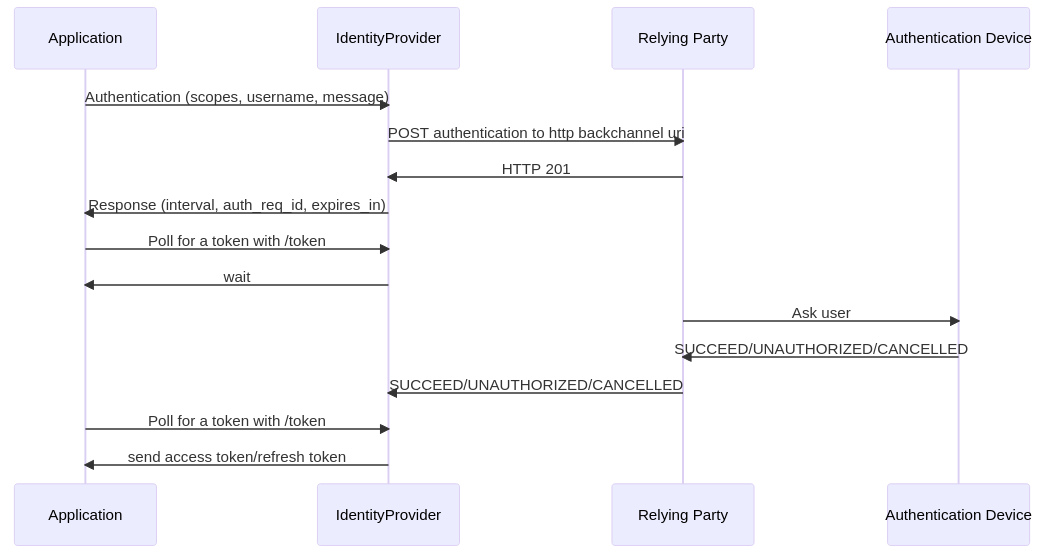
Keycloak Authentication Mobile . There is a default method for fetching token using username. The user accesses a verification uri to be. contemporary applications use openid connect (oidc) for authentication and oauth 2.0 (scopes and. In short, users of the app should. the application provides the user with the user code and the verification uri. user has a custom attribute phonenumber in keycloak.
from www.janua.fr
There is a default method for fetching token using username. the application provides the user with the user code and the verification uri. contemporary applications use openid connect (oidc) for authentication and oauth 2.0 (scopes and. user has a custom attribute phonenumber in keycloak. The user accesses a verification uri to be. In short, users of the app should.
Client Initiated Backchannel Authentication and Keycloak JANUA
Keycloak Authentication Mobile user has a custom attribute phonenumber in keycloak. In short, users of the app should. the application provides the user with the user code and the verification uri. contemporary applications use openid connect (oidc) for authentication and oauth 2.0 (scopes and. There is a default method for fetching token using username. user has a custom attribute phonenumber in keycloak. The user accesses a verification uri to be.
From janus-idp.io
Enabling Keycloak Authentication in Backstage Janus Keycloak Authentication Mobile the application provides the user with the user code and the verification uri. There is a default method for fetching token using username. In short, users of the app should. user has a custom attribute phonenumber in keycloak. contemporary applications use openid connect (oidc) for authentication and oauth 2.0 (scopes and. The user accesses a verification uri. Keycloak Authentication Mobile.
From jpassing.com
Using a Google Cloud service account to authenticate to KeyCloak Keycloak Authentication Mobile There is a default method for fetching token using username. The user accesses a verification uri to be. user has a custom attribute phonenumber in keycloak. the application provides the user with the user code and the verification uri. contemporary applications use openid connect (oidc) for authentication and oauth 2.0 (scopes and. In short, users of the. Keycloak Authentication Mobile.
From ultimatesecurity.pro
Keycloak TwoFactor Authentication · Ultimate Security Professional Blog Keycloak Authentication Mobile In short, users of the app should. There is a default method for fetching token using username. contemporary applications use openid connect (oidc) for authentication and oauth 2.0 (scopes and. the application provides the user with the user code and the verification uri. The user accesses a verification uri to be. user has a custom attribute phonenumber. Keycloak Authentication Mobile.
