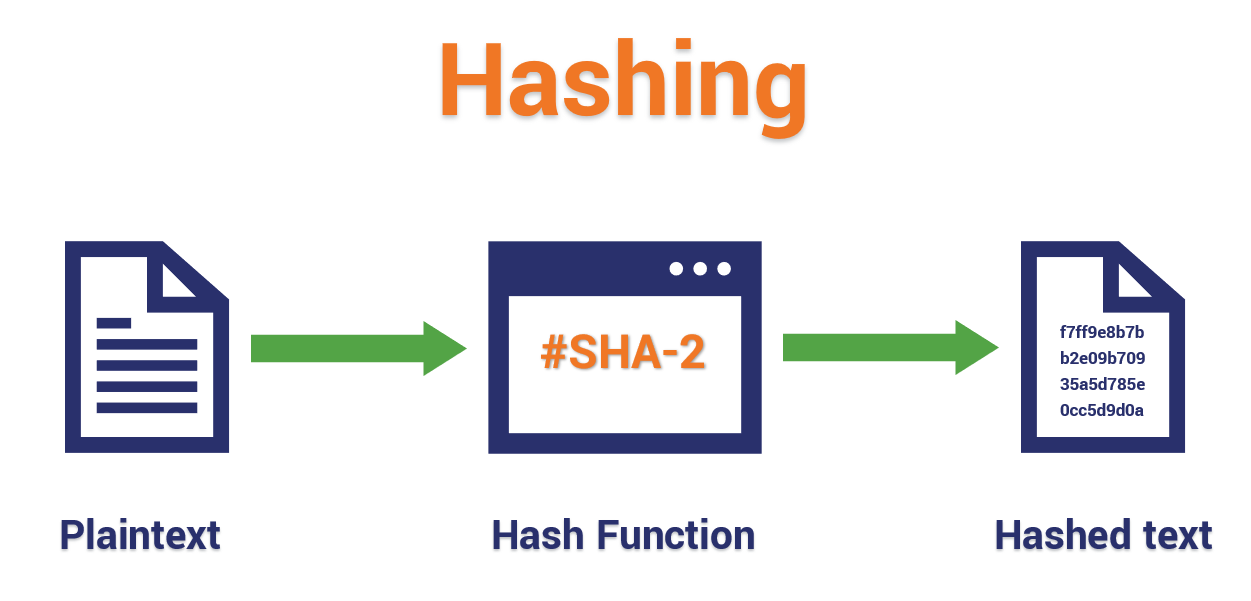
Hash Examples . Here “%” is the symbol for the mod function. If you get a “line length exception” error in hashcat, it is often because the hash mode that you have requested does not match the hash. Consider the following hash function used to hash integers to a table of sixteen slots. Learn how hashing works, why it's used, and popular hashing algorithms. Recall that the values 0 to 15 can be. 16 rows this is a list of hash functions, including cyclic redundancy checks, checksum functions, and cryptographic hash functions. Hash functions, tables, types, collisions, and methods (division, mid square, folding, multiplication) with practical examples and. Explore hashing in data structures: Hashing in data structure refers to using a hash function to map a key to a given index, which represents the location of where a key’s value, or hash value, is stored.
from www.thesslstore.com
Hash functions, tables, types, collisions, and methods (division, mid square, folding, multiplication) with practical examples and. Consider the following hash function used to hash integers to a table of sixteen slots. If you get a “line length exception” error in hashcat, it is often because the hash mode that you have requested does not match the hash. Learn how hashing works, why it's used, and popular hashing algorithms. Explore hashing in data structures: Recall that the values 0 to 15 can be. Hashing in data structure refers to using a hash function to map a key to a given index, which represents the location of where a key’s value, or hash value, is stored. 16 rows this is a list of hash functions, including cyclic redundancy checks, checksum functions, and cryptographic hash functions. Here “%” is the symbol for the mod function.
What Is a Hash Function in Cryptography? A Beginner’s Guide Hashed
Hash Examples Hash functions, tables, types, collisions, and methods (division, mid square, folding, multiplication) with practical examples and. Hash functions, tables, types, collisions, and methods (division, mid square, folding, multiplication) with practical examples and. 16 rows this is a list of hash functions, including cyclic redundancy checks, checksum functions, and cryptographic hash functions. If you get a “line length exception” error in hashcat, it is often because the hash mode that you have requested does not match the hash. Recall that the values 0 to 15 can be. Here “%” is the symbol for the mod function. Learn how hashing works, why it's used, and popular hashing algorithms. Consider the following hash function used to hash integers to a table of sixteen slots. Explore hashing in data structures: Hashing in data structure refers to using a hash function to map a key to a given index, which represents the location of where a key’s value, or hash value, is stored.
