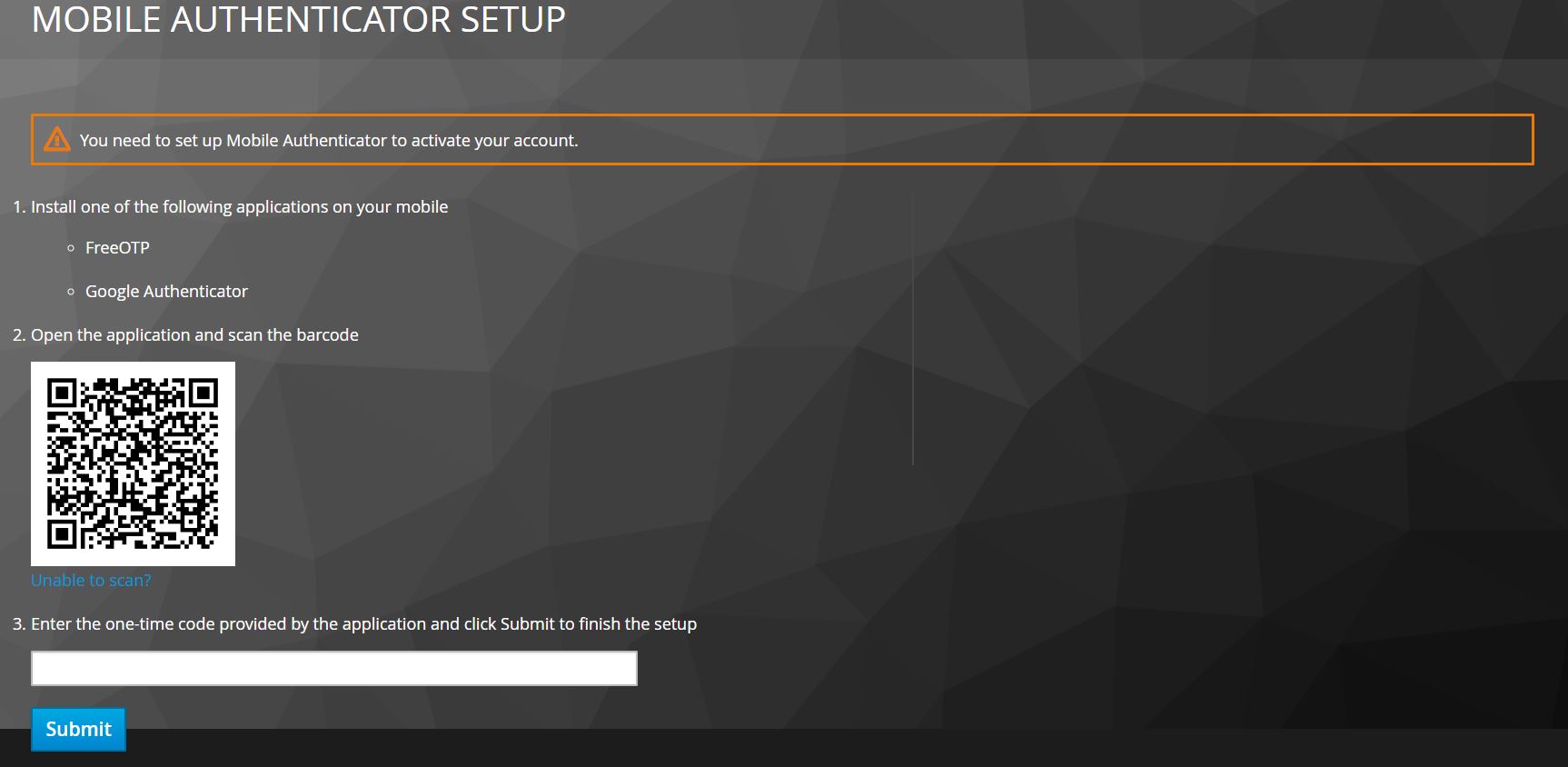
Keycloak Authentication Otp . This article will guide you through the. This approach involves extending the sms otp. User visits the application website and enters the mobile number or username. Learn how to create a custom authenticator using sms/otp verification in keycloak. Learn how to configure authentication policies, credential types, and kerberos integration for red hat build of keycloak. The user is presented with a choice of three otp methods for authentication:
from ultimatesecurity.pro
This article will guide you through the. Learn how to configure authentication policies, credential types, and kerberos integration for red hat build of keycloak. This approach involves extending the sms otp. User visits the application website and enters the mobile number or username. The user is presented with a choice of three otp methods for authentication: Learn how to create a custom authenticator using sms/otp verification in keycloak.