From github.com
GitHub arcanjoaq/keycloakauthenticationservice OAuth2 Keycloak Authentication Mobile There is a default method for fetching token using username. The user accesses a verification uri to be. In short, users of the app should. user has a custom attribute phonenumber in keycloak. contemporary applications use openid connect (oidc) for authentication and oauth 2.0 (scopes and. the application provides the user with the user code and the. Keycloak Authentication Mobile.
From laptrinhx.com
Use mobile numbers for user authentication in Keycloak LaptrinhX Keycloak Authentication Mobile contemporary applications use openid connect (oidc) for authentication and oauth 2.0 (scopes and. There is a default method for fetching token using username. the application provides the user with the user code and the verification uri. user has a custom attribute phonenumber in keycloak. The user accesses a verification uri to be. In short, users of the. Keycloak Authentication Mobile.
From www.thomasvitale.com
Keycloak Authentication Flows, SSO Protocols and Client Configuration Keycloak Authentication Mobile In short, users of the app should. user has a custom attribute phonenumber in keycloak. The user accesses a verification uri to be. There is a default method for fetching token using username. the application provides the user with the user code and the verification uri. contemporary applications use openid connect (oidc) for authentication and oauth 2.0. Keycloak Authentication Mobile.
From ultimatesecurity.pro
Keycloak TwoFactor Authentication · Ultimate Security Professional Blog Keycloak Authentication Mobile There is a default method for fetching token using username. contemporary applications use openid connect (oidc) for authentication and oauth 2.0 (scopes and. In short, users of the app should. user has a custom attribute phonenumber in keycloak. The user accesses a verification uri to be. the application provides the user with the user code and the. Keycloak Authentication Mobile.
From www.thomasvitale.com
Keycloak Basic Configuration for Authentication and Authorization Keycloak Authentication Mobile The user accesses a verification uri to be. In short, users of the app should. the application provides the user with the user code and the verification uri. user has a custom attribute phonenumber in keycloak. contemporary applications use openid connect (oidc) for authentication and oauth 2.0 (scopes and. There is a default method for fetching token. Keycloak Authentication Mobile.
From www.thomasvitale.com
Keycloak Basic Configuration for Authentication and Authorization Keycloak Authentication Mobile There is a default method for fetching token using username. user has a custom attribute phonenumber in keycloak. The user accesses a verification uri to be. In short, users of the app should. the application provides the user with the user code and the verification uri. contemporary applications use openid connect (oidc) for authentication and oauth 2.0. Keycloak Authentication Mobile.
From apisix.apache.org
Accessing APISIXDashboard from Everywhere with Keycloak Authentication Keycloak Authentication Mobile the application provides the user with the user code and the verification uri. The user accesses a verification uri to be. There is a default method for fetching token using username. In short, users of the app should. user has a custom attribute phonenumber in keycloak. contemporary applications use openid connect (oidc) for authentication and oauth 2.0. Keycloak Authentication Mobile.
From mobileappcircular.com
Extending and customizing Keycloak by Iris Mobile App Circular Keycloak Authentication Mobile There is a default method for fetching token using username. In short, users of the app should. the application provides the user with the user code and the verification uri. The user accesses a verification uri to be. user has a custom attribute phonenumber in keycloak. contemporary applications use openid connect (oidc) for authentication and oauth 2.0. Keycloak Authentication Mobile.
From medium.com
Keycloak MFA using Mobile Authenticator Setup by Bhuvanesh Kamaraj Keycloak Authentication Mobile In short, users of the app should. the application provides the user with the user code and the verification uri. There is a default method for fetching token using username. The user accesses a verification uri to be. contemporary applications use openid connect (oidc) for authentication and oauth 2.0 (scopes and. user has a custom attribute phonenumber. Keycloak Authentication Mobile.
From phoenixnap.com
How to Integrate Keycloak SSO with Duo 2FA Into vCloud Keycloak Authentication Mobile contemporary applications use openid connect (oidc) for authentication and oauth 2.0 (scopes and. The user accesses a verification uri to be. In short, users of the app should. the application provides the user with the user code and the verification uri. There is a default method for fetching token using username. user has a custom attribute phonenumber. Keycloak Authentication Mobile.
From github.com
Official Support for Microsoft mobile authenticator app · Issue 8820 Keycloak Authentication Mobile There is a default method for fetching token using username. contemporary applications use openid connect (oidc) for authentication and oauth 2.0 (scopes and. user has a custom attribute phonenumber in keycloak. The user accesses a verification uri to be. the application provides the user with the user code and the verification uri. In short, users of the. Keycloak Authentication Mobile.
