. The owner of a domain can set a txt record in its dns that states what servers are allowed to send mail on behalf of that domain. Email headers are read chronologically from the bottom up and can be broken down into three main categories: I want to address this because it’s often why people. What Is X-Sender.
From www.chegg.com
Solved Q4. The diagram below right shows two TCP senders at What Is X-Sender If the message is spoofed, you’ll see. 1) message information 2) x. Let's start by finding bill's mail server. Now, to find the real sender of your email, you must find the earliest trusted gateway — last when reading the headers from top. The owner of a domain can set a txt record in its dns that states what servers. What Is X-Sender.
From www.youtube.com
How to address an envelope Writing sender, recipient address and What Is X-Sender If the message is spoofed, you’ll see. A field like this will contain the actual sending email address of the attacker. Let's start by finding bill's mail server. For a very simple example, ars. 1) message information 2) x. I want to address this because it’s often why people go digging into headers in the first place. Now, to find. What Is X-Sender.
From www.chegg.com
Solved Problem 3 (6 points). Consider the scenario below What Is X-Sender The owner of a domain can set a txt record in its dns that states what servers are allowed to send mail on behalf of that domain. For a very simple example, ars. 1) message information 2) x. Let's start by finding bill's mail server. A field like this will contain the actual sending email address of the attacker. Email. What Is X-Sender.
From www.chegg.com
Solved Consider the figure below in which a TCP sender and What Is X-Sender I want to address this because it’s often why people go digging into headers in the first place. The owner of a domain can set a txt record in its dns that states what servers are allowed to send mail on behalf of that domain. For a very simple example, ars. Let's start by finding bill's mail server. Email headers. What Is X-Sender.
From www.chegg.com
Solved 5. Consider Figure 1 in which a sender and receiver What Is X-Sender I want to address this because it’s often why people go digging into headers in the first place. If the message is spoofed, you’ll see. The owner of a domain can set a txt record in its dns that states what servers are allowed to send mail on behalf of that domain. Now, to find the real sender of your. What Is X-Sender.
From www.chegg.com
Solved Packet Transmission Delay. Consider the network shown What Is X-Sender Let's start by finding bill's mail server. For a very simple example, ars. The owner of a domain can set a txt record in its dns that states what servers are allowed to send mail on behalf of that domain. Email headers are read chronologically from the bottom up and can be broken down into three main categories: A field. What Is X-Sender.
From apkpure.com
Android용 File Sender X Sender File APK 다운로드 What Is X-Sender 1) message information 2) x. If the message is spoofed, you’ll see. Let's start by finding bill's mail server. A field like this will contain the actual sending email address of the attacker. Now, to find the real sender of your email, you must find the earliest trusted gateway — last when reading the headers from top. For a very. What Is X-Sender.
From apkpure.com
X Sender Share Video, Music APK for Android Download What Is X-Sender I want to address this because it’s often why people go digging into headers in the first place. For a very simple example, ars. Email headers are read chronologically from the bottom up and can be broken down into three main categories: Let's start by finding bill's mail server. If the message is spoofed, you’ll see. A field like this. What Is X-Sender.
From www.chegg.com
Solved Q4.Suppose that a sender and a receiver exchange data What Is X-Sender I want to address this because it’s often why people go digging into headers in the first place. If the message is spoofed, you’ll see. Now, to find the real sender of your email, you must find the earliest trusted gateway — last when reading the headers from top. 1) message information 2) x. A field like this will contain. What Is X-Sender.
From apkpure.com
Android용 File Sender X Sender File APK 다운로드 What Is X-Sender Let's start by finding bill's mail server. A field like this will contain the actual sending email address of the attacker. Email headers are read chronologically from the bottom up and can be broken down into three main categories: The owner of a domain can set a txt record in its dns that states what servers are allowed to send. What Is X-Sender.
From www.3nions.com
10 Best WhatsApp Message Sender Tools(Free & Paid) What Is X-Sender I want to address this because it’s often why people go digging into headers in the first place. Let's start by finding bill's mail server. Email headers are read chronologically from the bottom up and can be broken down into three main categories: 1) message information 2) x. Now, to find the real sender of your email, you must find. What Is X-Sender.
From www.dreamstime.com
Letter Sender and Receiver Format Stock Image Image of letter, post What Is X-Sender I want to address this because it’s often why people go digging into headers in the first place. A field like this will contain the actual sending email address of the attacker. Email headers are read chronologically from the bottom up and can be broken down into three main categories: Now, to find the real sender of your email, you. What Is X-Sender.