Keycloak TwoFactor Authentication · Ultimate Security Professional Blog
Keycloak Authentication Otp The user is presented with a choice of three otp methods for authentication: Learn how to create a custom authenticator using sms/otp verification in keycloak. Learn how to configure authentication policies, credential types, and kerberos integration for red hat build of keycloak. The user is presented with a choice of three otp methods for authentication: This article will guide you through the. User visits the application website and enters the mobile number or username. This approach involves extending the sms otp.
From www.agile-solutions.ch
Keycloak agilesolution Keycloak Authentication Otp The user is presented with a choice of three otp methods for authentication: Learn how to configure authentication policies, credential types, and kerberos integration for red hat build of keycloak. This article will guide you through the. This approach involves extending the sms otp. User visits the application website and enters the mobile number or username. Learn how to create. Keycloak Authentication Otp.
From www.janua.fr
Keycloak Multifactor authentication (MFA) using OTP JANUA Keycloak Authentication Otp The user is presented with a choice of three otp methods for authentication: This approach involves extending the sms otp. Learn how to create a custom authenticator using sms/otp verification in keycloak. This article will guide you through the. Learn how to configure authentication policies, credential types, and kerberos integration for red hat build of keycloak. User visits the application. Keycloak Authentication Otp.
From stackoverflow.com
rest Keycloak Oauth2 Authentication Flow Stack Overflow Keycloak Authentication Otp Learn how to create a custom authenticator using sms/otp verification in keycloak. The user is presented with a choice of three otp methods for authentication: User visits the application website and enters the mobile number or username. This article will guide you through the. Learn how to configure authentication policies, credential types, and kerberos integration for red hat build of. Keycloak Authentication Otp.
From www.thomasvitale.com
Keycloak Authentication Flows, SSO Protocols and Client Configuration Keycloak Authentication Otp The user is presented with a choice of three otp methods for authentication: This article will guide you through the. Learn how to create a custom authenticator using sms/otp verification in keycloak. Learn how to configure authentication policies, credential types, and kerberos integration for red hat build of keycloak. User visits the application website and enters the mobile number or. Keycloak Authentication Otp.
From github.com
GitHub 5stones/keycloakemailotp A Keycloak Authentication step Keycloak Authentication Otp This approach involves extending the sms otp. Learn how to create a custom authenticator using sms/otp verification in keycloak. This article will guide you through the. User visits the application website and enters the mobile number or username. The user is presented with a choice of three otp methods for authentication: Learn how to configure authentication policies, credential types, and. Keycloak Authentication Otp.
From ultimatesecurity.pro
Keycloak TwoFactor Authentication · Ultimate Security Professional Blog Keycloak Authentication Otp This approach involves extending the sms otp. Learn how to create a custom authenticator using sms/otp verification in keycloak. Learn how to configure authentication policies, credential types, and kerberos integration for red hat build of keycloak. This article will guide you through the. User visits the application website and enters the mobile number or username. The user is presented with. Keycloak Authentication Otp.
From walkingtree.tech
Keycloak Identity Access Management Solutions WalkingTree Technologies Keycloak Authentication Otp The user is presented with a choice of three otp methods for authentication: Learn how to configure authentication policies, credential types, and kerberos integration for red hat build of keycloak. This article will guide you through the. User visits the application website and enters the mobile number or username. This approach involves extending the sms otp. Learn how to create. Keycloak Authentication Otp.