From www.youtube.com
Python hash() Function A Simple Guide with Example YouTube Hash Examples Recall that the values 0 to 15 can be. Hashing in data structure refers to using a hash function to map a key to a given index, which represents the location of where a key’s value, or hash value, is stored. Explore hashing in data structures: Consider the following hash function used to hash integers to a table of sixteen. Hash Examples.
From www.slideserve.com
PPT Hash Tables in C PowerPoint Presentation, free download ID3043234 Hash Examples Recall that the values 0 to 15 can be. Hashing in data structure refers to using a hash function to map a key to a given index, which represents the location of where a key’s value, or hash value, is stored. Consider the following hash function used to hash integers to a table of sixteen slots. Explore hashing in data. Hash Examples.
From narodnatribuna.info
What Is A Hash And How Does It Work Sentinelone Hash Examples Learn how hashing works, why it's used, and popular hashing algorithms. Explore hashing in data structures: 16 rows this is a list of hash functions, including cyclic redundancy checks, checksum functions, and cryptographic hash functions. Consider the following hash function used to hash integers to a table of sixteen slots. If you get a “line length exception” error in hashcat,. Hash Examples.
From www.ritchievink.com
Sparse neural networks and hash tables with Locality Sensitive Hashing Hash Examples Recall that the values 0 to 15 can be. Consider the following hash function used to hash integers to a table of sixteen slots. If you get a “line length exception” error in hashcat, it is often because the hash mode that you have requested does not match the hash. Here “%” is the symbol for the mod function. 16. Hash Examples.
From www.hackerearth.com
Basics of Hash Tables Tutorials & Notes Data Structures HackerEarth Hash Examples Here “%” is the symbol for the mod function. If you get a “line length exception” error in hashcat, it is often because the hash mode that you have requested does not match the hash. Explore hashing in data structures: Consider the following hash function used to hash integers to a table of sixteen slots. Learn how hashing works, why. Hash Examples.
From www.ionos.com
Hash functions definition, usage, and examples IONOS Hash Examples Hashing in data structure refers to using a hash function to map a key to a given index, which represents the location of where a key’s value, or hash value, is stored. Hash functions, tables, types, collisions, and methods (division, mid square, folding, multiplication) with practical examples and. 16 rows this is a list of hash functions, including cyclic redundancy. Hash Examples.
From www.hackerearth.com
Basics of Hash Tables Tutorials & Notes Data Structures HackerEarth Hash Examples Here “%” is the symbol for the mod function. 16 rows this is a list of hash functions, including cyclic redundancy checks, checksum functions, and cryptographic hash functions. Recall that the values 0 to 15 can be. Hashing in data structure refers to using a hash function to map a key to a given index, which represents the location of. Hash Examples.
From www.thesslstore.com
What Is a Hash Function in Cryptography? A Beginner’s Guide Hashed Hash Examples 16 rows this is a list of hash functions, including cyclic redundancy checks, checksum functions, and cryptographic hash functions. Recall that the values 0 to 15 can be. Explore hashing in data structures: Learn how hashing works, why it's used, and popular hashing algorithms. Hashing in data structure refers to using a hash function to map a key to a. Hash Examples.
From www.thesslstore.com
What Is a Hash Function in Cryptography? A Beginner’s Guide Hashed Hash Examples Here “%” is the symbol for the mod function. Learn how hashing works, why it's used, and popular hashing algorithms. Consider the following hash function used to hash integers to a table of sixteen slots. 16 rows this is a list of hash functions, including cyclic redundancy checks, checksum functions, and cryptographic hash functions. Explore hashing in data structures: Recall. Hash Examples.
From codeahoy.com
Hash Functions CodeAhoy Hash Examples If you get a “line length exception” error in hashcat, it is often because the hash mode that you have requested does not match the hash. Explore hashing in data structures: Consider the following hash function used to hash integers to a table of sixteen slots. 16 rows this is a list of hash functions, including cyclic redundancy checks, checksum. Hash Examples.
From akshatm.svbtle.com
Consistent Hash Rings Explained Simply Hash Examples Consider the following hash function used to hash integers to a table of sixteen slots. Learn how hashing works, why it's used, and popular hashing algorithms. Hash functions, tables, types, collisions, and methods (division, mid square, folding, multiplication) with practical examples and. 16 rows this is a list of hash functions, including cyclic redundancy checks, checksum functions, and cryptographic hash. Hash Examples.
From www.geeksforgeeks.org
Hashing Data Structure Hash Examples Consider the following hash function used to hash integers to a table of sixteen slots. Learn how hashing works, why it's used, and popular hashing algorithms. Here “%” is the symbol for the mod function. If you get a “line length exception” error in hashcat, it is often because the hash mode that you have requested does not match the. Hash Examples.