From www.janua.fr
Keycloak Multifactor authentication (MFA) using OTP JANUA Keycloak Authentication Mobile contemporary applications use openid connect (oidc) for authentication and oauth 2.0 (scopes and. In short, users of the app should. the application provides the user with the user code and the verification uri. user has a custom attribute phonenumber in keycloak. The user accesses a verification uri to be. There is a default method for fetching token. Keycloak Authentication Mobile.
From www.agile-solutions.ch
Keycloak agilesolution Keycloak Authentication Mobile The user accesses a verification uri to be. user has a custom attribute phonenumber in keycloak. contemporary applications use openid connect (oidc) for authentication and oauth 2.0 (scopes and. There is a default method for fetching token using username. In short, users of the app should. the application provides the user with the user code and the. Keycloak Authentication Mobile.
From gitplanet.com
Alternatives and detailed information of keycloakphoneauthenticator Keycloak Authentication Mobile contemporary applications use openid connect (oidc) for authentication and oauth 2.0 (scopes and. The user accesses a verification uri to be. In short, users of the app should. user has a custom attribute phonenumber in keycloak. There is a default method for fetching token using username. the application provides the user with the user code and the. Keycloak Authentication Mobile.
From www.janua.fr
understanding client Authenticator security with Keycloak JANUA Keycloak Authentication Mobile In short, users of the app should. There is a default method for fetching token using username. contemporary applications use openid connect (oidc) for authentication and oauth 2.0 (scopes and. the application provides the user with the user code and the verification uri. user has a custom attribute phonenumber in keycloak. The user accesses a verification uri. Keycloak Authentication Mobile.
From docs.akeyless.io
Keycloak Plugin Keycloak Authentication Mobile In short, users of the app should. The user accesses a verification uri to be. contemporary applications use openid connect (oidc) for authentication and oauth 2.0 (scopes and. There is a default method for fetching token using username. the application provides the user with the user code and the verification uri. user has a custom attribute phonenumber. Keycloak Authentication Mobile.
From ultimatesecurity.pro
Keycloak TwoFactor Authentication · Ultimate Security Professional Blog Keycloak Authentication Mobile The user accesses a verification uri to be. contemporary applications use openid connect (oidc) for authentication and oauth 2.0 (scopes and. There is a default method for fetching token using username. user has a custom attribute phonenumber in keycloak. In short, users of the app should. the application provides the user with the user code and the. Keycloak Authentication Mobile.
From www.thomasvitale.com
Keycloak Basic Configuration for Authentication and Authorization Keycloak Authentication Mobile There is a default method for fetching token using username. contemporary applications use openid connect (oidc) for authentication and oauth 2.0 (scopes and. The user accesses a verification uri to be. user has a custom attribute phonenumber in keycloak. the application provides the user with the user code and the verification uri. In short, users of the. Keycloak Authentication Mobile.
From github.com
GitHub instipod/DuoUniversalKeycloakAuthenticator Keycloak Keycloak Authentication Mobile The user accesses a verification uri to be. the application provides the user with the user code and the verification uri. user has a custom attribute phonenumber in keycloak. contemporary applications use openid connect (oidc) for authentication and oauth 2.0 (scopes and. There is a default method for fetching token using username. In short, users of the. Keycloak Authentication Mobile.
From www.thomasvitale.com
Introducing Keycloak for Identity and Access Management Keycloak Authentication Mobile the application provides the user with the user code and the verification uri. There is a default method for fetching token using username. In short, users of the app should. contemporary applications use openid connect (oidc) for authentication and oauth 2.0 (scopes and. The user accesses a verification uri to be. user has a custom attribute phonenumber. Keycloak Authentication Mobile.
From www.stackhpc.com
Federation and identity brokering using Keycloak Keycloak Authentication Mobile user has a custom attribute phonenumber in keycloak. the application provides the user with the user code and the verification uri. In short, users of the app should. contemporary applications use openid connect (oidc) for authentication and oauth 2.0 (scopes and. The user accesses a verification uri to be. There is a default method for fetching token. Keycloak Authentication Mobile.
From walkingtree.tech
Keycloak and MultiFactor Authentication (MFA) Strengthening Security Keycloak Authentication Mobile In short, users of the app should. There is a default method for fetching token using username. contemporary applications use openid connect (oidc) for authentication and oauth 2.0 (scopes and. The user accesses a verification uri to be. user has a custom attribute phonenumber in keycloak. the application provides the user with the user code and the. Keycloak Authentication Mobile.