From andrevianna-1662831931436.hashnode.dev
Understanding the Powerful Keycloak Tool Keycloak Authentication Otp User visits the application website and enters the mobile number or username. Learn how to configure authentication policies, credential types, and kerberos integration for red hat build of keycloak. Learn how to create a custom authenticator using sms/otp verification in keycloak. This article will guide you through the. This approach involves extending the sms otp. The user is presented with. Keycloak Authentication Otp.
From www.thomasvitale.com
Keycloak Basic Configuration for Authentication and Authorization Keycloak Authentication Otp User visits the application website and enters the mobile number or username. Learn how to configure authentication policies, credential types, and kerberos integration for red hat build of keycloak. This article will guide you through the. The user is presented with a choice of three otp methods for authentication: This approach involves extending the sms otp. Learn how to create. Keycloak Authentication Otp.
From www.typingdna.com
Add twofactor authentication to your web app using Keycloak & Node.js Keycloak Authentication Otp Learn how to create a custom authenticator using sms/otp verification in keycloak. User visits the application website and enters the mobile number or username. The user is presented with a choice of three otp methods for authentication: This approach involves extending the sms otp. This article will guide you through the. Learn how to configure authentication policies, credential types, and. Keycloak Authentication Otp.
From keycloak.discourse.group
Keycloak Authentication Set up OTP after registration approved Keycloak Authentication Otp This article will guide you through the. Learn how to configure authentication policies, credential types, and kerberos integration for red hat build of keycloak. Learn how to create a custom authenticator using sms/otp verification in keycloak. User visits the application website and enters the mobile number or username. The user is presented with a choice of three otp methods for. Keycloak Authentication Otp.
From keycloak.discourse.group
Conditional Authenticator Getting advice Keycloak Keycloak Authentication Otp This approach involves extending the sms otp. Learn how to configure authentication policies, credential types, and kerberos integration for red hat build of keycloak. The user is presented with a choice of three otp methods for authentication: This article will guide you through the. User visits the application website and enters the mobile number or username. Learn how to create. Keycloak Authentication Otp.
From github.com
GitHub dasniko/keycloak2fasmsauthenticator Keycloak Keycloak Authentication Otp Learn how to create a custom authenticator using sms/otp verification in keycloak. The user is presented with a choice of three otp methods for authentication: User visits the application website and enters the mobile number or username. This article will guide you through the. Learn how to configure authentication policies, credential types, and kerberos integration for red hat build of. Keycloak Authentication Otp.
From github.com
GitHub akshatsachdeva/keycloakotpwebhook Keycloak authentication Keycloak Authentication Otp Learn how to configure authentication policies, credential types, and kerberos integration for red hat build of keycloak. This approach involves extending the sms otp. User visits the application website and enters the mobile number or username. Learn how to create a custom authenticator using sms/otp verification in keycloak. This article will guide you through the. The user is presented with. Keycloak Authentication Otp.
From github.com
GitHub 5stones/keycloakemailotp A Keycloak Authentication step Keycloak Authentication Otp The user is presented with a choice of three otp methods for authentication: Learn how to configure authentication policies, credential types, and kerberos integration for red hat build of keycloak. Learn how to create a custom authenticator using sms/otp verification in keycloak. User visits the application website and enters the mobile number or username. This article will guide you through. Keycloak Authentication Otp.
From www.thomasvitale.com
Keycloak Authentication Flows, SSO Protocols and Client Configuration Keycloak Authentication Otp Learn how to create a custom authenticator using sms/otp verification in keycloak. This approach involves extending the sms otp. User visits the application website and enters the mobile number or username. Learn how to configure authentication policies, credential types, and kerberos integration for red hat build of keycloak. The user is presented with a choice of three otp methods for. Keycloak Authentication Otp.