From iq.opengenus.org
Hash Map / Hash table Hash Examples Here “%” is the symbol for the mod function. Recall that the values 0 to 15 can be. Learn how hashing works, why it's used, and popular hashing algorithms. If you get a “line length exception” error in hashcat, it is often because the hash mode that you have requested does not match the hash. 16 rows this is a. Hash Examples.
From www.youtube.com
Hash Tables Explained in Simple Terms YouTube Hash Examples 16 rows this is a list of hash functions, including cyclic redundancy checks, checksum functions, and cryptographic hash functions. Recall that the values 0 to 15 can be. Hashing in data structure refers to using a hash function to map a key to a given index, which represents the location of where a key’s value, or hash value, is stored.. Hash Examples.
From www.slideserve.com
PPT Hash Tables PowerPoint Presentation, free download ID257158 Hash Examples Explore hashing in data structures: 16 rows this is a list of hash functions, including cyclic redundancy checks, checksum functions, and cryptographic hash functions. Learn how hashing works, why it's used, and popular hashing algorithms. Consider the following hash function used to hash integers to a table of sixteen slots. Recall that the values 0 to 15 can be. Hash. Hash Examples.
From medium.com
Generalities Of The Hash Functions (Part I) ALTCOIN MAGAZINE Medium Hash Examples Hash functions, tables, types, collisions, and methods (division, mid square, folding, multiplication) with practical examples and. Here “%” is the symbol for the mod function. Learn how hashing works, why it's used, and popular hashing algorithms. 16 rows this is a list of hash functions, including cyclic redundancy checks, checksum functions, and cryptographic hash functions. If you get a “line. Hash Examples.
From www.slideserve.com
PPT 12 HashTable Data Structures PowerPoint Presentation, free Hash Examples 16 rows this is a list of hash functions, including cyclic redundancy checks, checksum functions, and cryptographic hash functions. Hashing in data structure refers to using a hash function to map a key to a given index, which represents the location of where a key’s value, or hash value, is stored. If you get a “line length exception” error in. Hash Examples.
From blog.pantherprotocol.io
What are hash functions in crypto and how do they work? Hash Examples Explore hashing in data structures: Hash functions, tables, types, collisions, and methods (division, mid square, folding, multiplication) with practical examples and. If you get a “line length exception” error in hashcat, it is often because the hash mode that you have requested does not match the hash. Recall that the values 0 to 15 can be. Hashing in data structure. Hash Examples.
From techvidvan.com
Hash Table Hashing in Data Structure TechVidvan Hash Examples Recall that the values 0 to 15 can be. Learn how hashing works, why it's used, and popular hashing algorithms. Explore hashing in data structures: If you get a “line length exception” error in hashcat, it is often because the hash mode that you have requested does not match the hash. Hashing in data structure refers to using a hash. Hash Examples.
From www.geeksforgeeks.org
Cryptographic Hash Function in Java Hash Examples If you get a “line length exception” error in hashcat, it is often because the hash mode that you have requested does not match the hash. 16 rows this is a list of hash functions, including cyclic redundancy checks, checksum functions, and cryptographic hash functions. Hashing in data structure refers to using a hash function to map a key to. Hash Examples.
From www.ssla.co.uk
What is hash function? And how does it work ssla.co.uk Hash Examples Hash functions, tables, types, collisions, and methods (division, mid square, folding, multiplication) with practical examples and. Explore hashing in data structures: Consider the following hash function used to hash integers to a table of sixteen slots. Here “%” is the symbol for the mod function. Hashing in data structure refers to using a hash function to map a key to. Hash Examples.
From academy.bit2me.com
Hash function concept and application in Bitcoin Hash Examples 16 rows this is a list of hash functions, including cyclic redundancy checks, checksum functions, and cryptographic hash functions. Hashing in data structure refers to using a hash function to map a key to a given index, which represents the location of where a key’s value, or hash value, is stored. Consider the following hash function used to hash integers. Hash Examples.
From www.sqlshack.com
Diving deep with complex Data Structures Hash Examples Hash functions, tables, types, collisions, and methods (division, mid square, folding, multiplication) with practical examples and. If you get a “line length exception” error in hashcat, it is often because the hash mode that you have requested does not match the hash. 16 rows this is a list of hash functions, including cyclic redundancy checks, checksum functions, and cryptographic hash. Hash Examples.