From www.studyxapp.com
consider the figure below in which a tcp sender and receiver What Is X-Sender Let's start by finding bill's mail server. Email headers are read chronologically from the bottom up and can be broken down into three main categories: 1) message information 2) x. The owner of a domain can set a txt record in its dns that states what servers are allowed to send mail on behalf of that domain. A field like. What Is X-Sender.
From www.dreamstime.com
Return to sender letter stock illustration. Illustration of email What Is X-Sender Now, to find the real sender of your email, you must find the earliest trusted gateway — last when reading the headers from top. 1) message information 2) x. Let's start by finding bill's mail server. For a very simple example, ars. Email headers are read chronologically from the bottom up and can be broken down into three main categories:. What Is X-Sender.
From apkcombo.com
X File Sender File Transfer APK (Android App) Descarga Gratis What Is X-Sender For a very simple example, ars. 1) message information 2) x. The owner of a domain can set a txt record in its dns that states what servers are allowed to send mail on behalf of that domain. Let's start by finding bill's mail server. Now, to find the real sender of your email, you must find the earliest trusted. What Is X-Sender.
From giolfuetz.blob.core.windows.net
What Is The Best Way To Get Loot Bags In Pet Sim X at Connie Marez blog What Is X-Sender I want to address this because it’s often why people go digging into headers in the first place. If the message is spoofed, you’ll see. Let's start by finding bill's mail server. 1) message information 2) x. A field like this will contain the actual sending email address of the attacker. The owner of a domain can set a txt. What Is X-Sender.
From www.megashop365.de
Klingel Erweiterung per Funk Set mit 2 Empfänger ! 1 X What Is X-Sender 1) message information 2) x. Email headers are read chronologically from the bottom up and can be broken down into three main categories: If the message is spoofed, you’ll see. The owner of a domain can set a txt record in its dns that states what servers are allowed to send mail on behalf of that domain. A field like. What Is X-Sender.
From www.softwareske.com
Sender ID Explained. Top site Design, Development and SEO Company What Is X-Sender 1) message information 2) x. Now, to find the real sender of your email, you must find the earliest trusted gateway — last when reading the headers from top. The owner of a domain can set a txt record in its dns that states what servers are allowed to send mail on behalf of that domain. If the message is. What Is X-Sender.
From www.youtube.com
WA Bulk Sender with Buttons + Group Sender + Autobot YouTube What Is X-Sender 1) message information 2) x. The owner of a domain can set a txt record in its dns that states what servers are allowed to send mail on behalf of that domain. For a very simple example, ars. I want to address this because it’s often why people go digging into headers in the first place. A field like this. What Is X-Sender.
From cosmofeed.com
WA SENDER (Lifetime) Version 2.7.4 OFFER What Is X-Sender If the message is spoofed, you’ll see. Email headers are read chronologically from the bottom up and can be broken down into three main categories: For a very simple example, ars. Now, to find the real sender of your email, you must find the earliest trusted gateway — last when reading the headers from top. 1) message information 2) x.. What Is X-Sender.
From forcelearn.com
What is Task in Salesforce ForceLearn What Is X-Sender 1) message information 2) x. Let's start by finding bill's mail server. For a very simple example, ars. The owner of a domain can set a txt record in its dns that states what servers are allowed to send mail on behalf of that domain. Email headers are read chronologically from the bottom up and can be broken down into. What Is X-Sender.
From napkforpc.com
Fast X Sender File Transfer for PC / Mac / Windows 11,10,8,7 Free What Is X-Sender If the message is spoofed, you’ll see. Let's start by finding bill's mail server. Email headers are read chronologically from the bottom up and can be broken down into three main categories: 1) message information 2) x. A field like this will contain the actual sending email address of the attacker. For a very simple example, ars. Now, to find. What Is X-Sender.
From giojikvmz.blob.core.windows.net
Sun Water Temp Gauge Sending Unit at Christopher Jackson blog What Is X-Sender Now, to find the real sender of your email, you must find the earliest trusted gateway — last when reading the headers from top. If the message is spoofed, you’ll see. Email headers are read chronologically from the bottom up and can be broken down into three main categories: I want to address this because it’s often why people go. What Is X-Sender.