From ultimatesecurity.pro
Keycloak TwoFactor Authentication · Ultimate Security Professional Blog Keycloak Authentication Otp Learn how to configure authentication policies, credential types, and kerberos integration for red hat build of keycloak. This article will guide you through the. Learn how to create a custom authenticator using sms/otp verification in keycloak. User visits the application website and enters the mobile number or username. This approach involves extending the sms otp. The user is presented with. Keycloak Authentication Otp.
From ultimatesecurity.pro
Keycloak TwoFactor Authentication · Ultimate Security Professional Blog Keycloak Authentication Otp Learn how to create a custom authenticator using sms/otp verification in keycloak. User visits the application website and enters the mobile number or username. This approach involves extending the sms otp. This article will guide you through the. Learn how to configure authentication policies, credential types, and kerberos integration for red hat build of keycloak. The user is presented with. Keycloak Authentication Otp.
From blog.tharinduhasthika.com
Authenticating Jitsi Meetings using Keycloak Keycloak Authentication Otp Learn how to create a custom authenticator using sms/otp verification in keycloak. The user is presented with a choice of three otp methods for authentication: This article will guide you through the. Learn how to configure authentication policies, credential types, and kerberos integration for red hat build of keycloak. User visits the application website and enters the mobile number or. Keycloak Authentication Otp.
From github.com
GitHub akshatsachdeva/keycloakotpwebhook Keycloak authentication Keycloak Authentication Otp Learn how to configure authentication policies, credential types, and kerberos integration for red hat build of keycloak. User visits the application website and enters the mobile number or username. Learn how to create a custom authenticator using sms/otp verification in keycloak. The user is presented with a choice of three otp methods for authentication: This approach involves extending the sms. Keycloak Authentication Otp.
From github.com
GitHub 5stones/keycloakemailotp A Keycloak Authentication step Keycloak Authentication Otp This approach involves extending the sms otp. Learn how to create a custom authenticator using sms/otp verification in keycloak. The user is presented with a choice of three otp methods for authentication: This article will guide you through the. Learn how to configure authentication policies, credential types, and kerberos integration for red hat build of keycloak. User visits the application. Keycloak Authentication Otp.
From pm4ml.github.io
Managing user access in Keycloak Payment Manager OSS Documentation Keycloak Authentication Otp This approach involves extending the sms otp. This article will guide you through the. Learn how to create a custom authenticator using sms/otp verification in keycloak. Learn how to configure authentication policies, credential types, and kerberos integration for red hat build of keycloak. User visits the application website and enters the mobile number or username. The user is presented with. Keycloak Authentication Otp.
From copyprogramming.com
Reactjs Integrating Keycloak Authentication into a React Application Keycloak Authentication Otp The user is presented with a choice of three otp methods for authentication: This article will guide you through the. Learn how to configure authentication policies, credential types, and kerberos integration for red hat build of keycloak. Learn how to create a custom authenticator using sms/otp verification in keycloak. This approach involves extending the sms otp. User visits the application. Keycloak Authentication Otp.
From www.janua.fr
Keycloak Multifactor authentication (MFA) using OTP JANUA Keycloak Authentication Otp Learn how to configure authentication policies, credential types, and kerberos integration for red hat build of keycloak. User visits the application website and enters the mobile number or username. The user is presented with a choice of three otp methods for authentication: Learn how to create a custom authenticator using sms/otp verification in keycloak. This article will guide you through. Keycloak Authentication Otp.
From github.com
GitHub akshatsachdeva/keycloakotpwebhook Keycloak authentication Keycloak Authentication Otp The user is presented with a choice of three otp methods for authentication: This approach involves extending the sms otp. Learn how to create a custom authenticator using sms/otp verification in keycloak. User visits the application website and enters the mobile number or username. This article will guide you through the. Learn how to configure authentication policies, credential types, and. Keycloak Authentication Otp.
From docs.caascad.com
Keycloak Caascad Documentation Keycloak Authentication Otp User visits the application website and enters the mobile number or username. The user is presented with a choice of three otp methods for authentication: Learn how to configure authentication policies, credential types, and kerberos integration for red hat build of keycloak. This article will guide you through the. Learn how to create a custom authenticator using sms/otp verification in. Keycloak Authentication Otp.