From examples.javacodegeeks.com
Java Hash Example Java Code Geeks Hash Examples Explore hashing in data structures: Hashing in data structure refers to using a hash function to map a key to a given index, which represents the location of where a key’s value, or hash value, is stored. If you get a “line length exception” error in hashcat, it is often because the hash mode that you have requested does not. Hash Examples.
From www.xeushack.com
What Is a Hash? Hacking Tutorials by Xeus Hash Examples Hashing in data structure refers to using a hash function to map a key to a given index, which represents the location of where a key’s value, or hash value, is stored. 16 rows this is a list of hash functions, including cyclic redundancy checks, checksum functions, and cryptographic hash functions. Recall that the values 0 to 15 can be.. Hash Examples.
From auth0.com
How to Hash Passwords OneWay Road to Enhanced Security Hash Examples Hash functions, tables, types, collisions, and methods (division, mid square, folding, multiplication) with practical examples and. Explore hashing in data structures: Consider the following hash function used to hash integers to a table of sixteen slots. Here “%” is the symbol for the mod function. If you get a “line length exception” error in hashcat, it is often because the. Hash Examples.
From favtutor.com
Hashing in data structure Guide with Examples) FavTutor Hash Examples Explore hashing in data structures: If you get a “line length exception” error in hashcat, it is often because the hash mode that you have requested does not match the hash. Recall that the values 0 to 15 can be. Hash functions, tables, types, collisions, and methods (division, mid square, folding, multiplication) with practical examples and. Hashing in data structure. Hash Examples.
From blog.geisonbiazus.com
Algorithms and Data Structures Series Hash Maps Geison Biazus Hash Examples Here “%” is the symbol for the mod function. Consider the following hash function used to hash integers to a table of sixteen slots. If you get a “line length exception” error in hashcat, it is often because the hash mode that you have requested does not match the hash. Learn how hashing works, why it's used, and popular hashing. Hash Examples.
From en.wikipedia.org
Hash table Wikipedia Hash Examples Hashing in data structure refers to using a hash function to map a key to a given index, which represents the location of where a key’s value, or hash value, is stored. Consider the following hash function used to hash integers to a table of sixteen slots. Recall that the values 0 to 15 can be. 16 rows this is. Hash Examples.
From www.codingninjas.com
Hash Function in Data Structure Coding Ninjas Hash Examples Hashing in data structure refers to using a hash function to map a key to a given index, which represents the location of where a key’s value, or hash value, is stored. Explore hashing in data structures: Hash functions, tables, types, collisions, and methods (division, mid square, folding, multiplication) with practical examples and. If you get a “line length exception”. Hash Examples.
From www.hackerearth.com
Basics of Hash Tables Tutorials & Notes Data Structures HackerEarth Hash Examples Consider the following hash function used to hash integers to a table of sixteen slots. Explore hashing in data structures: Hash functions, tables, types, collisions, and methods (division, mid square, folding, multiplication) with practical examples and. Recall that the values 0 to 15 can be. 16 rows this is a list of hash functions, including cyclic redundancy checks, checksum functions,. Hash Examples.
From www.slideserve.com
PPT HashBased Indexes PowerPoint Presentation, free download ID Hash Examples 16 rows this is a list of hash functions, including cyclic redundancy checks, checksum functions, and cryptographic hash functions. Hash functions, tables, types, collisions, and methods (division, mid square, folding, multiplication) with practical examples and. Learn how hashing works, why it's used, and popular hashing algorithms. Here “%” is the symbol for the mod function. Consider the following hash function. Hash Examples.
From www.hackerearth.com
Basics of Hash Tables Tutorials & Notes Data Structures HackerEarth Hash Examples If you get a “line length exception” error in hashcat, it is often because the hash mode that you have requested does not match the hash. Learn how hashing works, why it's used, and popular hashing algorithms. Consider the following hash function used to hash integers to a table of sixteen slots. Explore hashing in data structures: 16 rows this. Hash Examples.
From www.slideserve.com
PPT Hash Tables PowerPoint Presentation, free download ID4352431 Hash Examples Explore hashing in data structures: 16 rows this is a list of hash functions, including cyclic redundancy checks, checksum functions, and cryptographic hash functions. Consider the following hash function used to hash integers to a table of sixteen slots. Hash functions, tables, types, collisions, and methods (division, mid square, folding, multiplication) with practical examples and. If you get a “line. Hash Examples.
From www.youtube.com
Learn Hash Tables in 13 minutes ️⃣ YouTube Hash Examples If you get a “line length exception” error in hashcat, it is often because the hash mode that you have requested does not match the hash. Consider the following hash function used to hash integers to a table of sixteen slots. Hash functions, tables, types, collisions, and methods (division, mid square, folding, multiplication) with practical examples and. Recall that the. Hash Examples.