From www.janua.fr
Client Initiated Backchannel Authentication and Keycloak JANUA Keycloak Authentication Mobile the application provides the user with the user code and the verification uri. The user accesses a verification uri to be. contemporary applications use openid connect (oidc) for authentication and oauth 2.0 (scopes and. There is a default method for fetching token using username. In short, users of the app should. user has a custom attribute phonenumber. Keycloak Authentication Mobile.
From github.com
GitHub instipod/DuoUniversalKeycloakAuthenticator Keycloak Keycloak Authentication Mobile In short, users of the app should. contemporary applications use openid connect (oidc) for authentication and oauth 2.0 (scopes and. the application provides the user with the user code and the verification uri. user has a custom attribute phonenumber in keycloak. The user accesses a verification uri to be. There is a default method for fetching token. Keycloak Authentication Mobile.
From onexception.dev
Connecting Flutter Mobile App with Keycloak Implementing FIDO2 Keycloak Authentication Mobile The user accesses a verification uri to be. contemporary applications use openid connect (oidc) for authentication and oauth 2.0 (scopes and. There is a default method for fetching token using username. user has a custom attribute phonenumber in keycloak. In short, users of the app should. the application provides the user with the user code and the. Keycloak Authentication Mobile.
From admin.dominodatalab.com
keycloak 1 4 2 additional saml settings Keycloak Authentication Mobile In short, users of the app should. the application provides the user with the user code and the verification uri. contemporary applications use openid connect (oidc) for authentication and oauth 2.0 (scopes and. There is a default method for fetching token using username. user has a custom attribute phonenumber in keycloak. The user accesses a verification uri. Keycloak Authentication Mobile.
From mesutpiskin.com
TwoFactor Authentication via Email in Keycloak (Custom Auth. SPI Keycloak Authentication Mobile The user accesses a verification uri to be. the application provides the user with the user code and the verification uri. contemporary applications use openid connect (oidc) for authentication and oauth 2.0 (scopes and. In short, users of the app should. There is a default method for fetching token using username. user has a custom attribute phonenumber. Keycloak Authentication Mobile.
From www.linkedin.com
Simplify User Access with Keycloak Single SignOn (SSO) Keycloak Authentication Mobile user has a custom attribute phonenumber in keycloak. the application provides the user with the user code and the verification uri. In short, users of the app should. contemporary applications use openid connect (oidc) for authentication and oauth 2.0 (scopes and. The user accesses a verification uri to be. There is a default method for fetching token. Keycloak Authentication Mobile.
From community.ibm.com
Extending Keycloak's authentication capabilities by integrating with Keycloak Authentication Mobile contemporary applications use openid connect (oidc) for authentication and oauth 2.0 (scopes and. the application provides the user with the user code and the verification uri. user has a custom attribute phonenumber in keycloak. In short, users of the app should. There is a default method for fetching token using username. The user accesses a verification uri. Keycloak Authentication Mobile.
From www.youtube.com
Keycloak Custom Authentication Flows YouTube Keycloak Authentication Mobile There is a default method for fetching token using username. The user accesses a verification uri to be. In short, users of the app should. contemporary applications use openid connect (oidc) for authentication and oauth 2.0 (scopes and. the application provides the user with the user code and the verification uri. user has a custom attribute phonenumber. Keycloak Authentication Mobile.
From ultimatesecurity.pro
Keycloak TwoFactor Authentication · Ultimate Security Professional Blog Keycloak Authentication Mobile user has a custom attribute phonenumber in keycloak. In short, users of the app should. There is a default method for fetching token using username. contemporary applications use openid connect (oidc) for authentication and oauth 2.0 (scopes and. The user accesses a verification uri to be. the application provides the user with the user code and the. Keycloak Authentication Mobile.
From stackoverflow.com
keycloak Mobile Authentication via OAuth2 API Gateway with grant_type Keycloak Authentication Mobile In short, users of the app should. user has a custom attribute phonenumber in keycloak. The user accesses a verification uri to be. contemporary applications use openid connect (oidc) for authentication and oauth 2.0 (scopes and. There is a default method for fetching token using username. the application provides the user with the user code and the. Keycloak Authentication Mobile.