From community.ibm.com
Extending Keycloak's authentication capabilities by integrating with Keycloak Authentication Otp User visits the application website and enters the mobile number or username. The user is presented with a choice of three otp methods for authentication: Learn how to configure authentication policies, credential types, and kerberos integration for red hat build of keycloak. This approach involves extending the sms otp. Learn how to create a custom authenticator using sms/otp verification in. Keycloak Authentication Otp.
From github.com
GitHub 9228883664/keycloakotppasswordauthenticator Keycloak Keycloak Authentication Otp User visits the application website and enters the mobile number or username. This approach involves extending the sms otp. The user is presented with a choice of three otp methods for authentication: Learn how to create a custom authenticator using sms/otp verification in keycloak. This article will guide you through the. Learn how to configure authentication policies, credential types, and. Keycloak Authentication Otp.
From www.soundsessential.com
Setting Up A Keycloak Server For Authenticating To FileMaker Part 7 Keycloak Authentication Otp Learn how to configure authentication policies, credential types, and kerberos integration for red hat build of keycloak. Learn how to create a custom authenticator using sms/otp verification in keycloak. User visits the application website and enters the mobile number or username. This article will guide you through the. This approach involves extending the sms otp. The user is presented with. Keycloak Authentication Otp.
From www.aukfood.fr
Les différents modes d'authentification sous Keycloak Aukfood Keycloak Authentication Otp This article will guide you through the. User visits the application website and enters the mobile number or username. The user is presented with a choice of three otp methods for authentication: This approach involves extending the sms otp. Learn how to create a custom authenticator using sms/otp verification in keycloak. Learn how to configure authentication policies, credential types, and. Keycloak Authentication Otp.
From ahus1.github.io
One Time Password (OTP) policies Keycloak Docs Keycloak Authentication Otp Learn how to configure authentication policies, credential types, and kerberos integration for red hat build of keycloak. This article will guide you through the. User visits the application website and enters the mobile number or username. Learn how to create a custom authenticator using sms/otp verification in keycloak. The user is presented with a choice of three otp methods for. Keycloak Authentication Otp.
From github.com
GitHub akshatsachdeva/keycloakotpwebhook Keycloak authentication Keycloak Authentication Otp Learn how to configure authentication policies, credential types, and kerberos integration for red hat build of keycloak. This article will guide you through the. This approach involves extending the sms otp. Learn how to create a custom authenticator using sms/otp verification in keycloak. The user is presented with a choice of three otp methods for authentication: User visits the application. Keycloak Authentication Otp.
From docs.wundergraph.com
Keycloak OpenID Connect Authentication Example WunderGraph Docs Keycloak Authentication Otp Learn how to configure authentication policies, credential types, and kerberos integration for red hat build of keycloak. The user is presented with a choice of three otp methods for authentication: This article will guide you through the. User visits the application website and enters the mobile number or username. This approach involves extending the sms otp. Learn how to create. Keycloak Authentication Otp.
From ultimatesecurity.pro
Keycloak TwoFactor Authentication · Ultimate Security Professional Blog Keycloak Authentication Otp Learn how to create a custom authenticator using sms/otp verification in keycloak. This approach involves extending the sms otp. Learn how to configure authentication policies, credential types, and kerberos integration for red hat build of keycloak. The user is presented with a choice of three otp methods for authentication: User visits the application website and enters the mobile number or. Keycloak Authentication Otp.
From github.com
GitHub akshatsachdeva/keycloakotpwebhook Keycloak authentication Keycloak Authentication Otp Learn how to configure authentication policies, credential types, and kerberos integration for red hat build of keycloak. The user is presented with a choice of three otp methods for authentication: This article will guide you through the. This approach involves extending the sms otp. Learn how to create a custom authenticator using sms/otp verification in keycloak. User visits the application. Keycloak Authentication Otp.